Microsoft’s August 2022 Patch Tuesday Addresses 118 CVEs (CVE-2022-34713)

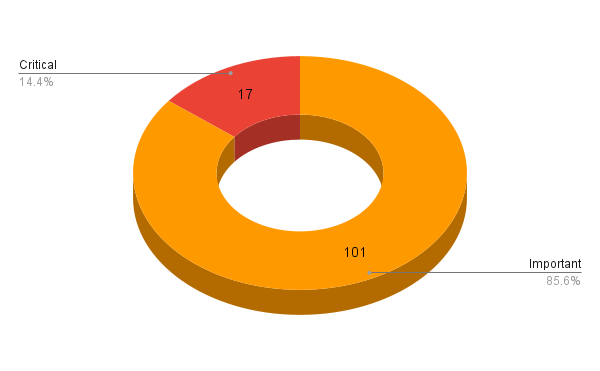
Microsoft addresses 118 CVEs in its August 2022 Patch Tuesday release, including 17 critical flaws.
- 17Critical
- 101Important
- 0Moderate
- 0Low
Microsoft patched 118 CVEs in its August 2022 Patch Tuesday release, with 17 rated as critical and 101 rated as important.
This month’s update includes patches for:
- .NET Core
- Active Directory Domain Services
- Azure Batch Node Agent
- Azure Real Time Operating System
- Azure Site Recovery
- Azure Sphere
- Microsoft ATA Port Driver
- Microsoft Bluetooth Driver
- Microsoft Edge (Chromium-based)
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Windows Support Diagnostic Tool (MSDT)
- Remote Access Service Point-to-Point Tunneling Protocol
- Role: Windows Fax Service
- Role: Windows Hyper-V
- System Center Operations Manager
- Visual Studio
- Windows Bluetooth Service
- Windows Canonical Display Driver
- Windows Cloud Files Mini Filter Driver
- Windows Defender Credential Guard
- Windows Digital Media
- Windows Error Reporting
- Windows Hello
- Windows Internet Information Services
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority (LSA)
- Windows Network File System
- Windows Partition Management Driver
- Windows Point-to-Point Tunneling Protocol
- Windows Print Spooler Components
- Windows Secure Boot
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows Storage Spaces Direct
- Windows Unified Write Filter
- Windows WebBrowser Control
- Windows Win32K
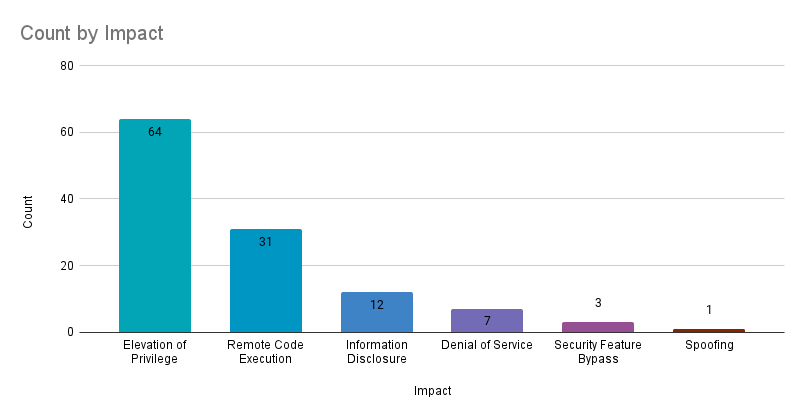
Elevation of privilege (EoP) vulnerabilities accounted for 54.2% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 26.3%.
As part of this month’s Patch Tuesday release, Microsoft addressed three security bypass vulnerabilities in a third-party driver affecting Windows Secure Boot: CVE-2022-34301, CVE-2022-34302 and CVE-2022-34303. These flaws were reported through the CERT Coordination Center (CERT/CC). We have not included these flaws as part of our metrics for this month’s Patch Tuesday release because they are standalone security updates for third-party drivers.
CVE-2022-34713, CVE-2022-35743 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerabilities
CVE-2022-34713 and CVE-2022-35743 are RCE vulnerabilities in the Microsoft Windows Support Diagnostic Tool (MSDT) for troubleshooting. Both CVEs received a CVSS score of 7.8 and are rated important.
CVE-2022-34713 is credited to security researcher Imre Rad, who first disclosed the flaw in January 2020. At the time, Microsoft chose not to patch the flaw. However, following renewed interest in MSDT spurred by the discovery and exploitation of CVE-2022-30190 (aka Follina), Microsoft patched the flaw this month.
Security researcher j00sean resurfaced Rad’s “related” flaw in MSDT that was dubbed DogWalk, though Microsoft says CVE-2022-34713 is a “variant of” DogWalk that has been exploited in the wild.
A variety of attackers have incorporated Follina into their campaigns according to researchers at Proofpoint, Symantec and Cyberint, so we strongly advise organizations apply the available patches for these similar vulnerabilities as soon as possible.
CVE-2022-21980, CVE-2022-24516, CVE-2022-24477 | Microsoft Exchange Server Elevation of Privilege Vulnerabilities
CVE-2022-21980, CVE-2022-24516 andCVE-2022-24477 are EoP vulnerabilities in Microsoft Exchange Server. Microsoft has published a companion blog post for this Exchange Server update. All three received a CVSSv3 score of 8.0 and were rated “Exploitation More Likely” according to Microsoft’s Exploitability Index. Tianze Ding with Tencent Xuanwu Lab is credited with discovering these vulnerabilities. Yuhao Weng with Sangfor Zhiniang Peng with Sangfor also share credit for CVE-2022-21980.
All three vulnerabilities require authentication and user interaction to exploit — an attacker would need to entice a target to visit a specially crafted Exchange server, likely through phishing. Microsoft also notes that Extended Protection needs to be enabled to fully mitigate these vulnerabilities.
CVE-2022-35755, CVE-2022-35793 | Windows Print Spooler Elevation of Privilege Vulnerabilities
CVE-2022-35755 andCVE-2022-35793are EoP vulnerabilities in Windows Print Spooler Components that both received a CVSSv3 score of 7.3 and were rated “Exploitation More Likely.” These vulnerabilities were discovered by Xuefeng Li with Sangfor who has a long history of disclosing Print Spooler flaws, tracing back to the original PrintNightmare (CVE-2021-34527). CVE-2022-35755 can be exploited using a specially crafted “input file,” while exploitation of CVE-2022-35793 requires a user click on a specially crafted URL. Both would give the attacker SYSTEM privileges.
Both vulnerabilities can be mitigated by disabling the Print Spooler service, but CVE-2022-35793 can also be mitigated by disabling inbound remote printing via Group Policy.
CVE-2022-35804 | SMB Client and Server Remote Code Execution Vulnerability
CVE-2022-35804 is a RCE vulnerability affecting both the Server Message Block (SMB) client and server on Windows 11 systems using Microsoft SMB 3.1.1 (SMBv3). Microsoft rated this as “Exploitation More Likely” and assigned an 8.8 CVSSV3 score. This vulnerability is reminiscent of past SMB vulnerabilities such as the EternalBlue SMBv1 flaw patched in MS17-010 in March of 2017 that was exploited as part of the WannaCry incident in addition to the more recent CVE-2020-0796 “EternalDarkness” RCE flaw in SMB 3.1.1.
In March of 2022, Microsoft patched CVE-2022-24508, another similar RCE vulnerability impacting SMBv3. Fortunately that flaw has not seen exploitation in the wild, however any flaws impacting SMB always raise concerns of another WannaCry scenario. We strongly recommend patching this vulnerability as soon as possible. Microsoft does provide workaround guidance for organizations that are not able to immediately patch.
CVE-2022-34691 | Active Directory Domain Services Elevation of Privilege Vulnerability
CVE-2022-34691 is an EoP vulnerability affecting Active Directory Domain Services. With an 8.8 CVSSv3 score, this vulnerability could be exploited by an authenticated attacker to manipulate attributes of accounts and possibly acquire a certificate from Active Directory Certificate Services. This certificate would allow the attacker to elevate their privileges. The advisory notes that exploitation is only possible when Active Directory Certificate Services is running on the domain.
31 Elevation of Privilege Vulnerabilities in Azure Site Recovery
Azure Site Recovery, a suite of tools used for disaster recovery, had a significant number of CVE’s patched in this month's release, including 31 EoP vulnerabilities. CVSS scores range from 4.4 to 8.1 and all of the flaws were rated as Important and “Exploitation Less Likely.” A table of the vulnerabilities can be found below:
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2022-35802 | Azure Site Recovery Elevation of Privilege Vulnerability | 8.1 |
| CVE-2022-35817 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35816 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35815 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35789 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35814 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35790 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35791 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35813 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35786 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35785 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35811 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35810 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35784 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35788 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35818 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35782 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35799 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35781 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35780 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35775 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35819 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35809 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35801 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35807 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35808 | Azure Site Recovery Elevation of Privilege Vulnerability | 6.5 |
| CVE-2022-35787 | Azure Site Recovery Elevation of Privilege Vulnerability | 4.9 |
| CVE-2022-35774 | Azure Site Recovery Elevation of Privilege Vulnerability | 4.9 |
| CVE-2022-35800 | Azure Site Recovery Elevation of Privilege Vulnerability | 4.9 |
| CVE-2022-35812 | Azure Site Recovery Elevation of Privilege Vulnerability | 4.4 |
| CVE-2022-35783 | Azure Site Recovery Elevation of Privilege Vulnerability | 4.4 |
In our coverage of July’s Patch Tuesday release, we highlighted another EoP vulnerability discovered by Tenable Researcher Jimi Sebree alongside highlights of multiple additional vulnerabilities patched in the platform. With this month’s release, it’s clear that researchers continue to analyze cloud resources, helping to secure these services before attackers can capitalize on flaws in these highly valuable targets.
Windows Server 20H2 End Of Support
With the August Patch Tuesday release, Windows Server, version 20H2 has now reached its end of service and will no longer receive security updates. A Tenable plugin to identify systems using this version of Windows server will be released soon and we will update this post with the plugin ID once it is available.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains August 2022.
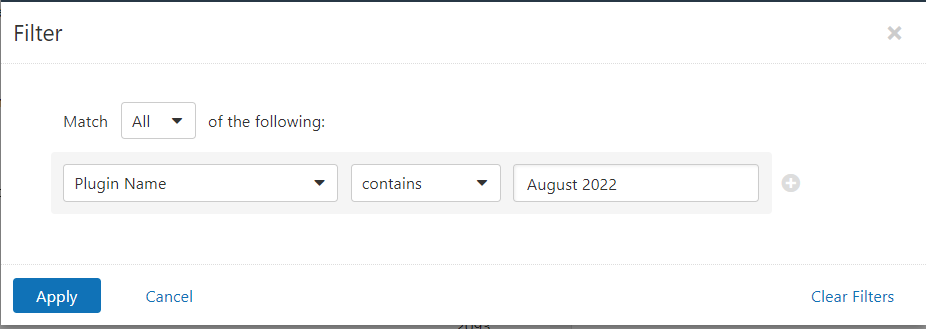
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
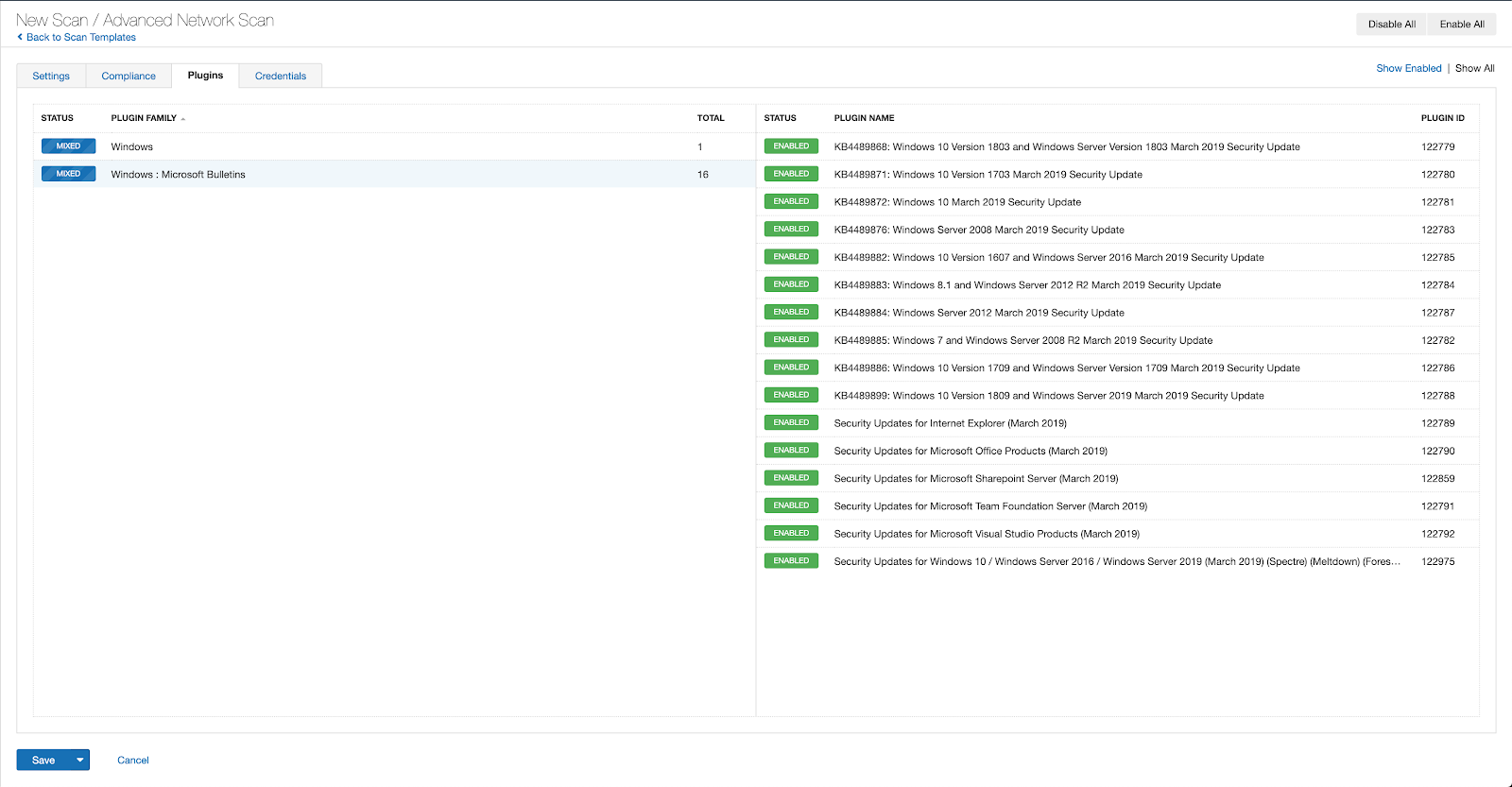
A list of all the plugins released for Tenable’s August 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's August 2022 Security Updates
- Tenable plugins for Microsoft August 2022 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

