Continuous Scanning, Better Vulnerability Metrics
Active scanning, for the most part, is a snapshot-in-time view of vulnerabilities that exist in an organization’s environment. In a typical organization, scans occur on a quarterly or even monthly basis. However, the scans only tell you what happened in that moment, not what happened in the intervening days between scans. By scanning more frequently (and introducing real-time, passive scanning), organizations will have more accurate metrics that show how long an detected vulnerability was present and when it was mitigated.
Choosing to ignore new vulnerabilities because your IT team can’t patch them as fast as you can scan for them is just like airline pilots ignoring engine indicator lights because they can’t go out on the wing to fix the engine. Performing scanning, continuous sniffing or daily patch audits is beneficial to many parts of the organization. In this blog, I will discuss some of the advantages of real time vulnerability detection, also known as continuous monitoring.
React Faster to Change
I truly sympathize when I hear IT administrators lamenting about the ability to apply patches in a timely manner. Applying patches can be as much of a political and human resources process as a technical process. However, this is only considering tracking missing patches on known systems.
For example, the unmanaged Windows 2008 server that got added to the network last night will never be patched. Similarly, the software that was installed without a change-control window may not be managed by your patch management system. And of course, the back door installed by the hacker or malware on your network won’t be stopped by your anti-virus or IDS.
Only with real-time, in-depth auditing can assets on a network be promptly updated or if they weren’t known about, brought into the managed list of IT assets.
Tenable’s Nessus scanner and Passive Vulnerability Scanner (PVS) can be used to alert on new hosts, new ports, new applications and much more. Tenable also has many customers who leverage SecurityCenter dashboards, reports and dynamically discovered assets to track open ports, change and new systems.
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
How do you know you are getting better?
If your organization has a 30 day patch window and you are trying to get them to move to a 20 day window, how can you tell if you are improving? Smaller patching windows may not even be feasible, especially if patching could cause more problems than the potential exploits. Other mitigating controls can be implemented to reduce the risk and improve your security posture. If you scanned every 30 days, every 20 days or even every 10 days, you will only have a few data points to chart progress.
For high-fidelity tracking, ideally you will measure a vulnerability on the day it was patched or otherwise mitigated. Otherwise, from your vulnerability scanner’s perspective, it can only tell you what was found the last time it was run. Slow scanning equates to slow comprehension of actual risk.
More importantly, if you are scanning infrequently, you won’t have any visibility into what “almost” was or if your IT teams got close. For example, consider a company that has two IT teams and a 30 day patch window. Team one patches continuously through their 30 day window and there is gradual improvement across the network. Team two miraculously deploys all patches on day 29. Both teams would scan the same on day 30, but they’ve had different historical risk profiles and an ability to patch – as well as a different security posture in the interval. Asking each team to patch “faster” would also be a very different conversation since they have different attitudes and potentially different technology to perform patching.
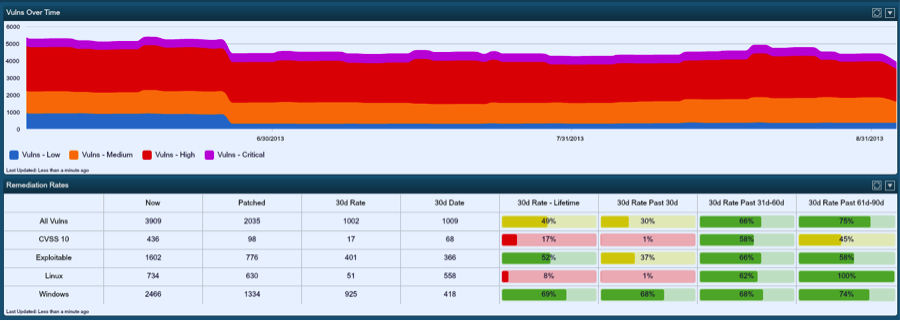
Tenable has shipped a wide variety of tools to help organizations track improvement in their security posture. For example, the SecurityCenter dashboard shown above not only shows the trend over time (and hopefully a reduction in vulnerabilities), but it also tracks the patch rates for technologies such as Windows and Linux, as well as security metrics such as old vulnerabilities or exploitable vulnerabilities. Many SecurityCenter users have leveraged this type of dashboard to show patch rates by specific geographies, political groups and even patch management systems.
Are you patching the right thing?
Another way to look at the patching problem is that there is a limitation in resources. Often, patching the Windows operating system, browser and technologies such as Java or Adobe may be performed with a certain patch management tool, but are accomplished with different confidence levels and success rates. This causes an IT team to not blindly push every patch they get out as soon as they get it. They need to monitor the effects of the patch and roll back if needed.
So if your IT team was remediating ONE thing and ONE thing only today, what should it be? I’ve seen lots of issues in this area over the past eleven years as Tenable’s CEO. Could you be making that decision based on a scan from 30 days ago that said Oracle had a medium Java issue and missing the fact that Microsoft just released an out of band security patch for Internet Explorer? What if a team silently pushed out an older and even more vulnerable version of .Net or Java for backward compatibility for one of your corporate applications? What if you assume that users running Chrome or Firefox automatically update and they don’t?
Tenable has a variety of tools that allow for dynamic prioritization of patches that have the most impact to your network. Here is an example link to one of our SecurityCenter report templates that addresses this for missing Windows patches. SecurityCenter automatically prioritizes missing remediation in general, by exploitability, by age of vulnerability, the severity of the missing patch and many other items.
Add Clarity to Incident Response
If you have ever responded to an intrusion or an incident, you will most likely ask for information about the system that was compromised. What was it? What software did it have? What configurations and vulnerabilities did it have? This data is crucial in determining how an intruder broke in and is also vital in determining if your organization has other assets which could have targeted.
Previously, I used an example where multiple groups all come up clean on a monthly vulnerability scan. Since the scan only happens once a month we don’t know if these groups are patching their security issues the day before the scan, if they’ve been vulnerable for the entire month or something in between. This information is crucial to know what risk these systems were exposed to.
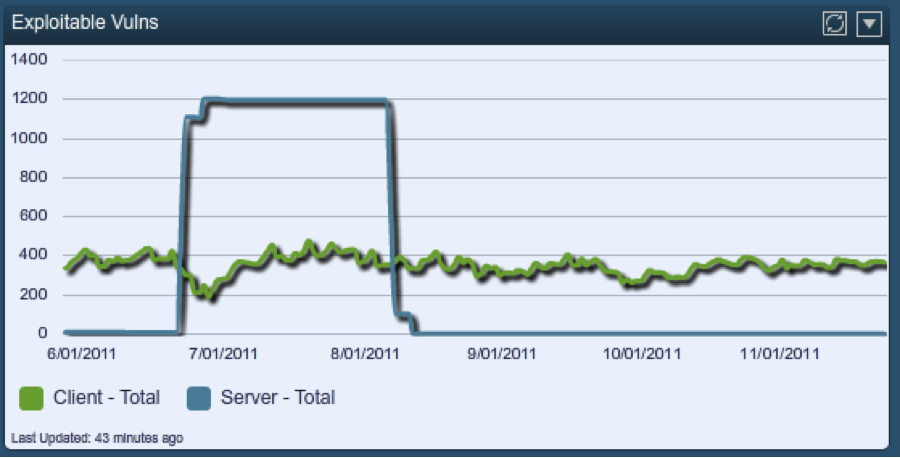
Tenable’s real time tracking of vulnerabilities allows for very detailed detection of risk. For example, in the screen shot blow, daily vulnerability audits were used to graph out a server’s “exploitable” Internet facing services.
The blue line shows that for the entire month of July, this server was known to be “exploitable” from the Internet with tools like Core, Canvas or MetaSploit against services such as Apache. If only monthly scans were used, this type of knowledge would not be available to your incident response team.
Conclusion
Tenable offers many different technical solutions to the political problem of measuring vulnerabilities as fast as possible. Our solutions leverage scanning, integration with patch management systems, sniffing network traffic and log analysis to allow for rapid detection of vulnerabilities on all sizes of networks. The solution is called SecurityCenter Continuous View. To learn more, please feel free to contact our sales team to set up a demo.
- Passive Network Monitoring
- Vulnerability Scanning