CVE-2021-20019: SonicWall Fixes Incomplete Patch for CVE-2020-5135

SonicWall issues a new advisory and CVE identifier to address an incomplete fix for CVE-2020-5135.
Background
On June 22, SonicWall published an advisory (SNWLID-2021-0006) to address an incomplete fix for a vulnerability in its operating system, SonicOS, used in a variety of SonicWall network security devices, including its SSL VPNs. This advisory contains a newly assigned CVE identifier; the original vulnerability was CVE-2020-5135.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2021-20019 | SonicOS Buffer Overflow Vulnerability (Partial Memory Leak) | 5.3 |
Discovery of the vulnerability is credited to Craig Young of Tripwire’s Vulnerability and Exposure Research Team (VERT). According to Young, this advisory addresses an “unsuccessful” fix for CVE-2020-5135, a critical vulnerability that was patched in October 2020. Young was one of the researchers credited with the original discovery of CVE-2020-5135.
Analysis
CVE-2021-20019 is a buffer overflow vulnerability in SonicWall’s SonicOS. A remote, unauthenticated attacker could exploit the flaw by sending a specially crafted HTTP request to a vulnerable SonicWall device. Successful exploitation of this vulnerability would result in a partial memory leak, disclosing sensitive internal information to the attacker. In a blog post, Young says that the information disclosed could include memory addresses that would be “useful information” for “exploiting an RCE bug.” For more technical details, please refer to Young’s blog post.
Over 680,000 SonicWall devices remain publicly accessible
In our previous blog post about CVE-2020-5135, we highlighted that there were nearly 800,000 SonicWall devices publicly accessible based on results from two separate Shodan queries.
Reviewing those same queries today, we see that there are still over 680,000 SonicWall devices that remain publicly accessible, more than seven months after the initial disclosure of CVE-2020-5135.
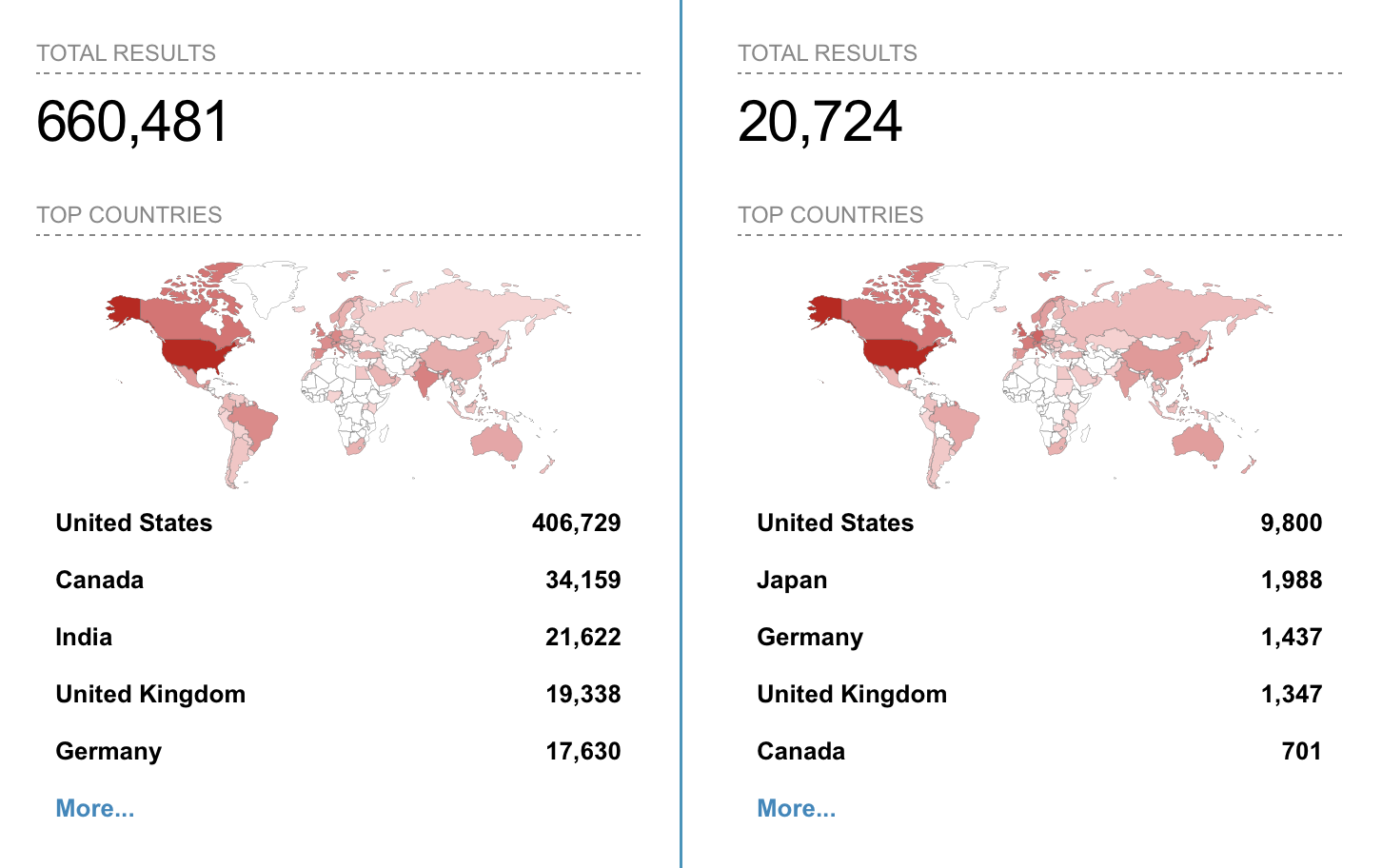
As a word of caution, Tenable’s Security Response Team cannot independently confirm that all of the hosts publicly accessible via these Shodan search results are impacted by CVE-2021-20019. The intention behind highlighting the number of publicly accessible hosts is to provide context for the potential attack surface for threat actors.
A reminder that remote access vulnerabilities are a valuable tool in attacker playbooks
As we highlighted in our 2020 Threat Landscape Retrospective report, three of the top five vulnerabilities from last year were SSL VPN flaws. In 2021, we’ve seen remote access product flaws remain a valuable tool in attacker playbooks, including CVE-2021-20016, a zero-day vulnerability in SonicWall’s Secure Mobile Access (SMA) devices that was exploited in the wild earlier this year.
If your organization uses SonicWall devices, including their SSL VPN, we strongly recommend you apply these patches as soon as possible.
Proof of concept
At the time this blog post was published, there were no publicly available proof-of-concept (PoC) exploits for CVE-2021-20019, aside from Young’s own private PoC.
Solution
SonicWall has patched CVE-2021-20019 across several versions of SonicOS, though at the time this blog post was published, two versions did not have a fix available yet. We will update the table below once those fixes become available.
| Affected Version | Fixed Version |
|---|---|
| SonicOS 6.0.5.3-94o and below | Unavailable (Pending) |
| SonicOS 6.5.1.12-3n and below | Unavailable (Pending) |
| SonicOSv 6.5.4.4-44v-21-955 and below | SonicOS 6.5.4.4-44v-21-1288 |
| SonicOS 6.5.4.7-83n* and below | SonicOS 6.5.4.8-89n |
| SonicOS 7.0.0-R713 and below | SonicOS 7.0.0-R906 and above SonicOS 7.0.1-R1456 |
| SonicOS 7.0.1-R1036 and below | SonicOS 7.0.1-R1282/1283 |
| SonicOS 7.0.0.376 and below | SonicOS 7.0.0.376 and above SonicOS 7.0.1-R579 |
* In its advisory, SonicWall lists SonicOS 6.5.4.7-83 and below as affected, but in the table of Fixed Software, they list 6.5.4.8-83 and below as affected, creating a discrepancy.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- Analyzing SonicWall’s Unsuccessful Fix for CVE-2020-5135
- Tenable Blog Post for CVE-2020-5135
- SonicWall Advisory for CVE-2021-20019 (SNWLID-2021-0006)
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


