by Cesar Navas
April 23, 2024
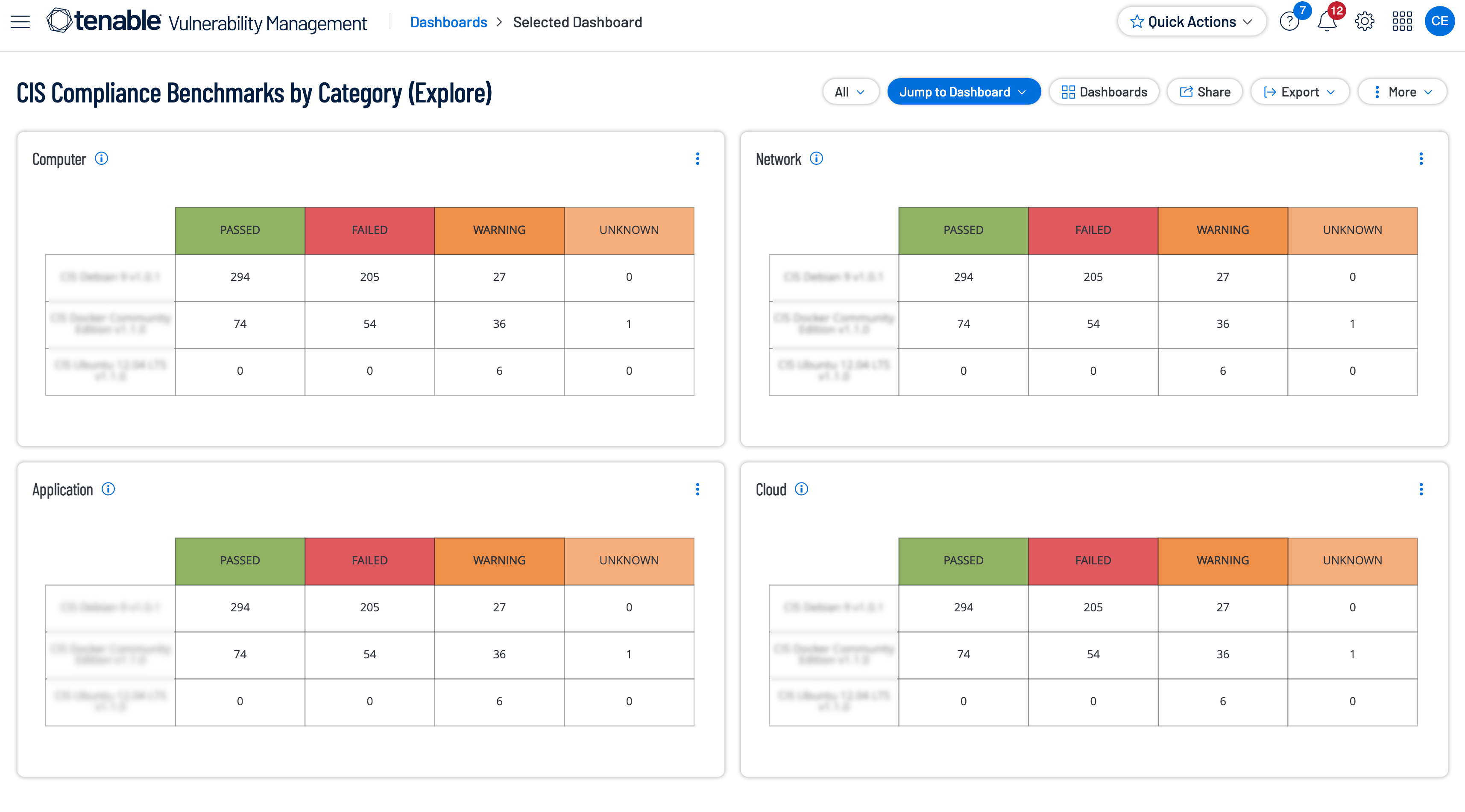
As networks continue to become increasingly complex and interconnected, many organizations struggle to maintain a secure enterprise. Even the most complex networks are still subject to vulnerabilities and attacks, if left unmanaged, the vulnerabilties can have devastating consequences for an organization. The Center for Internet Security (CIS) is an organization that works with security experts to develop a set of best practice security standards designed to harden operating systems and applications. This dashboard provides a high-level overview of results gathered from CIS compliance scans using the benchmarks.
Tenable has been certified by CIS to perform a wide variety of platform and application audits based on the best practice consensus benchmarks developed by CIS. Tenable submits example test cases for all of the criteria within each unique benchmark, and then submits our results to CIS personnel for official certification. When performing managed scans with Tenable Vulnerability Management, some CIS audits require additional patch audits and vulnerability checks. Any additional requirements for completing an audit is included within the audit file description text. In some cases, multiple scans may be required to be performed.
Tenable provides both Level 1 and Level 2 audit checks. Level 1 checks provide minimum setting recommendations, and are generally considered safe to apply to most systems. Level 2 checks include recommendations for complex or highly secure environments, and can lead to reduced functionality of key systems or applications. CIS compliance results have been broken down into four categories (Application, Computer, Cloud, and Network). This dashboard contains widgets which display information on CIS compliance benchmarks for all four Categories.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management (formerly Tenable.io) discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable Vulnerability Management.
Widgets:
- Computer: This widget reports on CIS compliance benchmarks for the following computer groups: Windows, Unix, Windows File Contents, Unix File Contents, Generic SSH, RHEV, OpenShift Container Platform, Zoom, and Mobile Device Manager.
- Network: This widget displays the results grouped by the Network related benchmarks.
- Application: This widget reports on CIS compliance benchmarks for the following application groups: Database, MongoDB, PostgreSQL DB, MySQL DB, Oracle DB, MS SQL DB, IBM DB2 DB, Sybase DB, and IBM iSeries.
- Cloud: This widget reports on CIS compliance benchmarks for the following cloud groups: Amazon AWS, Salesforce.com, Rackspace, Microsoft Azure, Office 365, Google Cloud Platform, and Splunk.