Tenable Podcast Episode 201 - "Internet Explorer 0Day"
Announcements
- We're hiring! - Visit the Tenable website for more information about open positions.
- Want to ask questions about Nessus, SecurityCenter, LCE, and PVS and get answers from the experts at Tenable? Join Tenable's Discussion Forum for custom scripts, announcements, and more!
- You can find links to subscribe to Tenable's Podcast feed, YouTube Channel, Twitter and Facebook accounts at http://www.tenable.com/podcast!
- IE 0Day Vulnerability - Several interesting points regarding this vulnerability:
- It affects most versions of Internet Explorer, including Windows XP and Microsoft still has not released a patch at the time of this writing.
- Workarounds include using a different web browser, disabling ActiveX, Un-Installing Adobe Flash and enabling and configuring EMET
- Tenable customers can detect which versions of Internet Explorer are in use, and on which systems, using credentialed scanning, passive detection, and log correlation. Nessus will report the version of IE in use, PVS will detect it on the wire, and LCE will report User-Agent data from your web servers.
- Nessus will report on the version of EMET in use on target systems, and report if Adobe Flash is installed
- Tenable customers can use a configuration auditing file to check for the pretense and correct configuration of EMET
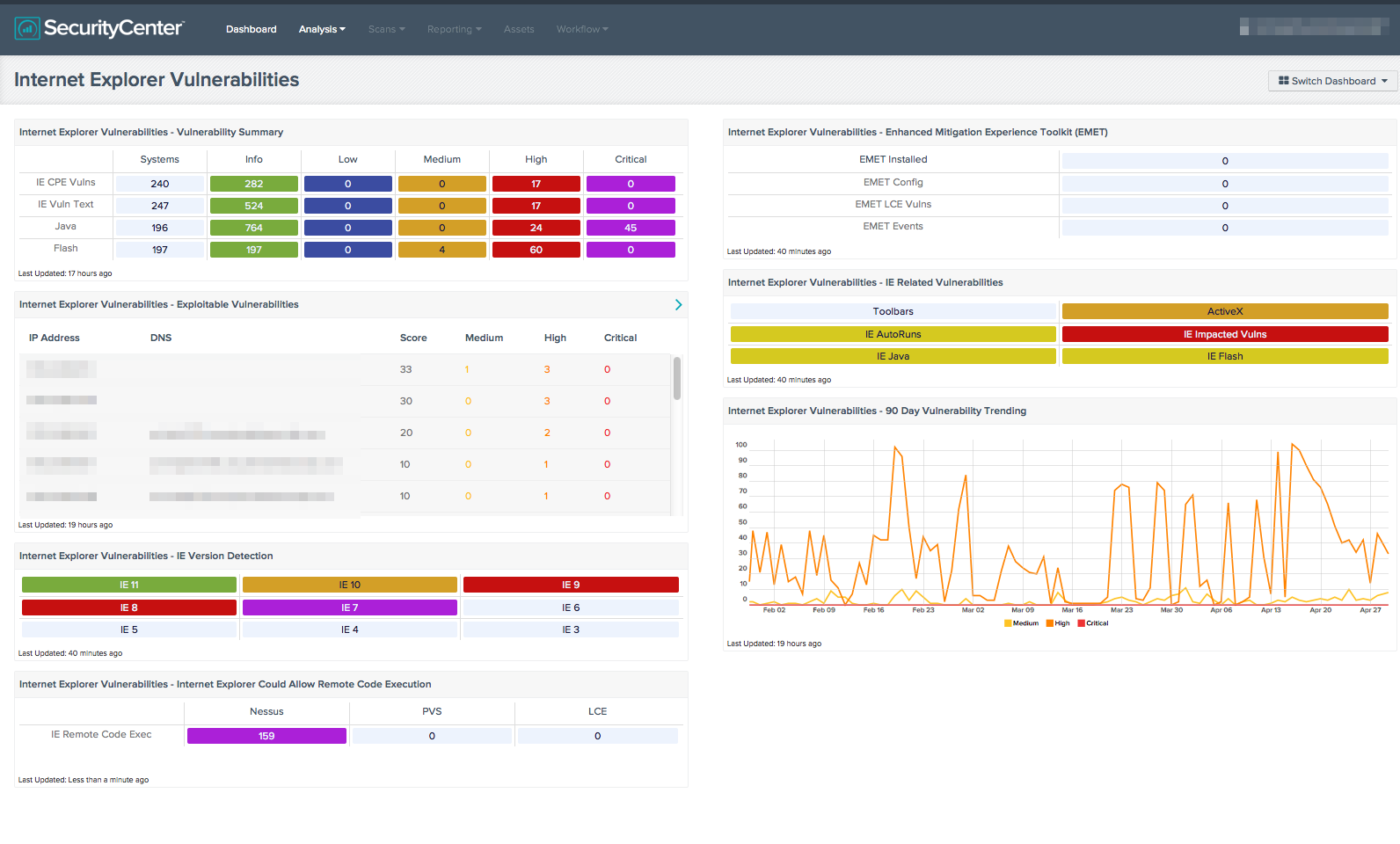
- We've released a new SC Dashboard to summarize the reporting of this vulnerability.
- Once a patch is released Nessus will be updated to include a check
Between IE and OpenSSL there is recent evidence of how vulnerabilities can hide within your network. You need ways to continuously discover them, evaluate risk and react.
The SecurityCenter Dashboard mentioned in this episode is below:
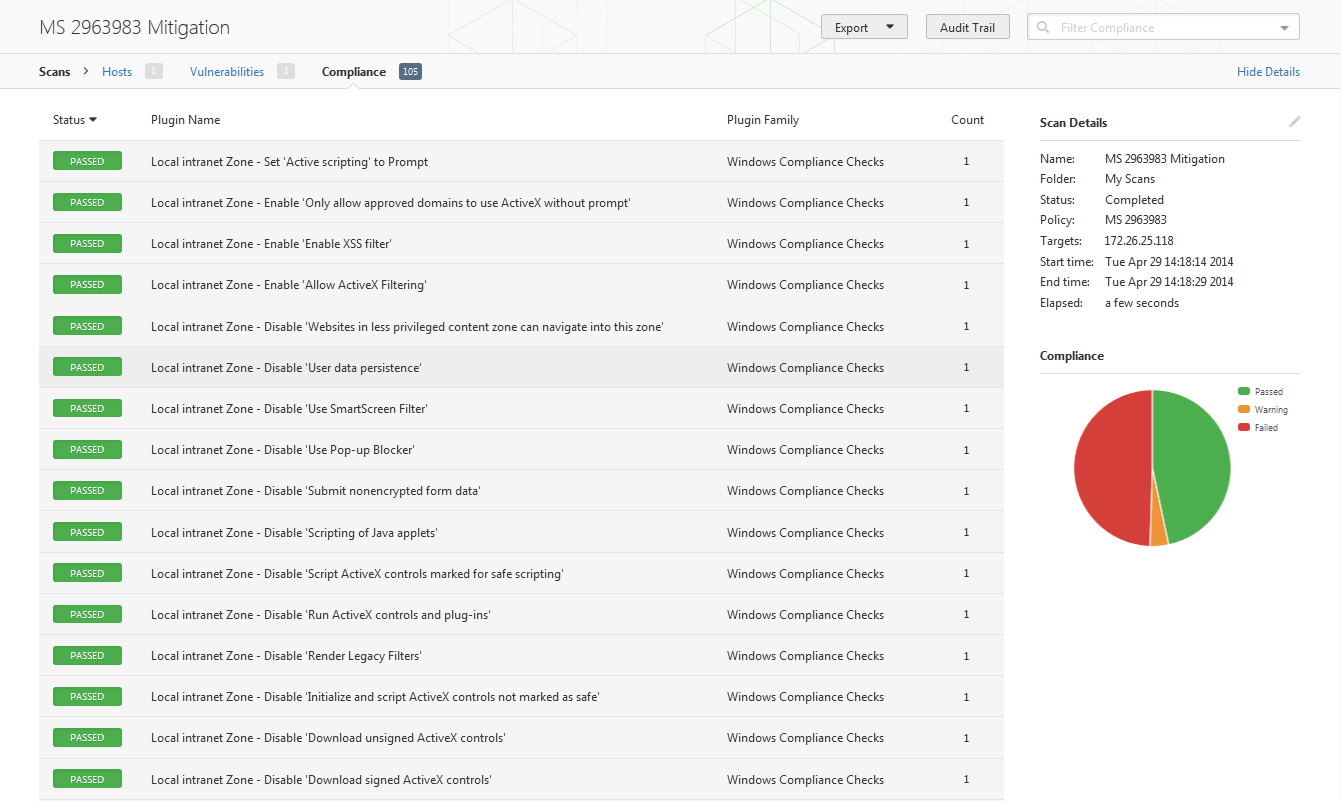
Nessus also has the ability to perform configuration auditing against EMET, also mentioned in the show, example results are shown below:
- IE 0Day Vulnerability - Several interesting points regarding this vulnerability:
Discussion
Nessus
- Fortinet OpenSSL Information Disclosure
- MaraDNS 1.2.12.06 / 1.3.05 Wildcard Resource Record Remote DoS
- HP LeftHand OS Unmanaged Host Detection
- MS14-020: Vulnerability in Microsoft Publisher Could Allow Remote Code Execution (2950145)
- OpenSSL 1.0.1 < 1.0.1g Multiple Vulnerabilities
- Ajax Pagination (twitter Style) Plugin for WordPress Local File Inclusion
- Silex USB Device Server Web Configuration Page Empty Password
- CUPS < 1.7.2 is_path_absolute Function XSS
- OpenVPN Installed
- FortiWeb 5.x < 5.0.4 XSS
- Symantec Messaging Gateway 10.x < 10.5.2 Management Console XSS (SYM14-006)
- NAS4Free Web UI Default Credentials
- Oracle OpenSSO Multiple Vulnerabilities (April 2014 CPU)
- Oracle OpenSSO Detection
- Cisco IOS IKE Module DoS
- MS KB2963983: Vulnerability in Internet Explorer Could Allow Remote Code Execution
- MS KB2961887: Update for Vulnerabilities in Adobe Flash Player in Internet Explorer
- Flash Player for Mac <= 11.7.700.275 / 13.0.0.201 Pixel Bender Component Buffer Overflow (APSB14-13)
- Flash Player <= 11.7.700.275 / 13.0.0.182 Pixel Bender Component Buffer Overflow (APSB14-13)
Passive Vulnerability Scanner
SecurityCenter Apps
Security News Stories
- Snapchat's Expired Snaps Are Not Deleted, Just Hidden
- Not to be outdone by Microsoft, Adobe announces zero-day exploit patch for Flash
- The Rise of the Insider in a Collaborative IT World
- Study finds data moving to cloud, encrypted or not
- AOL Subscriber Data Stolen: You've Got Pwned
- Thief in the night: Stealing in a digital age
- Dashboards
- Nessus
- Plugins
- Podcast
- SecurityCenter