Synopsis
Tenable Research has identified and responsibly disclosed a critical SQL injection vulnerability in Looker Studio. Through the custom query feature, this vulnerability allows an attacker to execute arbitrary SQL queries on a victim's Spanner or BigQuery data sources.
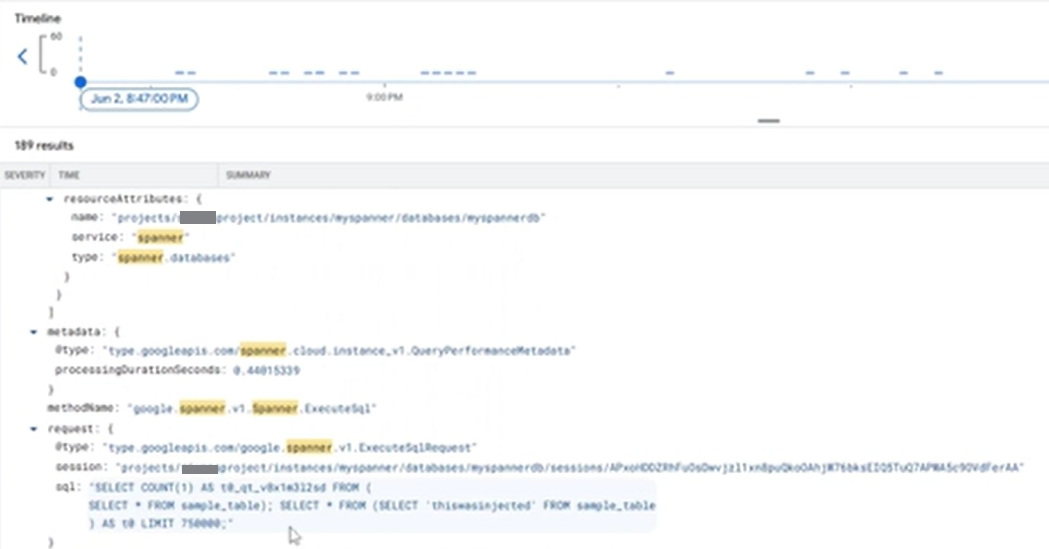
The vulnerability exploits a flaw in how Looker Studio validates a user's access to a data source. An attacker could bypass the access check by initially connecting to their own data source, which would return a successful getColumns request. By intercepting and modifying subsequent HTTP requests (createBlockDatasource and publishDatasource), the attacker could swap out their project details and replace them with the victim's, while also embedding a malicious custom SQL query.
This malicious report could then be shared with the victim. When the victim viewed the report, the pre-injected SQL query would execute on their data source under their user context, granting the attacker the ability to exfiltrate, insert, or delete all data the victim had access to. This effectively bypasses the single-statement limitation of custom queries and allows for a full compromise of the victim's data with a single action.
Proof of Concept
Set up a mock data source for the getColumns HTTP request:
- Create a Spanner instance and a db, for example, we will name the instance “attackerspanner” and the db “attackerdb”. Alternatively, just choose a public Spanner table of your choice.
Set up the attacker’s report:
- Create a report.
- Choose the Spanner connector.
- Input the attacker’s project, spanner instance name “attackerspanner”, and the attacker’s DB “attackerdb” or a public spanner. Input a random query that will work on the attacker’s DB, for example “SELECT NULL”
- Proxy the HTTP requests, and forward the requests, including the getColumns request.
- Intercept the createBlockDatasource and publishDatasource HTTP requests, and change the project name, instance name, and database name to the victim’s details, and also swap the SQL query to the malicious injection you want to inject into the victim’s Spanner (notice the fields are present a couple of times in each request).
- Click Resource → Manage added data sources → edit the added Spanner data source, and change the credentials to Viewer Credentials.
- Add a table to the report by pressing “Add a chart” and choosing a Table.
- Choose the added victim’s Spanner data source to be attached to the table chart, the end result should be “No Data Set Access.”
- Share the report with the victim, and uncheck the “Notify” checkbox.
- (Optional) Make the report embeddable by clicking File → Embed report → check “Enable Embedding” and press Done.
- (Optional) Host a website and iframe the report with the granted iframe when allowing embedding, for example:
`<iframe width="600" height="450" src="https://lookerstudio.google.com/embed/reporting/<attacker’s-report-id>/page/MK5LF" frameborder="0" style="border:0" allowfullscreen sandbox="allow-storage-access-by-user-activation allow-scripts allow-same-origin allow-popups allow-popups-to-escape-sandbox"></iframe>`
- Visit the attacker’s site as the victim, and the data will be exfiltrated.
Solution
Google has fixed the issue.
Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]