Auditing Microsoft Azure with Nessus v6.5

Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
“I want to audit the cloud,” said a visitor to the Tenable booth at a recent conference.
“Which cloud? There are several,” I asked.
“The one with clear blue skies” he said with a wink.
“Ah, you mean Microsoft Azure,” I replied.
“Yes, that’s the one!”
For customers who have asked us to support Microsoft Azure, Nessus® v6.5 now supports auditing Microsoft Azure. In fact, Nessus is the first and only solution to offer security visibility, system hardening and auditing for Microsoft Azure. More and more customers want to audit their cloud systems and applications. And why not? Migrating workloads to the cloud doesn’t absolve organizations of their responsibility to secure what’s in the cloud.
There are many “clouds” (read cloud services) to choose from. But the three cloud services that keep popping up in our conversations are Amazon AWS, Rackspace, and Microsoft Azure. With the release of v6.5, Nessus can now audit them all.
Nessus can now audit Amazon AWS, Rackspace, and Microsoft Azure
But how do you secure something which you don’t have physical control over? In general when it comes to securing the cloud, most cloud providers advocate the shared responsibility model: the provider is responsible for the security of the cloud, and the customer is responsible for what’s deployed in the cloud.
Application Programming Interfaces, or APIs from each cloud provider, are a big help when it comes to securing what’s deployed in the cloud. And in our increasingly API-enabled world, Nessus is now able to audit your Microsoft Azure account(s) through the Microsoft APIs.
Setup
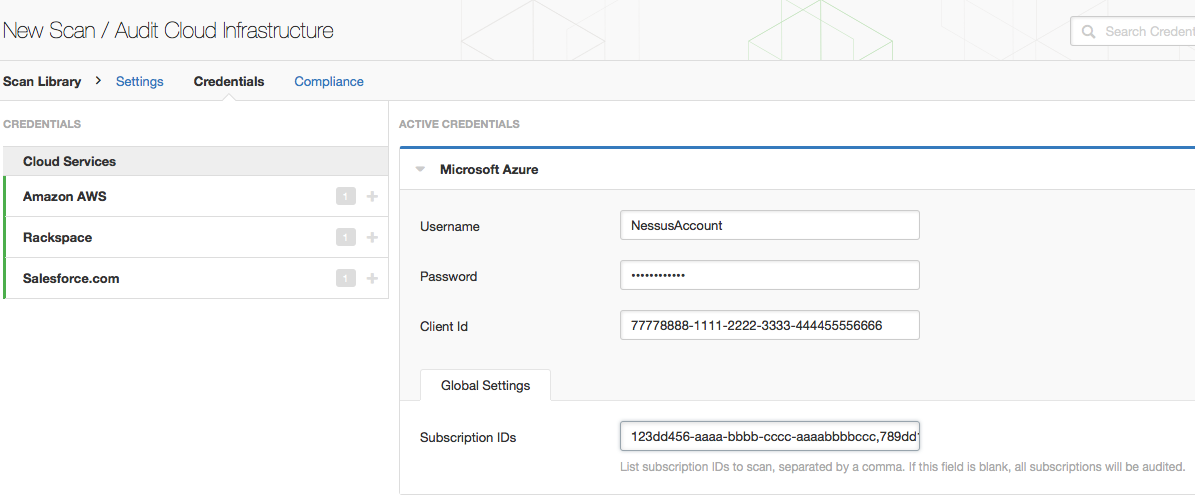
Setting up access for Nessus to audit Microsoft Azure is straightforward. To accurately audit a Microsoft Azure account, Nessus needs these details:
- Username
- Password
- Client-Id and optional Subscription IDs
All these fields can be configured via the Audit Cloud Infrastructure template:
Username and Password
This is the username and password to access your Microsoft Azure Account.
Client Id
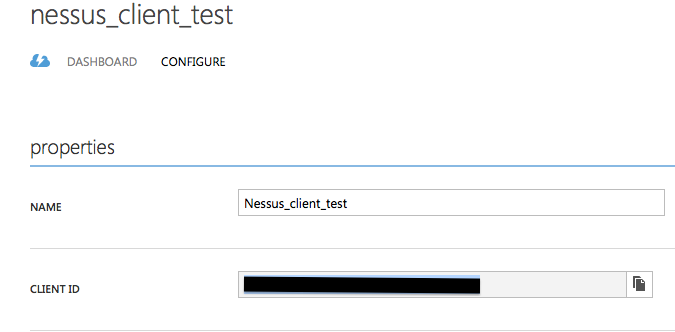
For Nessus to audit your Microsoft Azure account, you must define an app in your Azure account. Once you define the app, a client-id will be automatically generated by Microsoft Azure for the app, which you can then copy into your Nessus scan policy.
Steps to create a Client Id
- Navigate to your Microsoft Azure Account
- Navigate to Active Directory -> Applications tab -> Add -> Add an application my organization is developing
- Provide the app a name, and select Native client application
- Provide a redirect URL (for example, http://example.com)
- Configure the app, give it necessary permissions (Access Azure Service Management), and then copy the client-id to your Nessus scan policy:
Subscription IDs
This field is optional. By default (left blank), all subscriptions to which your account has access will be audited. But if you want to restrict the audit to a subset of subscriptions, you can list each subscription that needs to be audited, separated by commas. This is useful if you want to run an audit against each subscription and share the results with different teams.
What’s audited by Nessus?
In general, when it comes to auditing cloud services such as Microsoft Azure, our approach has been simple: go above and beyond the usual best practice guidelines. This has twin benefits for our customers. First, it obviously helps you to securely configure cloud services. And second, it provides visibility into what is deployed in the cloud. For example, which VMs are running, what is their status, what privileges does each user have, and so forth. In short, it provides you with a deployment snapshot of your Microsoft Azure account.
And we have done just that with Microsoft Azure. We are shipping three distinct audits in Nessus v6.5, each catering to a specific use case:
Infrastructure audit
The infrastructure audit checks the following items:
- Virtual machines
- Running/Stopped/Deallocated VMs/Public IPs used
- Certificates
- Certificates in use/expiring soon/recently used
- Azure deployment snapshot
- Provides details of all resources deployed in your account
- User account(s) review
- Accounts with admin level privileges
- Subscription(s) review
- Enabled/Disabled subscriptions
Website audit
- Websites that are enabled/disabled
- Websites without SSL turned on
Database
- Event logging configuration review
- User account review
- Admin/Non-admin users
- Stopped/Running databases
- Firewall rules for databases
Additional capabilities
Of course, auditing the cloud environment is the first step to improving the security posture of your Azure cloud deployments. You’ll also want to obtain further insight into systems that are vulnerable, understand which are compromised by malware, as well as which are out of compliance. Tenable offers flexible options to support each of these needs. For example, Nessus Agents, software programs installed on Azure virtual machines, offer in-depth local scans to identify vulnerabilities on that system as well as detect malicious processes running on it. The agent results are sent to Nessus Manager or Nessus Cloud. Tenable customers can also import the Nessus Cloud and Nessus Manager results into SecurityCenter™ for a centralized view of scan results from on-premises and cloud deployments. To learn more about the full spectrum of options available for securing your Azure deployments, visit the Azure section of the Tenable Integrations website.
Final thoughts
With support for Microsoft Azure, Nessus now provides support for all three major cloud services: Amazon AWS, Rackspace and Azure. And if you have ever experimented with any cloud services, you are probably aware that each service supports their own range of services. It’s no different when it comes to Azure. For our initial release, we are shipping these three audits with checks for infrastructure, website and databases; we will provide support for more Azure services as needed.
For more information, visit our Azure Integration page.
- Cloud
- Nessus