Web Services Indicator Dashboard

The same services we use to connect our networks to the vast resources of the internet can be used against us if not properly secured. Many of the most effective exploits leverage vulnerabilities in common web services, making our jobs more difficult because connectivity is synonymous with exposure. Finding the balance between easy access to resources and securing the network against exploitation is a major challenge that every organization faces, but one that Tenable can help overcome. With the Web Services Indicator dashboard in Tenable.io™, the information you need to earn leadership support to strengthen network defenses against web service exploitation is at your fingertips.
Locating the links
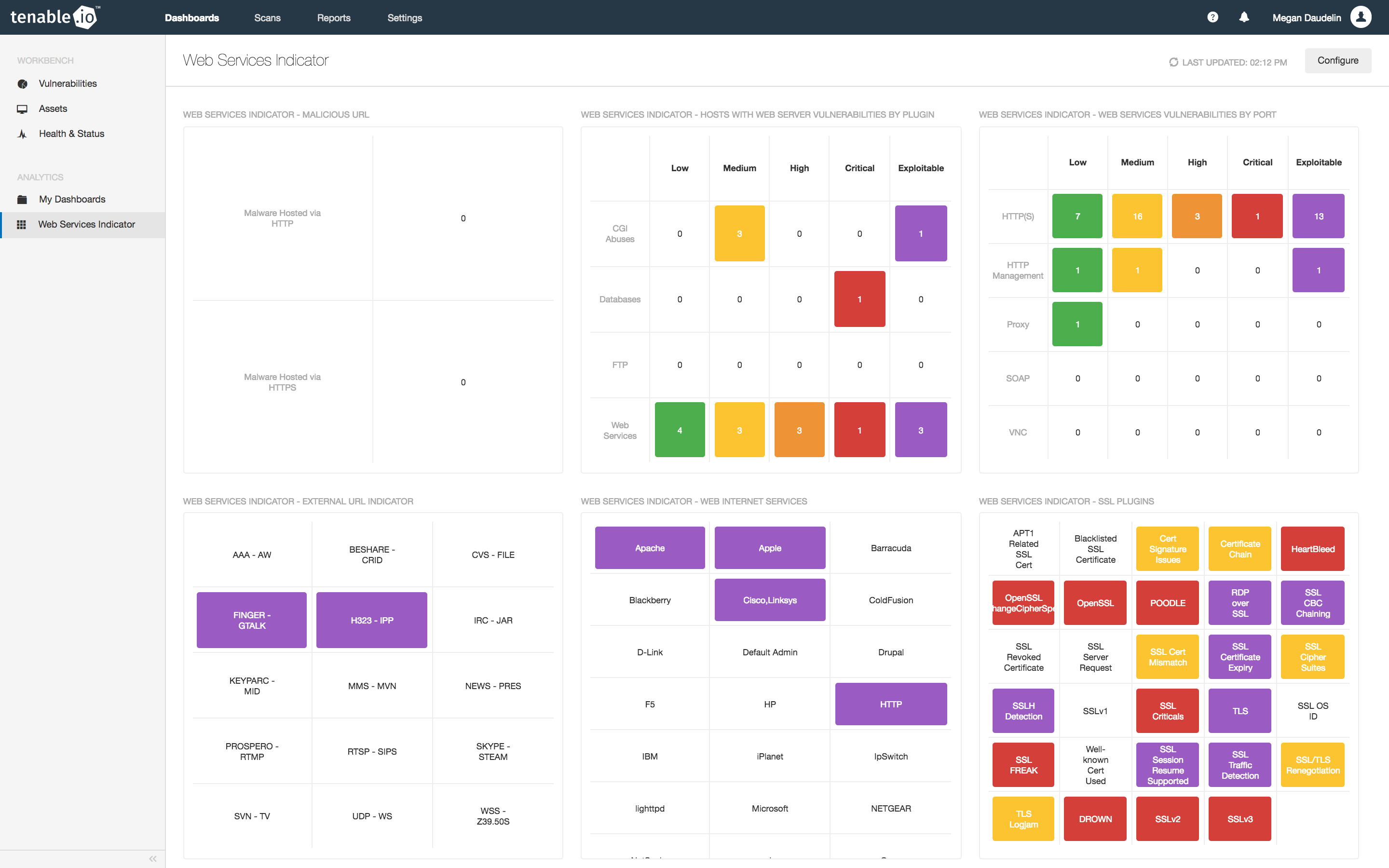
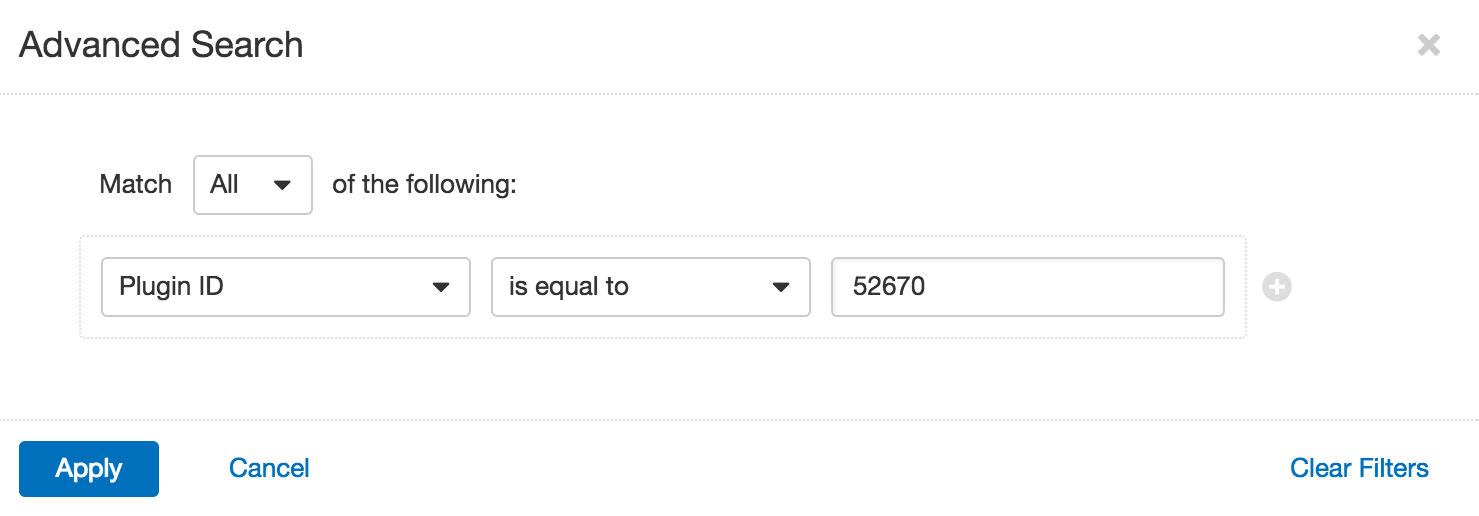
The Malicious URL matrix in the Web Services Indicator dashboard counts detections of HTTP and HTTPS that link to malicious content. The matrix leverages the Web Site Links to Malicious Content Nessus plugin (ID 52670) to detect website URLs that link to malicious sources. Since malware is so often distributed via web traffic, you should look into the causes for these detections promptly.
The easiest way to learn more about the hosts with links to malicious content is to apply an Advanced Filter to the Vulnerabilities workbench. Using a filter for plugin ID 52670 will present a list of all hosts on which the plugin detected malicious links:
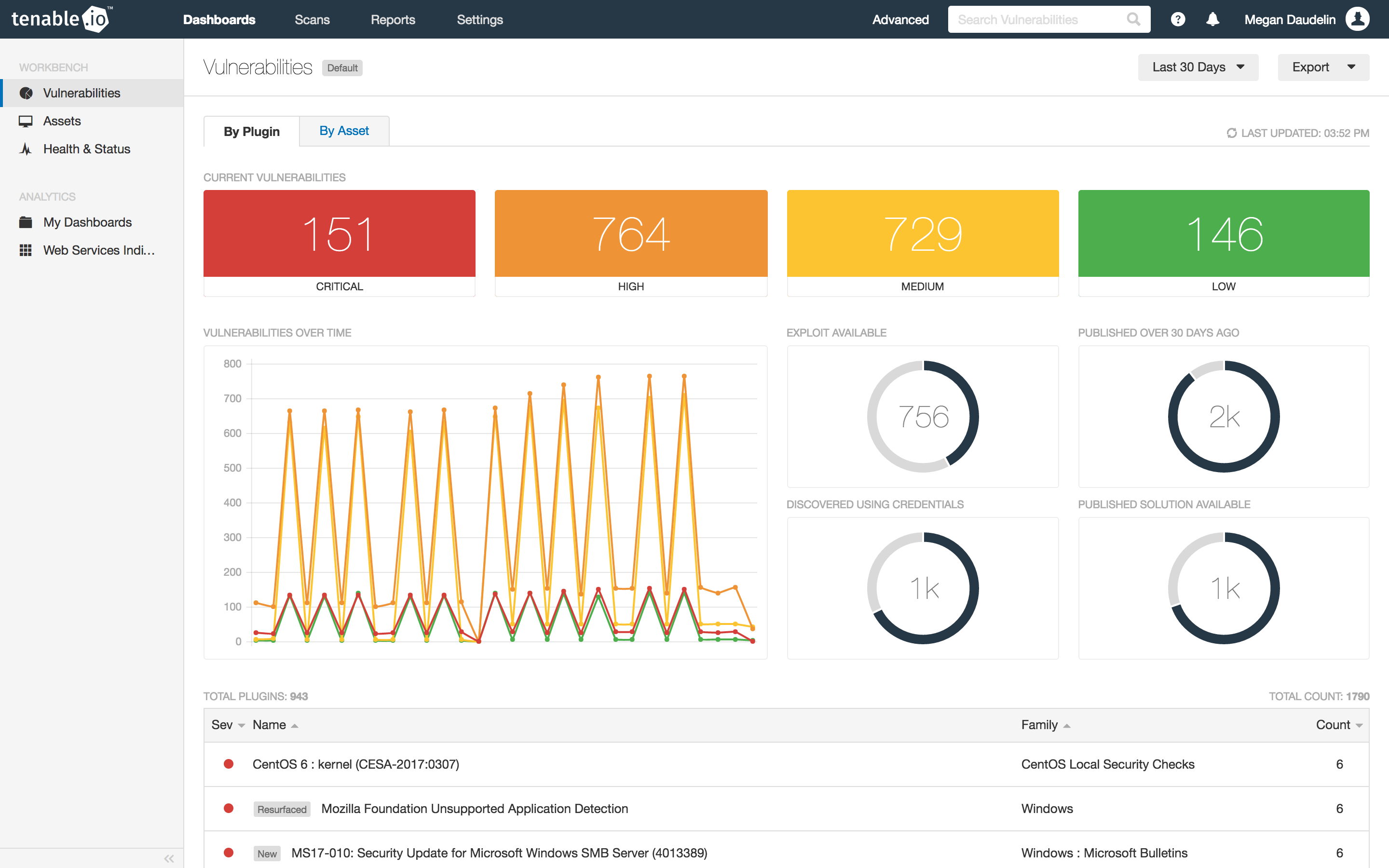
You can find lots of useful details on the drill-down page for a specific result. This includes the plugin description as well as the assets the activity was detected on. Plugin output, when the result was first seen, reference information, and links to more information may also be included. Often most importantly, solutions for remediating detected vulnerabilities are given.
The cells in the External URL Indicator matrix turn purple when a URL containing the specified Uniform Resource Identifier is discovered during a scan. The matrix uses the External URLs active plugin (ID 49704) to identify over 150 URIs on hosts. Common URIs include http, ftp, and about. URIs are typically the first section of a URL, followed by a colon and two slashes. If you notice results for unexpected URIs, you should investigate the source to ensure that only reliable and authorized external URLs are being accessed. Often, these results will just be links to a company’s additional resources in their support documentation. However, malware regularly contains URLs that are called back or connected to, so keeping an eye on these results is the safest bet.
Spotting the services
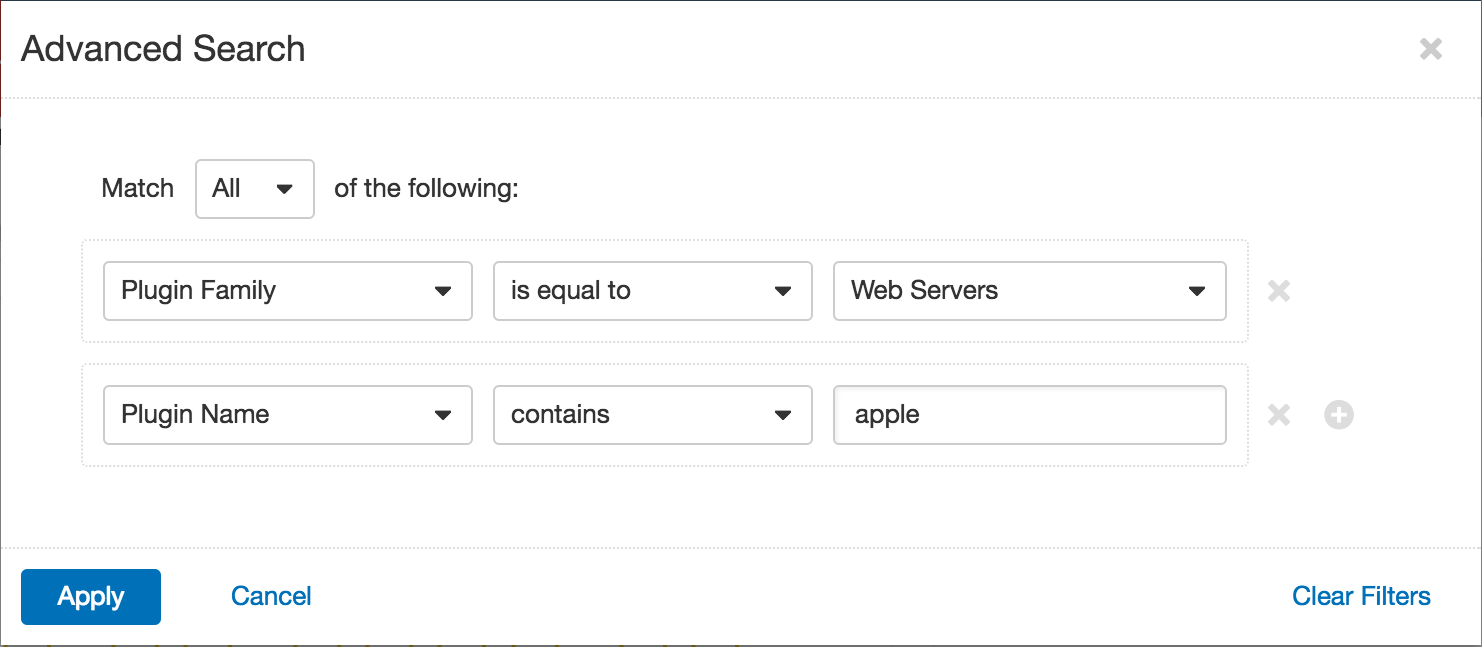
The Web Internet Services dashboard matrix provides indicators for the detection of 30 unique web services. The matrix uses the Web Servers plugin family to filter for plugins of particular concern, and the cells turn purple when a specific service or vulnerability is detected. I would recommend monitoring this information closely, since the presence of unexpected or unapproved web services could be indicative of an unauthorized or misconfigured device connecting to the network.
You can use an Advanced filter on the Vulnerabilities workbench to find detailed information about specific results. Applying a plugin family filter for the Web Servers family will display all the results reflected in this matrix. Adding a plugin name filter for keywords related to particular services will help you isolate the hosts causing a single indicator to turn purple.
The SSL Plugins matrix narrows the focus to detections and vulnerabilities related to TLS and SSL. Using filters for plugin ID, CVE ID, and plugin output, the 30 cells change color when specific TLS- or SSL-related vulnerabilities are detected. Since TLS and SSL are so commonly exploited, I like to keep a keen eye on these results. In a single glance I can get an overview of whether these protocols are being used and whether they are vulnerable to exploitation.
Validating the vulnerabilities
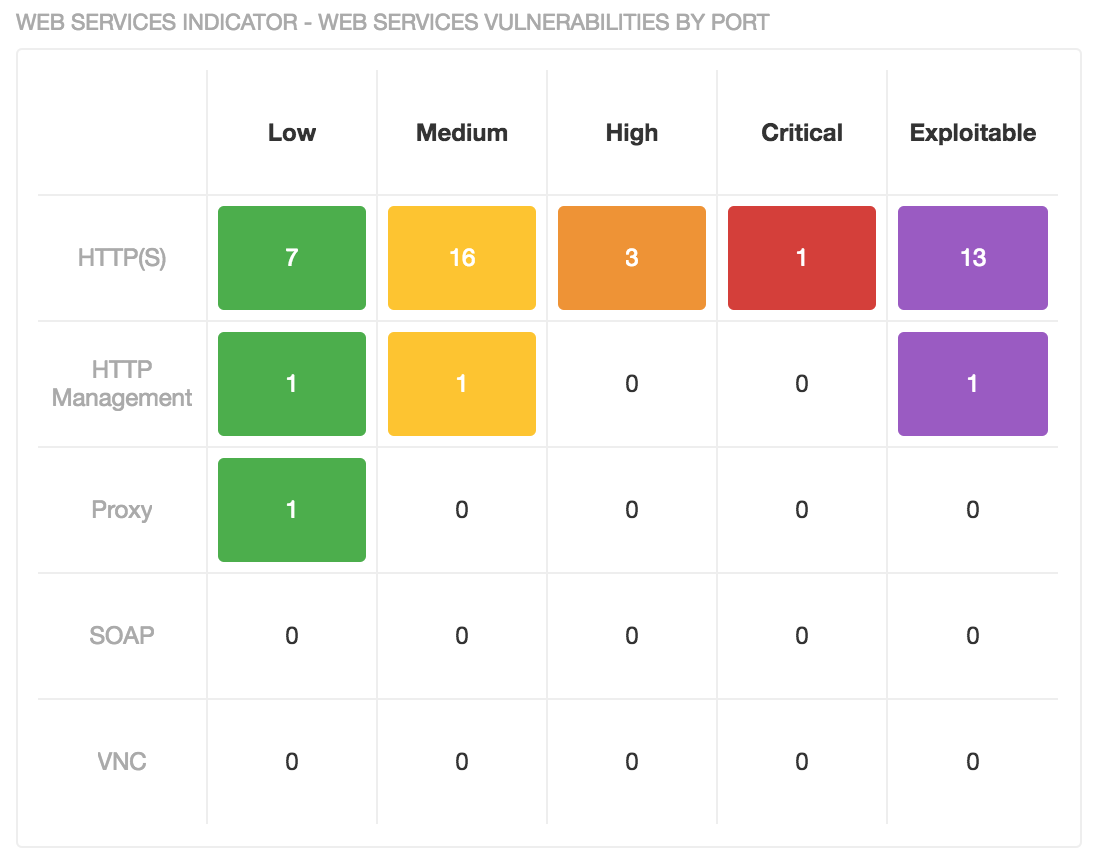
The Web Service Vulnerabilities by Port matrix displays the counts of detected vulnerabilities for specific web service ports by severity. The columns break out the counts by severity as well as exploitability to give you a clearer understanding of vulnerability. HTTP/HTTPS, HTTP Management, Proxy, SOAP, and VNC services are specifically identified by port number. You will likely want to prioritize the identification and remediation of hosts that have critical or exploitable vulnerabilities; use Advanced filters to track down hosts that use specific ports and have critical or exploitable vulnerabilities.
The Hosts with Web Service Vulnerabilities by Plugin Family matrix provides counts of plugin results from four different families by severity. The four families included are CGI Abuses, Databases, FTP, and Web Services. The columns display counts for each severity as well as for exploitability. By prioritizing the areas with critical and exploitable vulnerabilities, I can more effectively secure my network against intrusion and infection. Oftentimes simply applying the patches, updates, or upgrades needed to remediate a critical vulnerability will also take care of others.
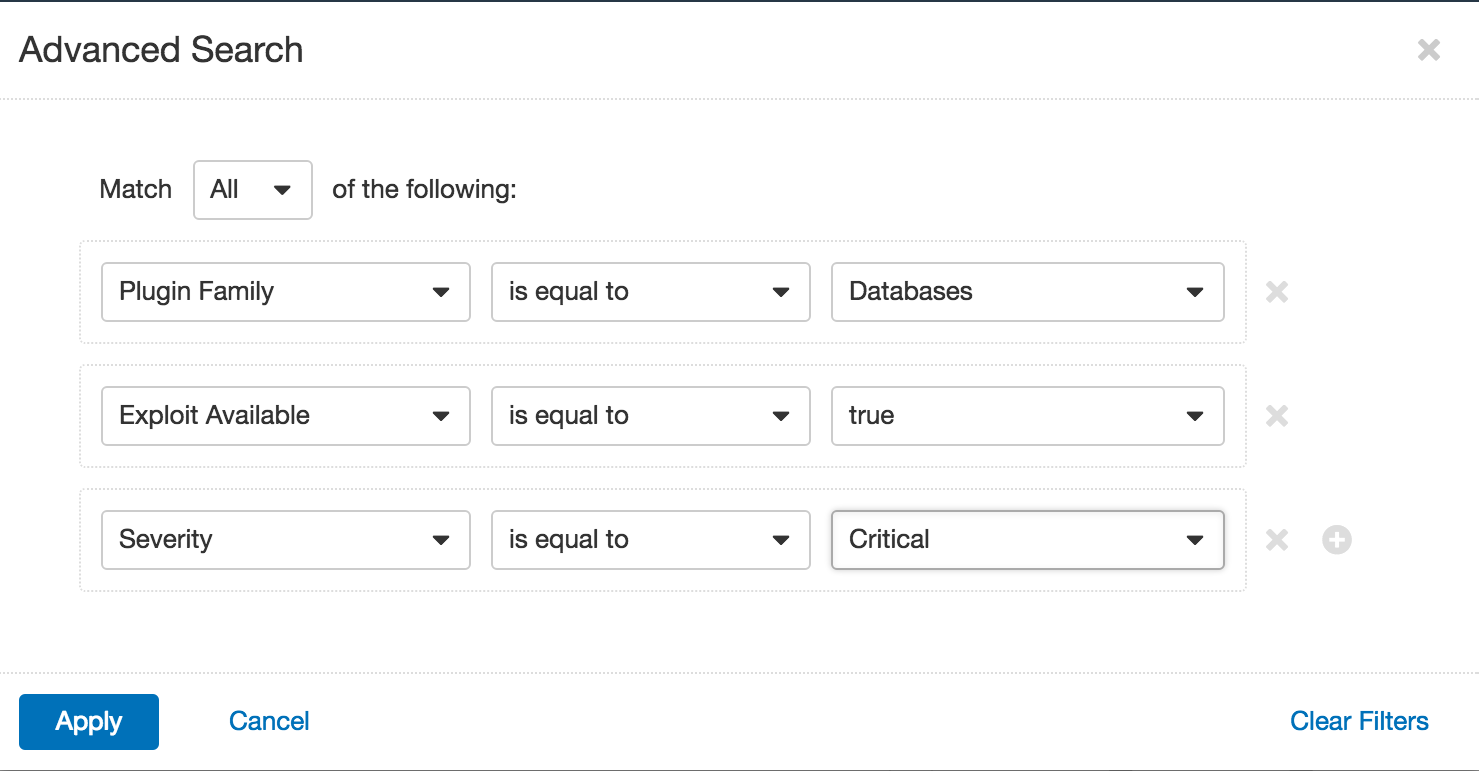
To track down the most severely impacted hosts, use an Advanced filter for the plugin family, severity, or exploitability. This can help to identify the hosts that are affected by relevant vulnerabilities and give insight into how to respond:
A variety of other Advanced filters can be used to investigate scan results related to web services. For example, adding a filter for CPE, hostname, or vulnerability state can help to focus efforts on securing web services in your environment.
Reducing risk
As you have likely inferred through reading this review of the Web Services Indicator dashboard, the primary goal is the ability to monitor the degree of vulnerability due to web services. Gaining insight into the available links, malicious and benign, enables you to ensure that your users can connect where they need to without exposing your organization to exploitation. The information in this dashboard also enables you to detect outdated configurations that should be targeted for removal or upgrade in order to dramatically reduce the risk of exploitation. With the ability to focus the lens on web service vulnerabilities by port, protocol, or plugin family, you can be ready to demonstrate where the organization’s greatest risk lies. By gathering all this insight, you can be prepared to enlighten your organization’s leadership and garner the support you need to effectively defend your network.
Try Tenable.io
Tenable.io provides accurate information on how well your organization is addressing security risks, and helps track improvements over time. Try Tenable.io Vulnerability Management free for 60 days.
- Vulnerability Management
- Vulnerability Scanning