NERC CIP-008-6: How Power Grid Operators Can Improve Their Incident Reporting

The new NERC CIP-008-6 regulation challenges power grid operators to differentiate attempts to compromise their environment from other non-malicious cyber incidents. Here’s how Tenable can help.
For more than a decade, regulatory agencies and computer security incident response teams (CSIRTs) encouraged organizations to responsibly share information on cybersecurity incidents and raise the community’s overall preparedness to manage cyberthreats. The latest example includes new requirements by the Federal Energy Regulatory Commission (FERC) that require bulk power system (BPS) utilities to report attempts to compromise their infrastructure and operations. The exact requirements, which became mandatory on Jan. 1, 2021, are defined in NERC CIP 008-6.
While the intention behind these new regulations is to raise the cyber resilience of the power grid and facilitate effective response to major security events, they also introduce two main challenges for responsible entities:
- Technically, how to correctly differentiate attempts to compromise the environment from human errors and routine events?
- Procedurally, how to achieve the above with minimal bureaucratic burden on already stretched-thin cybersecurity professionals?
Tenable’s approach to the new NERC CIP requirements mirrors our handling of other regulatory requirements. Security solutions purpose-built for operational technology (OT) environments should make it as easy and automated as possible for users to identify, triage and report incidents to authorities as required. Here are three aspects of Tenable’s OT security solution that can help streamline compliance for the power grid industry.
Policy-based detection streamlines compliance efforts
Tenable.ot’s policy-based detection is a deterministic, flexible and transparent engine in which customers express their network security rules as policies with a custom level of granularity. As a result, security teams can be alerted to every deviation from these policy rules. This is the ideal method to meet the requirements by NERC CIP to “have a process that includes criteria to evaluate and define attempts to compromise and to determine if an identified Cyber Security Incident is a reportable cyber incident or an attempt to compromise...” (extracted from CIP-008-6, Table R1, part 1.2).
When using policies in Tenable.ot, users can quickly establish communication alerts ranging from specific OT configuration commands to reads and writes of tags or anomalous traffic in any IT protocol. Furthermore, these alerts can be categorized by asset groups, network segments, specific time windows and other specifications. For example, if a certain group of substation controllers has a specific time window when changes are allowed, and those changes are only permitted through proprietary configuration protocols and by a closed list of engineering stations or subnets, these rules can be configured in less than a minute in Tenable.ot.
Setting user-specific policies acts like a safety net for our customers, defining the baseline for healthy operations and ensuring that no anomaly goes unnoticed. This set of policies can be exported and shared with any third-party stakeholder, providing a clear and immediate understanding of the measures taken to adhere to the regulatory requirements.
Figure 1: The policies tab in the Tenable.ot interface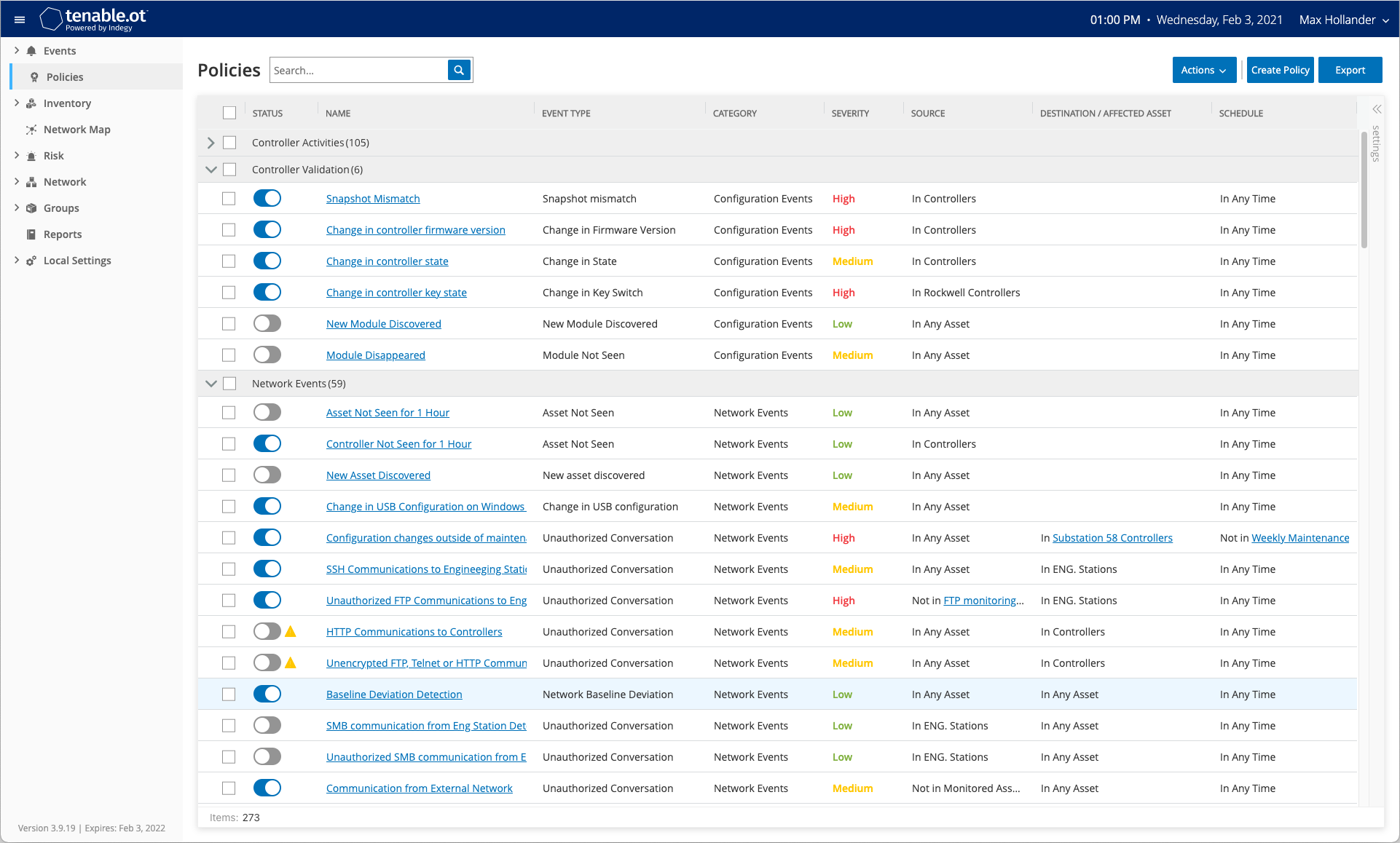
Threat landscape intelligence distinguishes malicious attacks from user anomalies
In some cases, policies can be set to alert on incidents that clearly indicate the existence of malicious intent. But in many other cases, analysts face uncertainty about the origin or cause of the alert and must look for additional information that can suggest malicious intentions.
When considering the network assets that are involved in a suspected incident, Tenable.ot users have at their hand the most recent threat intelligence as reflected in the Vulnerability Priority Rating (VPR), which incorporates parameters such as threat source, intensity and recency. Taking these parameters into consideration may provide the otherwise missing link in differentiating between operational anomalies and malicious attempts to compromise, a distinction that is the essence of the new additions to NERC CIP-008-6.
Figure 2: Attack vector simulation in the Tenable.ot interface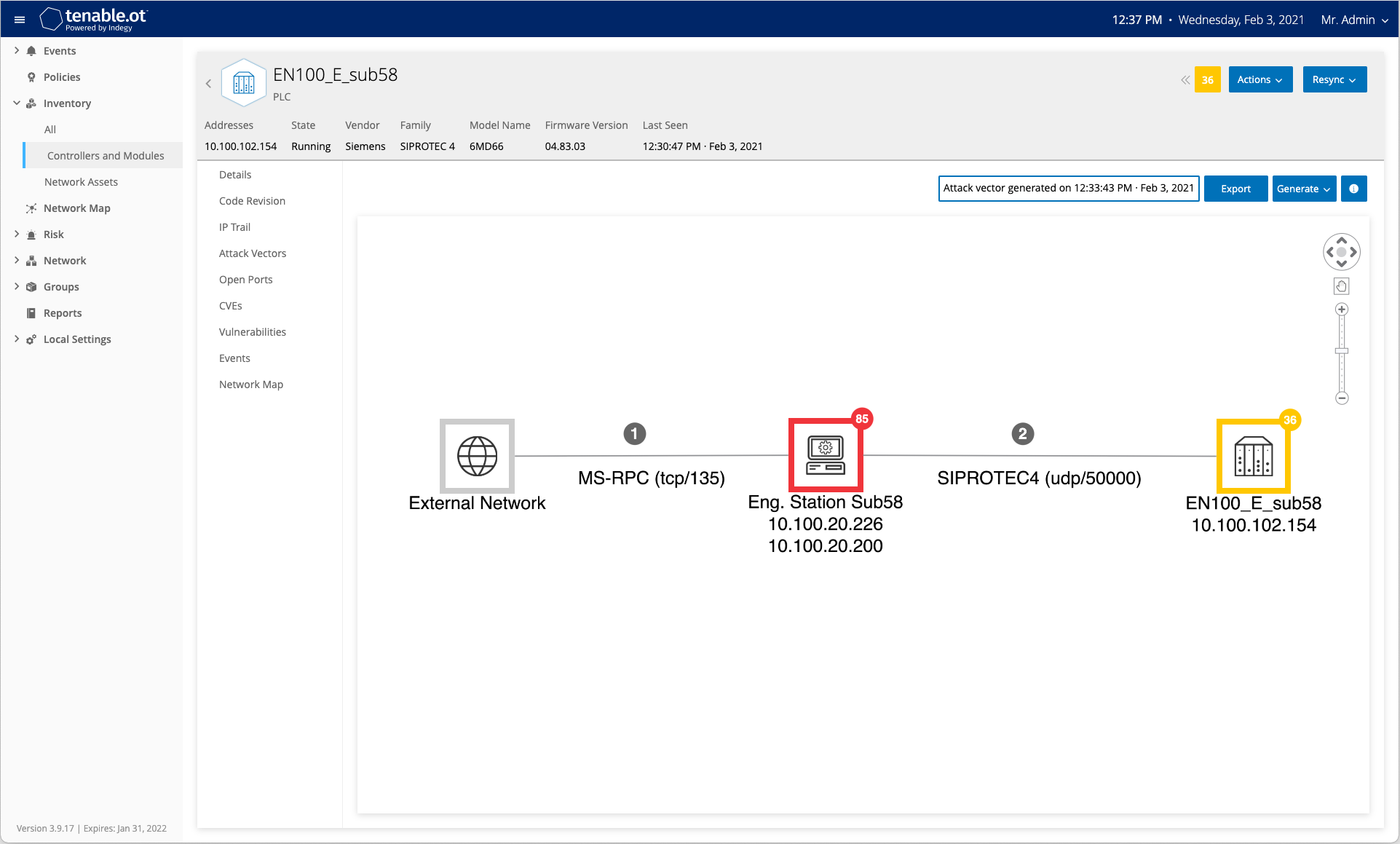
Unified IT-OT attack simulation protects critical network segments
Among the many cybersecurity tools available for identifying suspicious incidents, those with a unified view of both IT and OT environments have an advantage when it comes to correctly identifying attempts to compromise. Understanding possible attack vectors that stem from weaknesses in the IT environment is key for correctly assessing incidents, as previous attacks and proofs of concept teach us. Without such a broad view, OT engineers might miss essential pieces of the puzzle regarding the origin of their alerts. Similarly, IT security analysts might be blind to the consequences on the OT side of indications they witness and dismiss as non-events.
Addressing this gap is at the heart of Tenable’s efforts over the last year. Several new layers of integration are now available: Reflecting OT findings in enterprise-level applications (Tenable.io and Tenable.sc), unifying IT and OT vulnerability detection technology, and leveraging Nessus as part of Tenable.ot to best identify vulnerabilities in IT assets in the OT environment.
Figure 3: Unified IT-OT dashboard in Tenable.sc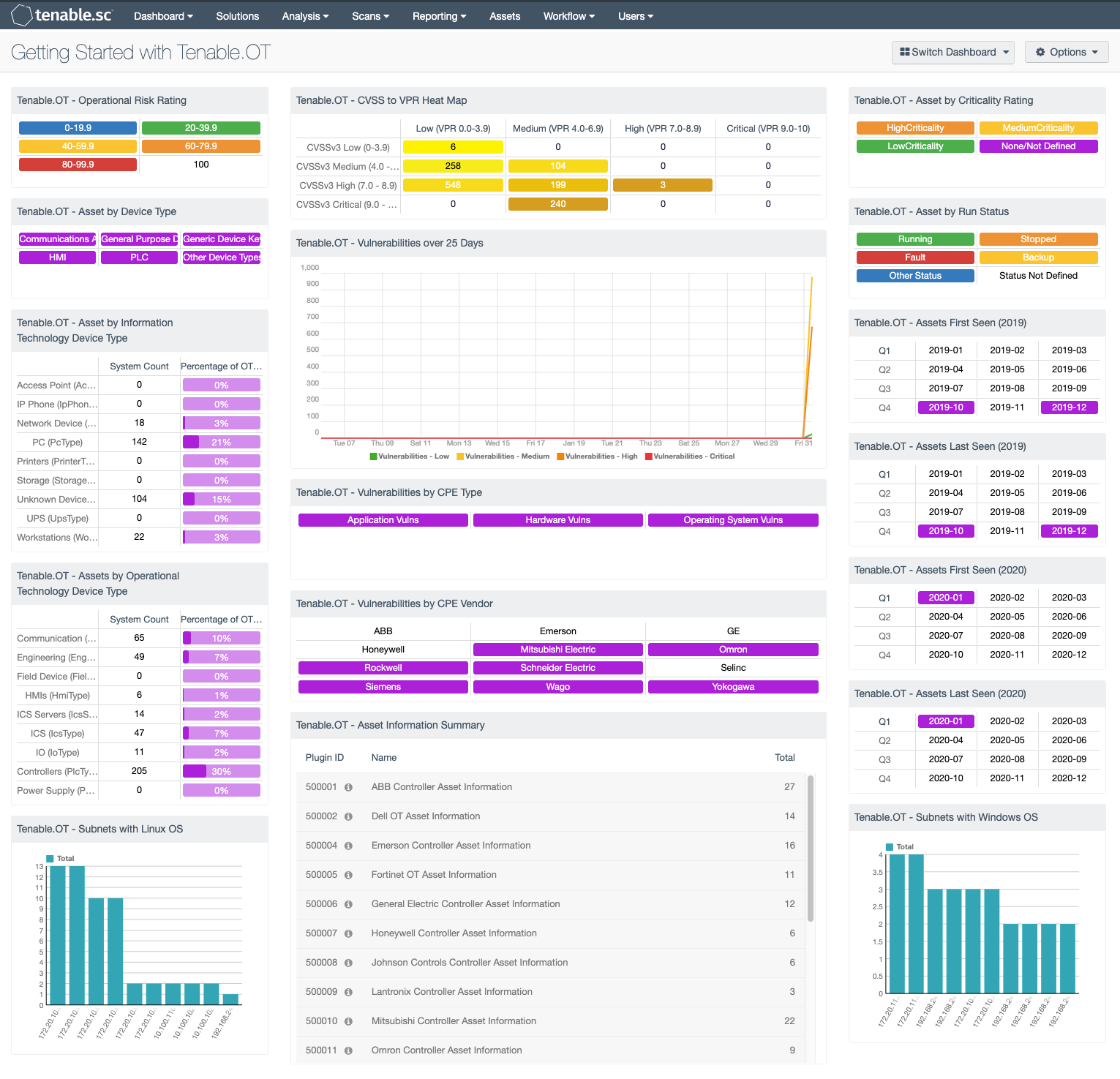
Summary
OT security professionals face increasing regulatory requirements for reporting cyber incidents, with the energy sector leading the way. Reporting attempts to compromise the grid requires highly skilled cybersecurity analysis, ready access to the data you need and clear reporting procedures. Tenable.ot, as part of the Tenable suite of security products, has exactly what it takes to identify cyber incidents and help categorize them as actual attacks, attempts to compromise, human errors or routine events.
For more information on how Tenable can help strengthen grid security, download our Guide to Compliance with NERC CIP Standards.
- Energy Industry
- Incident Response
- OT Security
- Security Frameworks



