by Cesar Navas
November 29, 2016
The risk from vulnerabilities can vary greatly from one organization to another. A well known vulnerability such as Heartbleed has a different impact to many organizations. The Heartbleed vulnerability is within the OpenSSL library. As organizations use technology in their own specific way, each organization had a different potential impact. An organization with Linux servers accessible from the internet may have a higher risk than an organization with Microsoft Windows servers. When organizations use Linux, Heartbleed has varying levels of risk to the organization depending on the version of OpenSSL and other factors.
Analysts are still left to assess the risk to the organization when issues like Heartbleed become known. There may be a heightened perceived impact and risk to the organization because OpenSSL was used, but the actual risk could be much smaller. If a vulnerable OpenSSL version was found in the organization, management may ask how much safer would the organization be if the OpenSSL vulnerability was patched? Knowing the answer to these kinds of questions can help guide discussions as to whether or not the organization ignores the problem, mitigates the issue, or remediates the vulnerability.
To answer the question above, analysts can use this dashboard within Tenable's Tenable.sc Continuous View (CV) to determine the risk to the organization. The dashboard relies upon data gathered from Tenable Nessus, Tenable Nessus Network Monitor (NNM), and Tenable Log Correlation Engine (LCE) to provide analysts with an accurate and comprehensive view of the risk from vulnerabilities within the organization. If issues like Heartbleed are within the organization, analysts can quickly determine the risk reduction of remediating the vulnerability.
Analysts now have the ability to accurately characterize the risk to the organization from specific vulnerabilities. The data that analysts can rely upon from this dashboard are vulnerabilities that were found across a multitude of vectors from active scanning, passive listening, and from host analysis mined from systems. The data within the dashboard provides analysts with views to vulnerabilities based on technology groups, CVSS scores, and age. Multiple views such as highly specific vulnerabilities and their risk to overall big picture views can help analysts to quickly sift through large amounts of vulnerabilities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Tenable.sc 5.4
- Nessus 8.5.1
- NNM 5.9.1
- LCE 6.0.0
Tenable Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, and security monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from our unique sensors, delivering continuous visibility and critical context, enabling decisive action that transforms your security program from reactive to proactive. Active scanning identifies vulnerabilities within systems, running processes and services, software applications, configuration settings, and additional vulnerabilities. With this information, analysts have greater insight to determine the risk from vulnerabilities across the organization. Continually scanning the network with passive sensors for servers, desktops and applications helps prioritize security efforts to mitigate threats and weaknesses. Organizations continue to operate with more mobile and transient network devices and need to have a system in place that continuously monitors traffic, devices, applications, and communications across environments. Tenable enables powerful, yet non-disruptive, continuous monitoring of the organization to ensure vulnerabilities and knowledge of their risk are available to analysts.
This dashboard contains the following components:
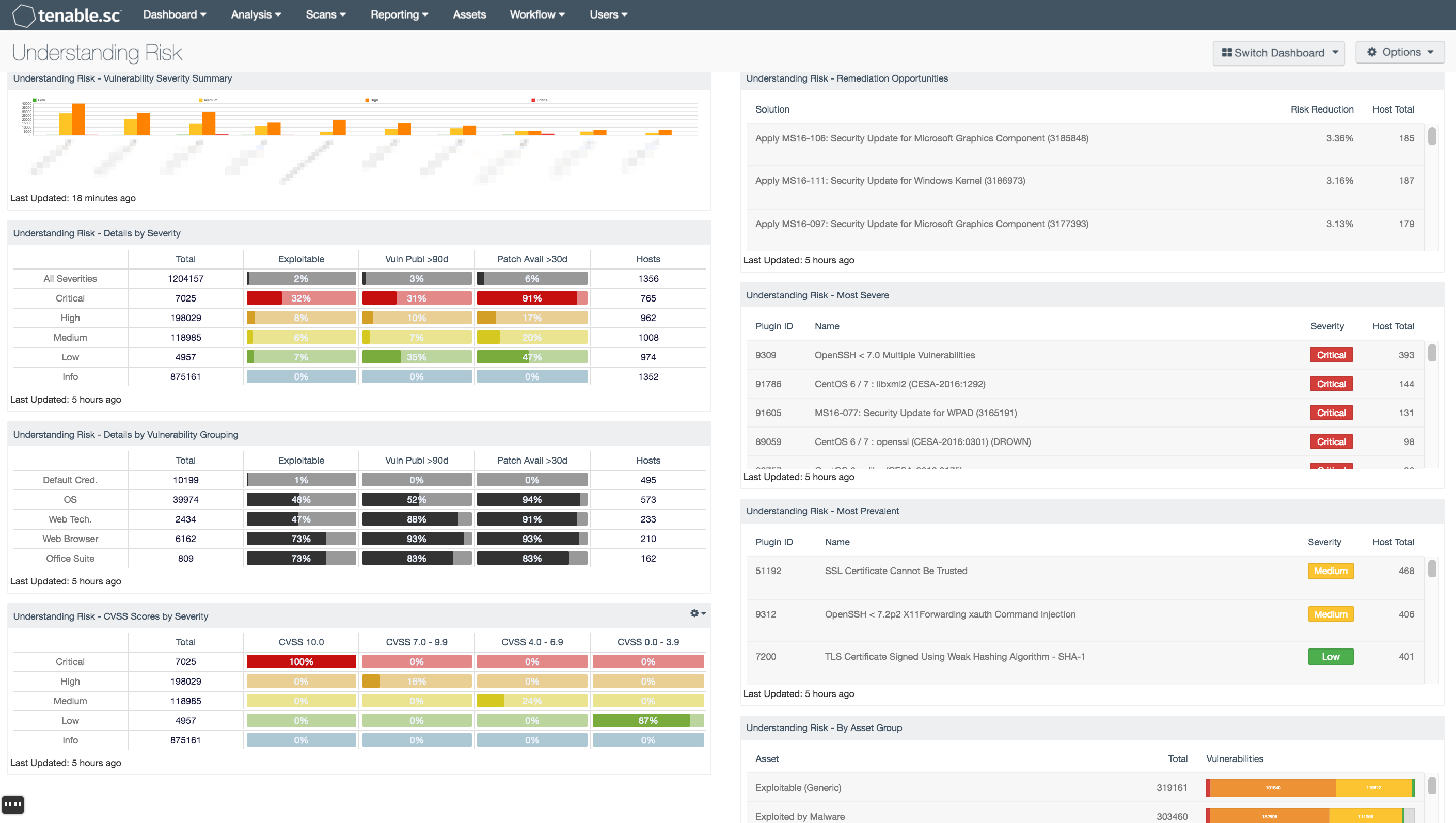
- Understanding Risk - Vulnerability Severity Summary: This bar chart displays totals of vulnerability severities by a Class C summary
- Understanding Risk - Details by Severity: This matrix presents details by severity on vulnerabilities found to exist in the environment
- Understanding Risk - Details by Vulnerability Grouping: This matrix presents details by vulnerability grouping on vulnerabilities found to exist in the environment
- Understanding Risk - CVSS Scores by Severity: This matrix presents Common Vulnerability Scoring System (CVSS) information by severity on vulnerabilities found to exist in the environment
- Understanding Risk - Remediation Opportunities: This table displays the top remediations for the network
- Understanding Risk - Most Severe: This table presents the most severe vulnerabilities found to exist in the environment
- Understanding Risk - Most Prevalent: This table presents the most prevalent vulnerabilities found to exist in the environment
- Understanding Risk - By Asset Group: This table presents a summary by asset grouping of vulnerabilities found to exist in the environment