CVE-2020-16846, CVE-2020-25592: Critical Vulnerabilities in Salt Framework Disclosed

SaltStack recommends immediate patching after their disclosure of three new vulnerabilities, two of which are rated critical and can be remotely exploited without authentication.
Background
On October 30, SaltStack published a pre-announcement advisory regarding three new vulnerabilities which had been discovered in Salt versions 3002 and earlier. The pre-announcement advisory stated that two of the vulnerabilities were likely to be rated high or critical severity and that updates would be released on November 3. In the November 3 advisory, SaltStack provided additional details about these CVEs and included a strong recommendation to prioritize these updates.
Analysis
CVE-2020-16846 is a critical shell injection vulnerability in the netapi Salt SSH client. According to the advisory, an unauthenticated attacker could use shell injection to execute arbitrary code on the Salt-API via the Salt SSH client. Interestingly, the patch was pushed to SaltStack’s GitHub on August 18th, though it’s not clear why the update and details were only recently disclosed. Based on the patch details, the fix prevents Popen with shell=True in the Salt SSH client.
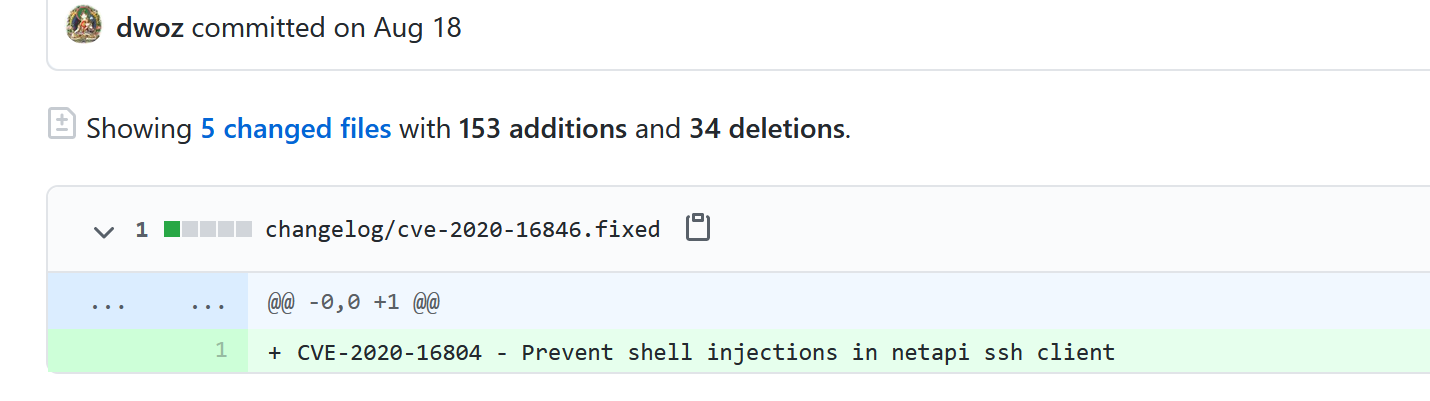
Image Source: SaltStack Github Repository
CVE-2020-25592 is an improper authentication vulnerability affecting users running the Salt API. Due to a validation issue when calling Salt SSH via the salt-api, an attacker could bypass authentication by simply supplying any value for “eauth” or “token” which would grant them the ability to run commands using Salt SSH.
CVE-2020-17490 is a low severity vulnerability in the SaltStack TLS module affecting any minions or masters which have used the create_ca, create_csr, and create_self_signed_cert functions. According to the information provided, private keys were created with world-readable permissions when these functions were used. The patch corrects this to ensure that private keys are not created with world-readable permissions.
Both CVE-2020-16846 and CVE-2020-17490 are credited to a researcher going by the nickname KPC, who reported these vulnerabilities through Trend Micro’s Zero Day Initiative (ZDI). KPC is also credited with four ZDI IDs which are listed in the upcoming advisories page, though we cannot confirm if those IDs are related to the recently disclosed vulnerabilities.
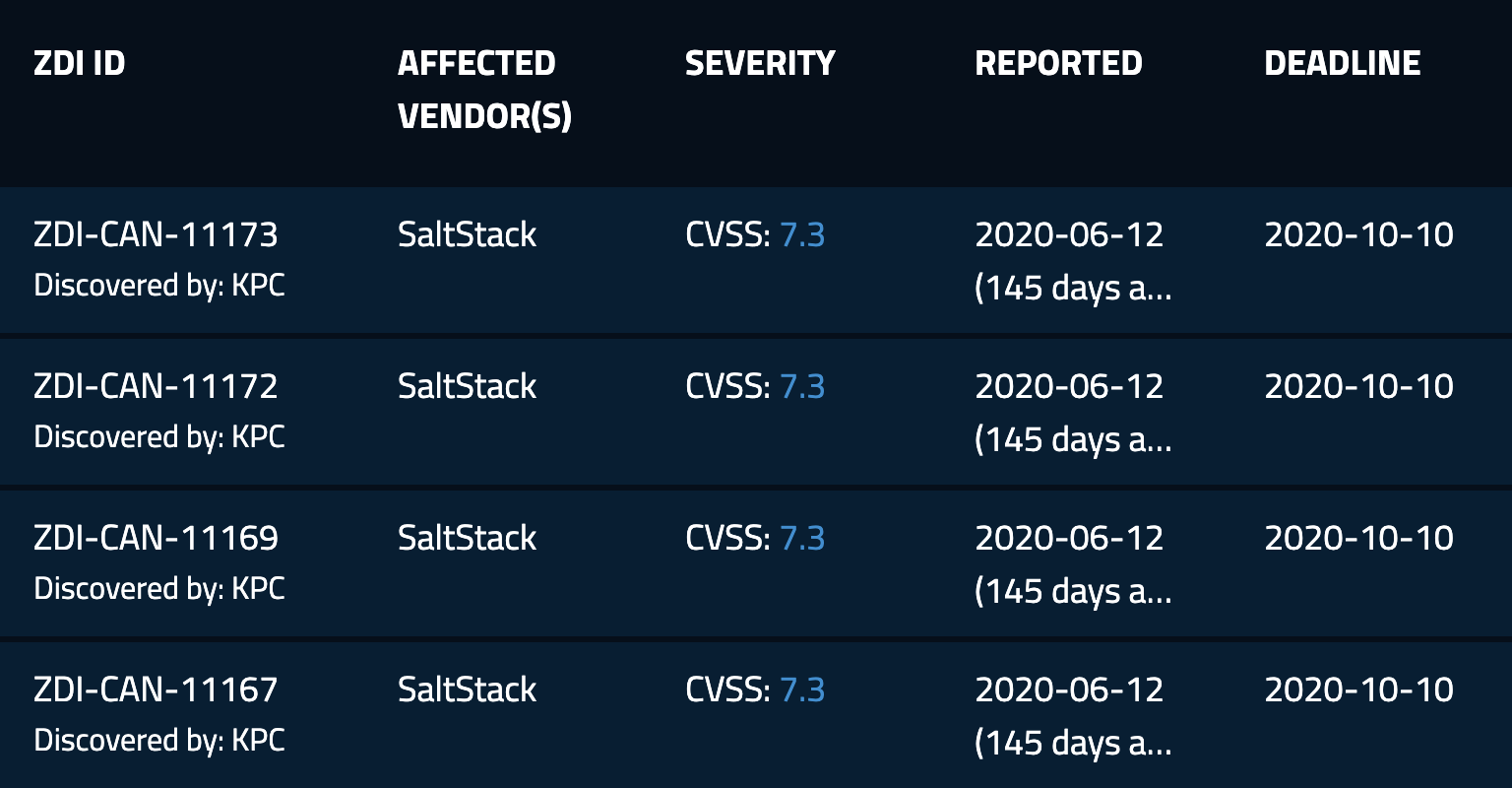
Image Source: Zero Day Initiative Upcoming Advisories
Ghosts of Vulnerabilities Past
The announcement of these critical vulnerabilities is reminiscent of flaws in the Salt framework disclosed earlier in the year. CVE-2020-11651, an authentication bypass vulnerability, and CVE-2020-11652, a directory traversal vulnerability, were both seen actively exploited just days after their patches were released by SaltStack. With a pre-announcement and advisory from SaltStack both encouraging users to apply these updates quickly, we anticipate attackers will be targeting these flaws and releasing exploits soon.
Over 6,000 publicly accessible Salt Master Nodes
According to data from Shodan, there are over 6,000 Salt master nodes publicly accessible, with a majority found in the United States.
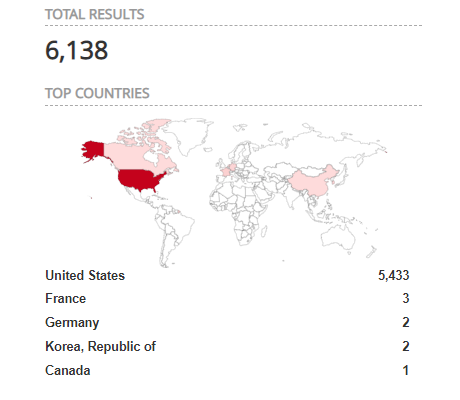
Image Source: Shodan
We anticipate that attackers will likely target these systems in the near future. Therefore, we highly recommend ensuring that these updates are applied as soon as possible.
Proof of concept
At the time this blog post was published, no proof-of-concept (PoC) code was available for any of the vulnerabilities.
Solution
SaltStack has published updates addressing all three of these CVEs. The following is a list of versions which have patches available:
- 3002.x
- 3001.x
- 3000.x
- 2019.x
The patches available have been released for the following versions:
- 3002
- 3001.1, 3001.2
- 3000.3, 3000.4
- 2019.2.5, 2019.2.6
- 2018.3.5
- 2017.7.4, 2017.7.8
- 2016.11.3, 2016.11.6, 2016.11.10
- 2016.3.4, 2016.3.6, 2016.3.8
- 2015.8.10, 2015.8.13
SaltStack encourages users running older versions of Salt to update to one of the versions listed above prior to applying available patches.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- SaltStack Advisory for CVE-2020-16846, CVE-2020-25592, CVE-2020-17490
- Tenable Blog for CVE-2020-11651 and CVE-2020-11652
- Patch details for CVE-2020-16846
- Patch details for CVE-2020-25592
- Patch details for CVE-2020-17490
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


