Detecting SambaCry CVE-2017-7494

We’ve seen several critical vulnerabilities lately. First there was WannaCry, and then WannaCry 2.0 (EternalRocks), and now do we have WannaCry 3.0? Well, not really. But a new seven-year-old remote code execution vulnerability (CVE-2017-7494) that is affecting Samba versions 3.5.0 and higher is making news this week. The vulnerability is billed as the WannaCry equivalent for Linux, and some are even calling it SambaCry since it affects the SMB protocol implementation in Linux and is potentially wormable. To be clear, this new vulnerability is unrelated to the SMB exploits that were released by the Shadow Brokers group and used by WannaCry ransomware to infect a large number of systems. SambaCry is similar only because the vulnerability affects the SMB protocol in Linux. The Tenable research team is always on top of these news-worthy vulnerabilities, and this latest Samba weakness is no different. You’ll find multiple detection tools in your Tenable feed, ready to use in your scan program.
What’s the attack surface?
Samba is an open source re-implementation of the SMB/CIFS networking protocol, which provides file and print services for various Microsoft Windows clients. It runs on most Unix, OpenVMS and Unix-like systems, such as Linux, Solaris, and AIX and is standard in most Linux distributions. As a result, it's available on a large variety of Unix-like systems.
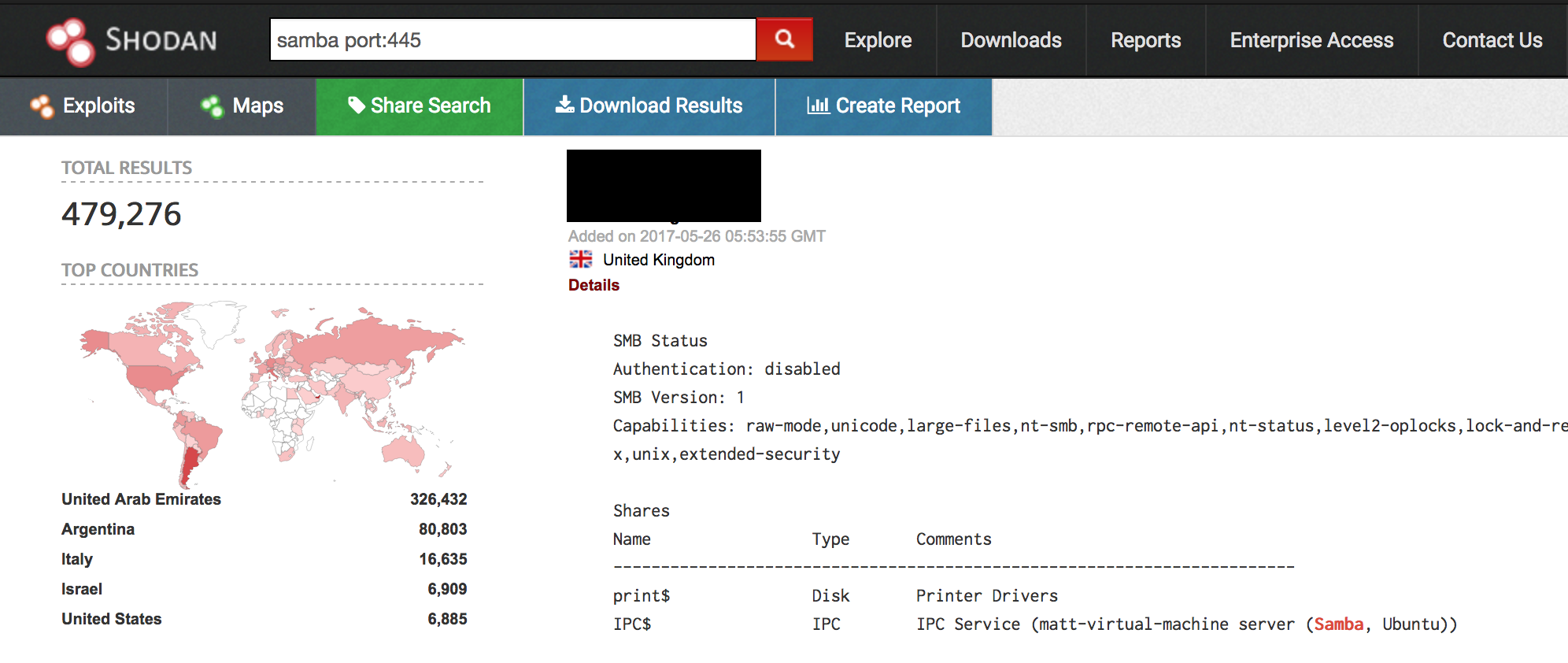
A quick Shodan search shows over 475,000 Samba-enabled hosts are accessible over the internet. However, it isn’t clear how many of them are running vulnerable versions of Samba.
The vulnerability itself can be exploited with a single line of code. A malicious client can upload and cause the smbd server to execute a shared library from a writable share. Exploit modules are already available from Metasploit to exploit this issue.
What steps can you take?
The first step is to patch vulnerable versions of Samba right away. Tenable has several tools to help you detect affected Samba versions.
Nessus
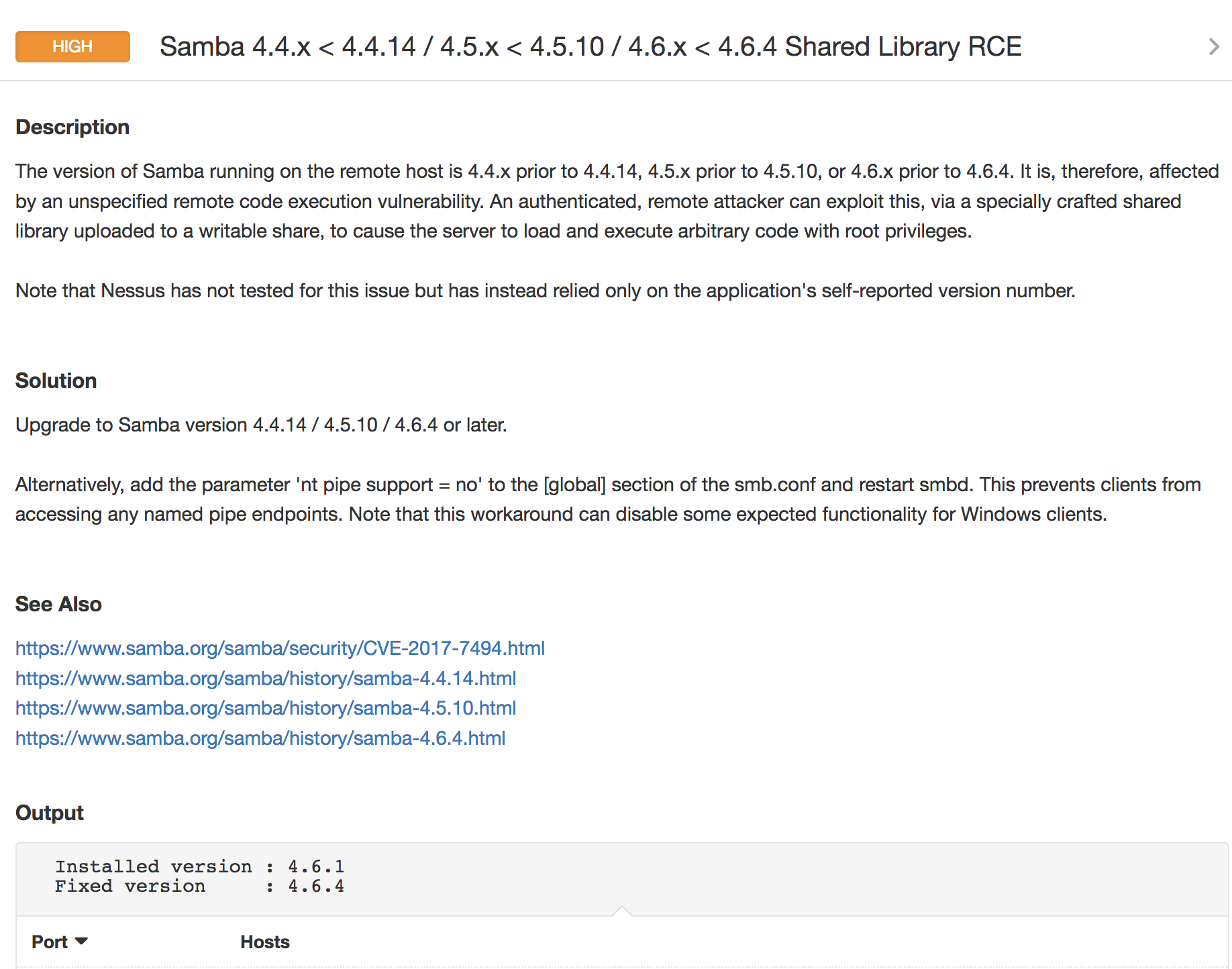
Tenable has released multiple credentialed Nessus® plugins to check for vulnerable Samba versions, and will continue to release more plugins as patches become available for other Linux distributions.
For example, here are results similar to what you might see after running plugin #100388 to detect vulnerable Samba versions:
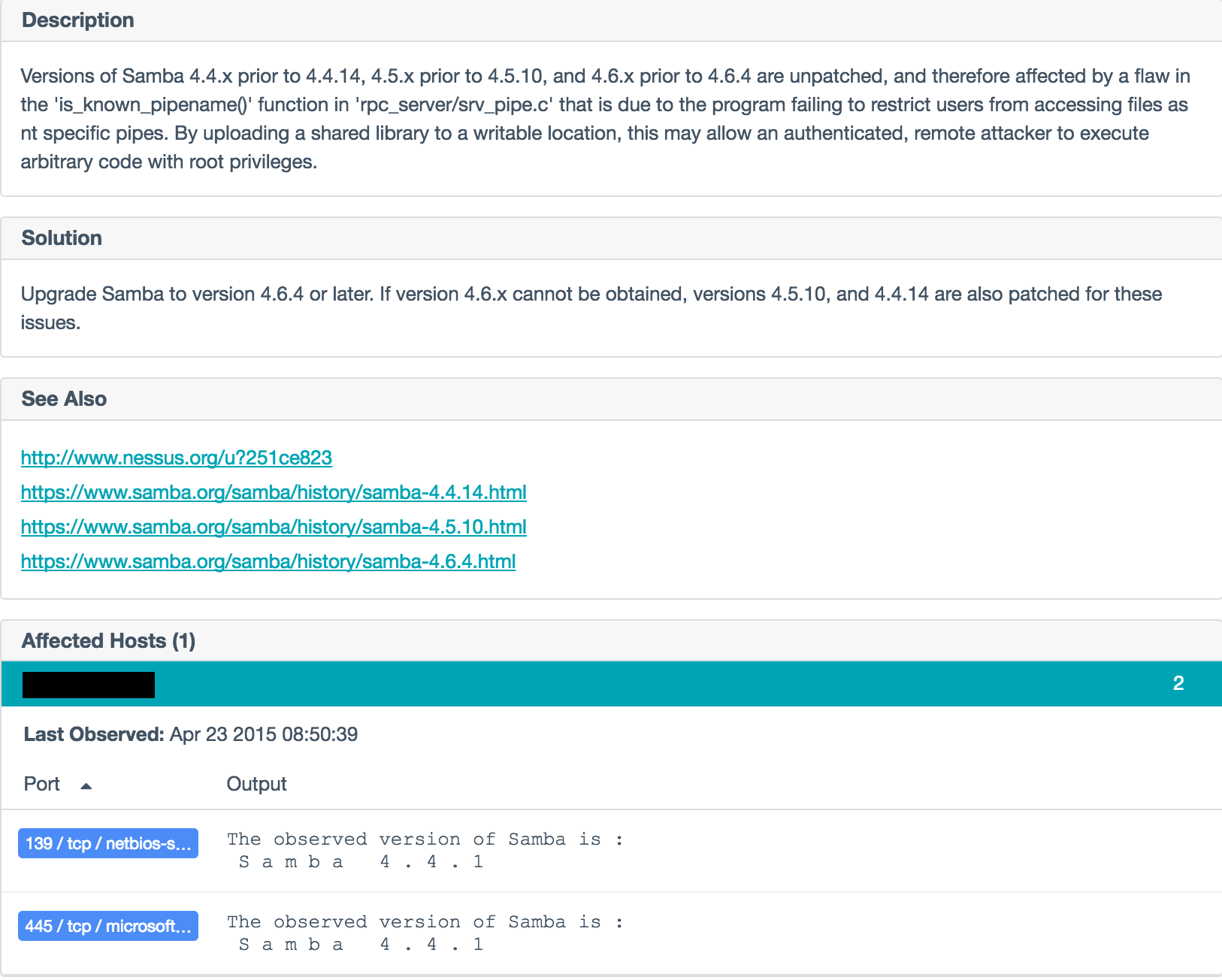
Tenable has also released a remote banner check to identify vulnerable Samba versions. The check only runs in paranoid mode because vendors have historically backported Samba patches and hence can result in false positives. Make sure that the following setting is checked when you create a new scan:
Settings > Assessment > General > Show Potential False Alarms
Next, check results for Nessus plugin 42411 to determine if there are any SMB shares which provide access to unprivileged users. If you find any instances, fix the permissions on those shares.
PVS
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
The Passive Vulnerability Scanner® (PVS™) is also capable of actively detecting vulnerable versions of SMB affected by SambaCry with plugin #700127.
SecurityCenter
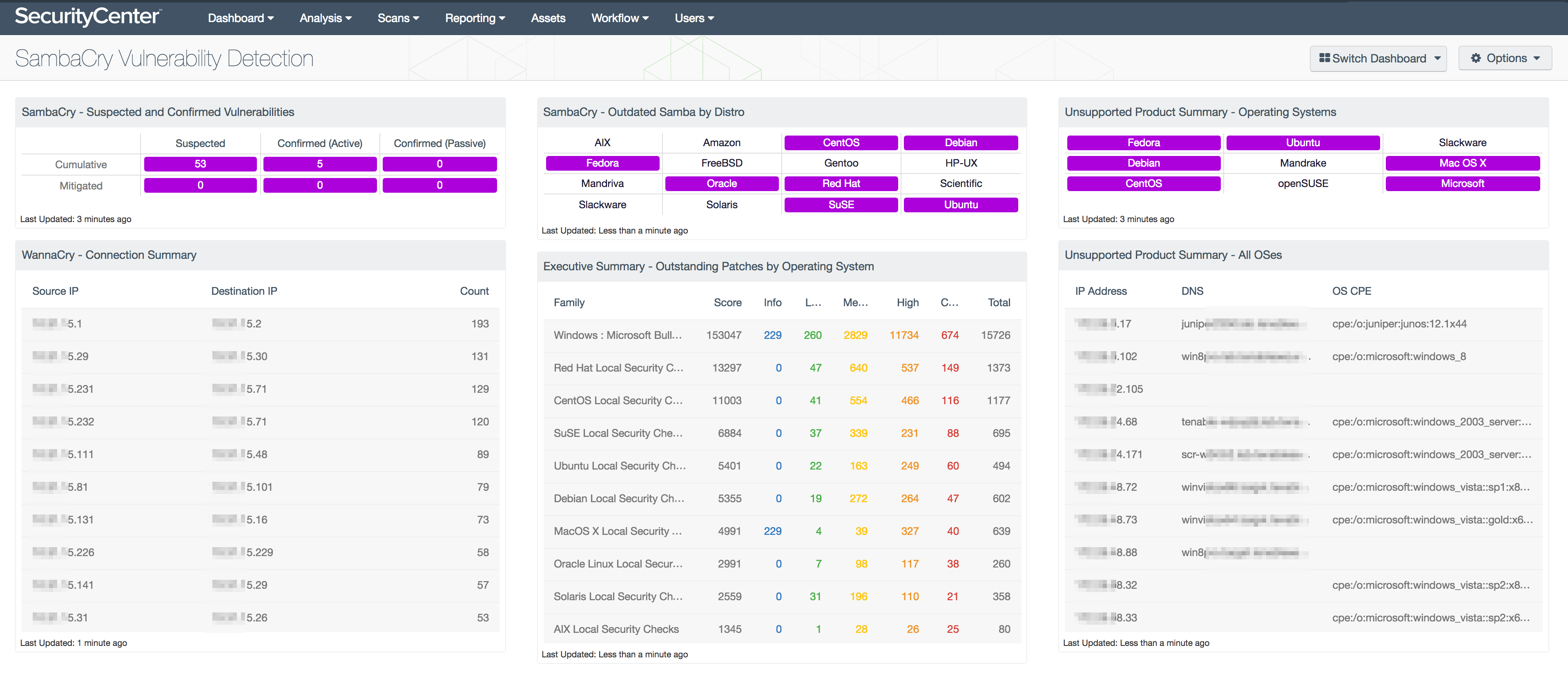
The SecurityCenter® SambaCry Vulnerability Detection dashboard is developed and tailored to identify Linux hosts that may be susceptible to the SambaCry vulnerability. The dashboard uses the methods of detection described in this blog and places them into an easy-to-use and understand location. The matrix in the upper left hand corner uses CVEs and plugin name strings to identify possible at-risk hosts vs. confirmed vulnerable hosts. The dashboard also uses many similar components used in the Detecting WannaCry and Eternal Rocks dashboard, and provides an overview of patching across all operating systems, to help you understand the current progress in patch deployments.
What if you can’t patch?
And finally, it's not possible to apply the patches, update smb.conf as a workaround. Add the parameter:
nt pipe support = no
to the [global] section of your smb.conf and restart smbd. This prevents clients from accessing any named pipe endpoints.
Note: This can disable some expected functionality for Windows clients.
Follow Tenable
Tenable strives to enhance visibility into your network systems and potential vulnerabilities, helping you proactively manage risk on a regular basis. Subscribe to the Tenable Blog as we share more tips and tools to add to your cyber arsenal.
Thanks to the Tenable research team for their contributions to this blog.
- Plugins
- Vulnerability Management
- Vulnerability Scanning