CVE-2021-30116: Multiple Zero-Day Vulnerabilities in Kaseya VSA Exploited to Distribute REvil Ransomware

Zero-day vulnerabilities in popular remote monitoring and management software targeted by threat actors to distribute ransomware to reportedly over one million systems.
Update July 22, 2021: Kaseya says they've received a universal decryptor from a "trusted third party" and that are providing it to affected customers.
Update July 12, 2021: The Solutions section has been updated to confirm the availability of a patch for on-premises versions of Kaseya VSA to address three zero-day vulnerabilities.
Update July 9, 2021: The Analysis section has been updated to reflect new information about the vulnerabilities discovered and disclosed by DIVD CSIRT, including CVE-2021-30119 and CVE-2021-30120, as well as updates to the Solutions section.
Update July 6, 2021: Tenable is not impacted by the recent supply chain ransomware attack. We do not use Kaseya VSA, so our products and infrastructure are not vulnerable to the zero days used in the attack.
Background
On July 2, reports emerged that a number of companies whose networks are administered by managed service providers (MSPs) using Kaseya Virtual System Administrator (VSA), a remote monitoring and management (RMM) software from Kaseya Limited, became the victims of a large-scale ransomware attack.
The attacks have been attributed to REvil, also known as Sodinokibi, one of the most active ransomware groups today. REvil operates as ransomware-as-a-service (RaaS), whereby they develop the ransomware payload itself and provide the infrastructure for managing victim communications for negotiating payment and distributing decryption tools after payment.
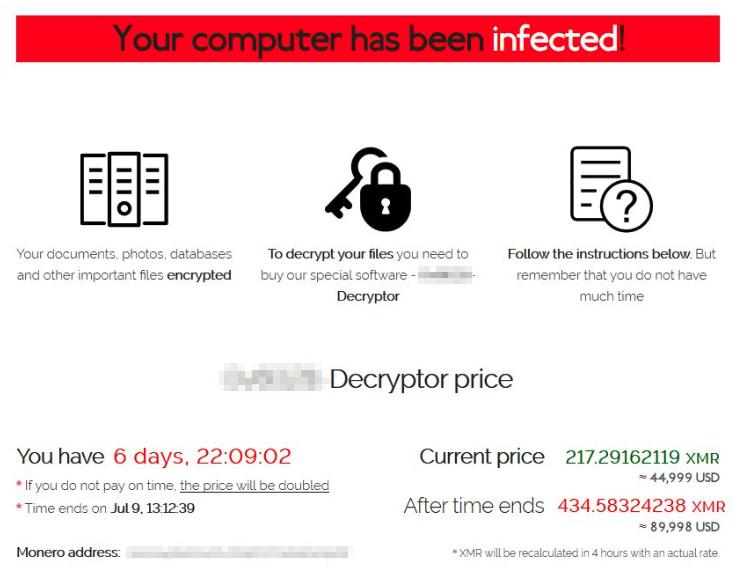
Image Source: Mark Loman (Twitter)
REvil does not attack organizations directly, rather they rely on affiliates, who do the dirty work to break into networks and deploy the ransomware. Affiliates receive a large portion of the ransom payment, while REvil takes a percentage for providing the ransomware and supporting infrastructure.
Similar to many other ransomware groups, REvil operates a leak website, where they publish the names of their victims along with a sampling of files they exfiltrated from the victim’s network. This is part of a tactic known as double extortion, which was pioneered by the Maze ransomware group in late 2019. Through double extortion, ransomware groups have seen their profits skyrocket, which has led to more activity in the space, and subsequently fueled the number of attacks.
Analysis
On July 5, Kaseya confirmed that multiple zero-day vulnerabilities were used to target vulnerable VSA server instances, including an authentication bypass flaw and an arbitrary command execution vulnerability. No specific details about the vulnerabilities were shared at the time and no additional CVEs have been reported.
Separately, through investigations into attacks against their clients, researchers at Huntress Labs and TrueSec identified three zero-day vulnerabilities:
- Authentication Bypass Vulnerability
- Arbitrary File Upload Vulnerability
- Code Injection Vulnerability
Huntress Labs, for example, believes the attackers were able to gain access to VSA servers through the use of the authentication bypass flaw.
“[...] we have high confidence that the threat actor used an authentication bypass in the web interface of Kaseya VSA to gain an authenticated session, upload the original payload, and then execute commands via code injection.”
In a later update from Huntress Labs, new evidence suggests that SQL injection may not have been the complete attack vector leading to code execution and another injection attack may be part of the attack chain.
Coordinated disclosure of zero-day vulnerabilities
On July 4, researchers at the Dutch Institute for Vulnerability Disclosure (DIVD) Computer Security Incident Response Team (CSIRT) published a blog post saying they’ve been working with Kaseya to coordinate the disclosure of “a number of zero-day vulnerabilities” in Kaseya VSA. They highlighted CVE-2021-30116, a vulnerability that they say is being used in these ransomware attacks, though they did not provide any further details about the other vulnerabilities. We suspect that these include the arbitrary file upload and code injection flaws.
On July 7, DIVD CSIRT published a follow-up blog providing a “limited” disclosure about their discoveries in Kaseya VSA. Several of the vulnerabilities listed in this limited disclosure have already been patched in previous versions of VSA, while three vulnerabilities have yet to be patched. These three vulnerabilities are expected to be addressed in the next on-premises release of Kaseya VSA, which has been scheduled for Sunday, July 11 at 4pm EDT. The following table breaks down each of the vulnerabilities reported by DIVD CSIRT.
| CVE | Description | Patched | Patch Release |
|---|---|---|---|
| CVE-2021-30118 | Remote Code Execution Vulnerability | Yes | 9.5.5 |
| CVE-2021-30117 | SQL Injection Vulnerability | Yes | 9.5.6 |
| CVE-2021-30121 | Local File Inclusion Vulnerability | Yes | 9.5.6 |
| CVE-2021-30201 | XML External Entity Vulnerability | Yes | 9.5.6 |
| CVE-2021-30116 | Credentials Leak and Business Logic Vulnerability | Yes | 9.5.7a |
| CVE-2021-30119 | Cross-Site Scripting Vulnerability | Yes | 9.5.7a |
| CVE-2021-30120 | Two-Factor Authentication Bypass Vulnerability | Yes | 9.5.7a |
REvil publishes notice on their leak website
On July 4, REvil published a post to their leak website, confirming that they were behind the attack against Kaseya.
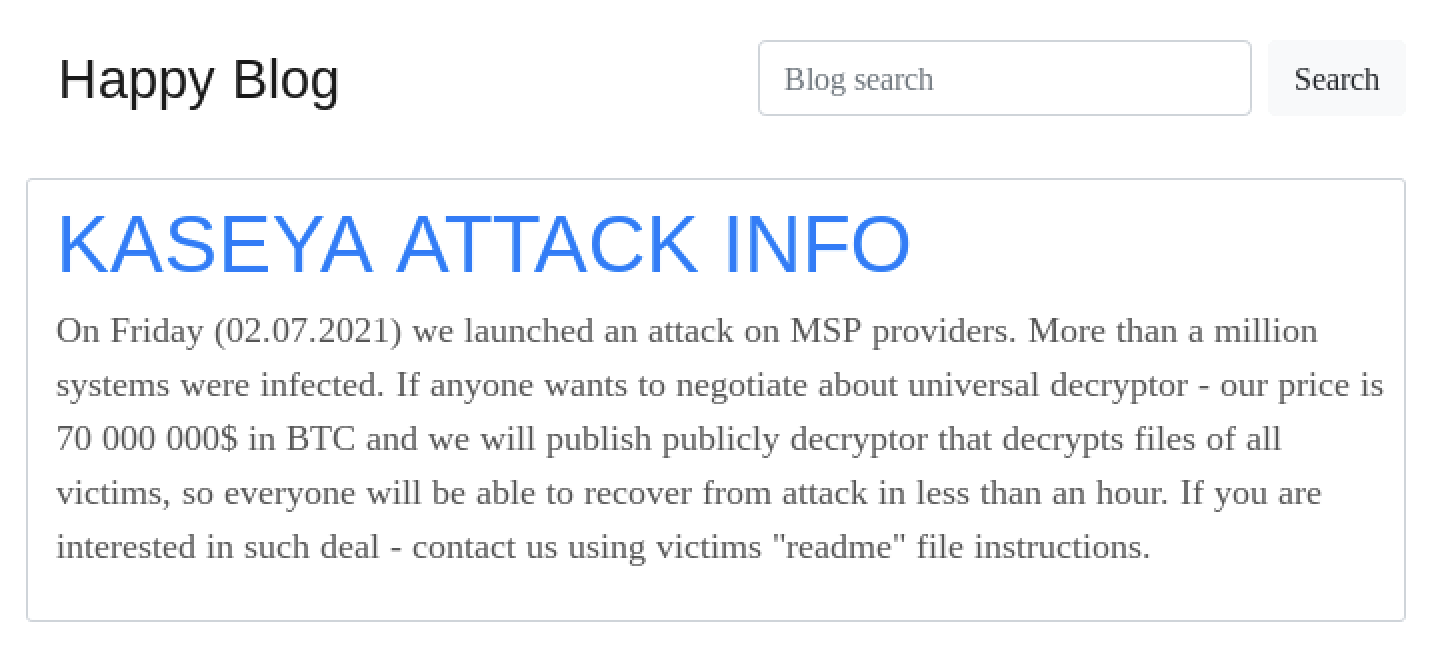
In the posting, REvil claims they have infected “more than a million systems” through this campaign and that they are willing to offer a universal decryptor tool for $70 million in Bitcoin, which could be used by any organization to decrypt files on systems that were struck by the REvil ransomware. If the number of systems infected is confirmed to be true, this attack would be considered the largest ransomware attacks ever conducted since the WannaCry ransomware attack in 2017.
Not the first time RMM tools have been targeted by ransomware groups
Over the last few years, threat actors have identified MSPs and RMMs as valuable targets for distributing ransomware to an MSP’s downstream customers. In February 2019, the GandCrab ransomware group exploited a two-year old vulnerability in the ConnectWise plugin for Kaseya VSA, which affected 126 Kaseya customers.
In December 2019, threat actors targeted an MSP and used the ConnectWise Control RMM software to distribute the Zeppelin Ransomware to the MSP’s downstream customers.
Because many organizations rely on MSPs to remotely monitor and manage their IT systems, and with the impact the attack against Kaseya VSA has had, we believe other ransomware groups will continue to look for flaws in other RMM software.
Proof of concept
At the time this blog post was published, there were no public proof-of-concept exploits for any of the vulnerabilities in Kaseya VSA.
Vendor response
Following the discovery of the vulnerability, Kaseya has been sharing updates for customers and other interested parties on their website. Kaseya proactively shut down their software-as-a-service (SaaS) servers while they investigated the attack, though they do not believe the attackers targeted SaaS customers. It appears the impacted organizations used Kaseya VSA on-premises.
Solution
At the time this blog post was published, there were no patches available for three zero-day vulnerabilities in Kaseya VSA. On July 11, 2021, Kaseya released VSA 9.5.7a (9.5.7.2994) for on-premises customers, which addresses the following vulnerabilities:
| CVE | Description |
|---|---|
| CVE-2021-30116 | Credentials Leak and Business Logic Vulnerability |
| CVE-2021-30119 | Cross-Site Scripting Vulnerability |
| CVE-2021-30120 | Two-Factor Authentication Bypass Vulnerability |
Customers are advised to follow Kaseya’s on-premises hardening and best practice guide prior to applying this patch.
Kaseya also deployed the patch to the SaaS platform prior to restoring the service, which should now be available for SaaS customers.
Identifying affected systems
Tenable has released a local Windows detection for Kaseya agents as well as a remote detection plugin for Kaseya VSA
A version check plugin for Kaseya VSA 9.5.7a will appear here once it has been released.
Get more information
- Reuters Report on Kaseya Ransomware Attack
- Kaseya Updates Regarding VSA Security Incident
- Huntress Labs Rapid Response: Mass MSP Ransomware Incident
- TRUESEC Blog on Kaseya Supply Chain Attack
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



