by Liz Hutto
January 5, 2022
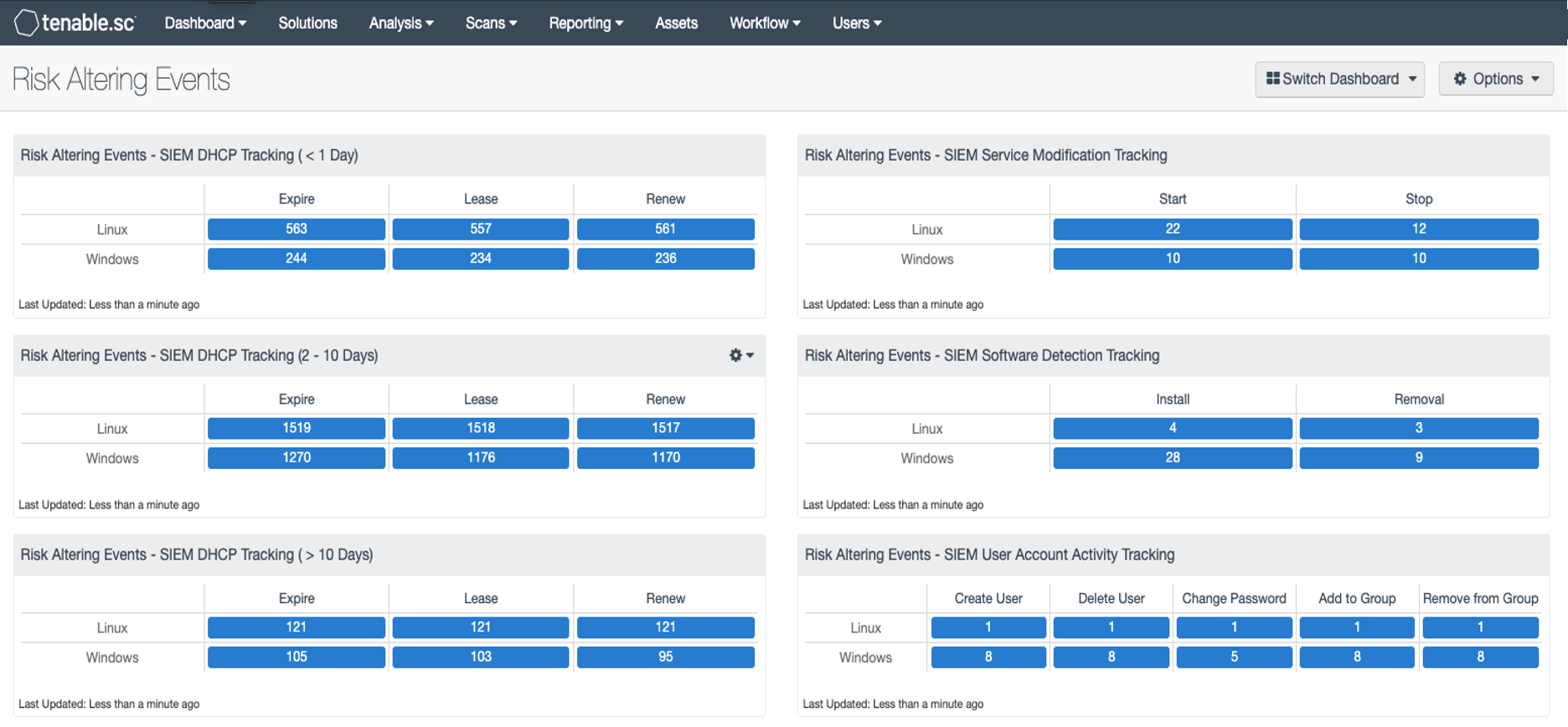
There are several events that often cause the risk posture of an asset to change, such as a new user account or a service stopping or starting; these are called risk-altering events. Organizations use SIEM products to consolidate and analyze these events. Nessus Network Monitor (NNM) 6.0.0 has the ability to pull these events from SIEM products, which downloads four categories of risk altering events. Tenable.sc now supports collecting these events from NNM by bringing these types of events together into this dashboard.
NNM provides security teams with the ability to poll events every five to ten minutes. This new service identifies assets from DHCP logs as well as events that track changes to risk posture, such as software installations, account changes and service changes.
These events are broken down into four categories:
- Software Detection: The addition or removal of software alters the risk profile of an asset, and this event should be recorded for risk analysis. When users or software management systems deploy or install software, the operating system records the process. NNM will use common language and analysis of logs from the SIEM to find these events and convert them into plugin data, which can be used to automate a vulnerability scan when software changes occur.
- User Account Activity: The modification of user accounts alters the risk profile of an asset. This includes adding users to groups, changing passwords, etc., and these events should be recorded for risk analysis.
- Service Modification: Service modification is often related to software installation, but when a service is added, stopped, or started, the risk profile of the asset will change. NNM will ask for these service-related events and provide the details based on the data collected.
- Assets Discovery: NNM will query for DHCP logs from SIEM providers to record address assignment. In the DHCP exchange, many attributes of the asset are discovered and will be recorded for selecting targets to add to a vulnerability scan.
Organizations are often required to maintain an asset inventory to adhere to compliance, such as the CIS Critical Control 1. As part of the compliance process, the security team needs to have an accurate count of the assets on the network, including assets not owned by the organization. With many assets not being static, the likelihood of having full asset coverage in an active scan is slim. Yet security teams are expected to provide an accurate asset inventory, despite the constantly changing network. This data can be leveraged to support compliance-based use cases, perform risk analysis, and establish new scan activities. This dashboard is tailored to assist security teams with identifying assets and events that alter the risk posture.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards (ARCs), and assets. The dashboard can be easily located in the Tenable.sc Feed under the Discovery & Detection category.
The dashboard requirements are:
- Tenable.sc 5.20.0
- Nessus Network Monitor 6.0.0
By incorporating risk-altering event analysis, Security Directors can enrich the organization’s Risk-Based Vulnerability Management (RBVM) Program. Tenable.sc brings the collected events together with active and passive scanning to increase asset detection and improve risk awareness. Discovery is the first step in the RBVM lifecycle; the data in this dashboard extends the scope of information provided to organizations to enable better asset discovery.
This dashboard contains the following components:
Risk Altering Events - SIEM Software Detection Tracking: This matrix displays software installation and removal events in Windows and Linux operating systems. These events include RPM and YUM installs as well as installs and uninstalls in Windows using standard install tools. The install events are enumerated from SIEM logs related to application installs.
Risk Altering Events - SIEM DHCP Tracking ( > 10 Days): This matrix displays DHCP events that occurred more than ten days ago for Windows and Linux operating systems, such as DHCP Expire, Lease, and Renew. NNM will query for DHCP logs from SIEM providers to record address assignment. In the DHCP exchange, many attributes of the asset are discovered and will be recorded for selecting targets to add to a vulnerability scan.
Risk Altering Events - SIEM Service Modification Tracking: This matrix displays service modification events related to service starts and stops in Windows and Linux operating systems. These events are enumerated from SIEM logs related to service stops and starts.
Risk Altering Events - SIEM DHCP Tracking (2 - 10 Days): This matrix displays DHCP events that occurred within the last two to ten days for Windows and Linux operating systems, such as DHCP Expire, Lease, and Renew. NNM will query for DHCP logs from SIEM providers to record address assignment. In the DHCP exchange, many attributes of the asset are discovered and will be recorded for selecting targets to add to a vulnerability scan.
Risk Altering Events - SIEM User Account Activity Tracking: This matrix displays user account activity events in Windows and Linux operating systems, such as users added or deleted as well as changes to groups and passwords. These events are enumerated from SIEM logs related to users’ creation and removal, changes in passwords, and group membership changes.
Risk Altering Events - SIEM DHCP Tracking ( < 1 Day): This matrix displays DHCP events that occurred within the last day for Windows and Linux operating systems, such as DHCP Expire, Lease, and Renew. NNM will query for DHCP logs from SIEM providers to record address assignment. In the DHCP exchange, many attributes of the asset are discovered and will be recorded for selecting targets to add to a vulnerability scan.