WannaCry 2.0: Detect and Patch EternalRocks Vulnerabilities Now

A new network worm dubbed EternalRocks is making the news this week as the successor to the WannaCry ransomware. EternalRocks leverages some of the same vulnerabilities and exploit tools as WannaCry but is potentially more dangerous because it exploits seven NSA tools that were released as part of the ShadowBrokers dump for infection instead of two used by WannaCry. So EternalRocks has the potential to spread faster and infect more systems. EternalRocks is currently dormant and isn’t doing anything nefarious such as encrypting hard drives. But EternalRocks could be easily weaponized in an instant, making the need for preventive action urgent.
Why EternalRocks may be bigger than WannaCry
WannaCry used only two of the SMB exploit tools: ETERNALBLUE and DOUBLEPULSAR. EternalRocks leverages seven NSA SMB exploit tools to locate vulnerable systems:
- ETERNALBLUE
- DOUBLEPULSAR
- ETERNALCHAMPION
- ETERNALROMANCE
- ETERNALSYNERGY
- SMBTOUCH
- ARCHITOUCH
EternalRocks does not have a kill-switch which helped curtail WannaCry and mitigate the ransomware damage.
The clock is ticking with EternalRocks; take advantage of the Tenable detection tools now before any damage is inflicted on your systems.
Tenable solutions
Nessus plugins for SMBv1 and MS17-010
All of the vulnerabilities exploited by the EternalRocks worm were patched by Microsoft earlier this year as part of MS17-010. Tenable released several Nessus plugins to look for unpatched systems or systems that could be vulnerable by having SMBv1 running.
| Plugin ID | Nessus Plugin | Description |
|---|---|---|
|
96982 |
Server Message Block (SMB) Protocol Version 1 Enabled (uncredentialed check) |
The system has been found to be vulnerable to SMBv1 attacks using uncredentialed checks. The Shadow Brokers group reportedly has an exploit that affects SMB, and the current WannaCry ransomware is using this exploit. |
|
97086 |
Server Message Block (SMB) Protocol Version 1 Enabled |
This plugin is similar to 96982, but the vulnerability is detected using credentials. The system has been confirmed vulnerable to SMBv1 attacks used by WannaCry and vulnerabilities described by Shadow Brokers. Credentialed checks are more accurate and provide mode details. |
|
97737 |
MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) |
Credentialed plugin to detect MS017-010 (detects the patch is missing) |
|
97833 |
MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (uncredentialed check) |
Remote plugin to detect the MS017-010 vulnerability |
|
99439 |
SMB Server DOUBLEPULSAR Backdoor / Implant Detection |
This uncredentialed plugin detects if the DOUBLEPULSAR implant exists on the remote Windows Host |
Malware detection plugin
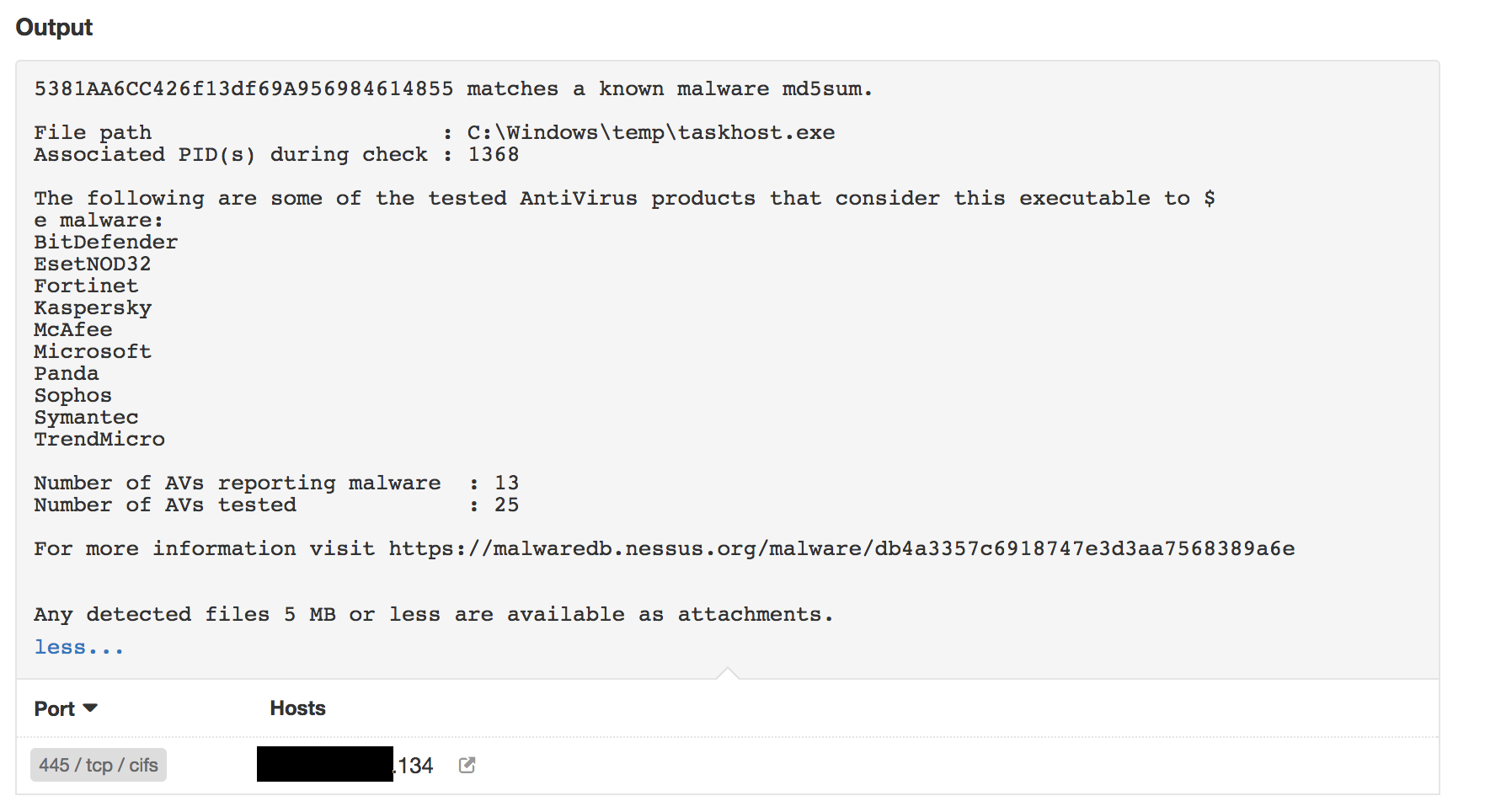
Tenable can also detect if the remote host is infected by EternalRocks worm through its malware detection plugin.
Here’s an example of an EternalRocks hash detected with the Malicious Process Detection plugin ID 59275:
Yara Detection
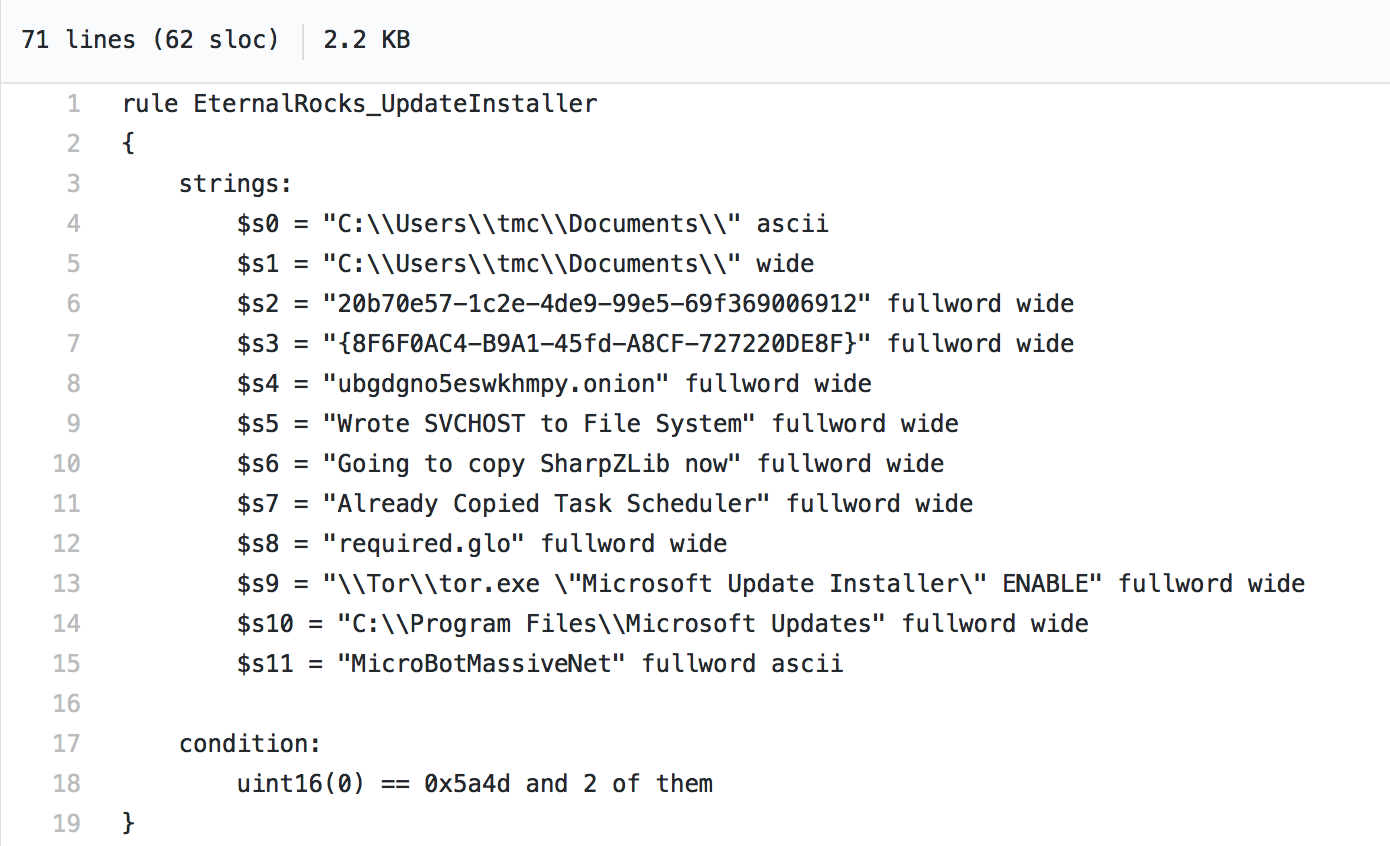
Tenable customers can also use YARA rules to identify infected systems through the Malicious File Detection Using Yara Nessus plugin.
Here’s a sample rule which can be used with Nessus to detect the EternalRocks worm:
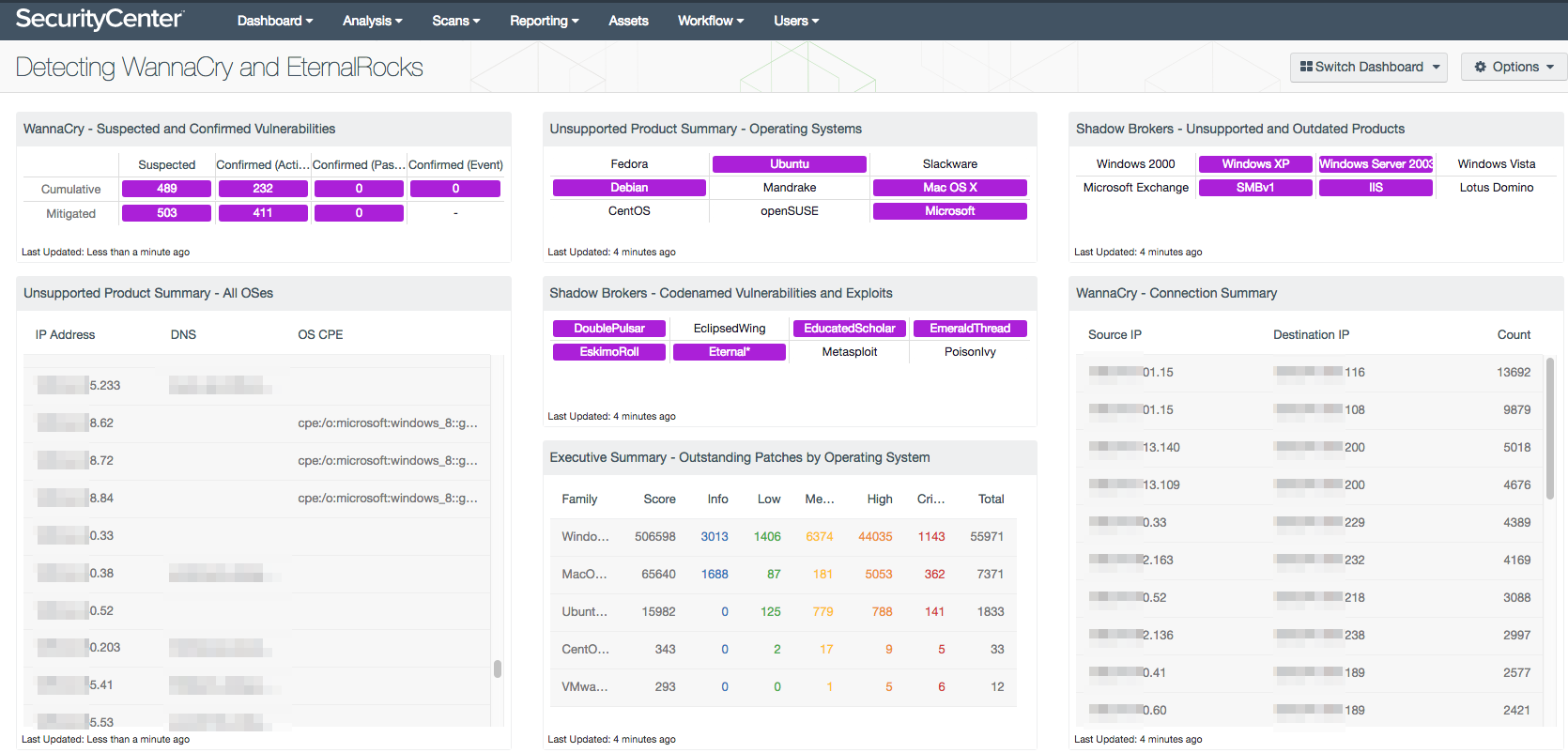
SecurityCenter dashboard
The WannaCry Vulnerability Detection dashboard has been updated to include information about EternalRocks. The filters did not require updating, so if you have the WannaCry Vulnerability Detection dashboard, you are all set. If you have not installed the previous dashboard, you can now download the Detecting WannaCry and EternalRocks dashboard.
Patch, don’t panic
We are fortunate to have some time to detect and patch EternalRocks vulnerabilities before they are exploited. There’s no need for a panic attack, but take time today to protect your systems.
If you don’t patch soon, there might be reason to panic later. One of the things EternalRocks does is that it leaves the DOUBLEPULSAR implant unprotected, which means other threat actors could leverage EternalRocks infected machines for their own intents and purposes.
Make it a habit to patch regularly and often. The single best thing you can do to protect your networks against malware attacks, worms and ransomware is to patch the known vulnerabilities; this is low-hanging fruit with a big return.
For more information
- What the Latest Shadow Brokers Dump Means for Your Business
- DOUBLEPULSAR Backdoor Detection with Nessus and PVS
- WannaCry? Three Actions You Can Take Right Now to Prevent Ransomware
- WannaCry? Patch or Protect
Many thanks to Tyler Coumbes, Cody Dumont and the Tenable research team for their contributions to this blog.
- Malware
- Plugins
- Vulnerability Scanning