Securing Active Directory: 3 Ways to Close the No-Password Loophole

Any Active Directory user can have their password requirements negated with a simple command. Here’s how to identify these gaps before an attacker does.
With Active Directory being around for so long, organizations and administrators get complacent with what they “think” is in place, which can lead to major security issues being exposed. Let’s take the fact that any Active Directory user can have their password requirements completely negated with a simple command. This setting is not obvious and can be missed during a security review or audit.
First, let’s see how this setting can be configured for a user, from a command line running as an administrator:
Net user <username> /passwordreq:no
Yes, it’s that simple! Now, how would you see such settings per user so you can then secure the accounts? There are a few options.
Saved Query in Active Directory Users and Computers (ADUC)
Create a new Saved Query that has a custom LDAP (Lightweight Directory Access Protocol) search like the following (also shown in Figure 1):
(&(&(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=32))))
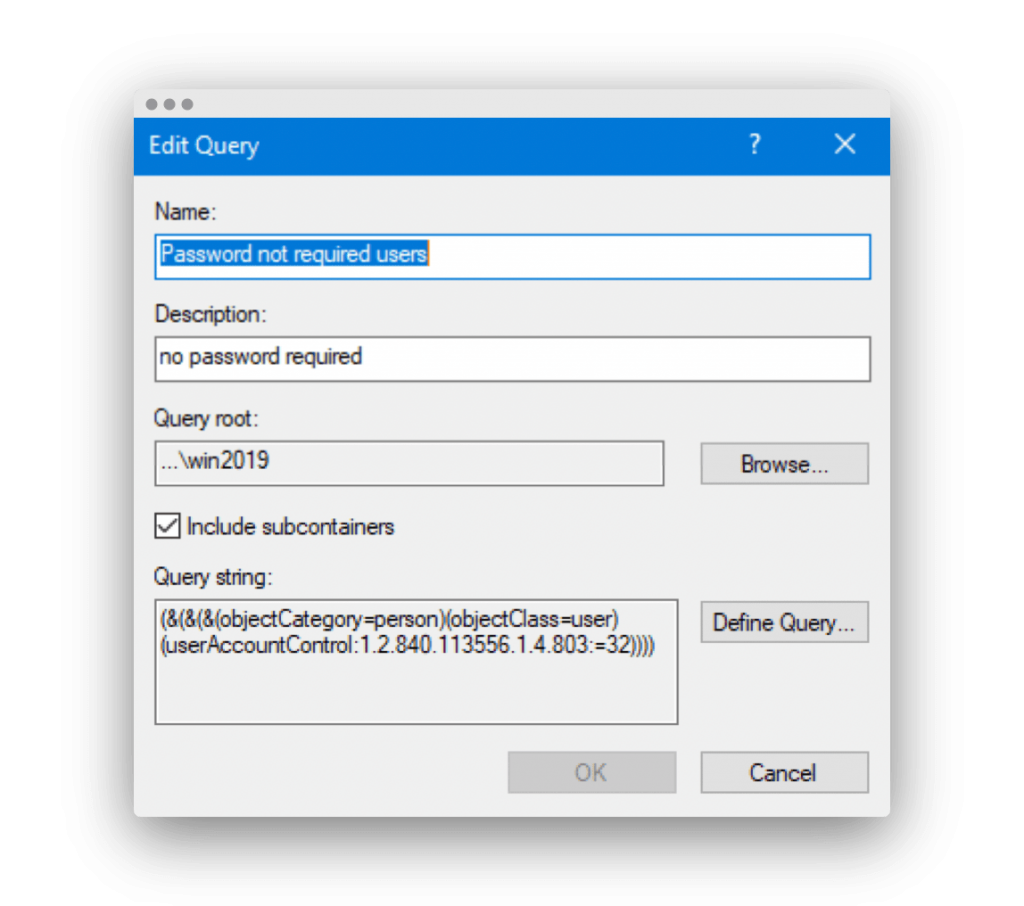
Figure 1. Custom LDAP search using Saved Queries to find users with no password required.
PowerShell
Using the Active Directory Module for Powershell, you can also use:
Get-ADUser -Filter {PasswordNotRequired -eq $true}
Tenable.ad
The above options for retrieving the list of users with no required password are easy, but they are only point-in-time solutions. You would need to constantly run and evaluate the output to ensure that no additional users have been configured to not require a password. Better yet is a real-time solution that constantly looks for these users and alerts you as needed. Enter Tenable.ad. (See Figure 2.)
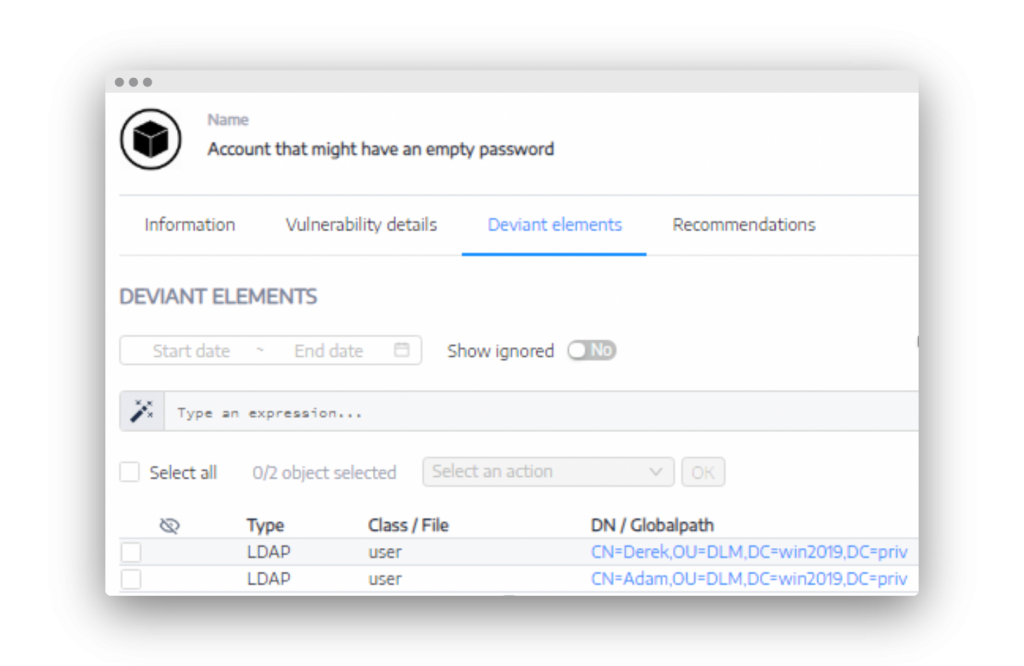
Figure 2. Tenable.ad can email you when a user is set to not require a password.
The fix for any user that does not require a password is to set the user account to require one. This is simple:
Net user <username> /passwordreq:yes
I strongly encourage you to verify if any users are allowed a blank password and to fix this loophole before someone else in the environment tries to attack these settings.
For more information on this topic and strategies for strengthening your Active Directory security, visit our Tenable.ad product page.
This blog post originally appeared on the Alsid website on July 14, 2020.
- Active Directory



