Detecting Mr. Robot Malware

Season 2 Episode 5 of Mr. Robot starts with Elliot preparing a malicious payload delivery system that we later find out is a femtocell. The goal is to create a Man in the Middle (MitM) attack vector using the femtocell. A femtocell “is a small, low-power cellular base station, typically designed for use in a home or small business” (Wikipedia). The idea is to create a small device that can be battery operated or powered using Power over Ethernet (PoE) and placed as a malicious cell tower in E Corp on the floor where the FBI agents are investigating the breach. Mobile devices, such as the FBI Android phones, periodically check for updates from a centralized update service, and this service delivers Android Application Package (APK) files. Elliot’s goal is to deploy a MitM device that will send the malware package instead. For example, Elliot could use a tool like Evilgrade to perform such an attack (we aren’t sure what tool Elliot is using during his attack). From this point, there would be a post exploit, and the malware would dial home and request a list of post exploitation activities. Once Elliot comprises several FBI or E Corp Android devices, he will have access to stored credentials and other data. With stored credentials, Elliot will have root, admin, or God level access, which Elliot describes as the thrill of PWNING a system.
Do you think you could detect the malicious activity and malware in these 5 steps described in this episode?
Step 1 - Identify the target and its flaws
As Elliot describes his plan to infiltrate the FBI, he says the first step is to identify the targets and flaws or vulnerabilities in the target system. While Elliot does not go into details about how he identified the target, he has identified the most common mobile device supposedly used by the FBI. Many adversaries use software to sniff the airwaves and detect user-agent strings, or may use network scanning methods to identify systems based on open ports and other behaviors.
Using SecurityCenter Continuous View™ (SecurityCenter CV™) and sending all the logs from firewalls, IDS, and other systems, the Tenable Log Correlation Engine™ (LCE®) can easily identify scanning activities. LCE uses advanced correlation technology to identify network probing activity for all available log sources.
Step 2 - Build malware and prepare the attack
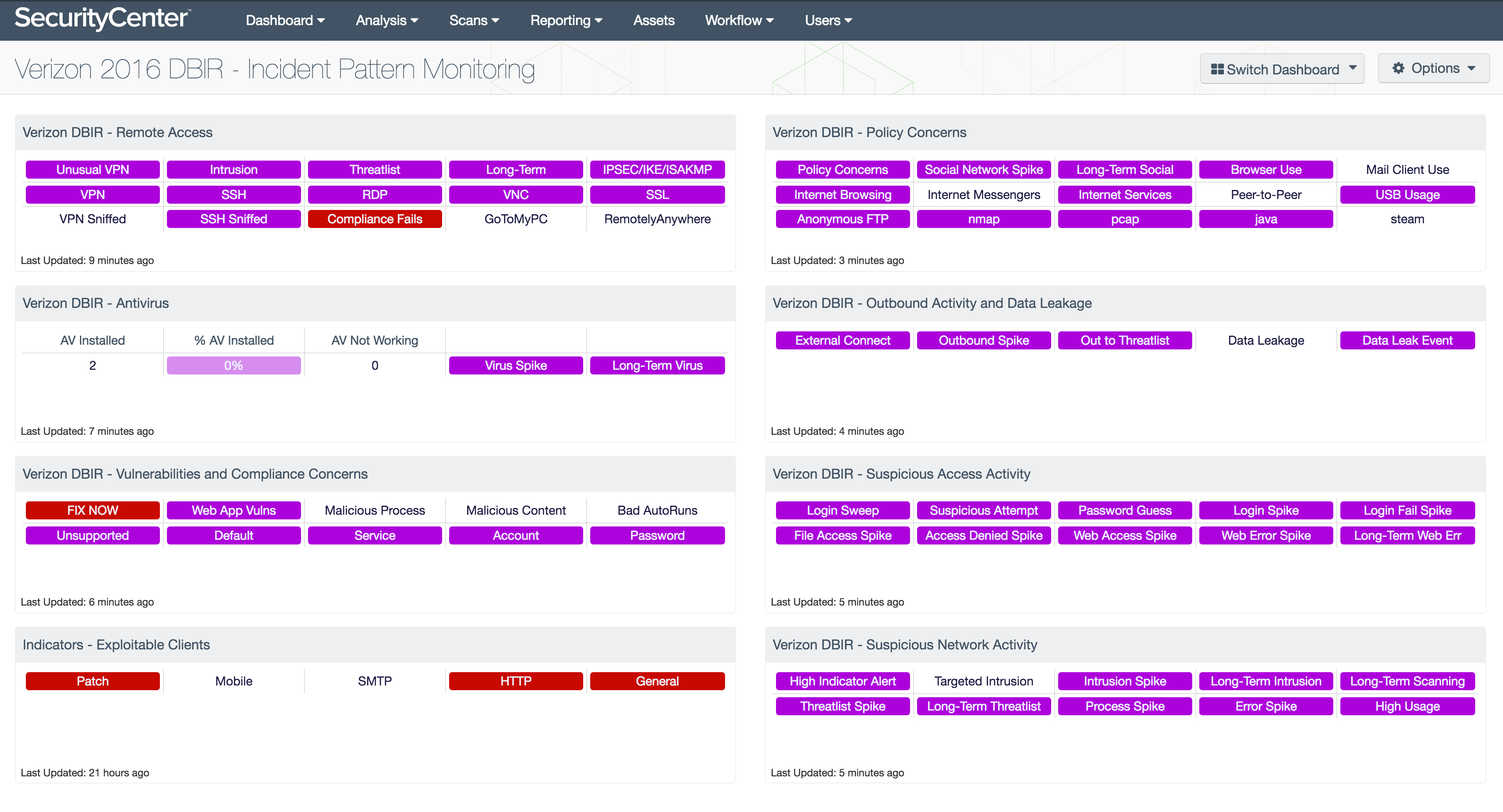
Custom built malware can be difficult to identify using traditional methods; Tenable uses more advanced and behavior methods. For example, Nessus® supports several plugins that monitor AutoRuns, running processes, and other forensic indicators of malware. When used with SecurityCenter CV, the Passive Vulnerability Scanner™ (PVS™) and LCE can also detect anomalous traffic patterns and Never Before Seen (NBS) events. Gaining an understanding of your network is key to learning when anomalies occur, and the Verizon 2016 DBIR - Incident Pattern Monitoring dashboard in SecurityCenter CV provides a series of indicators when this activity is prevalent.
Step 3 - Load malware into the delivery system
While there are several steps included in Elliot’s step 3 (reverse shell, two stage exploit, the delivery system), the key point is to deliver the femtocell, exploit the targeted phones, and then pivot from the phone and attack the network. This third step can be the hardest for an attacker to be successful at. In Season 1, delivery systems included USB flash drives and a CD disguised as a music disk - easier to deliver. But in this season, the 23rd floor is locked down and physical access is tight. How can they gain access? Elliot and Darlene must use an insider: Angela.
Using the Insider Threat Dashboard, SecurityCenter uses can embrace all input sources to identify malicious insider activity. Additionally, detecting new devices on the network is a key defense to this threat vector; the CIS CSC: Devices and Ports (CSC 1,9) dashboard provides users with a great view into new device activity. These dashboards and many others provide your security operations team with clear insights for identifying new threats to the network.
Steps 4 & 5 - Write the script and launch the attack
Elliot understands that to truly gain access to systems, his malware must launch a stable and reliable script to send credentials and other critical information to allow further penetration. Episode 5 does not provide enough information about the success of the attack, but we can be sure the scripts are ready to cause havoc for the FBI and E Corp.
SecurityCenter CV provides a highly effective solution to help identify and track malicious activity. Customers have the ability to identify threats using data collected from several sensors: Active Scanning, Intelligent Connectors, Agent Scanning, Passive Listening, and Host Data. By looking into all available data, your organization can go a long way towards detecting each of Elliot’s steps to a penetration. Can your security program detect all 5 steps?
- Malware
- SecurityCenter