Installing and Using Nessus on Kali Linux
Note: These 2014 instructions are for installing Nessus version 5 on Kali Linux. Please see the newer blog, Getting Started with Nessus on Kali Linux, for information on installing Nessus version 6 and higher on Kali Linux 2016.
Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
If you are using Nessus for vulnerability scanning activities, consider installing Nessus on Kali Linux. Kali Linux is a fantastic distribution specifically designed for penetration testing.
Nessus, Kali, and Penetration Testing
Tenable provides Nessus on a wide variety of platforms to choose from. One of those choices is a Linux distribution designed for penetration testers called Kali Linux. Kali Linux, formerly known as "Backtrack", is a Debian-based Linux distribution containing hundreds of tools to perform penetration tests.
The tools available in Kali Linux complement a Nessus installation, allowing everything to be in one place, easing maintenance and portability. Nessus reports on host discovery, vulnerability identification, and exploitability of a given vulnerability which are all important findings in the penetration testing process.
Nessus also has many other features to support penetration testing activities that you may not be aware of. These include:
- Correlating a vulnerability with an exploit (including cross referencing Metasploit, Core IMPACT, Immunity CANVAS, D2 exploitation packs, ExploitDB, vulnerabilities that do not require an exploit, and more)
- Filtering vulnerability results by exploit availability and/or exploitability ease
- Performing web application scanning and recon including site spidering, detecting common web application vulnerabilities specific to your applications, and fuzzing CGI parameters
- Using credentials harvested from other phases of testing to perform credentialed patch audits, local (client-side) application vulnerability scanning, and discovery of interesting configurations on targets
- Re-casting risk, identify low-severity vulnerabilities and allow an admin-level user to re-cast them as critical vulnerabilities. Re-casting risk empowers testers to review lower severity findings that often lead to serious exposures.
Installing and Configuring Nessus
Nessus does not come pre-installed on Kali Linux, but can be installed and activated easily:
- Step 1 - Purchase Nessus - You can purchase Nessus from Tenable's online store (including bundles containing training and additional products such as the Passive Vulnerability Scanner) or through one of our resellers.
Step 2 - Obtain Nessus and an Activation Code - Once you've purchased Nessus, you will receive an account on the Tenable Support Portal and an activation code to be used in the installation process. Simply login to the support portal download the Kali Linux install package based on your processor architecture, for example:
Nessus-5.2.7-debian6_amd64.deb Nessus 5.2.7 for Debian 6 and 7 / Kali Linux AMD64 Nessus-5.2.7-debian6_i386.deb Nessus 5.2.7 for Debian 6 and 7 / Kali Linux i386Step 3 - Installing Nessus:
Once you've transferred the appropriate Nessus Debian package to your Kali Linux installation, run the following commands to install and start Nessus (it is assumed that your Kali Linux is configured with access to the Internet):
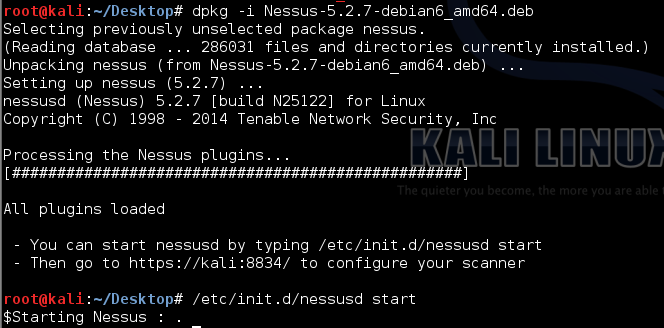
Installing Nessus on Kali Linux via the command line.
The web interface can be accessed with your browser by making an HTTPS connection to TCP port 8834 (e.g. https://localhost:8834/). You can also access the Nessus Web Interface remotely by using the default IP address assigned to Kali Linux (e.g. https://192.168.1.250:8834/). Make certain that Javascript is enabled in the browser you are using to manage the Nessus server.
Accessing the Nessus Web Interface.
Follow the installation wizard, which will prompt you to create an account to log in to Nessus and install your activation code.
Note: Once Nessus has been initially started, it will begin the process of downloading, indexing and compiling all plugins. This can take some time, depending on the speed of your system (or virtual system). If Nessus is still processing plugins, you will see a progress bar in the web interface.
Please refer to the Nessus 5.2 Installation and Configuration Guide for answers to common installation questions and more information about installing and configuring Nessus.
Conclusion
Nessus is the most trusted, accurate, and reliable vulnerability scanner on the market, making it a perfect complement to your penetration tests and security assessments. Nessus Manager (and Nessus Cloud) allows you to further extend your vulnerability scanning program by engaging others in IT and auditing through sharing of scanning resources (including assigning roles, scanners, reports, policies, and more). Tenable's other products, such as the Passive Vulnerability Scanner and SecurityCenter Continuous View, enable IT organizations to implement a continuous monitoring solution to collect vulnerability and operational data via scanning, sniffing and logging. All of these technologies combined allow for deep insights into your network, and any threats that may be lurking.
Further Reading:
- Nessus

