by David Schwalenberg
March 10, 2015
Insiders are those users – be they employees, contractors, or partners – that already have access to your organization's network and resources. The threat is that these insiders may either accidentally or intentionally do something to harm the network, compromise resources, or leak private data. Insider threats are different from external security threats in that they come from what would normally be considered a "trusted source." Organizations trying to detect these threats face the challenge not only of differentiating attacks from "normal" traffic, but also of ensuring that security analysts and system administrators are not inundated with false positives from users performing legitimate tasks.
Identifying and combating the insider threat is difficult to do solely through technical means. Much of current network security is focused on keeping bad guys out, not dealing with the people already inside making mistakes or acting maliciously. The best an organization can usually do is train their employees in security, keep them happy, and monitor for suspicious and anomalous activity.
This dashboard brings together passive scanning and log correlation to assist with this aspect of monitoring users on the network. The dashboard presents information on user login activity and system and resource access activity. It is important to note that this dashboard does not provide definite detections of insider threats, but only potential indicators and information that will need to be manually reviewed. The analyst can use this information to combat the insider threat by verifying whether users are authorized to have a presence on the systems they are on, and whether they are authorized to access the resources that they are accessing.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring.
The dashboard requirements are:
- SecurityCenter 4.8.2
- PVS 4.0.3
- LCE 4.4.1
Tenable's SecurityCenter Continuous View (SecurityCenter CV) is the market-defining continuous network monitoring platform. SecurityCenter CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Passive Vulnerability Scanner (PVS), as well as log correlation with Tenable's Log Correlation Engine (LCE). Using SecurityCenter CV, an organization will obtain the most comprehensive and integrated view of its network.
Listed below are the included components:
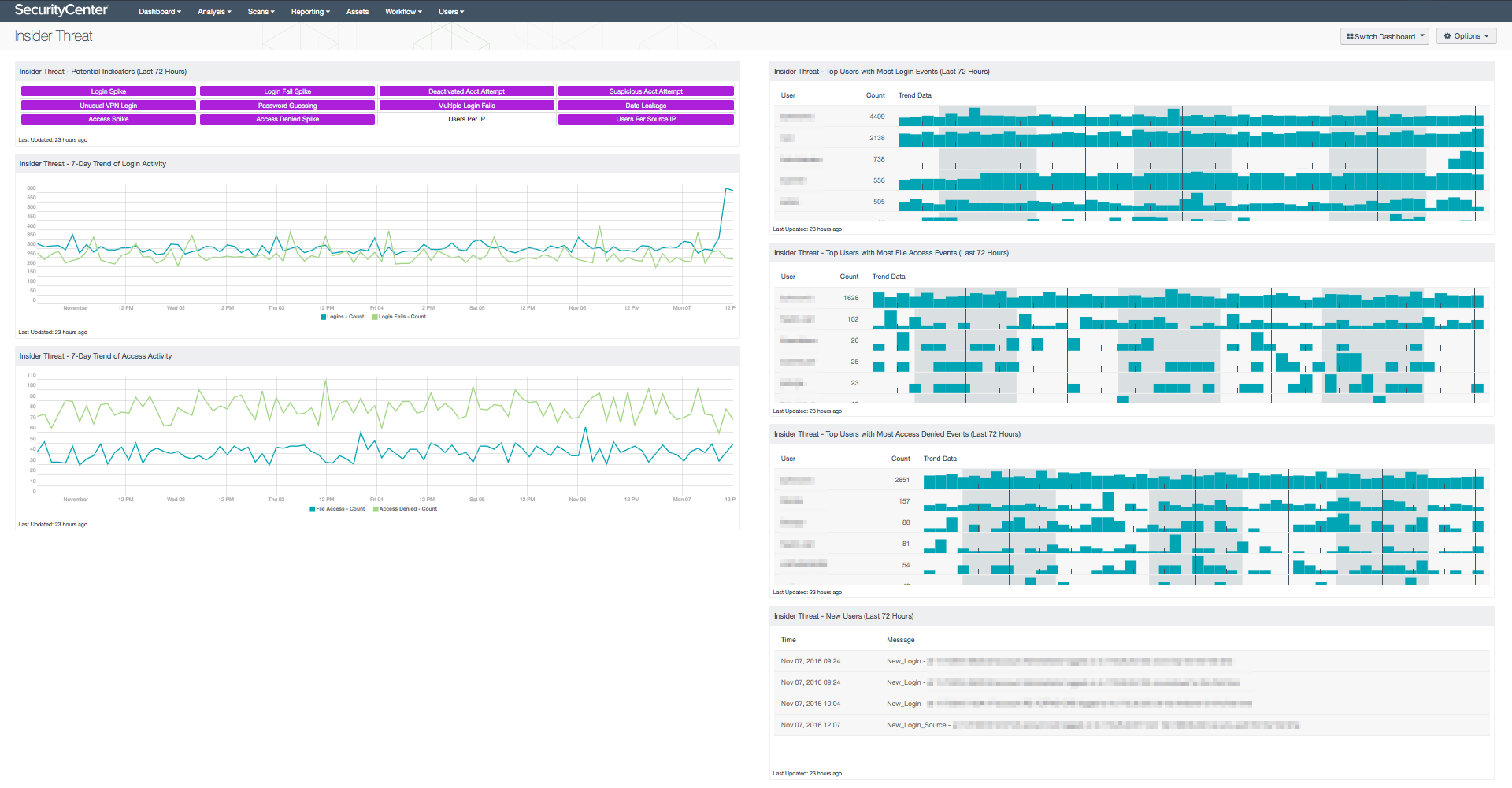
- Insider Threat - Potential Indicators (Last 72 Hours) - This matrix presents potential indicators of insider activity in the last 72 hours. These indicators include spikes in login and login failure activity, attempts to login to deactivated or suspicious accounts (such as default accounts), unusual VPN logins, password guessing, and multiple login failures. Indicators are also included for data leakage events, and spikes in file access and access denied activity. A purple indicator means that events in that area were detected; clicking on the indicator will bring up the analysis screen. In the analysis screen, setting the tool to Raw Syslog Events will display more information on the events. If needed, the final two indicators can be used to determine all users logged into the network per IP address, and all users that logged into other machines from each IP address (this will be a lot of data to look through!). Clicking on the indicators will bring up the analysis screen, and setting the tool to Detailed Vulnerability List will display the user information. Note the First Discovered and Last Observed timestamps to determine when the listed users were active.
- Insider Threat - 7-Day Trend of Login Activity - This chart presents a 7-day trend of counts of login and login failure events. These events are reported by LCE under the "login" and "login-failure" event types, respectively, and include events forwarded via syslog from PVS. Excessive login activity will display as spikes in the graphs. Any spikes should be further investigated, as they may represent someone on the network (an insider) attempting to gain access to systems and resources.
- Insider Threat - 7-Day Trend of Access Activity - This chart presents a 7-day trend of counts of file access and access denied events. These events are reported by LCE under the "file-access" and "access-denied" event types, respectively, and include events forwarded via syslog from PVS. Excessive access activity will display as spikes in the graphs. Any spikes should be further investigated, as they may represent someone on the network (an insider) attempting to gain access to systems and resources.
- Insider Threat - Top Users with Most Login Events (Last 72 Hours) - This table presents the top user accounts with the most login events in the last 72 hours. These events are reported by LCE under the "login" event type, and include events forwarded via syslog from PVS. A count of events and a trend graph is given for each user account. The listed users should be verified as being authorized to login. The list is ordered so that the user account with the most login events is at the top. Note that the top user accounts will likely be system accounts. Also, note that a stealthy insider may login to systems and resources relatively infrequently, so it may be worthwhile to edit the component and change the Sort Direction to "Ascending" so that the users who logged in the least number of times are shown.
- Insider Threat - Top Users with Most File Access Events (Last 72 Hours) - This table presents the top user accounts with the most file access events in the last 72 hours. These events are reported by LCE under the "file-access" event type, and include events forwarded via syslog from PVS. A count of events and a trend graph is given for each user account. The listed users should be verified as being authorized to access the resources they are accessing. The list is ordered so that the user account with the most file access events is at the top. Note that the top user accounts will likely be system accounts. Also, note that a stealthy insider may access resources relatively infrequently, so it may be worthwhile to edit the component and change the Sort Direction to "Ascending" so that the users who accessed resources the least number of times are shown.
- Insider Threat - Top Users with Most Access Denied Events (Last 72 Hours) - This table presents the top user accounts with the most access denied events in the last 72 hours. These events are reported by LCE under the "access-denied" event type, and include events forwarded via syslog from PVS. A count of events and a trend graph is given for each user account. The listed users should be checked to make sure there are no suspicious users or malicious access attempts. The list is ordered so that the user account with the most access denied events is at the top. Note that the top user accounts will likely be system accounts. Also, note that a stealthy insider may attempt to access resources relatively infrequently, so it may be worthwhile to edit the component and change the Sort Direction to "Ascending" so that the users who attempted to access resources the least number of times are shown.
- Insider Threat - New Users (Last 72 Hours) - This table presents new user events recorded in the last 72 hours. The raw syslog of the event is given, displaying the event, the user account, and the host IP address. The "New network user" event records the first time a user is ever seen on the network. The "New_User" event records the first time a user logs in to a new host and/or a new account type on a host. The "New_User_Source" event records the first time a user logs in from a new host. All of these new users should be verified as authorized to be on the network and accessing the systems that they are accessing.