What Is the Lifespan of a Vulnerability?
In the second of our three-part series on persistent vulnerabilities, Tenable Research examines survival data to assess how effectively traditional remediation tactics are combating the attacker's advantage.
Last week, we unveiled a new report from Tenable Research which explores the issue of common persistent vulnerabilities. As security teams wrestle with the vulnerability overload problem, this research seeks answers to the following questions:
- Do the characteristics of vulnerabilities affect their persistence? Or, is persistence merely related to the remediation process and its pace?
- Are there vulnerability remediation differences between organizations? And, are there differences within each organization?
Part 1 of our blog series detailed the motivation and methodology behind this research, as well as key findings around prioritization. In part 2, we analyze the data trends underlying vulnerability lifespans and the factors that determine the rates and effectiveness of traditional remediation efforts.
Most vulnerabilities are remediated within a year – the rest live on
We can examine persistence through multiple lenses. Let’s start by considering the overall lifespan of a vulnerability in an environment, from the first assessment to the last remediation.
Figure 1 tracks change over time for all vulnerabilities that have been remediated at least once within an environment. We did not include instances of vulnerabilities that were never remediated, as these open vulnerabilities can skew the overall results. This survival data is based on the lifespan of a vulnerability within a given organization, not across the global population.
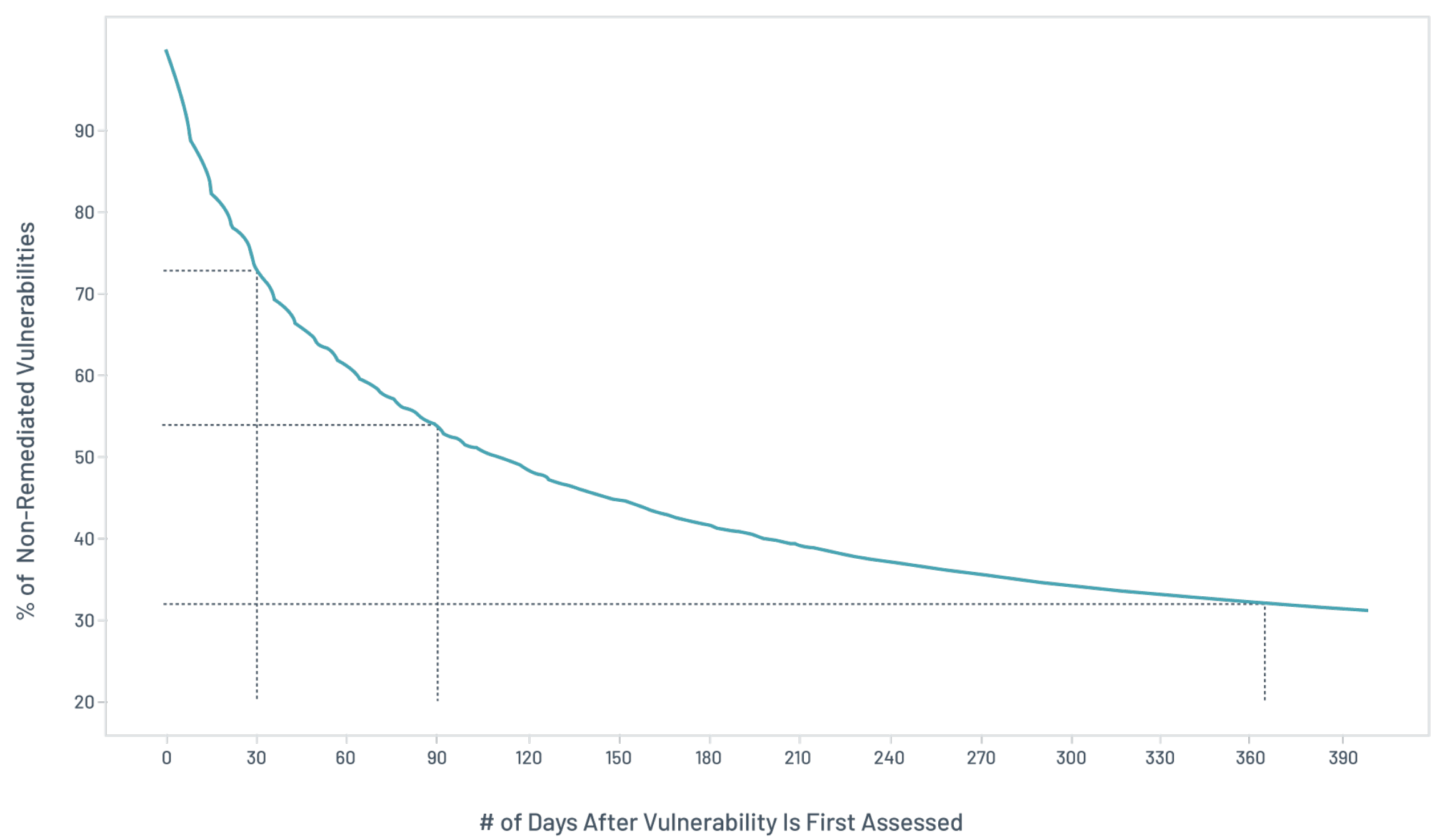
Figure 1. Vulnerability lifespan analysis – a per-organization view
We see that 73 percent of vulnerabilities are still extant within 30 days of the first assessment. After 120 days, close to 54 percent remain unremediated. Beyond that, 32 percent of those vulnerabilities still lurk after a year, and about 26 percent are never driven to zero. The vast majority of vulnerabilities over a year old are never dealt with. In fact, if a vulnerability gets past a year of its first assessment, it has less than a 20 percent chance of being remediated. The median lifespan of a vulnerability is 110 days.
As vulnerabilities age, the remediation pace slows. This may indicate a tradeoff with coverage (in favor of additional, newer vulnerabilities) or the presence of persistent vulnerabilities. The 32 percent of vulnerabilities that were not remediated after a year are still present in 90 percent of environments. This means only 10 percent of organizations have managed to address all their open vulnerabilities within a year of first assessment.
The above trend is not only related to remediation, but also a consequence of the time to assess. The median time to assess all instances of a given vulnerability across a single organization is 29 days, while the median time to remediate all those instances (in cases driven to zero) is 40 days.

Exploitable vulnerabilities are widespread in early months, despite higher risk
These timelines show there are differences within each organization that contribute to the overall remediation challenge and the large percentage of unremediated vulnerabilities over time. In a previous study, we measured the difference in days between when an exploit for a vulnerability becomes publicly available (i.e. “Time to Exploit Availability”) and when that vulnerability is first assessed within an environment. The results showed a negative median of 7.3 days, indicating the attacker’s advantage. The additional intra-organization timelines presented here further increase that advantage.
As shown in Figure 2, the lifespan trend for exploitable vulnerabilities is almost the same as the trend for all vulnerabilities. In the first few months, exploitable vulnerabilities are even slightly more persistent than the overall population:
- After 30 days, 76 percent are still unpatched (vs 73 percent of non-exploitable vulnerabilities)
- After 90 days, the delta narrows to 55 percent (vs 54 percent)
However, beyond this point, the rate drops more quickly and reaches 27 percent after a year. Roughly 18 percent of exploitable vulnerabilities are never driven to zero.
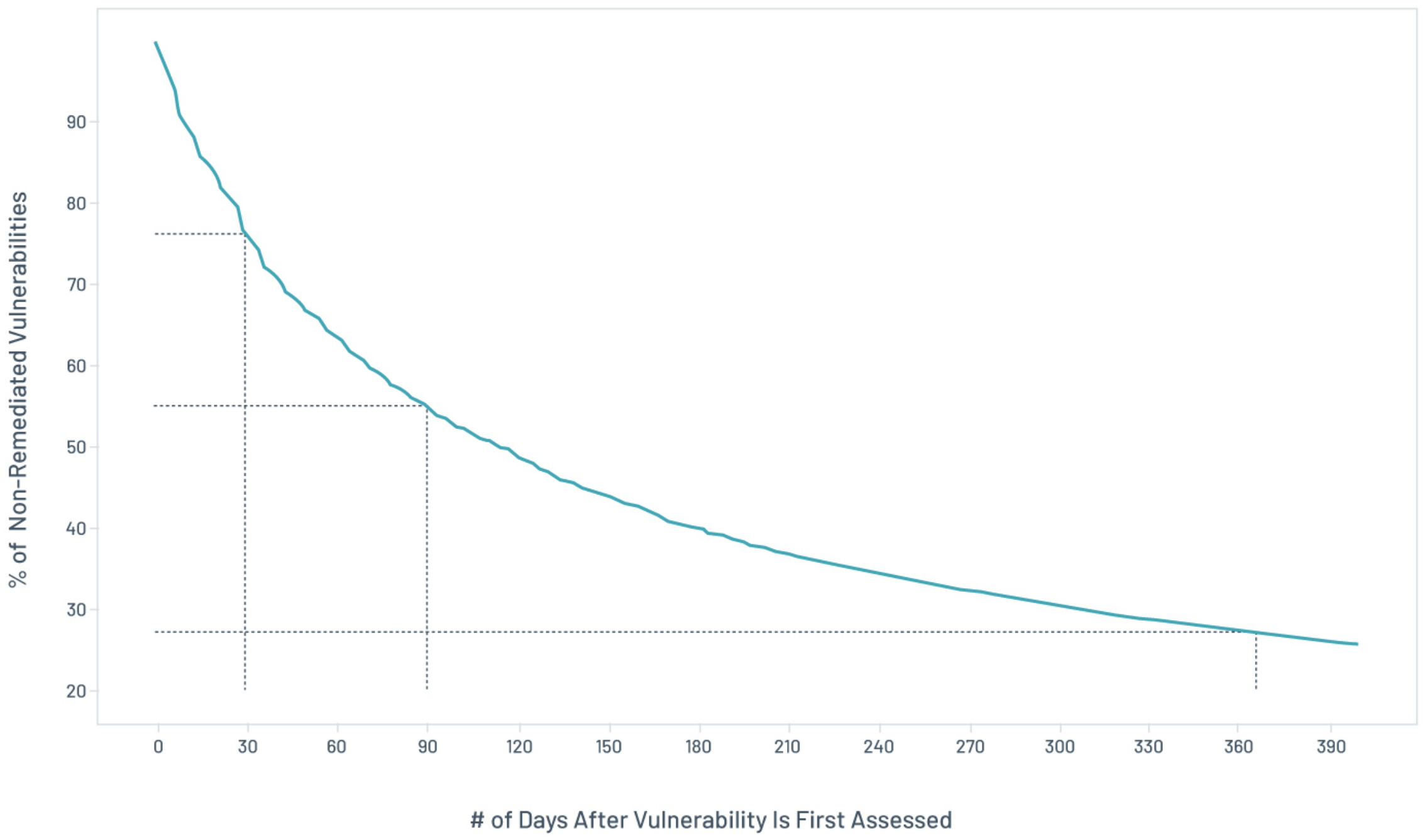
Figure 2. Exploitable vulnerability lifespan analysis – a per-organization view
This data suggests that defenders are still operating under the classic assumption that attackers can exploit any vulnerability. Under traditional remediation tactics, higher-risk threats are not resolved any faster than other vulnerabilities. Because exploit code for most exploitable vulnerabilities is used within a few months of publication, additional threat intelligence and risk-based prioritization is necessary to correct this trend.
On the other hand, we’ve also looked at the difference between vulnerabilities unremediated for over a year and those remediated within the year. Among the roughly 400 vulnerabilities that haven’t been remediated at least once within the year, only a dozen are exploitable (see Figure 3). These persistent, high-risk vulnerabilities have a very low prevalence, found in at most four organizations (out of more than 2,600). These are extreme cases of localized persistence.
Figure 3 includes three classes of exploit maturity:
- Proof-of-concept (PoC): Code is available on public websites and repositories (e.g., GitHub, Exploit-DB, Packet Storm)
- Functional: Exploit is ready to use within penetration testing and red-teaming frameworks (e.g., Canvas, Metasploit, Cobalt Strike)
- High: In-the-wild exploitation has been confirmed and attributed by antivirus vendors or other leading threat detection and intelligence solutions (e.g., ReversingLabs)
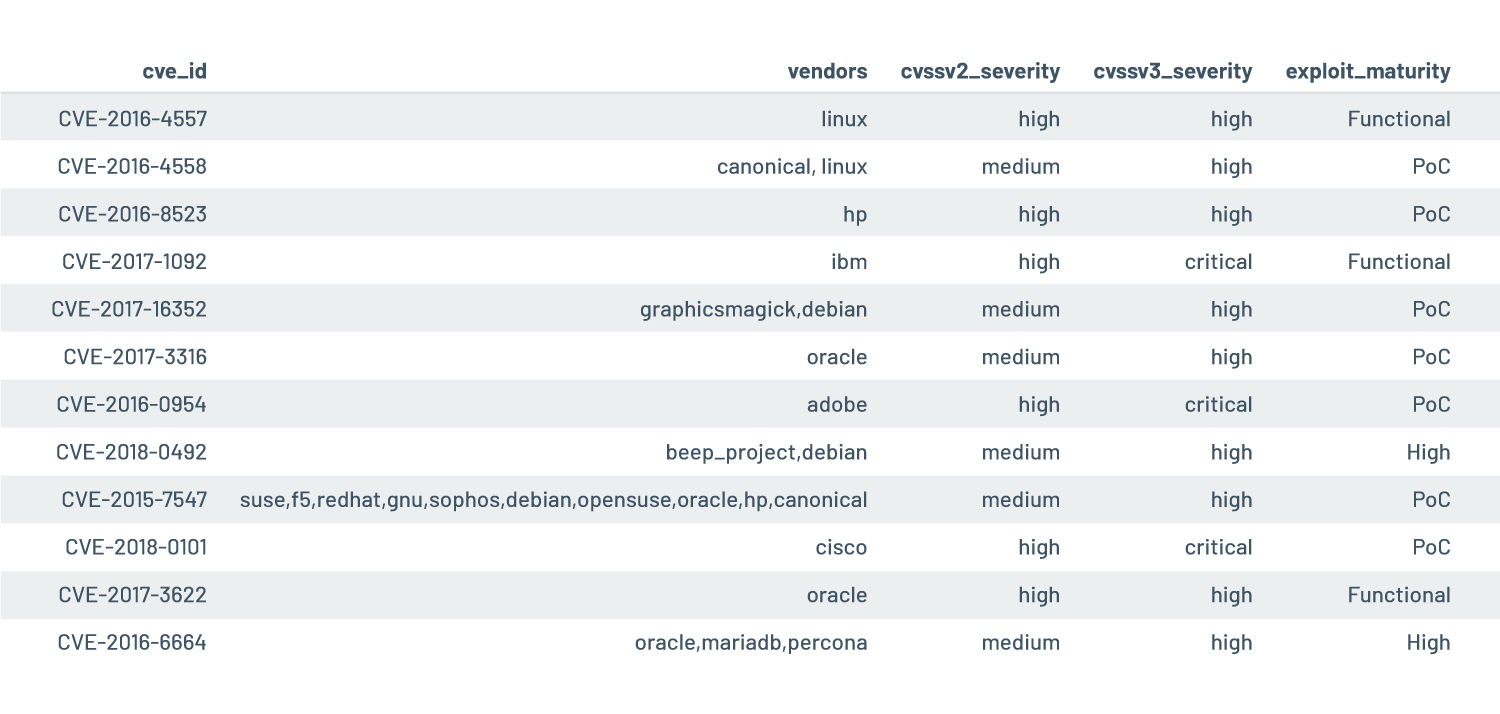
Figure 3. Exploitable vulnerabilities left unpatched for more than a year
After the one-year mark, the number of high-risk threats shrinks even further. A reverse lookup, across the entire population of organizations, into the exploitable vulnerabilities unpatched for over a year, reduces the set to only one vulnerability (CVE-2018-0492) in one organization. This confirms the localized aspect of these cases of persistence. It also shows that almost no exploitable vulnerabilities go unremediated for an extended period of time across the global population. We get a hint of an answer here to question one, suggesting that vulnerability characteristics would not play a role for these cases of localized persistence.
In the third and final part of this series, we’ll explore the persistence of exploitable vulnerabilities from a global, rather than a localized, perspective. We’ll analyze how vulnerabilities persist across all global assets, not just within a given organization. We’ll also look at the economic aspect of persistence and prevalence and ask, “To what degree must a vulnerability exist across the global user and asset population to make it a viable and attractive target for attackers?”
To learn more about our original research into common persistent vulnerabilities, you can download the full report today.
- Research Reports
- Vulnerability Management

