Nessus Amazon AWS Auditing Now Available
Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
The transition to cloud services is well underway, bringing with it traditional and new security challenges. Nessus is evolving to address these challenges. Unlike traditional environments, cloud services require a modified approach to scanning - users can't simply point their scanners to services such as Amazon AWS, and not expect to be throttled, if not outright blocked.
Today we are happy to announce Nessus support for auditing Amazon AWS infrastructure. This new capability in Nessus® includes a compliance plugin and a .audit file that leverages the AWS API.
What We Are Auditing
Our goal with this feature is to provide a snapshot of the AWS infrastructure at a given point of time. Information such as running instances, network ACL's, firewall configurations, account attributes, user listing, and so on are pulled back from AWS to provide this snapshot.
The .audit itself is based on AWS Security Best Practices and IAM Best Practices guides from Amazon.
Steps to Run the Scan
The Amazon AWS scan differs from a typical Nessus scan in one major way: it doesn't have any targets. Since AWS is a Web Service, all we need are Access keys to your AWS account. To run a scan, select the new Amazon AWS wizard as shown below and follow the steps to configure the scan.
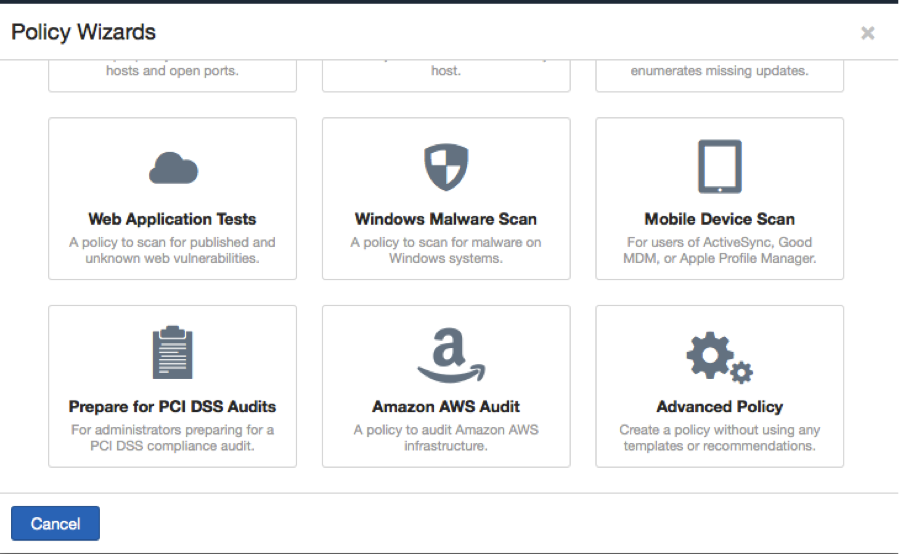
A majority of the checks are focused on gathering information that would be helpful in a manual review. Nessus users familiar with its configuration and compliance auditing capabilities can certainly use the usual compliance testing keywords such as regex/expect/not_expect to fulfill their compliance and auditing needs. In addition to that, starting with the Amazon AWS plugin, we are introducing a new feature that would allow users to compare the output of a check against a "known_good" value. If the value doesn't match, it will produce a diff style report (patience diff, specifically) on what changed. Users can also specify more than one known_good values. This feature is extremely useful to create a gold standard audit for your AWS infrastructure.
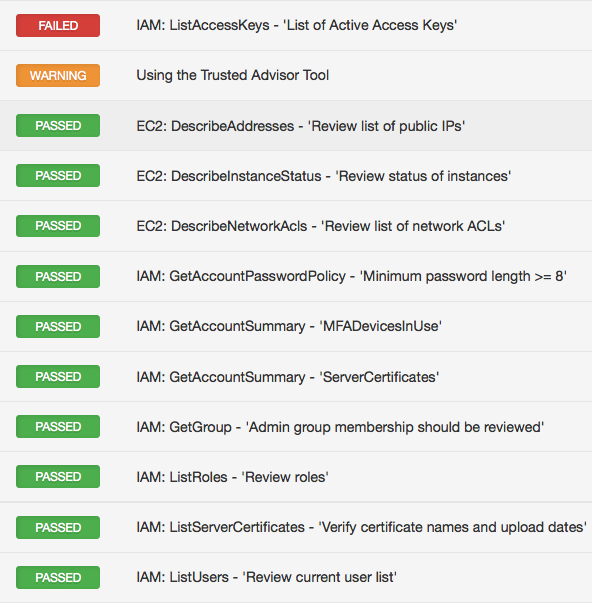
Below is a list of warnings, failed checks, and passed checks from an Amazon AWS audit scan.
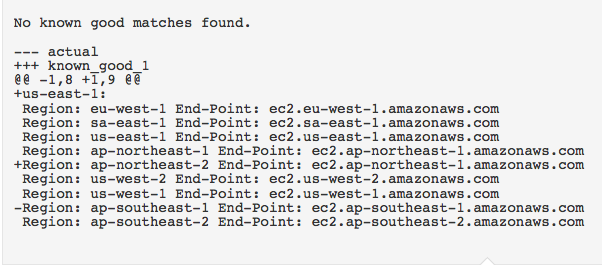
The image below shows the report when the actual value is different from the known_good value.
Final Thoughts
If you have settled on Nessus as your primary scanning platform for on-premises devices and services, it is now possible to leverage it to scan your external services as well. As cloud services become more prevalent, Nessus will evolve accordingly and account for more such services going forward. If you are not a Nessus user already, then features such as these are additional evidence that Nessus is one of the most forward-looking platforms, and you should give it a second look.
I welcome comments and feedback on this discussion of Amazon AWS integration in Nessus.
Thanks to Paul Asadoorian for edits and contributions.
- Cloud
- Nessus
- Plugins

