Favorite SecurityCenter Asset Lists

Note: Tenable SecurityCenter is now Tenable.sc. To learn more about this application and its latest capabilities, visit the Tenable.sc web page.
Do you want better insights into the systems you are scanning? One of the best ways to power up a SecurityCenter® analysis can come by tailoring asset lists. The assets can provide more understanding and productivity as you craft new lists of your inventory. For example, you can craft them by vendor, location, severity of vulnerability, software installed, or many other criteria. In this blog, I will highlight some unique lists formulated by such characteristics as new hosts, age of vulnerability, processor, reboot, unsupported software, sniffing, and vendor model number.
Dynamic and combination asset lists
In this how-to blog, I will discuss the two most powerful types of asset lists: dynamic and combination. With dynamic lists, you can make rules that search through repository information in SecurityCenter. The breadth and level of detail in the repositories can be surprising; you can see that in the examples below. These lists are called dynamic because as the repositories receive new information, SecurityCenter automatically updates the list.
The inner workings of dynamic asset lists come from the fields which are derived from the information in the repositories. Examples of those fields include Severity, Plugin Id, or Days Since Discovery and others. Some of the more unique searching can be implemented with operands like contains the pattern, POSIX regex, and Perl compatible regex. (See the Equipment-Specific asset list below.)
One of the least understood parts of assets lists is that when multiple rules are included, each rule generates a separate request. This makes the results a little looser than most people think. (See the Over 30 Day Exploitable Vulnerabilities asset list below.)
You can build combination asset lists out of existing asset lists with the operands AND, OR, and NOT. This enables you to quickly merge lists (like all systems in two data centers) or pick out from two lists (like only the Windows hosts in the internet facing portion of the network-DMZ.) Entering multiple asset lists has shortcuts (see the Sniffed but not Scanned asset list below).
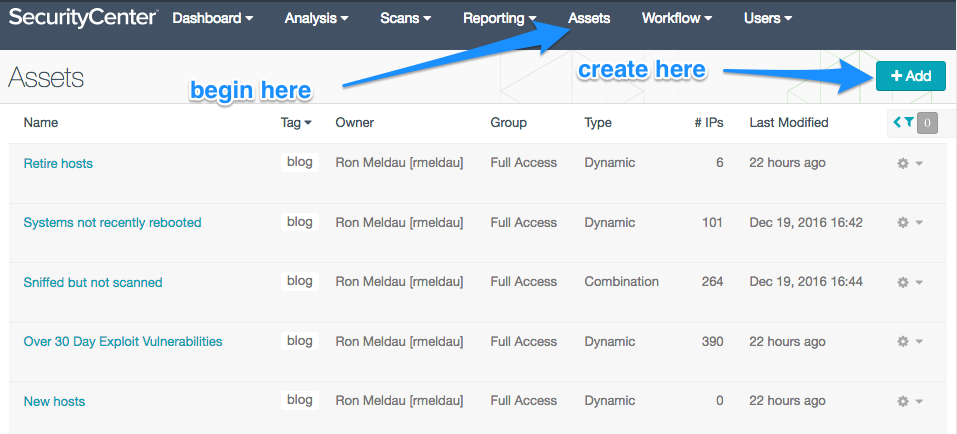
Part 1: Favorite customized asset lists
I teach classes for Tenable almost every week. Last year, while teaching at the state of Oregon, I was quite impressed with some of the asset lists that Steven Ketchum had put together. Here are a few favorites and how to set them up.
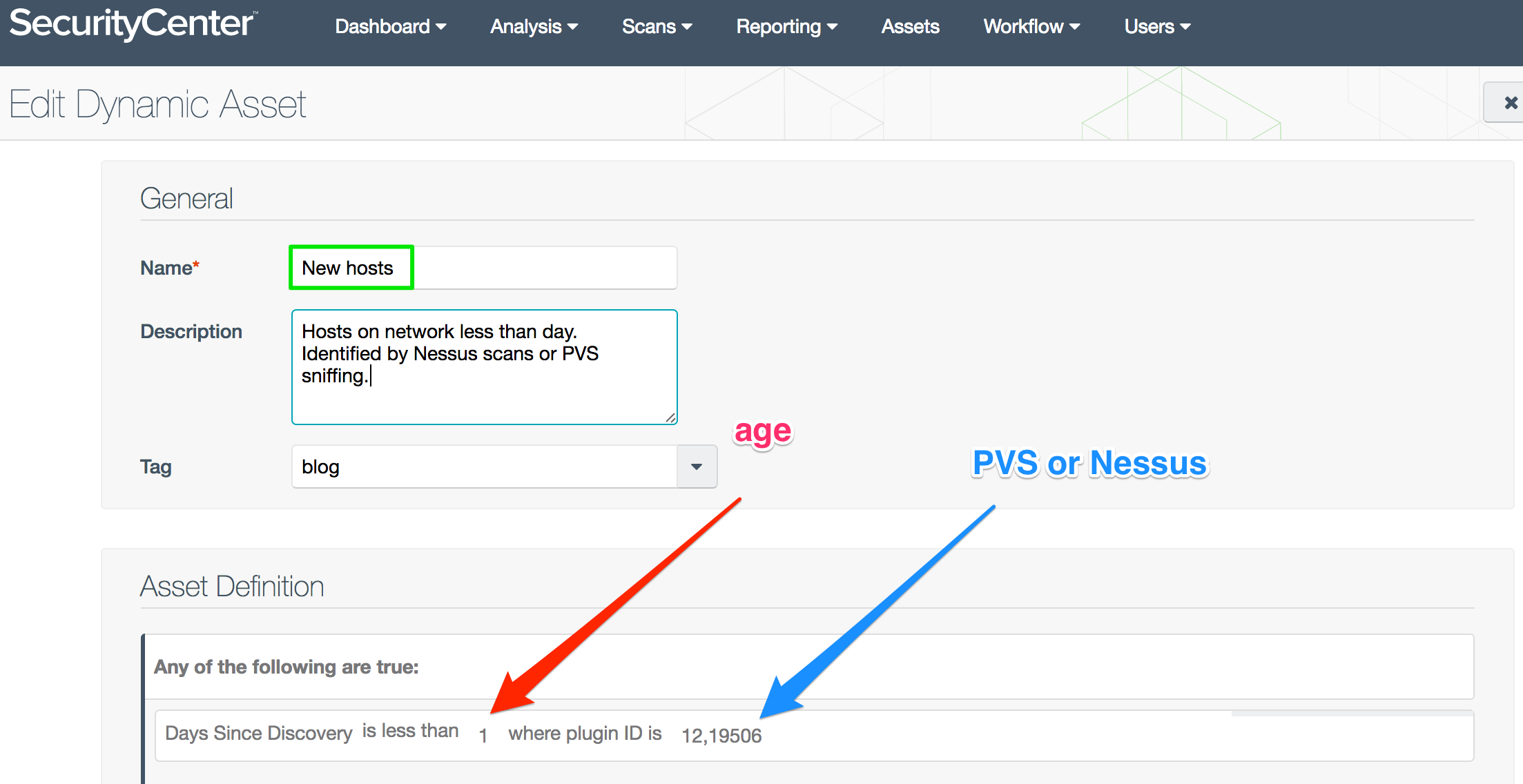
New Hosts asset list
In many enterprises—like data centers—you need to detect when new equipment shows up on the network. The New Hosts dynamic asset list uses daily, lightweight Nessus® scans or Passive Vulnerability Scanner® sensors to identify the new hosts. The list combines two plugins (Plugin ID 19506: Nessus Scan Information, and Plugin ID 12: PVS Hosts) with the Vulnerability Discovered filter.
You can also use this logic to trigger an alert which sends a report and performs a vulnerability scan of the new devices.
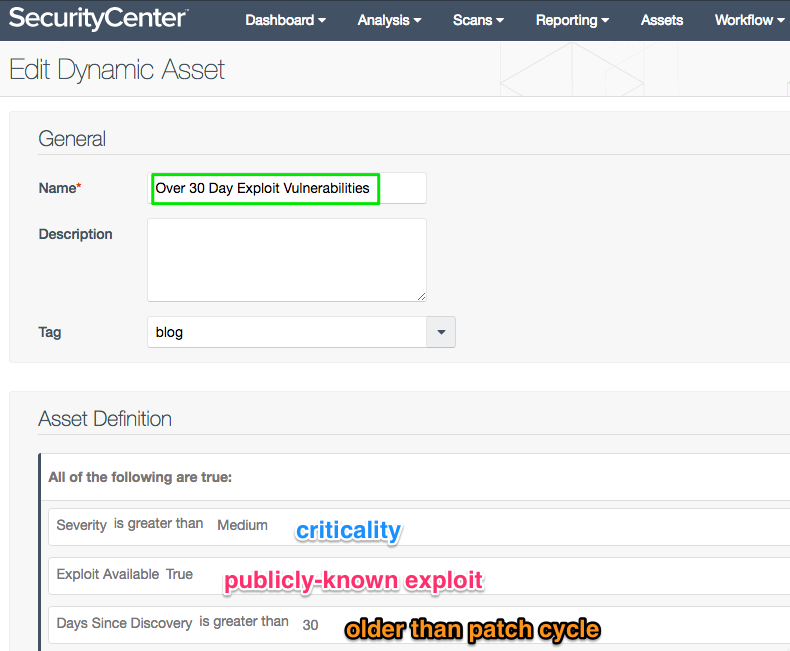
Over 30 Day Exploitable Vulnerabilities asset list
The Over 30 Day Exploitable Vulnerabilities asset list identifies hosts with the most urgent vulnerabilities that are in need of patching. The thirty day filter picks up hosts that are not fixed by the monthly patch cycle, which helps you find gaps in your patching processes. Second, the list filters to show the more urgent vulnerabilities—those of higher severity on the CVSS scale and which have publicly known exploits. This asset list needs a shorter name though; how about OTDEV?
Advanced tip: Since each rule will be a separate search, the results can be a little broader than intended. You can achieve tighter logic with a combination asset list built on these three rules.
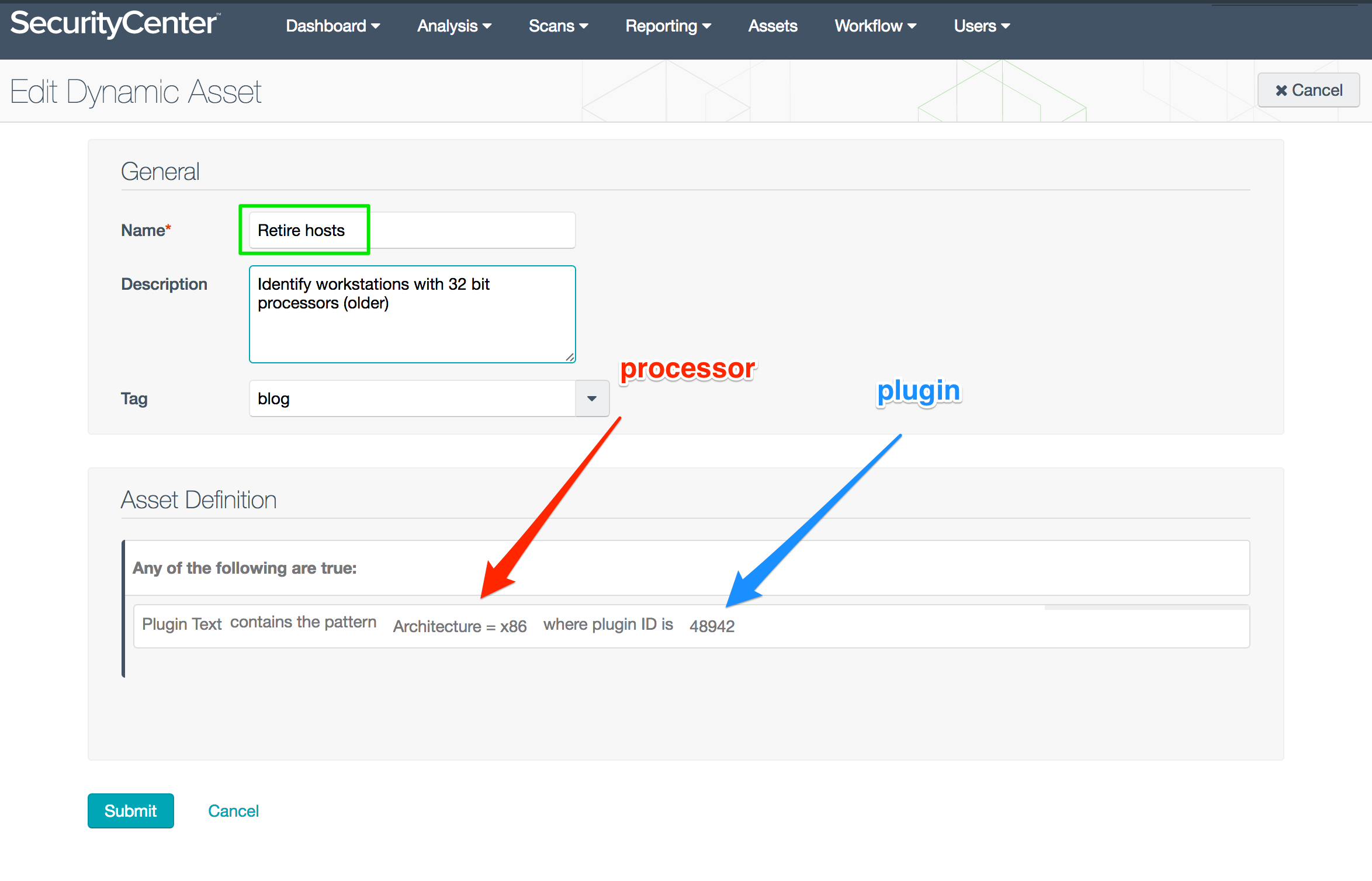
Retire Hosts asset list
With the Retire Hosts asset list, you can sort out your server and workstation inventory. For example, pick out your older servers which have x86 (32-bit) processors (as compared to 64 bit in newer systems). Then, target the older boxes in a hardware retirement program.
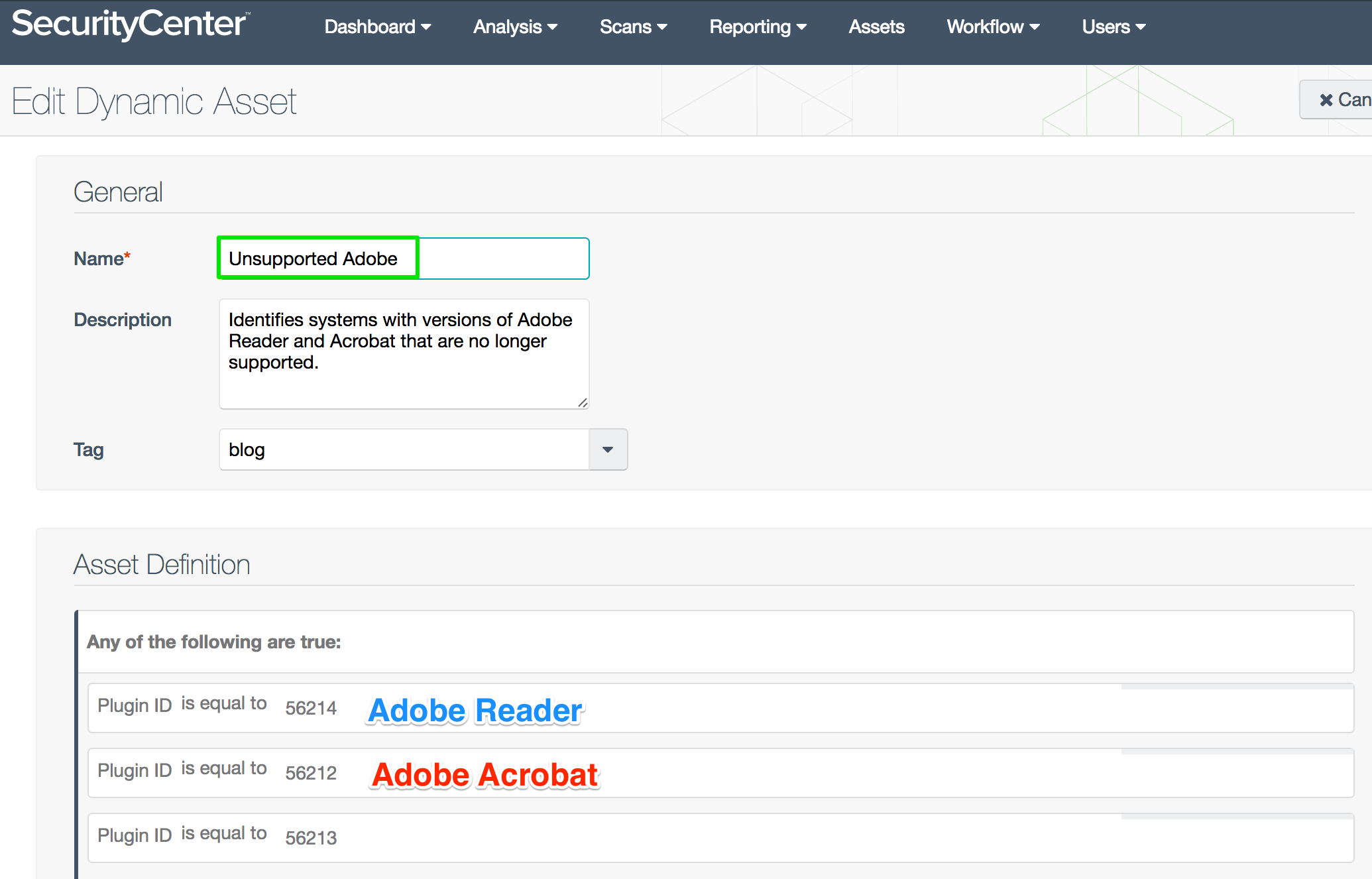
Unsupported Adobe asset list
The Unsupported Adobe asset list works with workstations and servers to identify hosts with outdated or unsupported Adobe Acrobat and Reader software. Cleaning up Adobe removes a well-known threat vector. The list also helps you provided the executive team with accurate counts for budgeting software replacement.
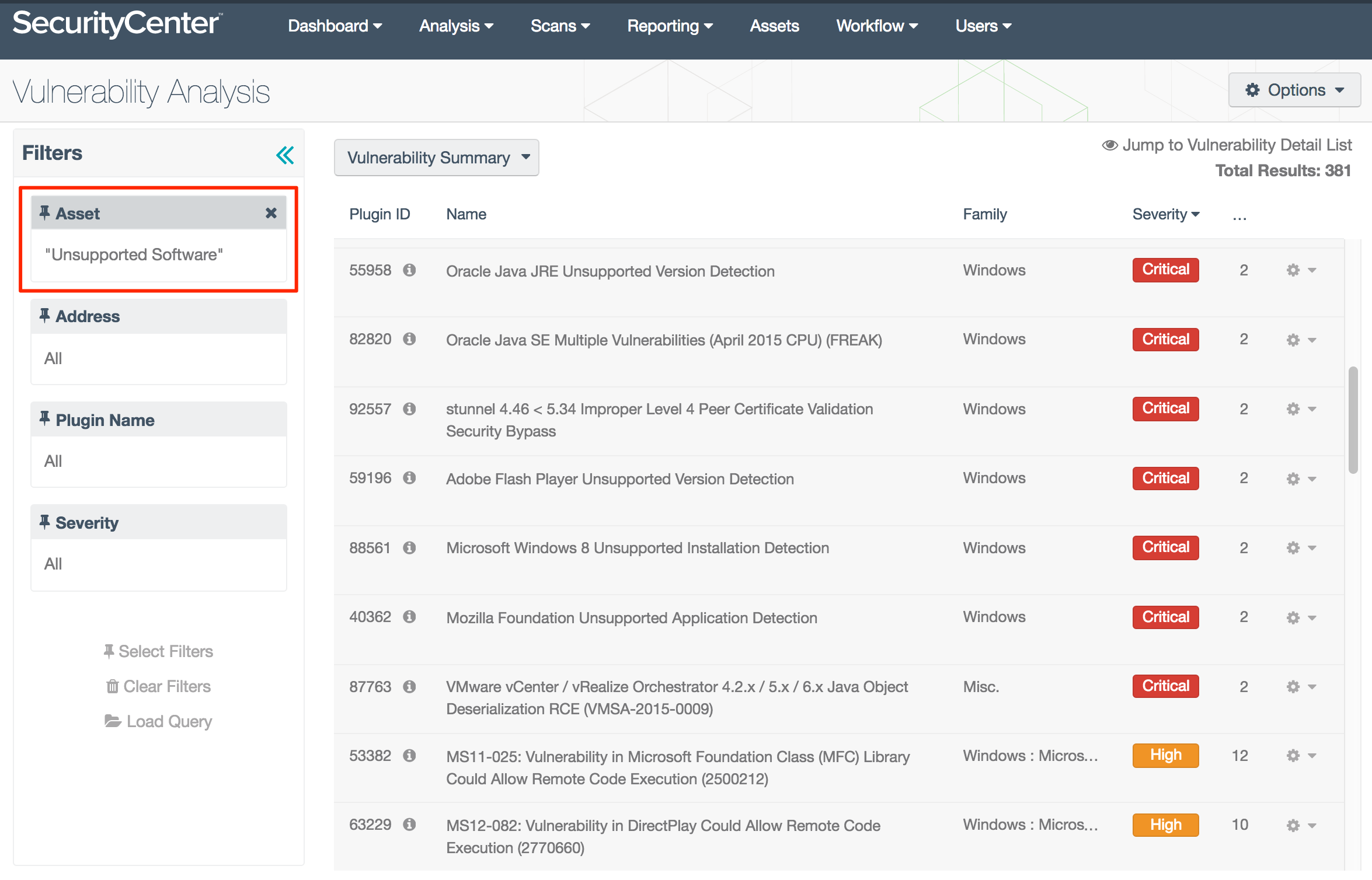
Tenable also provides an asset list template called Unsupported Software that identifies deprecated software from many vendors and not just Adobe. The following screenshot shows Microsoft, Java, VMWare, Flash and others.
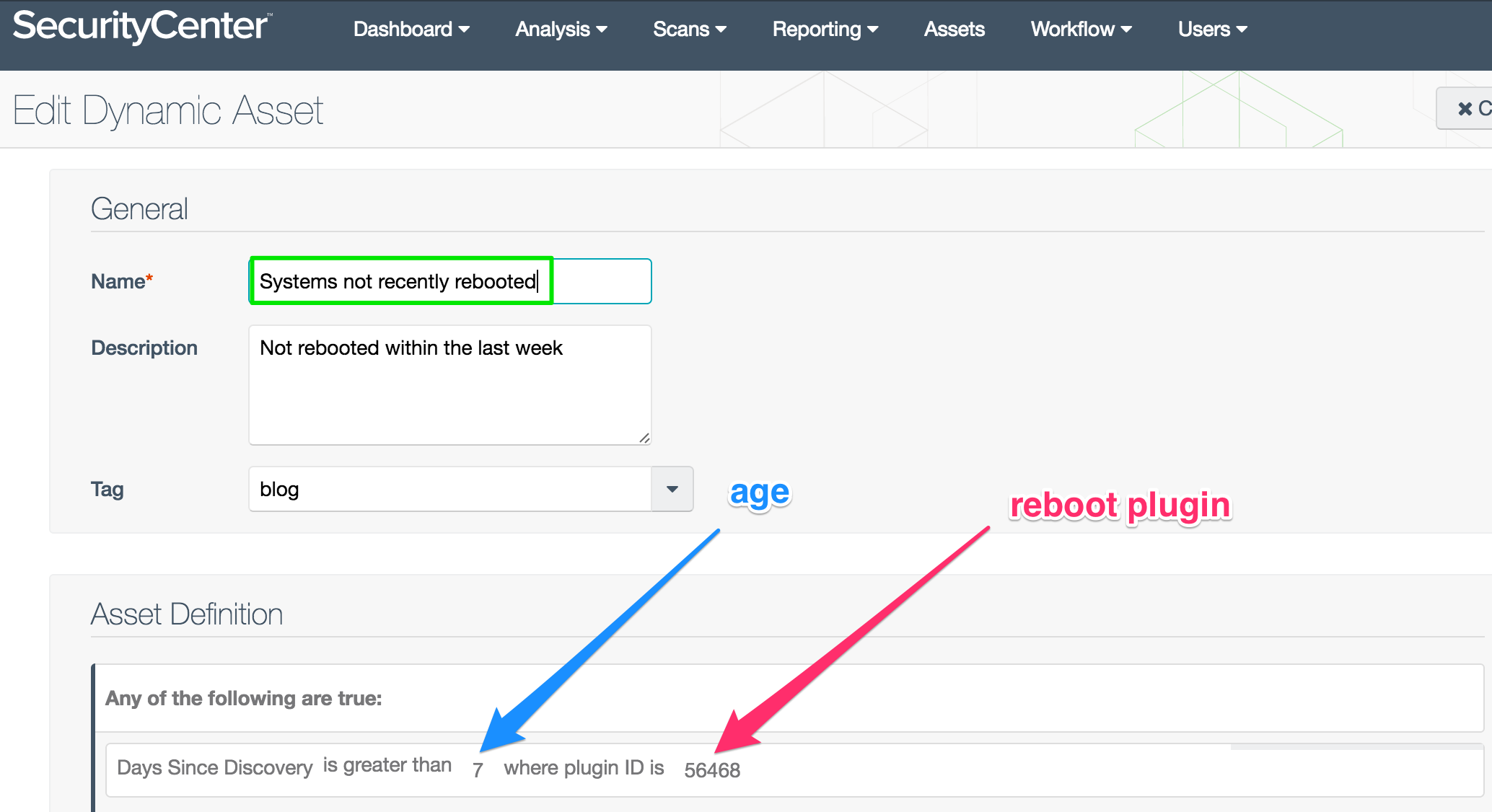
Systems Not Recently Rebooted asset list
Nessus scans can detect when a system last rebooted. One example of where this helps is with patching Windows systems. For example, some Windows patches do not take effect until the system reboots. And sometimes the reboot doesn’t occur. This asset list helps you find systems that were patched but still vulnerable.
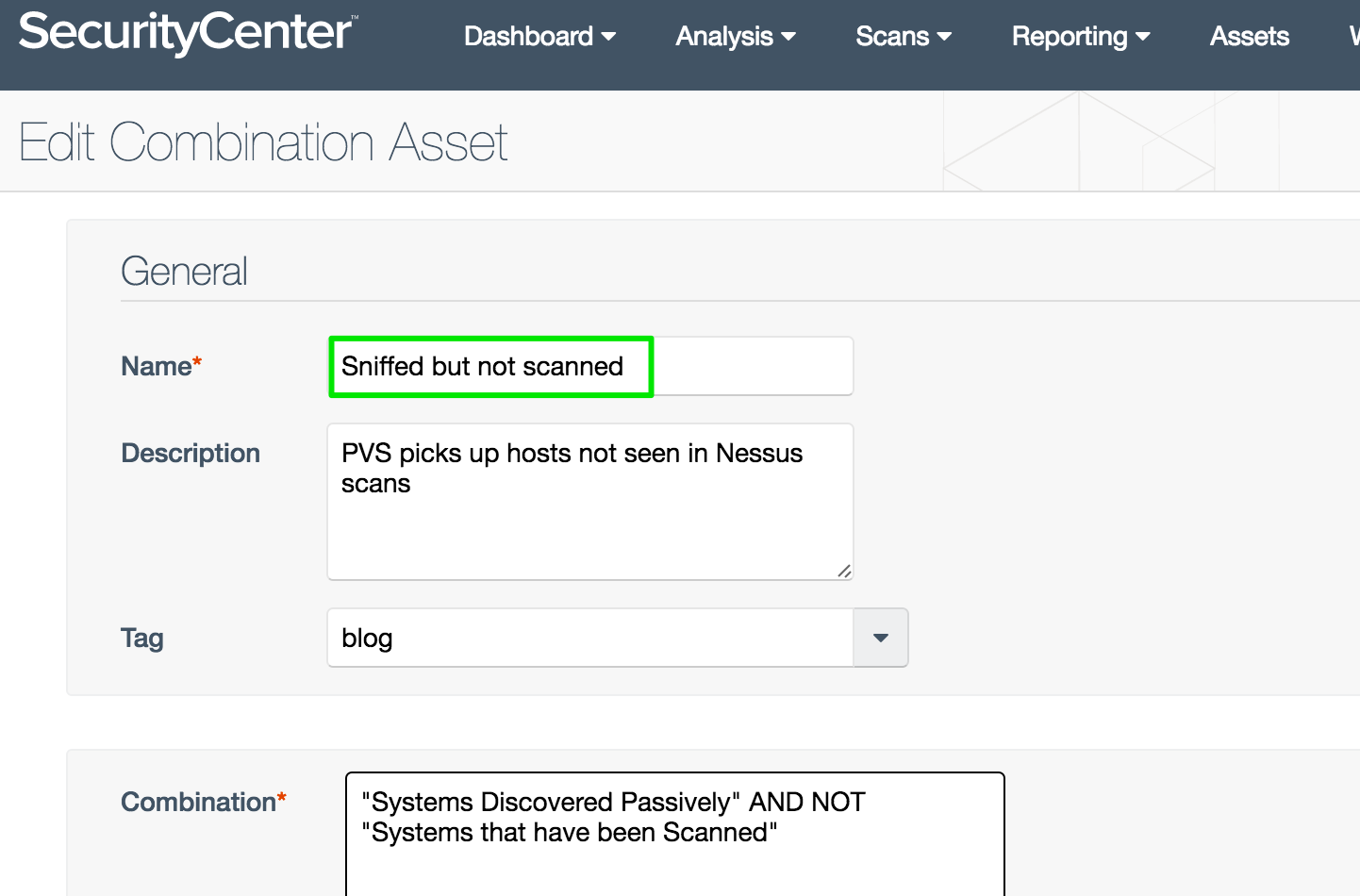
Sniffed But Not Scanned asset list
Does your Passive Vulnerability Scanner see hosts in your network that your scans are missing? The Sniffed But Not Scanned list helps verify inventory and find overlooked systems. This is a combination list built from two templates which have already been added to SecurityCenter.
Tip: The Combination field, where you enter the asset lists, is interactive. For example:
- Type the letters “pa” and SecurityCenter will filter the existing asset lists.
- Position the cursor on Systems Discovered Passively, press the Enter key and then the spacebar.
- Choose the operand AND by pressing the Enter key followed by the spacebar.
- Press the Enter key to select NOT, then tap the spacebar once.
- Type “sc”, move the highlight, and press Enter to select Systems that have been Scanned.
- Click Submit to save the new list.
With a little practice, this interface helps you build combination asset lists much faster.
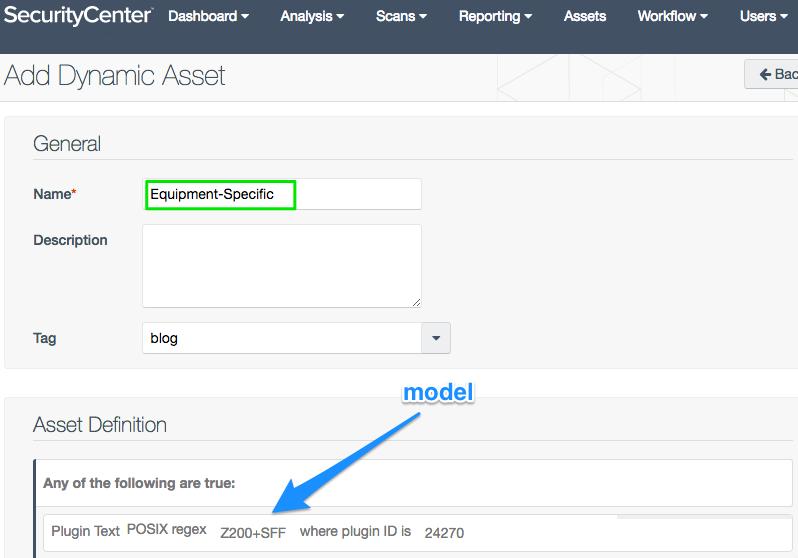
Equipment-Specific asset list
You can find specific types of equipment with Plugin ID 24270: Computer Manufacturer Information. With some regex filtering, you can search individual manufacturers and models. This plugin even reports the computer’s serial number.
Note: When possible, include an asset list to limit the scope of the search. Plugin text searches are the most expensive with respect to CPU time.
Part 2: Favorite asset lists from templates
The following asset lists are already predefined on your systems as templates. Many customers find these very helpful:
- Windows Hosts, Linux Hosts: Commonly used for setting up groups. Also helpful in adding Credential Scan dashboards (Windows, Linux, and Cisco.)
- Systems That Have Been Scanned: An essential list in working with inventory. How does this number compare with your current license count?
- Systems With Software Inventory: This list shows which hosts have been scanned with full access. How big a difference do you find between this list and the previous list (scanned hosts)?
- Bad Credentials: Which hosts had access issues during scans? Find them in the Credentialed dashboards, or set up an alert.
- Anti-virus Current: Performs three checks: 1) that anti-virus is installed, 2)running, and 3) has the latest signatures—which verify a critical element of endpoint defenses. In a combination asset list, you can combine Systems That Have Been Scanned AND NOT Anti-Virus Current. This helps find systems with anti-virus problems that are ripe for compromise.
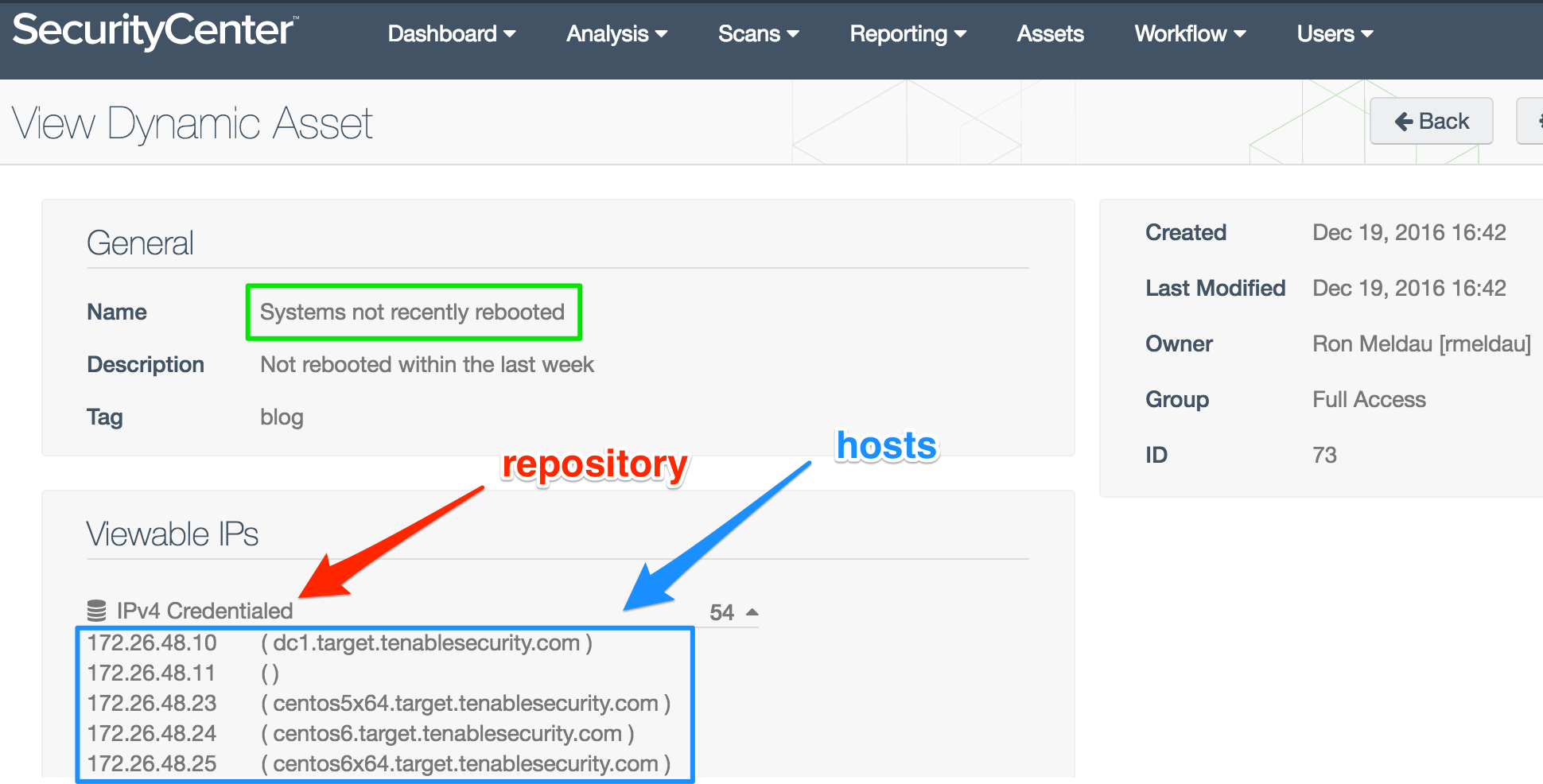
Part 3: Which hosts?
You may want to know which hosts are being referenced by an asset list. You’ll have to dig in to find that information. Start on the Assets page. For the asset list in question, click on the gear icon on the far right. Select View. Then in the Viewable IPs section, find the repository and click on the triangle. The host list appears.
Suggestions
SecurityCenter doesn’t only have vulnerability information. You can build asset lists with other characteristics such as processor architecture, software status, and equipment model to meet business needs in managing your inventory. Lists can combine exploit information, risk severity, and vulnerability age to help you discover which boxes to patch first. You can also datamine forensics like reboot time to debug patching problems.
Try these assets lists in your SecurityCenter and let us know what your favorite asset lists are. Which asset lists have been most helpful to you? Do you have a suggestion for an asset list template? Head on over to The Tenable Community to share your ideas.
Thanks to Steve Ketchum, Oregon Department of Corrections, for his asset list suggestions, and contributions to this blog.
- SecurityCenter
- Vulnerability Management
- Vulnerability Scanning