Securing Active Directory: How to Prevent the SDProp and adminSDHolder Attack

Attackers can get into your Active Directory by leveraging the SDProp process and gaining privileges through the adminSDHolder object. Here's how to stop them.
Attackers use every possible trick and process they can to get into your Active Directory environment by moving laterally and gaining privileges. One such method is to leverage the Security Descriptor Propagation (SDProp) process and gain privileges through the adminSDHolder object.
The brief history of the SDProp process goes back to the early 2000s. Administrators were breaking what privileged groups could do in Active Directory when the access control list of the privileged group was changed in error. Microsoft fixed this by introducing the SDProp process, which used the adminSDHolder objects’ access control list (ACL) and the adminCount attribute of both users and groups.
The process works like this:
- Every 60 minutes, the SDProp process runs.
- The SDProp process copies the ACL from the adminSDHolder object, shown in Figure 1.
- The ACL from adminSDHolder is then pasted onto every user and group with an adminCount = 1, as you can see in Figure 2.
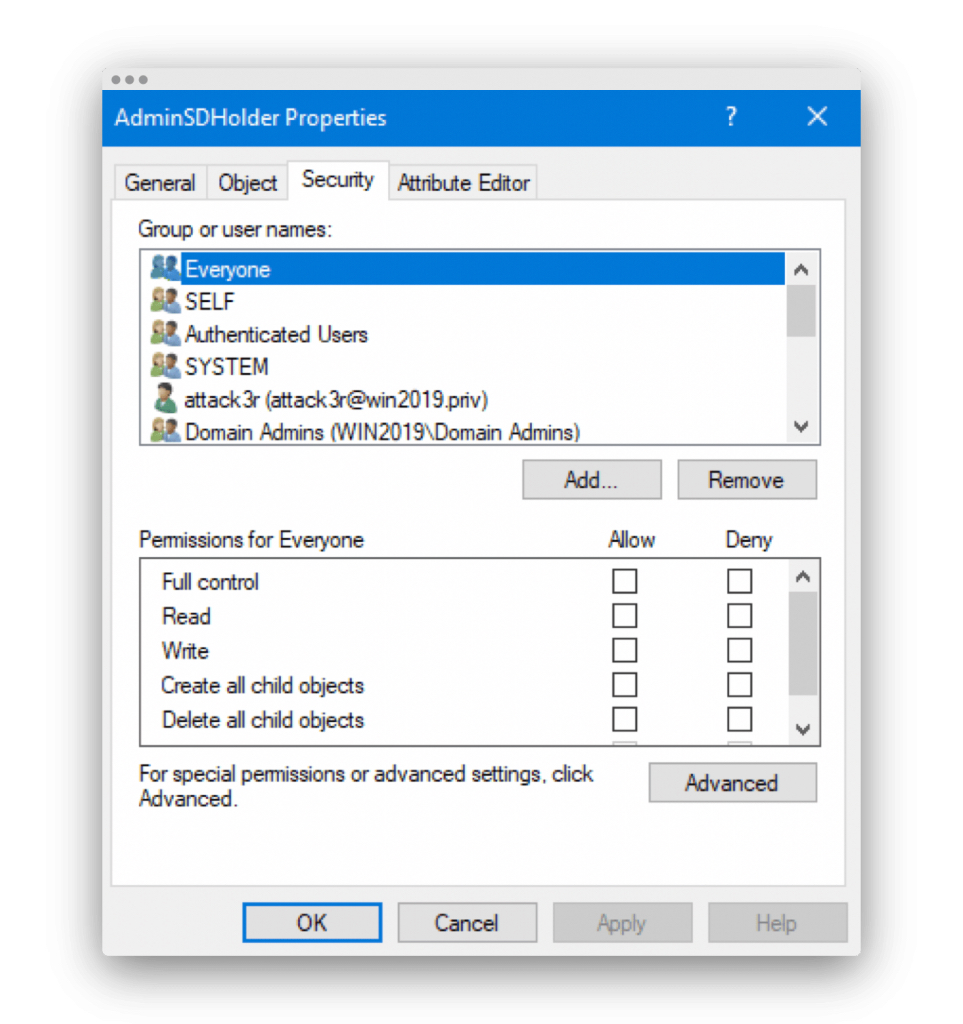
Figure 1. adminSDHolder object ACL.
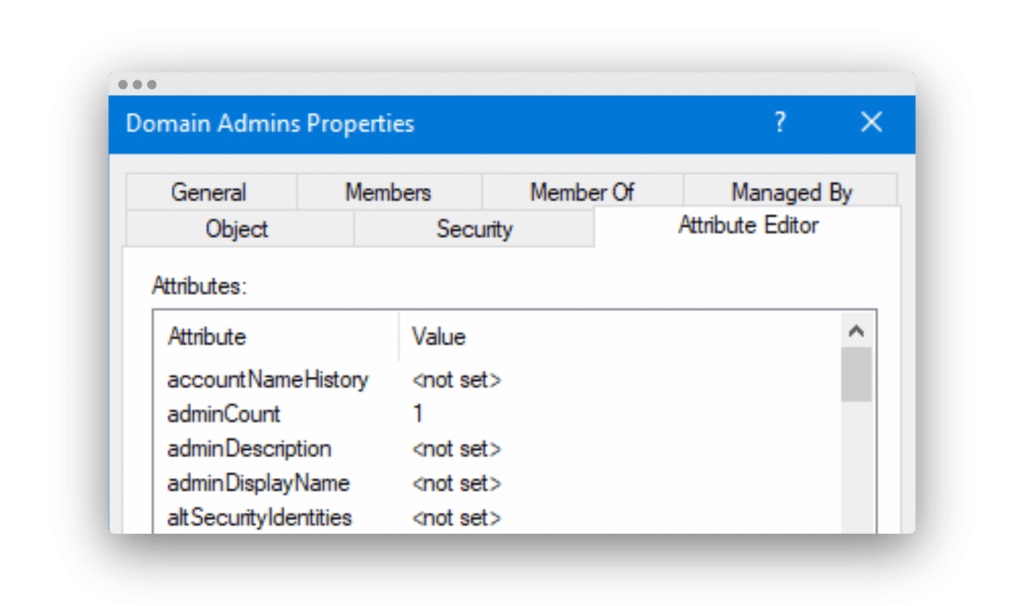
Figure 2. Group with adminCount = 1.
You can see this process in action by looking at the replication trail flow between domain controllers (Figure 3).
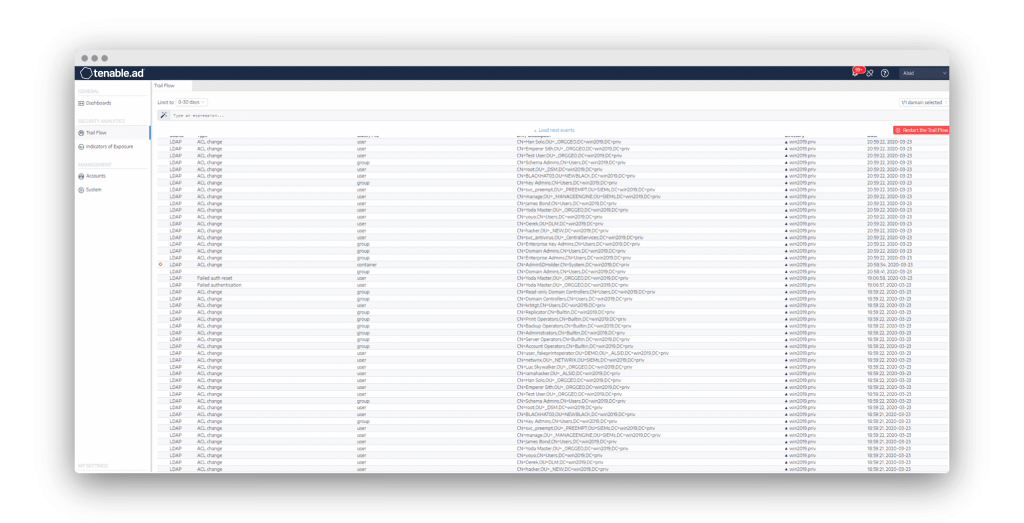
Figure 3. SDProp process updates the ACL on all users and groups with adminCount = 1.
Attackers realized that if they add a rogue user or group to the adminSDHolder ACL, when the SDProp process ran, they would be added to every privileged user and group automatically. Even if the user or group was manually removed from the ACL of the privileged user or group, the SDProp process would add them back 60 minutes later.
Thus, it is necessary to constantly evaluate the adminSDHolder ACL and accounts that have an adminCount = 1 (but shouldn’t), as these are attack pathways into Active Directory.
Tenable.ad is constantly looking at these attack pathways and will send an alert when one opens. You can see this in the Indicators of Exposure (IoE) shown in Figure 4.
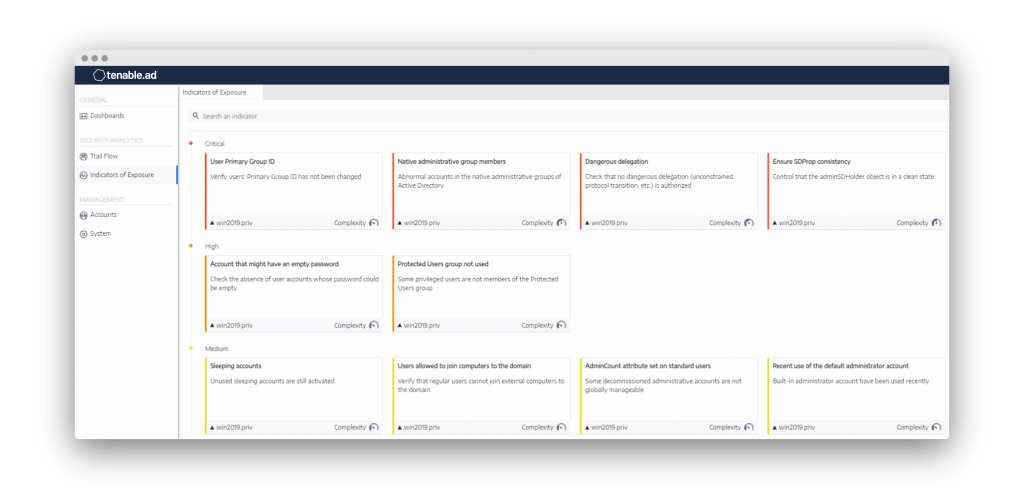
Figure 4. IoE clearly show attacks using the SDProp process and adminCount attribute.
Being able to see all aspects of an attack in real time enables the security team to react swiftly to prevent any further damage in Active Directory and safeguard the controls and information that users have access to.
For more information on this topic and strategies for strengthening your own Active Directory security, visit our Tenable.ad product page.
This blog post originally appeared on the Alsid website on July 14, 2020.
- Active Directory



