by Cesar Navas
December 12, 2019
An initial step in implementing Cyber Exposure is identifying assets on the network. The next step is creating an inventory of hardware assets. As part of the inventory process each asset has many different attributes that are collected to assist in the attribution of each asset. This dashboard provides organizations with many of the assets collected during a vulnerability scan.
The CIS ControlsTM are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks. These controls were developed by IT professionals using operational experiences and generally accepted best practices. This dashboard will focus on Control 1. Control 1 requires the organization to actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access. Unauthorized and unmanaged devices are found and prevented from gaining access. Tenable.sc helps by actively and passively scanning the systems and taking hardware attributes. System administrators and operation teams can review the content provided to better track and inventory assets.
Historically CIS has referred the first six CIS controls as cyber hygiene to focus an organization’s cybersecurity activities. The designation of cyber hygiene brought up the fact that these practices may be difficult for organizations with resource and/or expertise limitations. To address any resource or expertise limitation, CIS now recommends following Implementation Groups (IG) to help prioritize CIS control utilization. There are three IG’s which describe organizations by size. The IG specifies a subset of the controls that have been assessed to have a similar risk profile and resources to implement. The IG’s are also meant to be prioritized in IG order regardless of the IG organization size. For example, organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3. The IG’s are described as organizations with limited resources and cybersecurity expertise (IG1); Organizations with moderate resources (IG2); Organizations with significant resources (IG3).
Sub-Control 1.1 requires organizations to use active discovery tools to detect and inventory assets. Tenable.sc provides organizations at all IG’s to utilize an active scanning tool to collect unique information about each asset scanned. Using Nessus, Tenable.sc initially port scans each asset and collects any open ports grabbing service banners where applicable. Next, when scanned with credentials, Nessus will log in to the system and collect a multitude of system configuration data. While Tenable.sc is known for the vulnerability data collected, Tenable.sc also collects a wide range of asset identification attributes such as MAC address, CPU GUID, and many others. The components on the left column of the dashboard provide many of the actively collected attributes for further analysis by the operations team.
Sub-Control 1.2 requires organizations to use a passive asset discovery tool, Tenable.sc Continuous View includes the Nessus Network Monitor (NNM). Using NNM, Tenable.sc is able to discover assets on the network using a Switch Port Analyzer (SPAN) port. SPAN ports are also commonly referred to as a Mirrored port. Regardless of the nomenclature, the SPAN port will provide copies of traffic to a Network Interface Card (NIC) for analysis. The NNM will discover hardware assets and many different attributes. In addition to Sub-Control 1.2, Sub-Control 1.3 requires logging Dynamic Host Configuration Protocol (DHCP) traffic. Due to the passive nature of DHCP, NNM easily detects and logs this traffic for analysis.
All three of these Sub-Controls are required by IG3, while Sub-Control 1.1 & 1.3 are required for IG2. However, to benefit of all IG’s (IG1, IG2, IG3), Tenable.sc Continuous View supports assisting with hardware asset inventory. While IG1 & IG2 may have a less formalized inventory process, IG3 can use the data collected actively and passively to verify the more advanced and distributed inventory systems.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category, Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.8.0
- Nessus Network Monitor 5.10.1
Tenable.sc Continuous View (CV) is the market-defining on-prem Cyber Exposure platform. Tenable.sc CV provide the ability to discover hardware assets, for a more detailed analysis. Not only detecting risks based on Common Vulnerabilities and Exposures (CVE), but also using more advanced methods such a Vulnerability Priority Rating (VPR). Tenable.sc provides customers with a full and completed cyber exposure platform for completing an effective Cyber Hygiene program prescribed by CIS Controls framework.
This dashboard contains the following components:
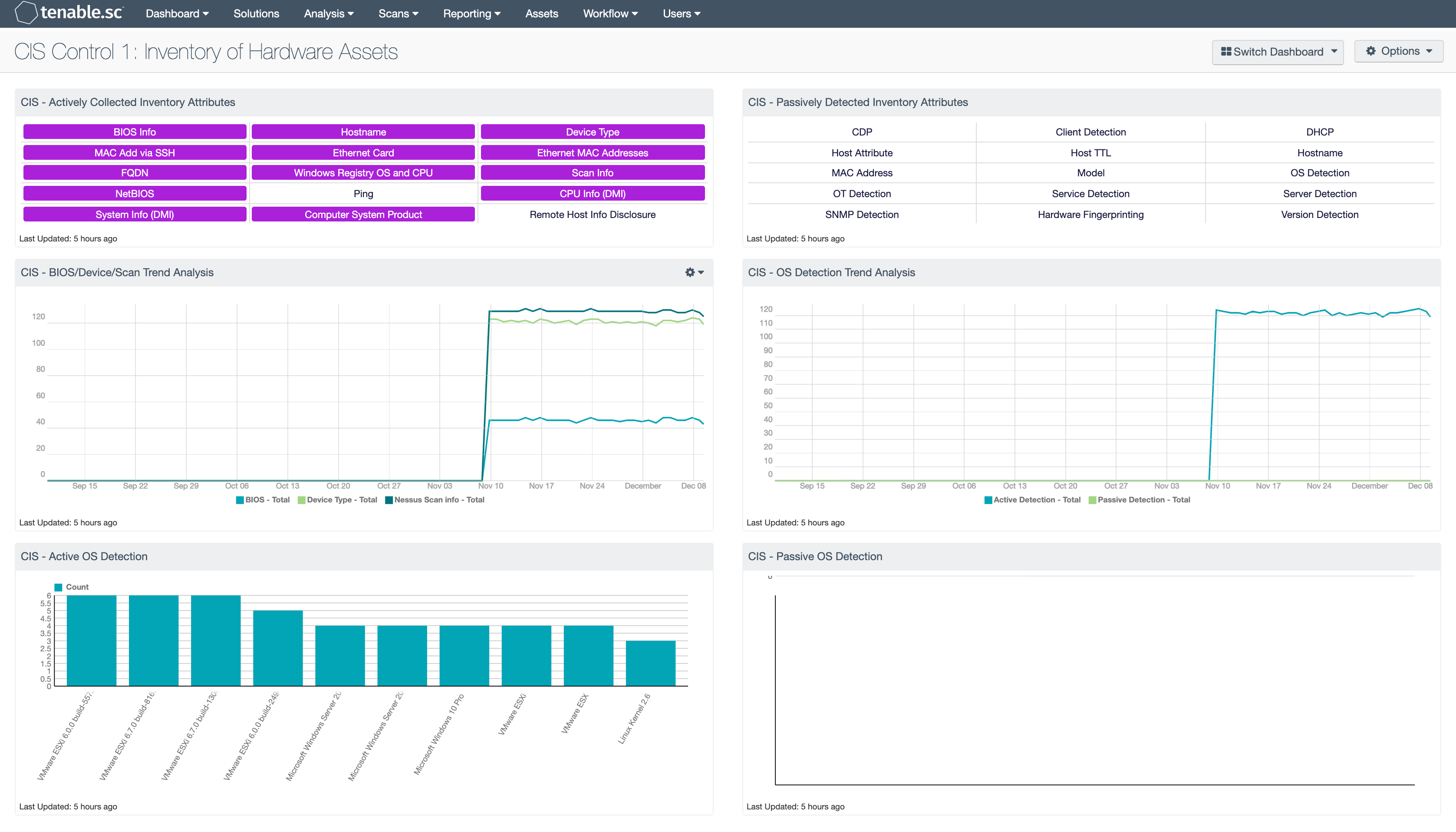
CIS - Actively Collected Inventory Attributes: This matrix provides a series of saved searches that contain hardware attributes, collected actively as part of a hardware inventory. Each indicator, when purple, will provide a list of IP addresses with the respective content. Analysis can then pivot using the “Vulnerability Detail List” tool to view the details of each discovered attribute. Other tools can also be used such as the “Class C” or “User Responsibility” tool to further analyze the data.
CIS - BIOS/Device/Scan Trend Analysis: This line chart provides a historic analysis of systems scanned, versus the BIOS and Device Type data. In a well-managed network, the number of devices scanned, and BIOS detections will be in close proximity. The values calculated at each data point provide a count of checks over 24 hours, allowing organizations the ability to track changes based on daily scans. However, if the organization scans in greater intervals, consider modifying the filters in this component.
CIS - Active OS Detection: This bar chart provides the summary of operating systems detected using the List OS tool and plugin 11936 (OS Identification). The chart provides the top 10 most prevalent operating systems detected in the network. This view provides analysts with a high-level view of their current network and the systems actively detected. Tenable.sc uses Nessus to actively scan assets and using a wide range of detections methods such as banner grabbing, protocol detections, and advanced finger printing, this component helps organizations to better understand and track risks based on OS detection.
CIS - Passively Detected Inventory Attributes: This matrix provides a series of saved searches that contain hardware attributes, collected passively, often part of a hardware inventory. Each indicator, when purple, will provide a list of IP addresses with the respective content. Analysis can then pivot using the “Vulnerability Detail List” tool to view the details of each discovered attribute. Other tools can also be used such as the “Class C” or “User Responsibility” tool to further analyze the data.
CIS - OS Detection Trend Analysis: This line chart provides analyst with a historic view of operating system detections both passively and actively. When initially deploying Tenable.sc Continuous View (CV), the passive detection will most likely be greater, the numbers should begin to align themselves over time. In the event there is an unusual difference, then there is either a passive detection gap, or an active scanning gap. Regardless, the organization should analyze the data and discover the deficiency. The values calculated at each data point provide a count of checks over 24 hours, allowing organizations the ability to track changes based on daily scans. However, if the organization scans in greater intervals, consider modifying the filters in this component.
CIS - Passive OS Detection: This bar chart provides the summary of operating systems detected using the List OS tool and plugin 1 (Passive OS Detection). The chart provides the top 10 most prevalent operating systems detected in the network. This view provides analysts with a high-level view of their current network and the systems passively detected. Tenable.sc uses Nessus Network Monitor to passively scan assets and using a wide range of detections methods such as banner grabbing, protocol detections, and advanced finger printing, this component helps organizations to better understand and track risks based on OS detection.