by Cesar Navas
August 22, 2016
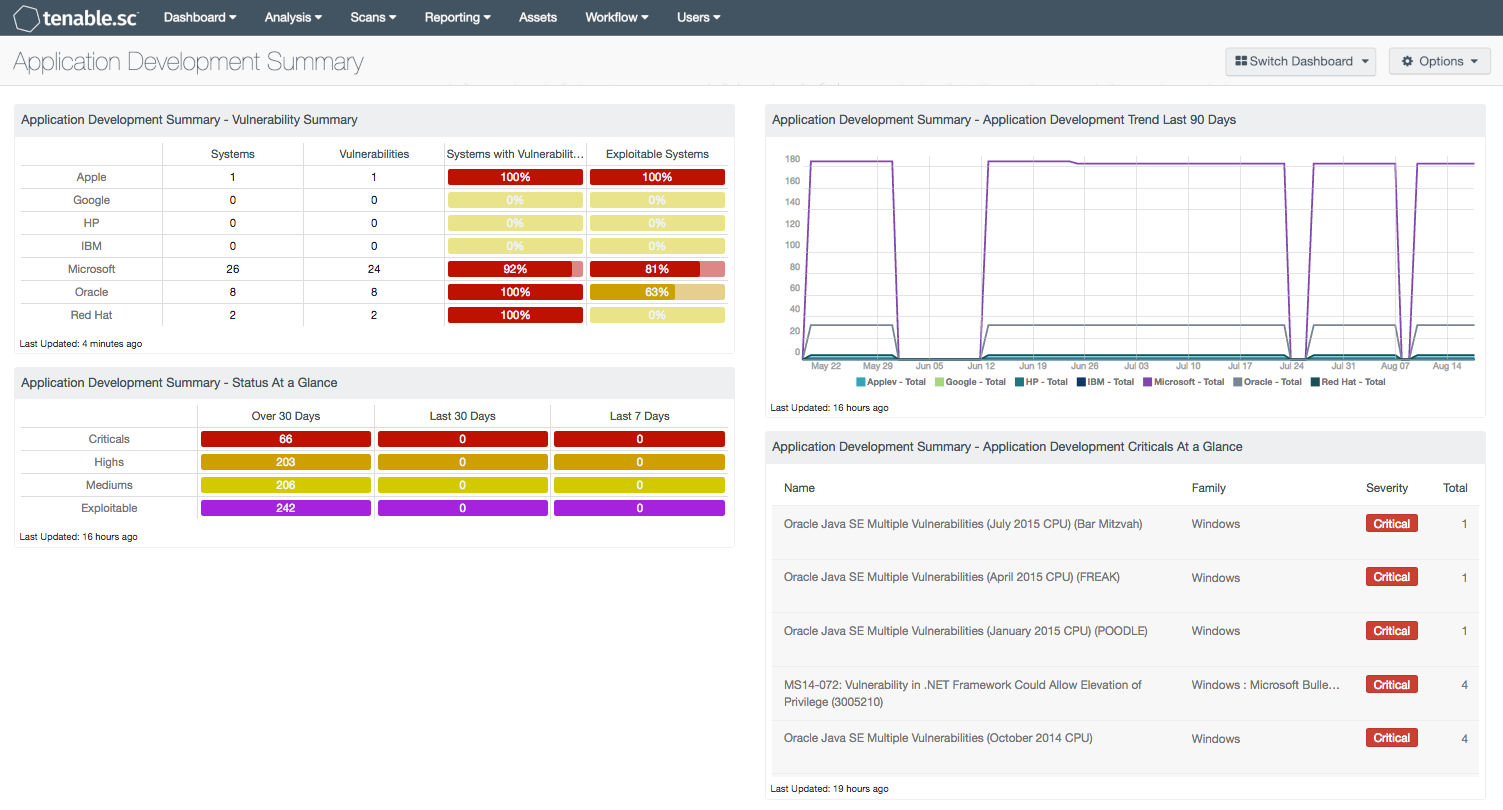
Tenable.sc Continuous View (CV) (via Nessus Network Monitor, Log Correlation Engine, and Nessus) collects information about installed products, and identifies those products using standardized industry methods. This dashboard enumerates known application development software, such as VBScript, Xcode, and Java Development Kit. The included components provide a quick visual representation of the number of systems certain development applications are installed on, the number of vulnerabilities, ratio of vulnerable systems, and percentage of systems that are currently exploitable. This dashboard can assist the analyst in the identification of vulnerable software, which potentially can give an attacker the ability to execute arbitrary code.
Application development software is software used to create and maintain applications and frameworks. Many times development systems and software are overlooked during the routine patching and update process of an organization’s workstations and servers. Vulnerable application development software can be exploited, increasing the threat landscape to an organization. Under certain circumstances, vulnerable libraries or components of these development applications can introduce vulnerabilities into software applications being developed, which can later be exploited. This information assists with the enforcement and verification of IT management policies relating to assets, such as vulnerability, configuration, and remediation policies.
The components in this dashboard leverage data gathered by active vulnerability scanning with Nessus. Application development software vulnerability data is presented to the analyst via four components. A Vulnerability Trend, which displays application vulnerabilities over the last 90 days. Additionally, two matrix components provide a fast, at-a-glance summary that demonstrates the effectiveness of the current patching and remediation policies, continuing the format of quick visual data presentation without having to drill down to get into it. A fourth table component provides greater detail, specifically targeting identified critical vulnerabilities, displaying the vulnerability name and plugin family. All fields are clickable for a deep dive analysis into the presented data.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Tenable.sc 5.3.1
- Nessus 8.5.0
Tenable.sc Continuous View (CV) provides extensive network monitoring by leveraging a unique combination of detection, reporting, and pattern recognition utilizing industry recognized algorithms and models. Tenable.sc CV is continuously updated to detect advanced threats and vulnerabilities. Tenable constantly analyzes information from our unique sensors, delivering continuous visibility and critical context and enabling decisive action that transforms the security program from reactive to proactive. Continuous vulnerability analysis enables security teams to more effectively tailor remediation efforts. Monitoring the network to ensure that all systems are secured against vulnerabilities is essential to ongoing security efforts. Tenable’s extensive network monitoring capabilities can verify that systems are successfully scanned regularly and secured against vulnerabilities, enabling ongoing improvements to an organization’s security posture.
The following components are included in this dashboard:
- Application Development Vulnerabilities - Vulnerability/Exploitability Indicator Panel - This component displays various defined technologies by row, and enumerates any found vulnerabilities across the columns. Included are the number of systems on which the development applications have been located, along with the number of identified vulnerabilities, the ratio of vulnerable systems, and a count of how many are exploitable.
- Application Development Vulnerabilities - Vulnerability Trend - This component tracks a trend of the number of vulnerabilities that have been identified within development applications over the last 90 days. Hovering the cursor over the spikes presents the analyst with a count per day of the identified events.
- Application Development Vulnerabilities - Status at a Glance - This component gives a quick visual status report on patching efforts. Vulnerabilities are identified by regex queries against CPE strings for known application development applications. The number of critical, high, and medium vulnerabilities is displayed across three columns, as well as the number of days they have been detected. Each column includes the number of vulnerabilities that have existed over the last 30 days, the last 30 days, and the last 7 days.
- Application Development Vulnerabilities - Criticals at a Glance - This component displays the most critical vulnerabilities in a text format, displaying the vulnerability name and plugin family, for a fast, readable reference without having to do a deep dive.