Oracle April 2021 Critical Patch Update Addresses 257 CVEs including ‘Zerologon’ (CVE-2020-1472)

Oracle addresses over 250 CVEs in its second quarterly update of 2021 with 390 patches, including 34 critical updates.
Background
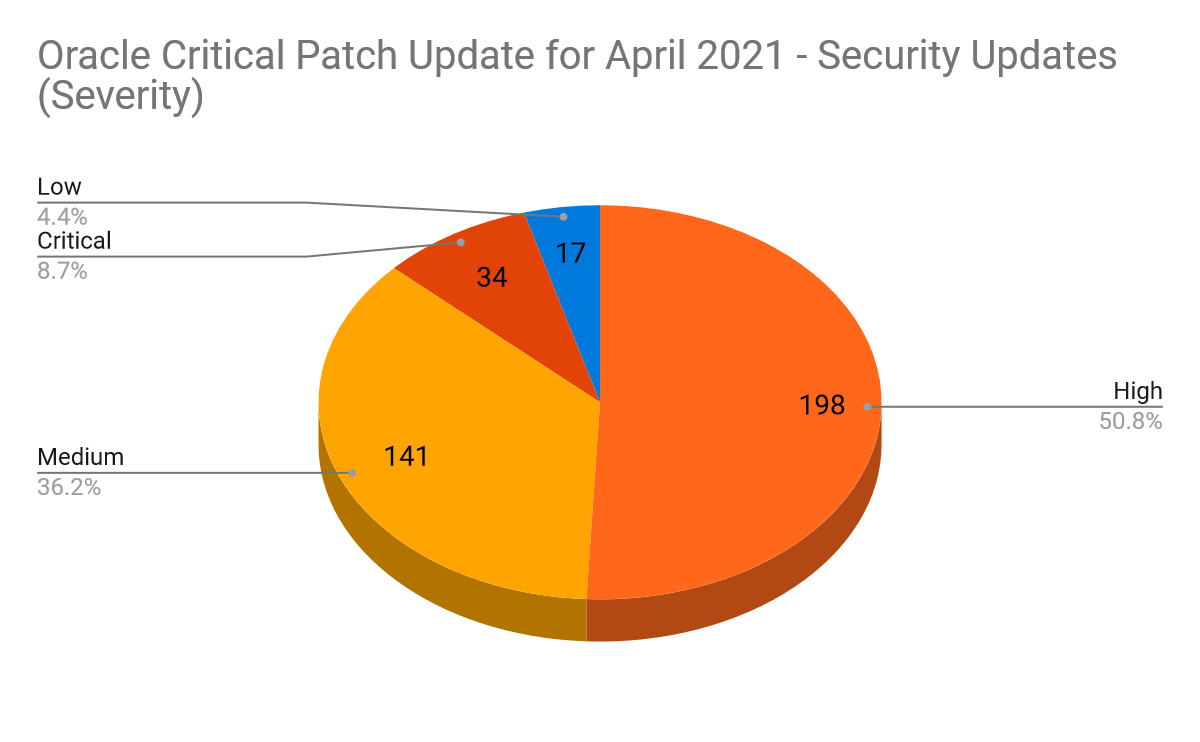
On April 20, Oracle released its Critical Patch Update (CPU) for April 2021, the second quarterly update of the year. This CPU update contains fixes for 257 CVEs in 390 security updates across 32 Oracle product families. Out of the 390 security updates published this quarter, over 50% were assigned a high severity. Critical vulnerabilities only accounted for eight percent of the security updates patched this quarter.
Analysis
This quarter’s update includes fixes for 34 critical issues across 30 CVEs. The Oracle E-Business Suite product family contained the highest number of patches at 70, representing just shy of 18% of the patches from this quarter. Of those 70 patches, 22 issues are remotely exploitable without authentication.
As we’ve seen with past CPUs, Oracle Fusion Middleware continues to take the lead in the number of vulnerabilities which can be exploited by unauthenticated attackers, as 36 of the 45 patches meet this criteria. A full breakdown of the patches can be seen in the table below:
| Oracle Product Family | Number of Patches | Remote Exploit without Auth |
|---|---|---|
| Oracle E-Business Suite | 70 | 22 |
| Oracle MySQL | 39 | 10 |
| Oracle Fusion Middleware | 45 | 36 |
| Oracle Retail Applications | 35 | 31 |
| Oracle Virtualization | 24 | 5 |
| Oracle Communications | 22 | 9 |
| Oracle PeopleSoft | 18 | 13 |
| Oracle Financial Services Applications | 15 | 10 |
| Oracle Communications Applications | 13 | 12 |
| Oracle Database Server | 10 | 4 |
| Oracle JD Edwards | 10 | 10 |
| Oracle Enterprise Manager | 9 | 8 |
| Oracle Construction and Engineering | 8 | 6 |
| Oracle Siebel CRM | 8 | 7 |
| Oracle Hospitality Applications | 6 | 4 |
| Oracle Storage Gateway | 6 | 2 |
| Oracle Supply Chain | 5 | 5 |
| Oracle Systems | 5 | 1 |
| Oracle Utilities Applications | 5 | 5 |
| Oracle NoSQL Database | 4 | 3 |
| Oracle Commerce | 4 | 4 |
| Oracle Java SE | 4 | 4 |
| Oracle Health Sciences Applications | 3 | 3 |
| Oracle Spatial Studio | 2 | 1 |
| Oracle Food and Beverage Applications | 2 | 1 |
| Oracle Hyperion | 2 | 1 |
| Oracle Global Lifecycle Management | 1 | 1 |
| Oracle REST Data Services | 1 | 1 |
| Oracle SQL Developer | 1 | 1 |
| Oracle iLearning | 1 | 0 |
| Oracle Insurance Applications | 1 | 1 |
| Oracle Support Tools | 1 | 0 |
Five 10.0 CVSSv3 Scoring Vulnerabilities
This quarter Oracle includes patches to address five CVEs, with the highest severity CVSSv3 score of 10.0. This includes the critical Zerologon vulnerability (CVE-2020-1472). These flaws could be exploited by unauthenticated, remote attackers and should be prioritized for patching. The table below outlines each affected Product and CVE:
| CVE | Oracle Product Family | Oracle Product and Component |
|---|---|---|
| CVE-2021-2177 | Oracle Virtualization | Oracle Secure Global Desktop / Gateway |
| CVE-2021-2248 | Oracle Virtualization | Oracle Secure Global Desktop / Server |
| CVE-2020-1472 | Oracle Systems | Oracle ZFS Storage Appliance Kit / Operating System Image |
| CVE-2021-2317 | Oracle Storage Gateway | Oracle Cloud Infrastructure Storage Gateway / Management Console |
| CVE-2021-2256 | Oracle Storage Gateway | Oracle Storage Cloud Software Appliance / Management Console |
Proof of concept
At the time this blog was written, several of the highest severity (CVSSv3 9.8 and 10.0) CVE’s have published proof-of-concept (PoC) scripts. While all of these have not been tested or verified by Tenable, we would recommend taking action to patch the flaws as soon as possible. The following table lists some of the CVEs that currently have published PoCs:
| CVE | Oracle Product and Component | PoC Links |
|---|---|---|
| CVE-2020-1472 | Oracle ZFS Storage Appliance Kit / Operating System Image | GitHub |
| CVE-2020-17530 | MySQL Enterprise Monitor / Monitoring: General (Apache Struts) Oracle Hospitality OPERA 5 / Login (Apache Struts) | GitHub |
| CVE-2019-17495 | Oracle Utilities Framework / General (Swagger UI) | GitHub |
| CVE-2019-17195 | Enterprise Manager Base Platform / Enterprise Manager Install (Nimbus JOSE+JWT) | GitHub |
Solution
Customers are advised to apply all relevant patches in this quarter’s CPU. Please refer to the April 2021 advisory for full details.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- Oracle Critical Patch Update Advisory - April 2021
- Oracle January 2021 Critical Patch Update Risk Matrices
- Oracle Advisory to CVE Map
- CERT Vulnerability Note VU#567764 for CVE-2021-2307
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

