How to Audit Microsoft Azure with Tenable Solutions

Microsoft Azure is a cloud offering that provides infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS) and software-as-a-service (SaaS) solutions. With the complexities associated with the cloud, auditing Azure architecture is challenging but vital to an organization’s cyber hygiene. Let's walk through how to audit Azure with Tenable.
Refactoring Microsoft Azure support to align with CIS guidance
Previously, compliance support in Tenable products was limited to the items and capabilities offered in the TNS Azure Best Practice audit files. Since those audit files were released, additional community guidance has come out, specifically guidance from the Center for Internet Security (CIS). To fully support the new CIS recommendations and incorporate feedback from customers using the TNS Azure Best Practice audits, we significantly refactored our Azure support in Tenable.io and Nessus.
Level 1 and Level 2 .audit files
This new CIS guidance offers users choices between Level 1 and Level 2 recommendations similar to its other benchmarks:
- Level 1: Generally, these recommendations should provide good security benefits without affecting most uses of the platform.
- Level 2: These settings are more secure, but can affect usage and workflows. As always, we recommend reviewing and testing new configurations to identify any settings that impact your business processes.
An example recommendation found in the CIS benchmark is to ensure RDP or SSH access is restricted from the internet for virtual machines. Such a misconfiguration could be catastrophic for an organization if utilized as an attack vector. Auditing Azure with Tenable audits based on CIS guidance ensures these misconfigurations are found and can be remediated in a reliable and expedient manner.
New audits being released
These new audits are based on the most recent benchmark guidance from CIS and should be considered direct replacements for the existing best-practice audits:
- CIS_Microsoft_Azure_Foundations_L1_v1.1.0.audit
- CIS_Microsoft_Azure_Foundations_L2_v1.1.0.audit
Existing audits being retired
Due to the refactoring of the compliance plugin for Azure and the more extensive coverage of the CIS benchmark, the existing TNS Azure Best Practice audits are being retired:
- TNS Microsoft Azure Best Practices Audit v1.0
- TNS Microsoft Azure Database Best Practices Audit v1.0.0
- TNS Microsoft Azure Websites Best Practices Audit v1.0.0
CIS Microsoft Azure Foundations Benchmark
The CIS Microsoft Azure Foundations benchmark is divided into multiple sections:
Identity and Access Management
Key recommendations include:
- Multi-factor authentication
- No guest users
- Users cannot register applications
Security Center
This section focuses on making sure key alert policies (e.g., ASC Default) are configured.
Storage Accounts
Key recommendations include:
- Enabling “secure transfer required”
- Setting default network access rule to “deny”
Database Services
Key recommendations include:
- “Ensuring Auditing is set to On”
- “Audit Retention is set to greater than 90 days“
- “Threat Detection types“ is set to “all“
Logging and Monitoring
A quality logging configuration is imperative to any secure IT environment. This section includes configuration checks to ensure:
- Logging for Azure Keyvault is enabled
- Activity Log Retention is set to 365 days or greater
- Log Profiles exist
Networking
A secure networking configuration is vital in a cloud environment. Some examples of CIS recommendations in this section are:
- “Ensuring that RDP/SSH access is restricted from the Internet“
- “Network Security Group Flow log retention is set to greater than 90 days“
Virtual Machine
Key recommendations include ensuring:
- Disks are encrypted
- Only approved extensions are installed
AppService
For Azure AppService, there are many recommendations to ensure the latest versions of the software are used as well as authentication and redirects are securely configured.
Other Security Considerations
Other security considerations include:
- Verifying expiration dates are set for keys and secrets
- Ensuring resource locks are used where appropriate
Check Overview
To audit appropriate configuration information as described in the CIS benchmark, Tenable has updated its Azure plugin with a list of new request types. An example check type using a new request type is here:

How to audit Microsoft Azure Foundations with Tenable using the CIS benchmark
Auditing an Azure environment requires some extra steps. As part of our release of plugin enhancements and audit coverage for the CIS benchmarks, we have implemented a new key credential type to simplify scanning setup.
At a high level, this involves: setting up an application registration in the Azure Active Directory (AD), ensuring it has proper API permissions, generating a secret key and providing the Tenable scan policy the appropriate client ID and key.
An example summary output for the CIS benchmarks:
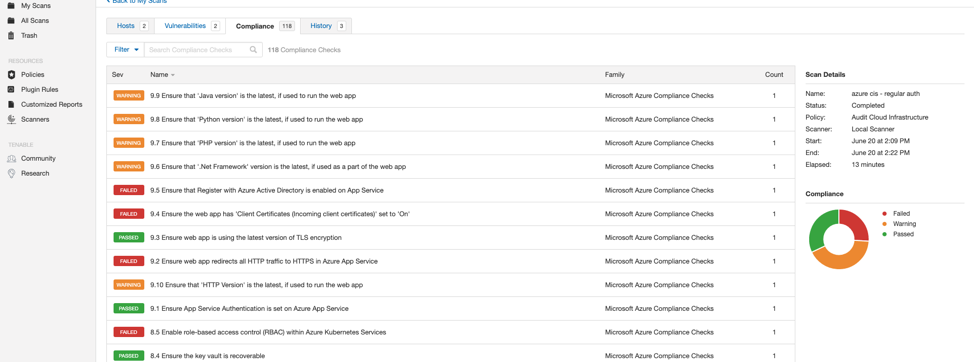
Below is a closer view of one of the results. This page shows:
- Pass/Fail status
- Remediation steps, if necessary
- Individual results from the systems scanned
- Reference information to cybersecurity frameworks
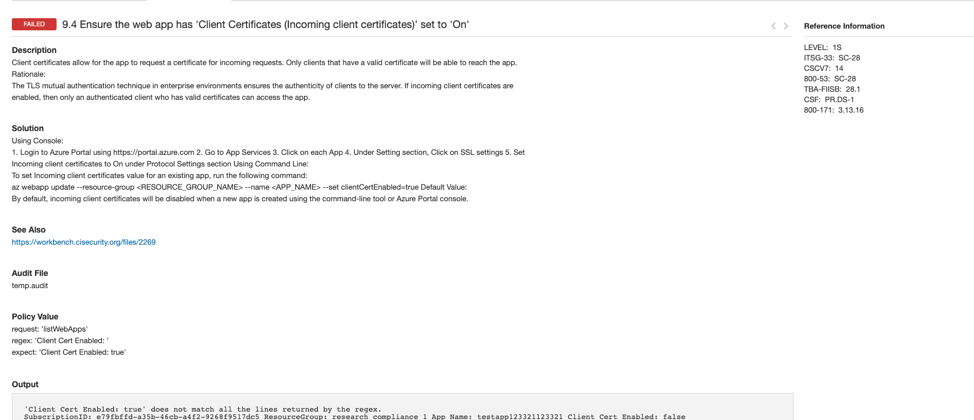
An example failing configuration check:
An example passing configuration check:
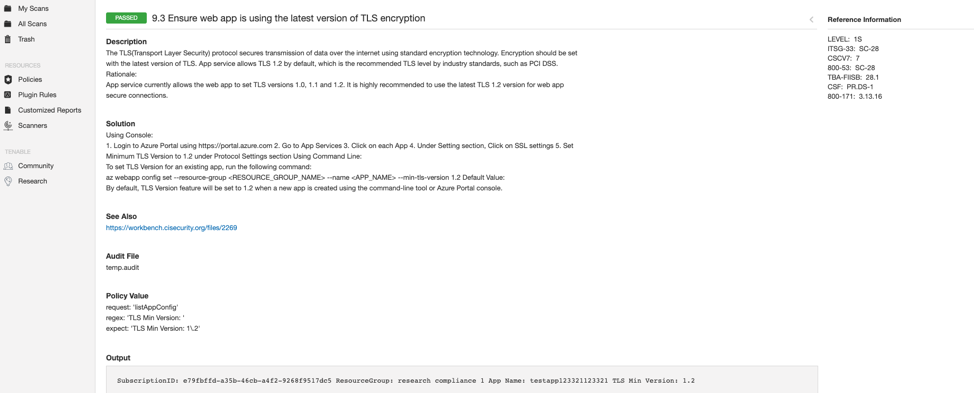
Summary
Auditing an Azure environment with Tenable.io and Nessus requires a little bit of extra setup compared to our standard compliance plugins but allows for a secure and automated method for evaluating your organization’s compliance.
At Tenable, we regularly update our policy compliance audits to match the newest versions by CIS and the U.S. Defense Information Systems Agency (DISA) to ensure our customers can easily keep pace with the latest best practices.
Azure compliance scan setup
The Azure plugin will scan the Azure REST API and audit the environment's configuration.
Scan requirements
Credentials
The plugin requires one of two supported credential sets.
- Password: This legacy credential set requires the username and password of a scan account created in Azure AD and the Application ID of a registered application.
- Key: This credential set requires the Application ID and client secret of a registered application as well as the Tenant ID.
Azure environment setup
To use the legacy password–based authentication for your scan, follow these steps:
Create Azure AD user account
- Create a new user for scanning in Azure AD
Assign user the Reader role
- Click the Subscriptions Blade -> **Your Subscription** -> Access Control (IAM) -> Role Assignments -> (+ Add)
- Add the Reader role to the user account you previously created for scanning
Register application - password
- Click Azure Active Directory->App Registrations
- Click the New Registrations application
- Give the application a name, choose your supported account types for your environment and click the register button
- Click Authentication and choose Yes for Default Client Type/Treat application as a public client
Assign API permissions
- Click your registered application in Azure Active Directory -> App Registrations - > Your Application -> API Permissions
- Add the following API permissions and click Grant admin consent for:
- Azure Active Directory Graph -> Directory.Read.All
- Azure Active Directory Graph -> User.Read
- Azure Service Management -> user_impersonation
To use the Key-based authentication method for your scan, follow these steps:
Register application - key
- Click Azure Active Directory -> App Registrations
- Click the New Registrations Application
- Give the application a name, choose your supported account types for your environment and click the register button
- Choose Public Client/Native for the redirect URI type. Add a redirect URL and click Register
Create application client secret
- Click your registered application in Azure Active Directory -> App Registrations
- Click Certificates and Secrets
- Click + New Client Secret
- Give the secret a name and click Add
- Copy the secret somewhere safe for use in authenticating during a scan
Assign the application the Reader role
- Click the Subscriptions Blade -> **Your Subscription** -> Access Control (IAM) -> Role Assignments -> (+ Add)
- Add the 'Reader' role to the application you previously created for scanning
Assign API permissions
- Click your registered application in Azure Active Directory -> App Registrations - > Your Application -> API Permissions
- Add the following API permissions and click Grant admin consent for:
- Azure Active Directory Graph -> Directory.Read.All
- Azure Active Directory Graph -> User.Read
- Azure Service Management -> user_impersonation
Join Tenable's Audit and Compliance Research Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

