Tenable’s Continuous Network Monitoring™ and SCADA Environments
Supervisory Control and Data Acquisition, or SCADA, security has been in the spotlight a lot recently. In the past few months, we have seen an increasing amount of specialized malware specifically targeting SCADA systems. Malware that was previously focused on banking software has been modified to also affect Integrated Control Systems (ICS), and other examples of malware have been created specifically to target ICSs. According to USA Today, the U.S. power grid sees either a physical or electronic attack, on average, every four days.
SCADA malware in the news
The U.S. power grid sees either a physical or electronic attack, on average, every four days
Recently, we have also started to see physical effects from these attacks. In December 2014, electronic attacks against a German steel mill were directly attributed to physical damage to a furnace. This instance was particularly noteworthy because it had previously been uncommon for any organization to actually report that there was physical damage from electronic attacks.
Nation-states have also taken notice of SCADA’s importance. While Stuxnet may be old news, we still continue to see attacks specially created for the purpose of damaging SCADA systems. For example, South Korea recently accused North Korea of organizing attacks against their electronic infrastructure through spear phishing.
While organizations that use SCADA systems may be seeing an increasing number of directed attacks, the tools and communities around SCADA defense are also increasing rapidly. Conferences such as S4x15 help provide places for SCADA security professionals to share intelligence and discuss the challenges that SCADA organizations face when defending against attackers. In addition to conferences, lists like the SCADASec mailing list provide a place for professionals to discuss technical challenges and changes to regulations.
Tenable’s SCADA solutions
The sensitive and often “delicate” SCADA environments are excellent candidates for continuous network monitoring™. Tenable's continuous network monitoring solutions can be an important part of any organization's SCADA security toolbox. While SCADA infrastructure has improved in some ways, actively scanning SCADA networks still runs the risk of impacting the stability of delicate control systems. With tools such as SecurityCenter Continuous View™ (SecurityCenter CV™), organizations can monitor the state of their environments without the potential to impact their networks.
With tools such as SecurityCenter CV, organizations can monitor the state of their environments without the potential to impact their networks
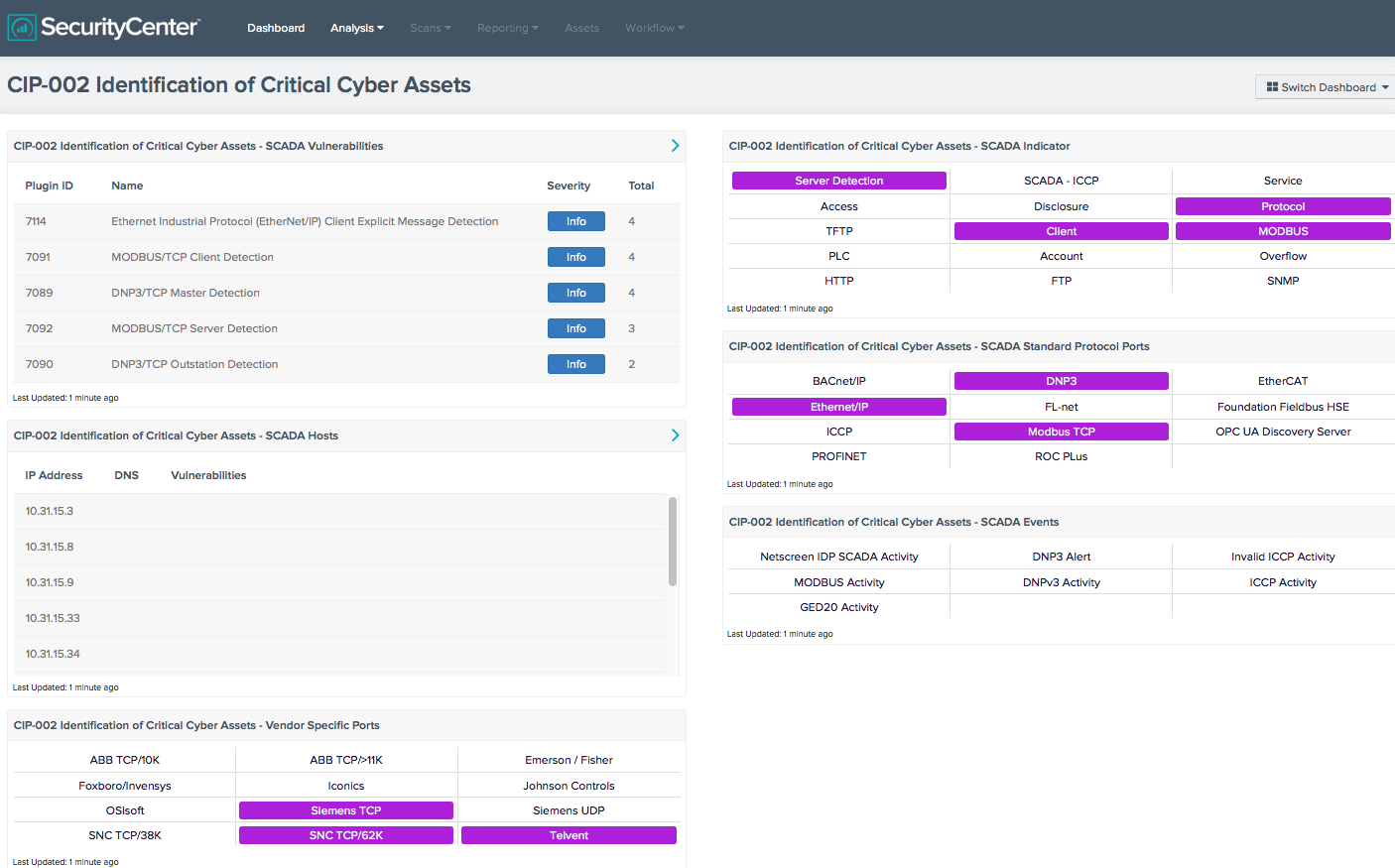
SecurityCenter CV doesn’t just discover the vulnerabilities affecting SCADA devices, but also monitors traffic and watches events for indicators of compromise and unauthorized activity. SecurityCenter CV uses active scanning, passive network monitoring and event log correlation to create a comprehensive, continuous view of network health.
SecurityCenter CV’s powerful capabilities offer organizations the ability to build dashboards that bring important information for analysts right to the forefront. For example, SecurityCenter CV can assist organizations with the regulatory challenges of North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP), which focuses on protecting the United States’ critical energy infrastructure. For organizations dealing with NERC CIP compliance, SecurityCenter CV has dashboards focusing on NERC CIP requirements in the Dashboard feed.
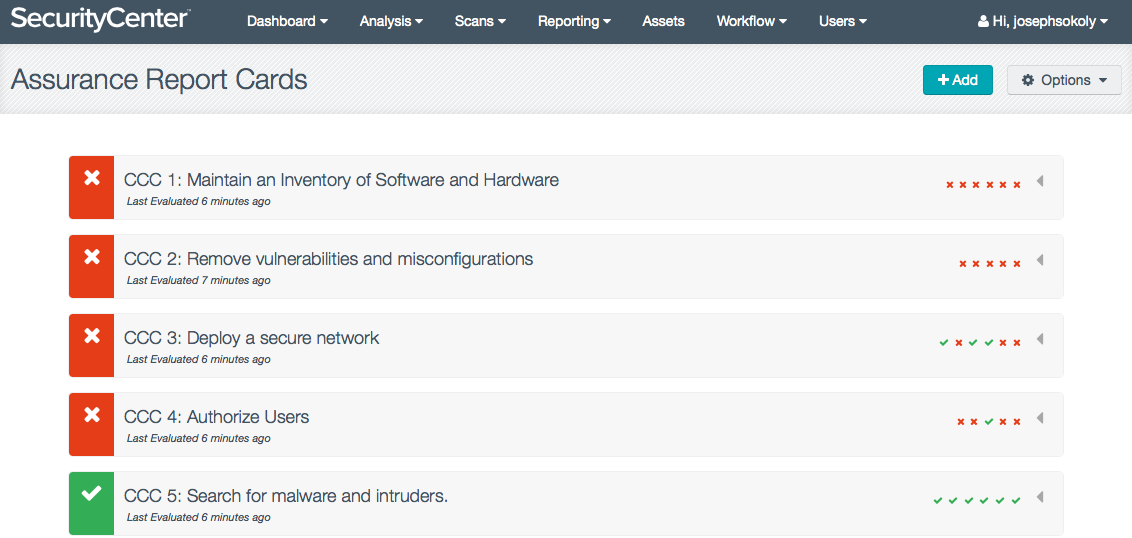
SecurityCenter CV’s new Assurance Report Cards™ (ARC) are also powerful tools in an organization’s toolbox. ARCs bridge the communication gap between business executives and security professionals by measuring and visually communicating the status of the most critical, fast-moving, automated security controls in an intuitive format. While organizations that deal with SCADA technologies face some unique challenges, all organizations face the challenge of communicating the efficiency of their security programs to executives. ARCs are updated continuously, providing the most current status information on an organization's security standards and compliance effectiveness in business language that is familiar to executives.
Tenable has recently updated the whitepaper, SCADA Network Security Monitoring: Protecting Critical Infrastructure, to reflect some of the recent changes to both the challenges that organizations with SCADA systems face and the new capabilities of Tenable’s continuous network monitoring solutions.
Conclusion
SecurityCenter CV doesn’t just discover the vulnerabilities affecting SCADA devices, but also monitors traffic and watches events for indicators of compromise and unauthorized activity
While SCADA environments can be similar to traditional networks, they have unique challenges, both technically and in regulatory compliance. There have certainly been increases in both targeted and more general attacks against SCADA infrastructure, but the tools and communities available to security professionals have also gotten better over time. As the attacks against critical infrastructure increase, the tools to defend against those attacks mature and Tenable’s SecurityCenter CV is no exception.
SecurityCenter CV’s Assurance Report Cards and dashboards bring important security information to the fingertips of analysts and package that information for presentation to executives. Tenable's Research team is constantly writing Nessus® plugins to detect malware and other threats to SCADA systems. These plugins are also used in SecurityCenter CV to help organizations detect and respond to new threats through continuous network monitoring.
Additional resources
For more information on how SecurityCenter CV can help organizations solve SCADA challenges, consult these resources:
- Energy Industry
- SCADA
- SecurityCenter