by Sharon Everson
June 30, 2020
The privileges assigned to users can often be misconfigured and is a common problem for many organizations. National Information Assurance (NIA) Policy v2.0 requires that organizations have an understanding of the access granted and at what levels. Tenable.sc uses active and compliance scanning to detect and monitor user privileges and permissions. This dashboard assists risk managers in understanding user privileges, group memberships, and related configurations. The Assess phase of the Cyber Exposure lifecycle provides information needed to identify the permission and privilege based vulnerabilities, misconfigurations, and other security configuration indicators.
Tenable.sc helps to provide visibility into these common questions related to user management and privileged access, for example:
- Are there unnecessary administrative privileges in the organization?
- Are all user accounts unique?
- Do administrators log on to non-administrative workstations?
- Are inactive accounts purged from the environment?
- Are effective controls for separation of duties in place?
The answers to these questions provide a solid basis for understanding credential hygiene and maintaining NIA compliance.
The NIA Access Control Security [AM] domain contains controls related to access control and ensuring the confidentiality, integrity, and availability of assets. These controls include best practices for user account management, such as providing access based on the concept of “least privilege”. Administrative privileges should be controlled and limited specifically to those with a need, to limit the risk from account compromise. Each user of a system should have a unique account assigned to them. Sharing of user accounts limits accountability for actions. Administrator credentials should only be used to log on to workstations specifically designated for administrative work and all actions by the administrator should be logged. This limits the risk of account compromise via non-hardened workstations and ensures an appropriate audit trail exists in case of credential use by a bad actor. Following the principle of least privilege, users should only have the access specifically needed and no more. Similarly, user privileges should be separated by functional groups preventing fraud by ensuring that no individual has unnecessary authority to perform critical functions.
Tenable.sc provides many mechanisms for understanding credential hygiene. Local checks provide group membership, local user access, and user account information including information about inactivity and password change status. Local checks can also identify inactive and duplicate accounts on Linux and UNIX systems. Tenable.sc uses audit files to determine the state of logging on hosts and the associated risks. Separation of duties can be inferred by understanding the group memberships and other checks.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization's adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Information Security Management program prescribed by the NIA standard.
Components
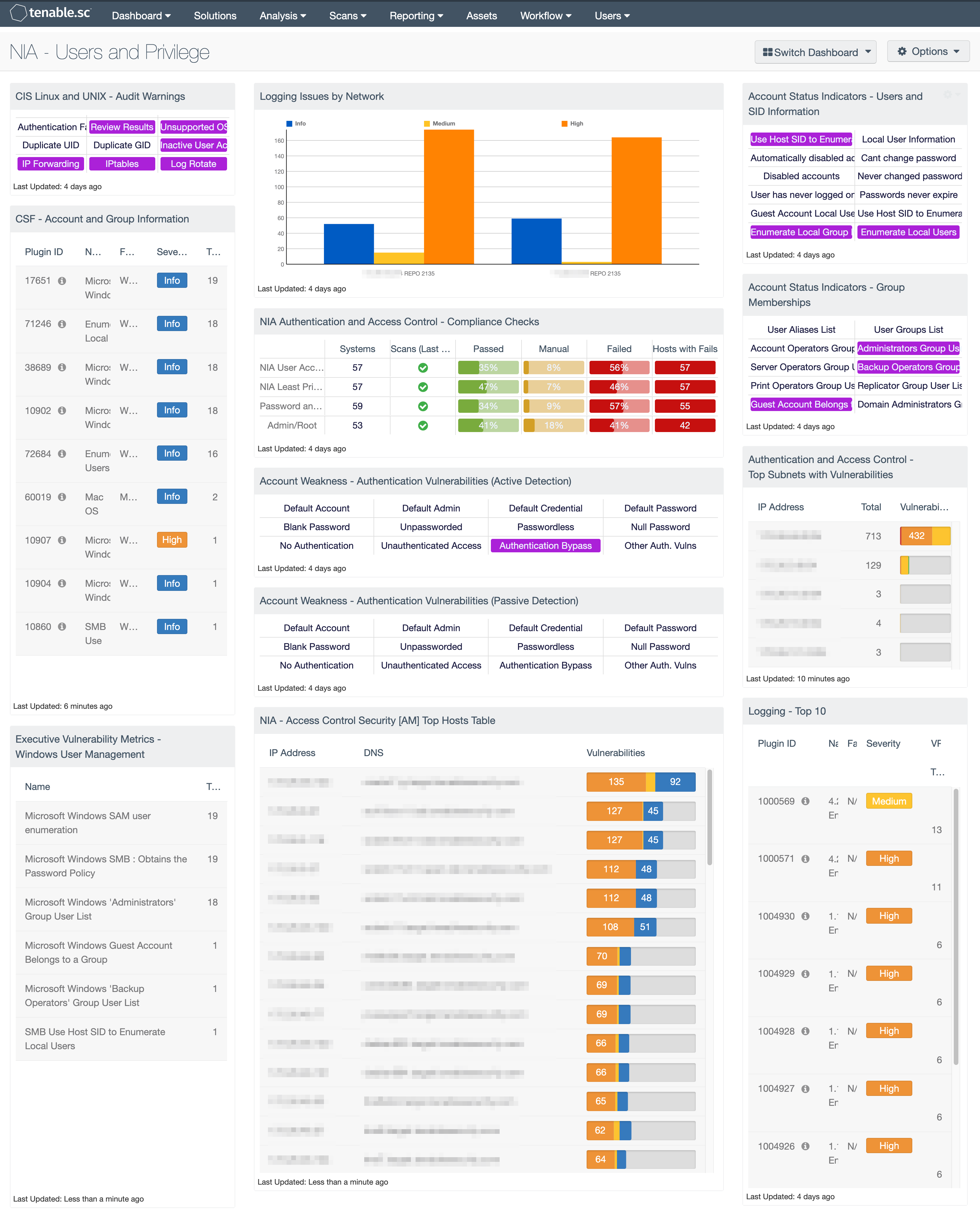
CIS Linux and UNIX - Audit Warnings: This component presents Audit Warnings indicators that trigger if one or more vulnerabilities are found to exist. Common checks included are: Duplicate UID/GID, Inactive User Account, and Unsupported OS. Indications can be customized to highlight specific CIS Linux and Unix vulnerabilities as the organization sees fit.
CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
Executive Vulnerability Metrics - Windows User Management: This table provides a list of informational vulnerabilities on Microsoft user accounts. This component selects the 'Windows: User management' plugin family and is then sorted by the total of vulnerabilities discovered. The 'Windows: User management' plugin family checks for issues in Microsoft Windows user management, and includes user information disclosure, group enumeration, and more.
Logging Issues by Network: This component shows a breakdown of logging issues by CIDR range. The Class C tool is used to group audit checks related to logging.
NIA Authentication and Access Control - Compliance Checks: This matrix displays a summary of NIA compliance checks related to user access and least privilege and compliance checks based on keywords for password, admin, root, account, and credentials. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. The component provides host count columns and ratio bars for each severity level. Checks that have passed are green, failed checks are red, and checks that require manual verification are orange.
Account Weakness - Authentication Vulnerabilities (Active Detection): This matrix shows active detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name. This component is also included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).
Account Weakness - Authentication Vulnerabilities (Passive Detection): This matrix shows passive detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name. This component is also included in dashboards related to the 2015 Verizon Data Breach Investigation Report (DBIR).
NIA - Access Control Security [AM] Top Hosts Table: The NIA Compliance Summary - Hosts with Top Failed Checks table provides a list of the top 100 systems on the network with NIA compliance audits and results for the AM domain. This table uses the IP Summary tool and displays systems with Passed, Failed, and Manual Check audit results sorted by Failed audit checks.
Account Status Indicators - Users and SID Information: This component provides easy access to several plugins used to collect information about user accounts and security identifiers (SID). Listed below are the details for plugins identified in this matrix:
- SMB Use Host SID to Enumerate Local Users: Using the host security identifier (SID), Nessus is able to enumerate local users on the remote Windows system.
- Microsoft Windows Local User Information: Nessus is able to retrieve information for each local user. Note that this plugin itself does not issue a report and only serves to store information about each local user in the KB for further checks.
- Microsoft Windows - Local Users Information Automatically disabled accounts: Nessus is able to list local user accounts that have been automatically disabled. These accounts may have been disabled for security reasons or due to brute-force attack attempts.
- Microsoft Windows - Local Users Information Can't change password: Nessus is able to list local users who cannot change their own passwords.
- Microsoft Windows - Local Users Information Disabled accounts: Nessus is able to list local user accounts that have been disabled.
- Microsoft Windows - Local Users Information Never changed passwords: Nessus is able to list local users who have never changed their passwords.
- Microsoft Windows - Local Users Information User has never logged on: Nessus is able to list local users who have never logged into their accounts.
- Microsoft Windows - Local Users Information Passwords never expire: Nessus is able to list local users that are enabled and whose passwords never expire.
- Microsoft Windows SMB Guest Account Local User Access: The remote host is running one of the Microsoft Windows operating systems or the SAMBA daemon. It was possible to log into it as a guest user using a random account.
- SMB Use Host SID to Enumerate Local Users Without Credentials: Using the host security identifier (SID), Nessus is able to enumerate local users on the remote Windows system without credentials.
- Enumerate Local Group Memberships: Nessus connects to a host via SMB to retrieve a list of local groups and their members.
- Enumerate Local Users: Connects to a host via SMB to retrieve a list of local users.
Account Status Indicators - Group Memberships: There are several default groups such as the administrators, server operators, account operators, backup operators, print operators, and replicator; this matrix provides an easy method to monitor these memberships. Listed below are the plugin details:
- Microsoft Windows User Aliases List: Nessus is able to retrieve the list of groups each user belongs to. Aliases are stored in the KB for further checks.
- Microsoft Windows User Groups List: Nessus is able to retrieve the list of groups each user belongs to. Groups are stored in the KB for further checks.
- Microsoft Windows 'Account Operators' Group User List: Nessus is able to extract the member list of the 'Account Operators' group. Members of this group can create or modify local user accounts but cannot modify or create administrative accounts or edit user rights.
- Microsoft Windows 'Administrators' Group User List: Nessus is able to extract the member list of the 'Administrators' group. Members of this group have complete access to the remote system.
- Microsoft Windows 'Server Operators' Group User List: Nessus is able to extract the member list of the 'Server Operators' group. Members of this group can perform most common administrative tasks.
- Microsoft Windows 'Backup Operators' Group User List: Nessus is able to extract the member list of the 'Backup Operators' group. Members of this group can logon to the remote host and perform backup operations (read/write files) but have no administrative rights.
- Microsoft Windows 'Print Operators' Group User List: Nessus is able to extract the member list of the 'Print Operators' group. Members of this group can manage printers within a Windows Domain or shutdown a server.
- Microsoft Windows 'Replicator' Group User List: Nessus is able to extract the member list of the 'Replicator' group. Members of this group can replicate (or copy) files or directories within a domain.
- Microsoft Windows Guest Account Belongs to a Group: Nessus is able to determine that the 'Guest' user belongs to groups other than 'Guests' (RID 546) or 'Domain Guests' (RID 514). Guest users should not have any additional privileges.
- Microsoft Windows 'Domain Administrators' Group User List: Nessus is able to extract the member list of the 'Domain Administrators' group. Members of this group have complete access to the Windows Domain.
Authentication and Access Control - Top Subnets with Vulnerabilities: This component displays the top Class C subnets with actively and passively detected vulnerabilities related to authentication and access control. These vulnerabilities may include password vulnerabilities, default account and credential vulnerabilities, and other authentication-related vulnerabilities. Presenting these interactions by subnet allows easy understanding of which areas of the network are more vulnerable. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to allow further investigation. If desired, the analysis tool can be changed to present the authentication and access control vulnerabilities by vulnerability, IP address, or asset list.
Logging - Top 10: This table shows the Top 10 logging issues. Audit checks are filtered for those related to logging issues and displayed.