Understanding Tenable Plugins

Are you pluggin’ along looking for vulnerabilities? The heart of Tenable vulnerability detection comes from the individual tests called plugins – simple programs that check for specific flaws. Each plugin contains a vulnerability description, fix recommendations, and algorithms for detection. Tenable products receive new plugins nightly, which keep the tests current and relevant.
Finding plugin information
SecurityCenter® has at least four places to research plugins:
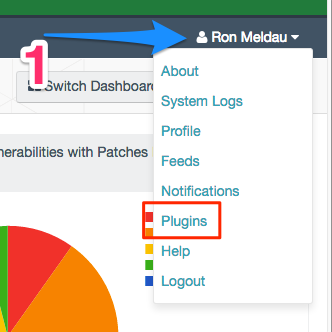
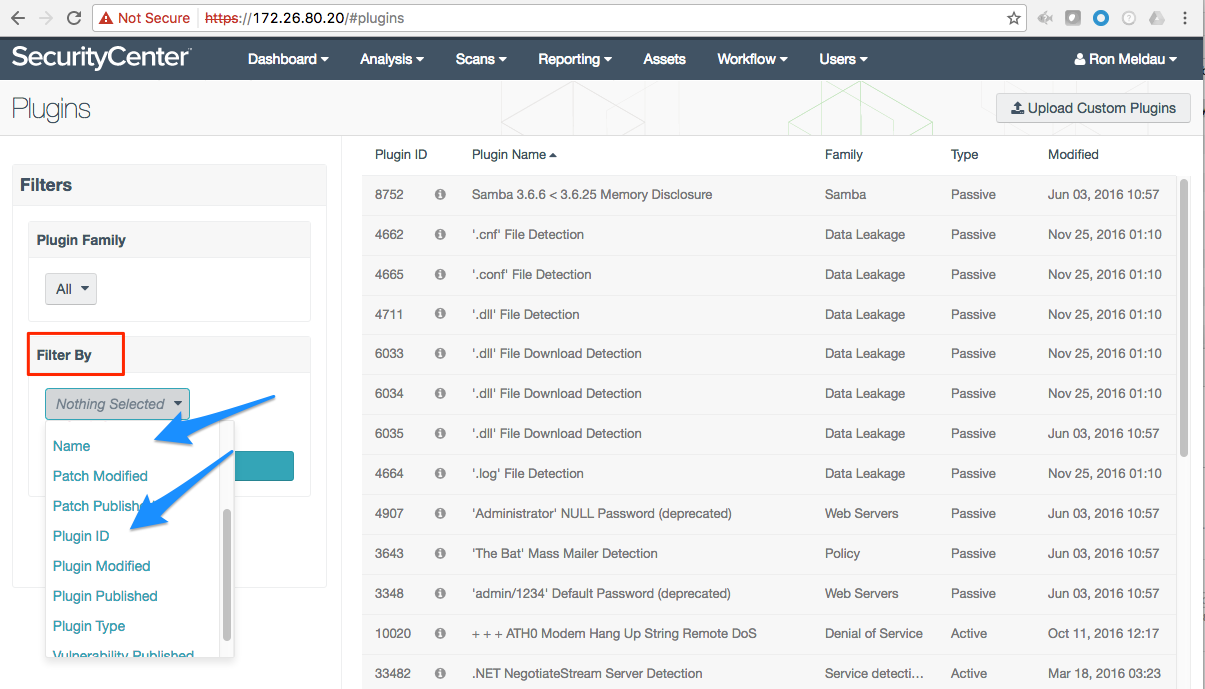
1. Click on your userid (top right) to find the Plugins. This is the quickest source while working on SecurityCenter. You can also use a URL such as: https://<SecurityCenterhostname>/#plugins
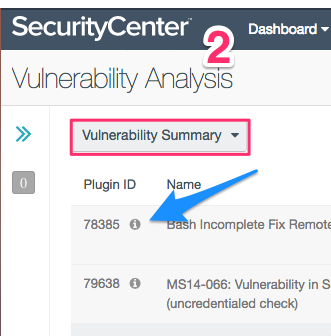
2. On the analysis screens and plugin screens, click the i icon next to the Plugin ID This is the most informative source.
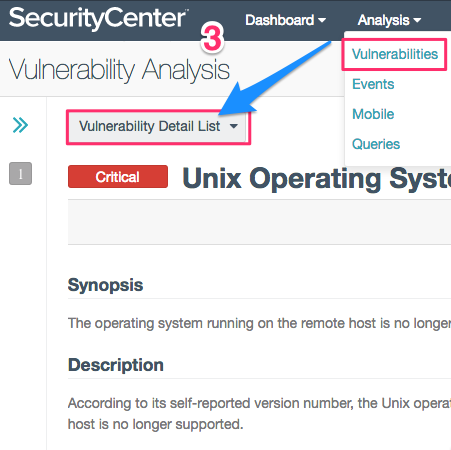
3. Click on Analysis / Vulnerabilities and choose the Vulnerability Detail List (VDL) tool to find many explanations related to individual plugins.
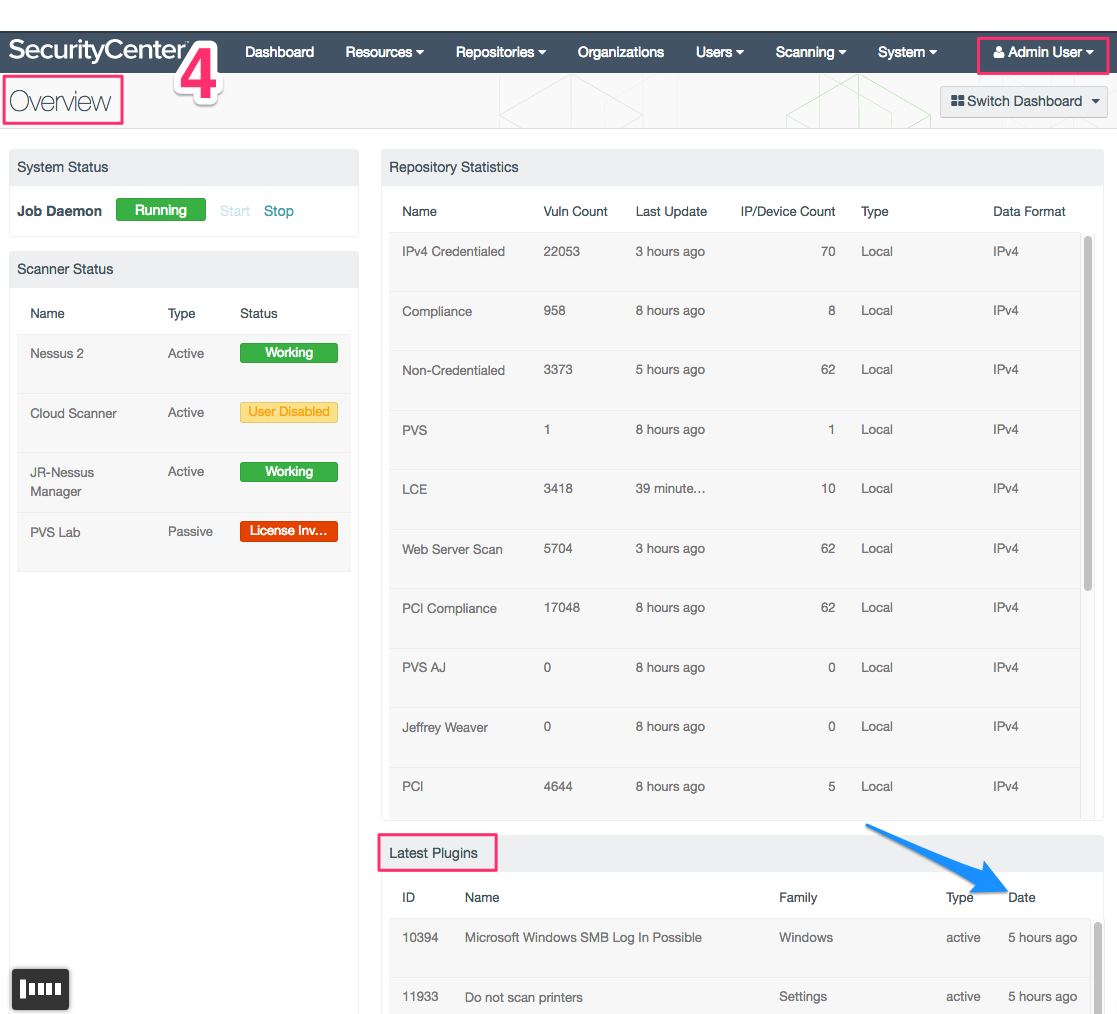
4. Log in as administrator. The initial Overview dashboard (bottom right) lists the plugins currently loaded in SecurityCenter.
You can also find plugins in other Tenable products.
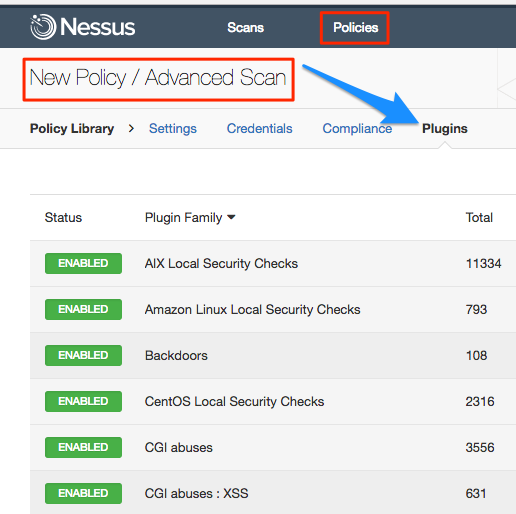
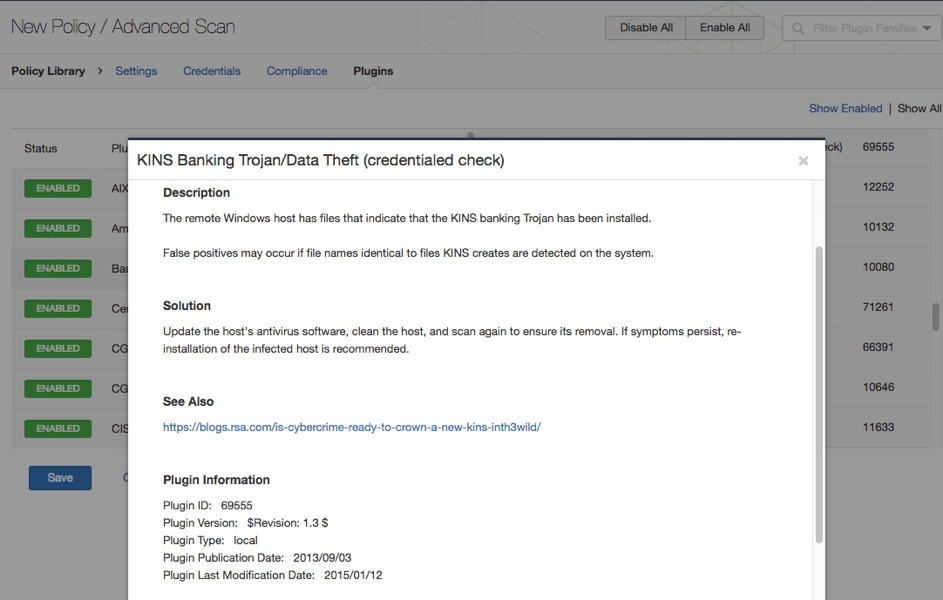
Nessus® takes a few clicks to drill down to plugins. Go to Policies / New Policy / Advanced Scan /Plugins. Then select a family on the left and a plugin on the right:
You can also see Nessus plugin information in scan results and by drilling down on individual plugin results. This provides similar information as VDL in SecurityCenter.
Tenable.io™ provides very similar information as Nessus, both in content and location (see Tenable.io Vulnerability Management for information about this new application).
You can use three places on the Internet to research plugins:
- Plugins: This site is very useful. The Tenable Support Portal also links to the Plugins.
- Tenable Community: provides technical discussions on individual plugins. Use this site to see how a plugin is used by others.
- Google: Of course, an organic search for a Nessus Plugin Name or ID is often the easiest to remember.
Explanation of plugin sources
Each plugin source has its advantages and peculiarities. They vary in the information provided. Here are the nine sources, comparing their advantages and unique details.
Plugin
This source provides many fields to search on. I use Plugin Name or Plugin ID most often.
This view has several unique characteristics. First, it shows the plugins currently in SecurityCenter:
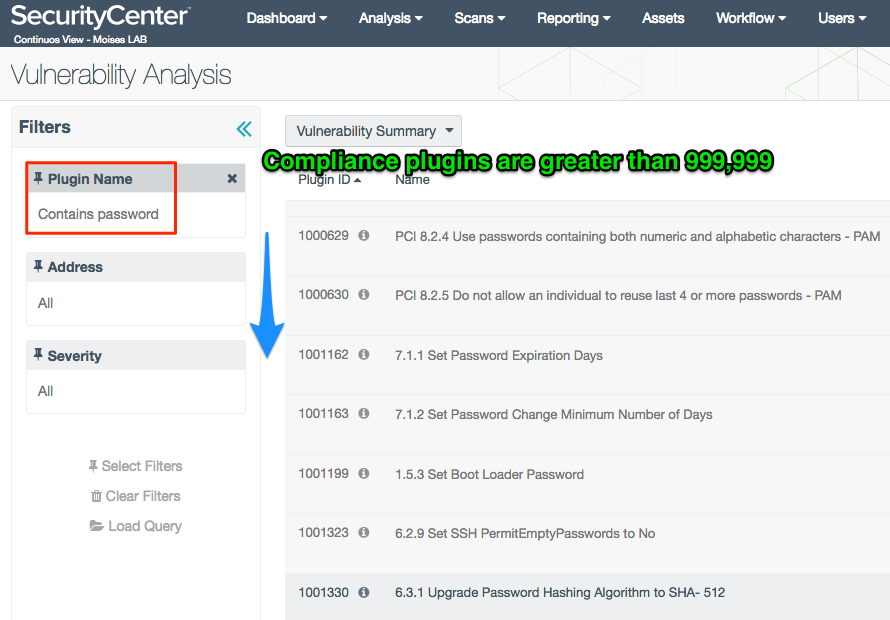
Second, this source enables you to search against the audit files that have been activated in your SecurityCenter installation. For example, you can see the compliance password tests:
i icon
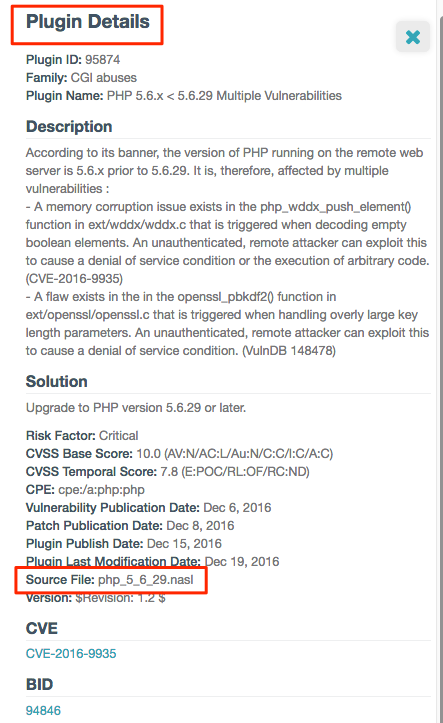
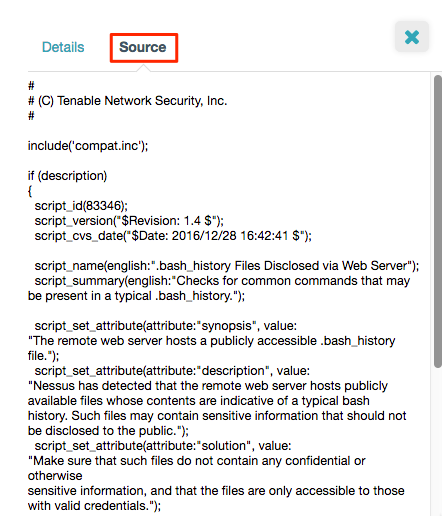
Clicking the small i icon results in voluminous information. If you carefully search through the Details tab’s Solution section, you can find the plugin’s source filename:
A second Source tab (top right) displays the plugin’s actual scripting in Tenable’s proprietary Nessus Attack Script Language (NASL):
Not all plugins are provided in NASL. Others plugins are compiled to protect confidential techniques.
VDL
You can find a gold mine of information in the VDL analysis tool. This is usually the best resource for researching plugin results.
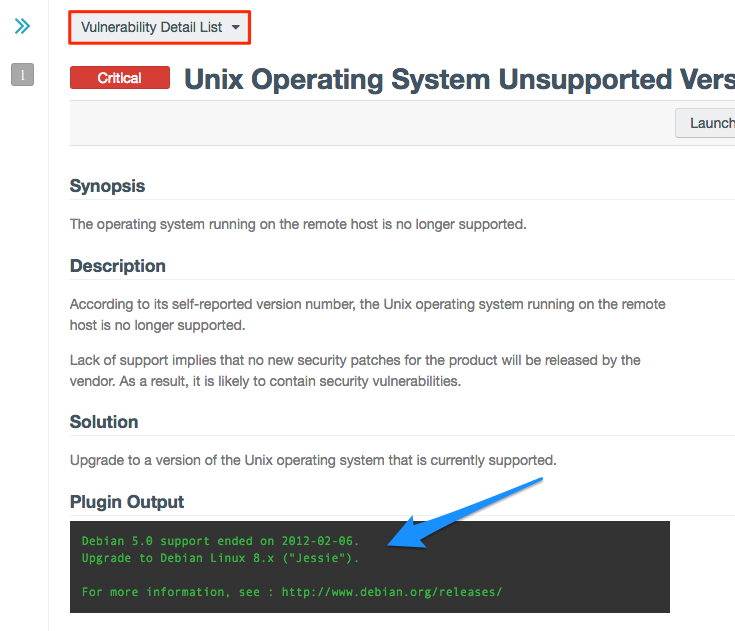
- The Plugin output field is one of the most valuable fields, because you can see the actual response from the target during testing. It stands out with green-on-black coloring:
- The VDL output is the best for assessing risk and how the CVSS score was tallied. It includes the vector, the version, and more.
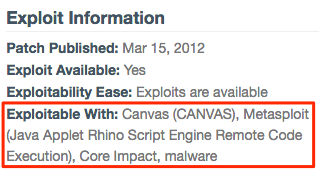
- If a publicly-known exploit is available, the VDL will provide details. In this example, the specific Metasploit module is specified:
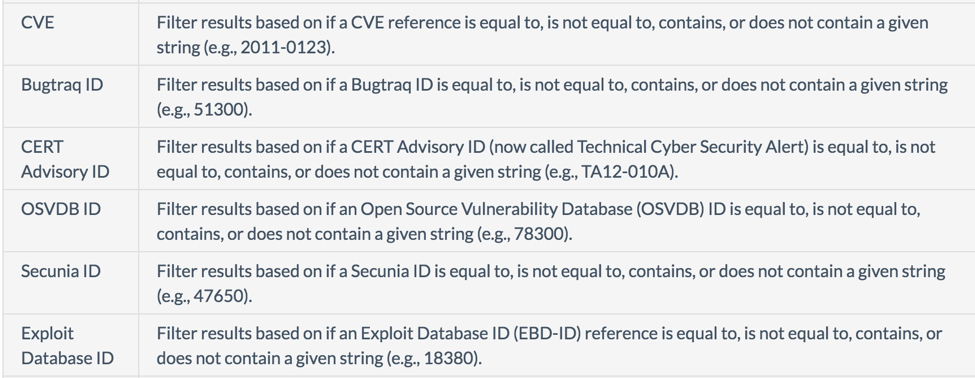
- VDL includes ties to many industry vulnerability sources like BID, IAVM, CVE, and CERT announcements:
- VDL also references frameworks like 800-53, CSF, PCI, ISO 27000, Critical Security Controls (formerly SANS top 20) and several others. Tenable provides audit files, which in the individual stanzas correlate the framework modules by tags in the Reference field. The tags enable framework dashboards, reports, and Assurance Report Cards® to automatically populate with appropriate scan results related to the framework. A listing of related audit files can be found by posting a specific question on the Tenable Community.
- The Host field includes items such as the date that the vulnerability was first seen. It also gathers asset identity details like DNS, NetBIOS, and MAC address.
Admin overview dashboard
After logging in as admin, I like to sort by modified date to see when plugins arrived. The date for the newest plugin downloads should be less than 24 hours (except for an offline SecurityCenter). I also like to see what issues the recent plugins address.
Nessus
Finding plugin information takes several steps. Nessus also provides many fields about a plugin.
To identify risk severity, Nessus shows both CVSS versions two and three in the detailed view.
Tenable.io
Similar to Nessus.
www.tenable.com/plugins/
This has been my favorite interface to work with for quick lookups. It also lists plugins by families. The Plugins portal includes several pages:
- Helpful screens on newest plugins and options on obtaining an activation code for plugin updates.
- View all plugins provides the latest count of plugins at the top. The page is organized by research plugin families.
- Search: I often start my research here. I usually search by Plugin Name and Plugin ID.
Example: A customer asked if Tenable had any tests for nginx. I typed in nginx, searched with Plugin Name, and was surprised by how many plugins were listed.
TIP: Though the page suggests using double quotes for an exact search, I have not had success with that search technique.
Be aware that this page is showing Nessus plugins only. To see the PVS™ plugins, go to bottom left of the page, click Product Resources, and then click PVS Plugins.
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
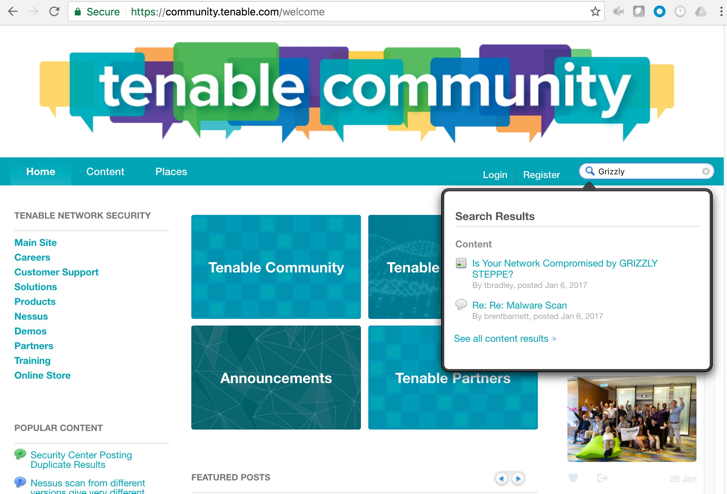
Tenable Community
This portal provides technical discussions between customers and Tenable support staff. I often search it to see how others use a particular plugin.
This site is especially helpful for late-breaking vulnerabilities. Here is an example with the recent GRIZZLY STEPPE exploit:
Even if you forget the first eight sources, you will probably remember to use Google (or another search tool). It often points to information from sources 7 and 8.
Common questions and tips
Tip #1: What is the best plugin?
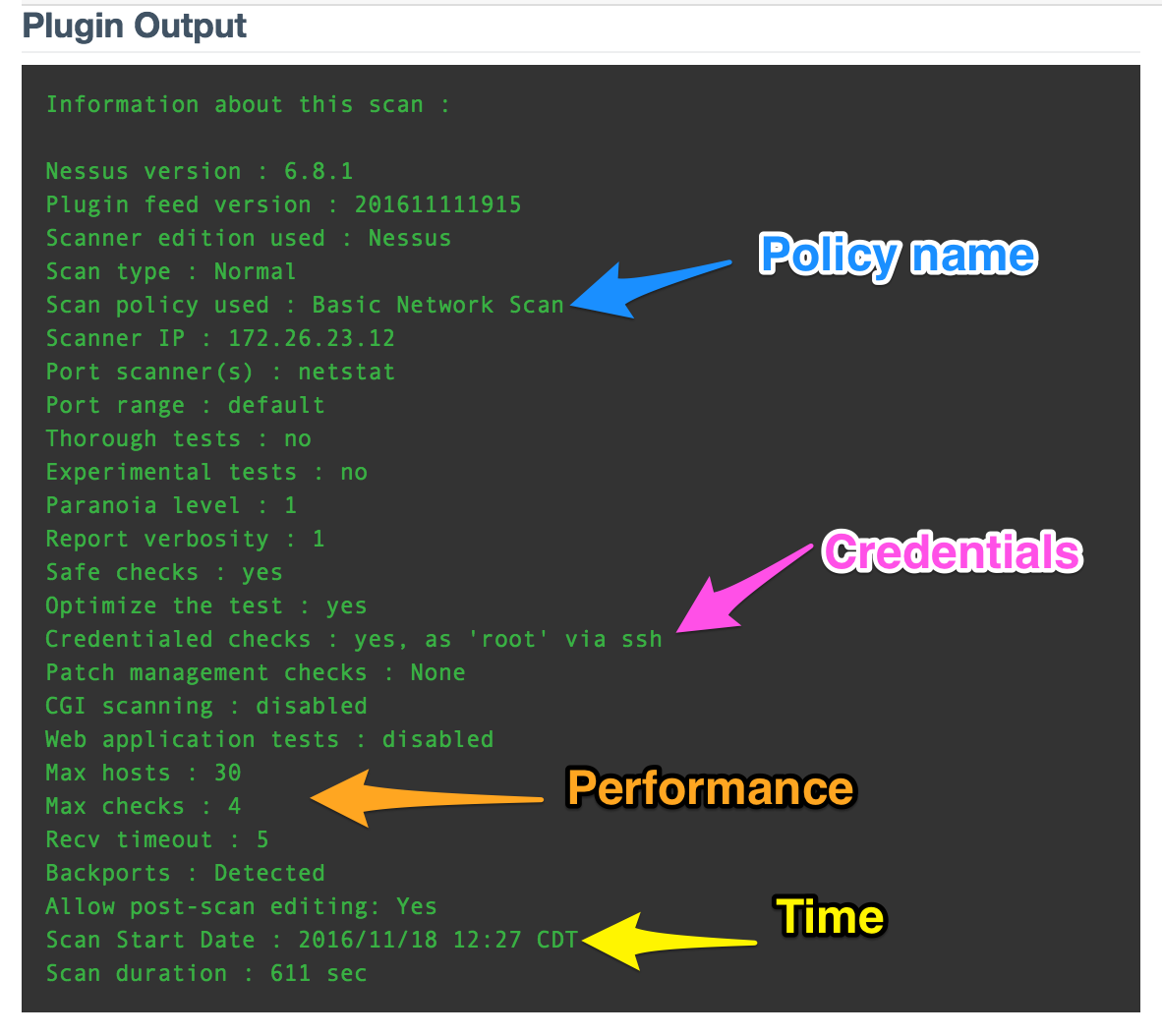
I nominate Nessus Scan Information, #19506. I chose this plugin even though it does not do any vulnerability testing. It gathers many scan forensics like how long the scan took, if the credentials worked, what scanner was used, and more.
Details include:
- Policy name (both hash and field)
- Scan options
- Performance settings
- When started and how long scan ran
- Type of Nessus scan (agent or sensor)
- Credentialed scan successful or not
- Credentials used
This plugin is often used as part of a daily discover scan to identify a new host on the network. See my blog about Favorite SecurityCenter Asset Lists for details.
What is your favorite plugin? Let us know at the Tenable Community. Also feel free to request plugins you would find helpful that we currently do not provide.
Tip #2: Can customers code plugins?
Yes. Some sage advice comes from Ron Gula, Tenable co-founder, in a Tenable Community posting:
Tenable does not officially support custom NASLs as part of our support program but if you look in the API section you will see plenty of responses from Tenable staff answering questions about NASLs in general.
Most of the time, what people need to do with a NASL is actually already covered by another NASL or covered more easily by writing an .audit policy.
You can easily add tests to an audit file with PowerShell commands for Windows targets, or with a Linux command or script.
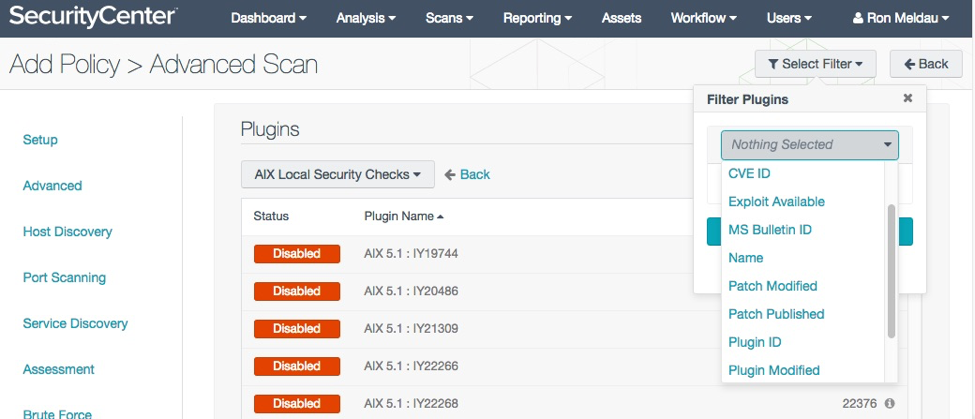
Tip #3: How do I set up a plugin-specific scan?
Identify the plugin IDs and their family that you want to use in the policy. Scan policies that are crafted with only individual plugins do not change their contents after nightly updates.
The Nessus User’s Guide provides excellent directions on setting up the scan.
SecurityCenter provides a helpful search filter for locating the individual plugins to build a new scan policy:
Tip #4: What dates can I find on plugins?
Plugins have four different dates: vulnerability release, patch release, initial plugin release, and latest date for plugin modifications. You can find two additional dates in the plugin results: when the vulnerability was originally discovered on a particular system and when the vulnerability was last observed. The periodicity of the last two dates depends upon the frequency of scans.
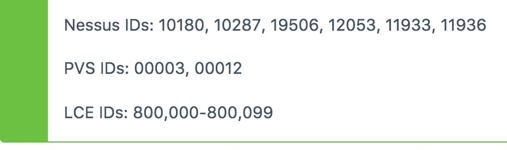
Tip #5: Which plugins do not count against the IP license?
The answer is in the SecurityCenter User’s Guide, but know that this list does change:
Summary
Plugins are invaluable tests that Tenable provides for tracking down vulnerabilities. You can find detailed plugin information within the products or on the internet. While Tenable provides lots of good information, sharing tips with other users is often quite helpful. Please share your plugin tips or questions in the Tenable Community!
- LCE
- Nessus
- Nessus Network Monitor
- Plugins
- SecurityCenter