Tenable comparé à Microsoft
Une gestion des vulnérabilités « suffisamment bonne » pour Microsoft ne suffit pas
En mars 2022, Tenable Research a découvert deux vulnérabilités (dont une critique) dans la plateforme Microsoft Azure, les deux étant exploitables. Microsoft a minimisé le risque et il a fallu 89 jours à la société pour reconnaître en privé la gravité du problème.
Découvrez Tenable en action
Vous voulez savoir comment Tenable peut aider votre équipe à dévoiler et éliminer les cyber-failles prioritaires qui mettent votre activité en péril ?
Complétez ce formulaire pour obtenir un devis personnalisé ou une démonstration.
Pourquoi les clients choisissent Tenable plutôt que Microsoft
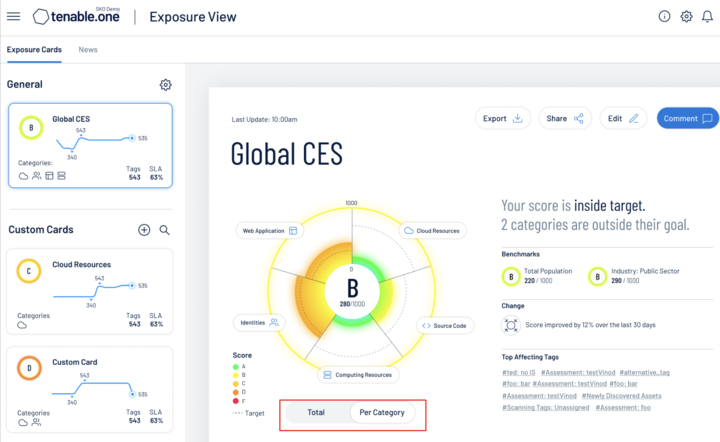
Comparaison de Tenable avec Microsoft
Précision au niveau des vulnérabilités et de la couverture
89 000 CVE - la couverture du secteur la plus large
Non communiqué
Priorisation
Exposure View combine le classement VPR de Tenable avec un score de criticité des assets
Ne prend pas en compte l'importance du contexte métier
Étendue de la couverture
Grande variété d'assets - points de terminaison, dispositifs réseau, technologies opérationnelles (OT), charges de travail cloud, applications web
Limité aux points de terminaison avec un agent et une capacité de base basée SNMP
Dashboarding et reporting
Bibliothèque extensive de dashboards et de rapports
Manque de dashboards et de rapports
Écosystème d’outils de gestion des vulnérabilités
Intégration et prise en charge des outils de remédiation tiers, workflow de remédiation
Intégration minimale avec des outils de remédiation comme BigFix
Technologies de scan
Basé sur agent et sans agent
Basé sur agent avec prise en charge limitée pour le scan réseau
Trust a leader
À LA UNE
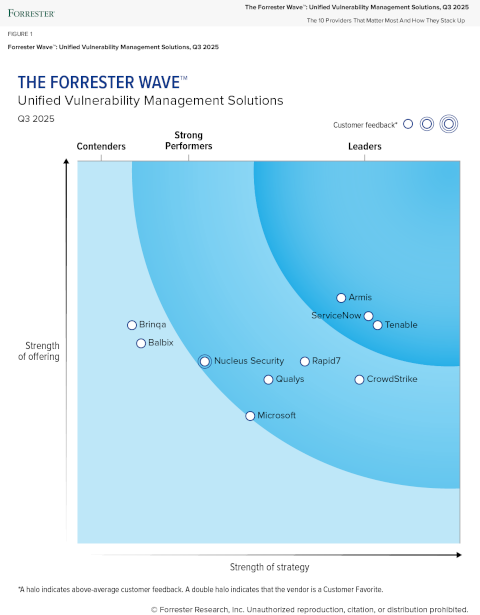
Tenable désigné comme l'un des leaders du marché dans le rapport « The Forrester Wave™ : Unified Vulnerability Management, Q3 2025
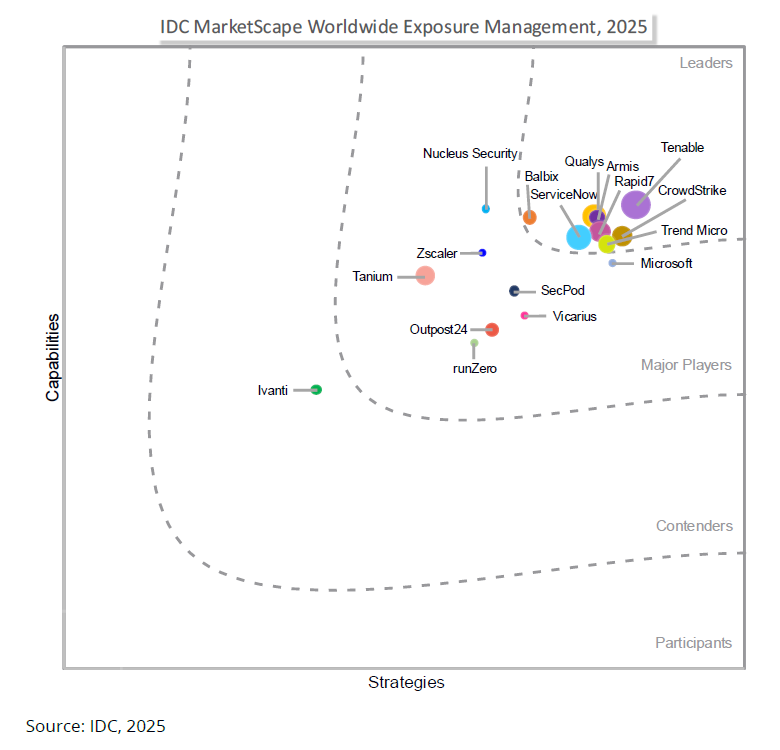
Lire le rapportTenable a été désigné leader dans le rapport « IDC MarketScape Worldwide Exposure Management 2025 Vendor Assessment »
"Organizations should consider Tenable One when seeking a unified exposure management platform that delivers broad asset coverage across IT, cloud, OT/IoT, identity, and application environments."
Lire le rapportDécouvrez Tenable en action
Vous voulez savoir comment Tenable peut aider votre équipe à dévoiler et éliminer les cyber-failles prioritaires qui mettent votre activité en péril ?
Complétez ce formulaire pour obtenir un devis personnalisé ou une démonstration.