CVE-2020-6819, CVE-2020-6820: Critical Mozilla Firefox Zero-Day Vulnerabilities Exploited in the Wild

Researchers report multiple zero-day vulnerabilities in Mozilla Firefox and note that other browsers are also affected.
Contexte
On April 3, Mozilla Foundation published advisory 2020-11 for Mozilla Firefox and Mozilla Firefox Extended Support Release (ESR). The advisory includes fixes for two critical zero-day vulnerabilities, both of which were exploited in the wild as part of targeted attacks.
The discovery of these vulnerabilities was credited to security researchers Francisco Alonso and Javier Marcos. Alonso tweeted there are “more details to be published (including other browsers),” indicating these flaws likely extend to other web browsers. However, that information is currently not public, likely an effort to keep the details private until patches are available.
There is still lots of work to do and more details to be published (including other browsers). Ouvrez l'œil !
— Francisco Alonso (@revskills) April 3, 2020
As we’ve seen time and again, attackers continue to target widely installed applications such as web browsers. These latest vulnerabilities follow on the heels of another zero-day vulnerability in Mozilla Firefox exploited in the wild in January 2020.
Analyse
CVE-2020-6819 is a use-after-free vulnerability due to a race condition when the nsDocShell destructor is running. Based on the GitHub commit history for the nsDocShell.cpp file, it appears the issue exists due to the mContentViewer not being released properly.
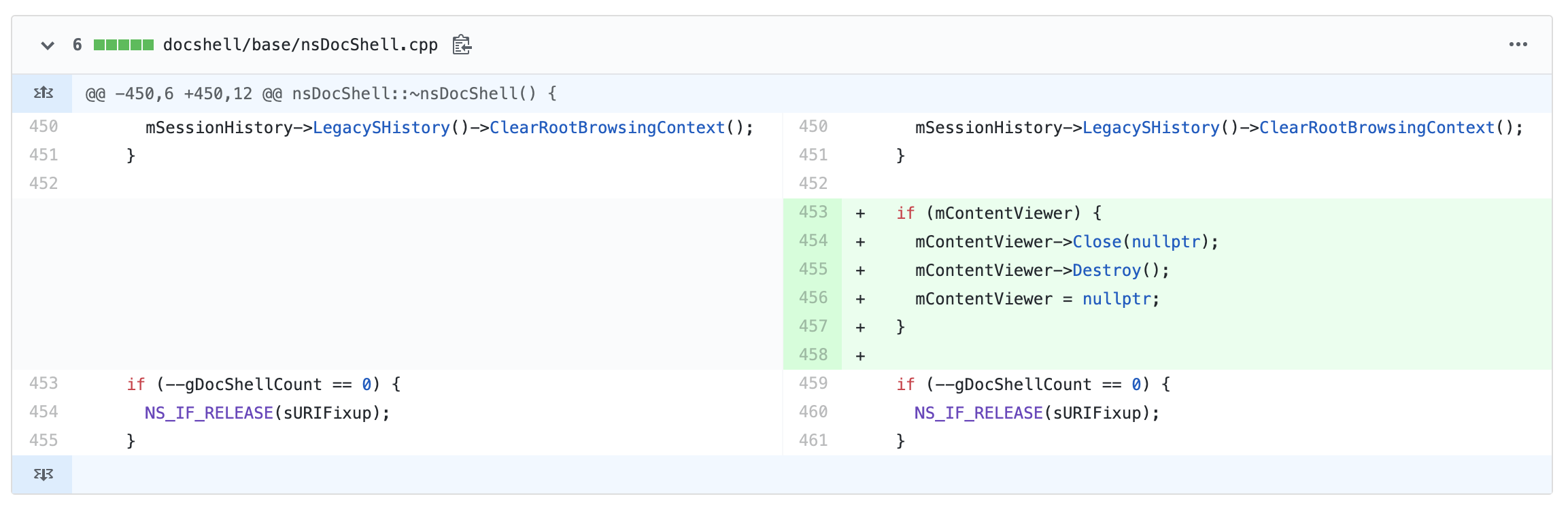 Image source: GitHub of nsDocShell changes made to address CVE-2020-6819
Image source: GitHub of nsDocShell changes made to address CVE-2020-6819
CVE-2020-6820 is a use-after-free vulnerability due to a race condition in the ReadableStream class, which is used to read a stream of data.
Source de l'image : MDN web docs
We anticipate further details about these vulnerabilities will be publicly available once the researchers publish their findings.
Démonstration de faisabilité (PoC)
At the time this blog post was published, there was no proof-of-concept code available for either of these vulnerabilities.
Solution
Mozilla Foundation released Mozilla Firefox 74.0.1 and Mozilla Firefox ESR 68.6.1 to address these vulnerabilities. While these vulnerabilities were exploited in targeted attacks, Firefox users are still encouraged to upgrade as soon as possible.
Identification des systèmes affectés
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
En savoir plus
Rejoignez l'équipe SRT de Tenable sur Tenable Community.
Apprenez-en plus sur Tenable, la première plateforme de Cyber Exposure qui vous permet de gérer votre surface d'attaque moderne de manière globale.
Profitez d'un essai gratuit de 30 jours de Tenable.io Vulnerability Management.
- Vulnerability Management


