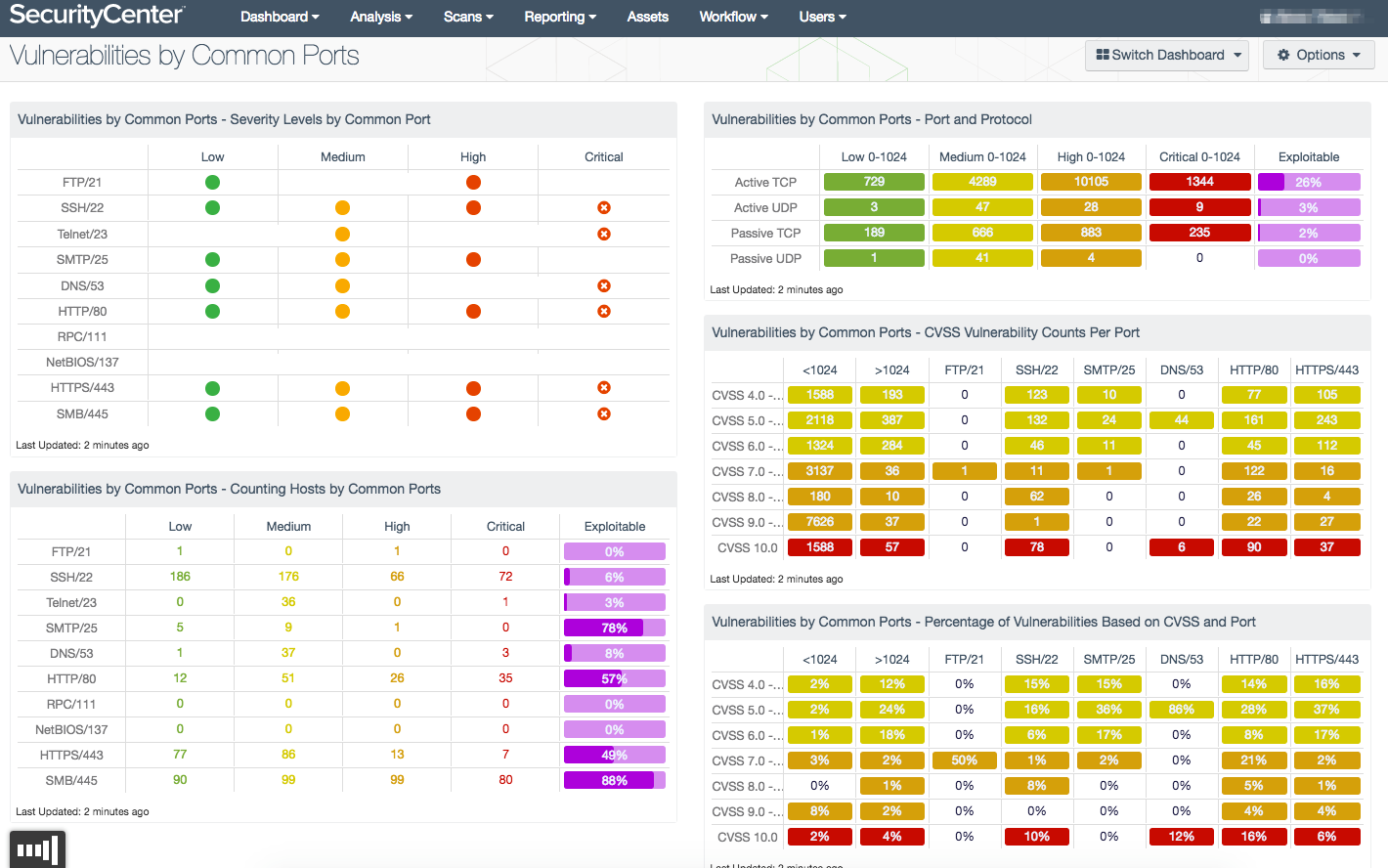
Vulnerabilities by Common Ports Dashboard
Vulnerabilities within network services may result in data loss, denial of services, or allow attackers to facilitate attacks against other devices. Checking for insecure or non-essential services is critical to reducing risk on the network. By identifying open ports along with their associated services, you can ensure said services are necessary and the associated risks are mitigated accordingly. Leveraging Tenable.io™ enhanced vulnerability management capabilities provides an effective way to detect port and service related vulnerabilities, and provides insight into hidden security risks, enabling you to make better informed decisions to protect your organization.
The vast majority of network attacks are focused around easily identified vulnerabilities which can be exploited
The vast majority of network attacks are focused around easily identified vulnerabilities which can be exploited. Targeted attacks utilize a particular vulnerability and a well defined methodology. The Tenable.io Vulnerabilities by Common Ports dashboard leverages a variety of port filters to display vulnerability information in multiple ways. This dashboard can assist you in identifying any potential risk associated with open ports and services.
What are we protecting and why are open ports important?
A port can be thought of as a refinement of a computer's IP address. A packet destined for an IP address will be routed to the device that owns that particular IP address. This IP address only identifies the device on the network. A port further defines where that packet should be delivered, and defines the type of connection that should be made. An open port is essential for devices using a specific protocol to connect with each other. The Internet Assigned Numbers Authority (IANA) has developed several port categories:
- 1 to 1023 are known as Well Known Ports
- 1024 to 49151 are known as Registered Ports
- 49152 to 65535 are known as Dynamic Ports
Well Known Ports usually make some type of network connection, and are typically assigned to a particular network protocol. These well known ports are described by the IANA as ports that “can only be used by system (or root) processes or by programs executed by privileged users.” Ports in this range are assigned a specific network protocol. Registered Ports are defined as ports that “can be used by ordinary user processes or programs executed by ordinary users.” Registered ports are typically available to any program that wishes to use them. While the IANA does in fact register port numbers in this range, they do not assign a network protocol. Finally, Dynamic Ports are defined as “unassigned and unregistered ports for private applications, client-side processes, or other processes that dynamically allocate port numbers.”
Increasing network visibility with port usage data
“Common ports” is a further refinement of the port ranges of Well Known Ports to describe those ports that are commonly found across multiple systems. For example, you will likely find ports such as 22/SSH, 25/SMTP, 80/HTTP, and 443/HTTPS, open within most organizations. Vulnerabilities associated with those ports can be easily targeted for intrusion by attackers. Understanding what ports are open within the network is a good step in reducing the probability of compromise, and in some cases improving performance.
Understanding what ports are open within the network is a good step in reducing the probability of compromise
Network attacks are not always quickly identifiable. Many attacks are low and slow, creating command and control channels that allow them to exfiltrate more data and remain undetected for longer periods of time. The complexity of networks, and the multitude of open ports across an organization make identifying threats increasingly difficult. The simplest, most straightforward, and costliest approach is a reactive stance where you wait for something to happen and fix it. But that’s not the best approach. The best solution is to proactively scan and analyze the network infrastructure. Tenable.io enables analysts to compare known open ports between scans. New active ports and vulnerabilities can be detected, avoiding potential blind spots where new services are installed or enabled.
Setting attainable goals
The Vulnerabilities by Common Ports dashboard identifies vulnerabilities associated with commonly used ports, and provides analysts with a reference point to identify port related vulnerabilities. This is not to say that ports themselves are vulnerable, as ports themselves do not have vulnerabilities. Vulnerabilities exist in the services associated with the ports. During a scan, ports are queried. The results of the query may be a banner, or other information that is returned by the service running on the specified port. The information is utilized to quickly and easily determine what service is running on the port, and if a vulnerability has been identified.
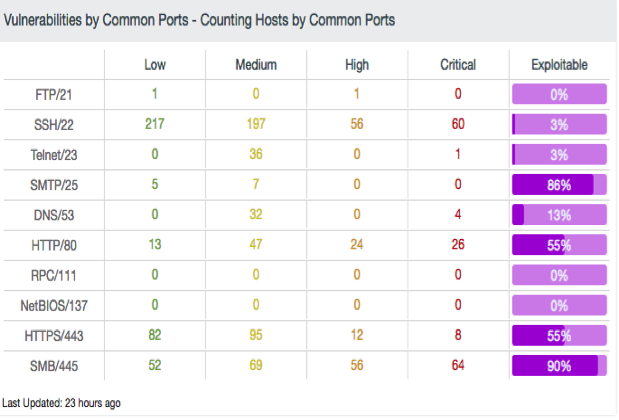
Two components that aid analysts in easily attaining these goals are the Counting Hosts by Common Ports and the Port and Protocol components. Each component communicates risks and aids in the identification of vulnerabilities, unknown services, or backdoors, which are associated with various open ports and services. The Counting Hosts by Common Ports component enumerates vulnerable hosts providing details based on specific ports and severity levels.
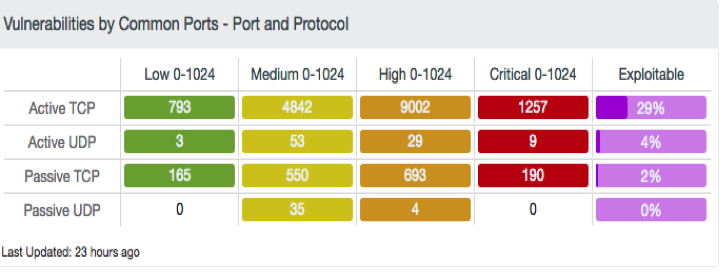
The Port and Protocol component also provides a count of vulnerabilities by severity level, adding active and passive vulnerability results by TCP and UDP protocol. Port ranges from 0-1024, covering all Well Known Ports, along with severity levels of low, medium, high, and critical, are displayed. With each component, a percentage of exploitable vulnerabilities is also displayed.
Using CVSS to identify vulnerabilities by ports
The Common Vulnerability Scoring System (CVSS) provides a robust and useful scoring system for vulnerabilities. CVSS is owned and managed by FIRST, a US-based non-profit organization, whose mission is to help computer security incident response teams across the world.
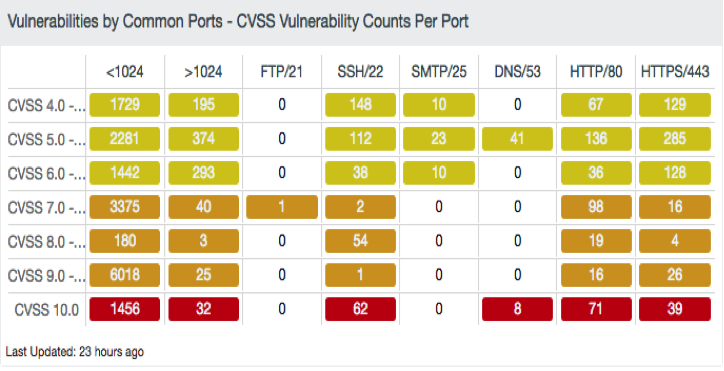
CVSS is widely used, providing an open and universal standard for severity ratings, and helps determine the urgency and priority of responses. Vulnerabilities can be quickly identified and tracked based on CVSS score. Within the dashboard’s CVSS Vulnerability Counts per Port component, vulnerabilities can be selected by severity or port range. Analysts can quickly identify and select vulnerabilities and mitigate risks due to unnecessary and vulnerable services.
The CVSS Vulnerability Counts per Port component uses a combination of CVSS scores and severity ranking to communicate the risk of discovered vulnerabilities.
Details for ports vulnerabilities less than 1024, greater than 1024 and unique filters for FTP, SSH, SMTP, HTTP and HTTPS are included. The colors used to communicate the severity levels are yellow (medium), orange (high), and red (critical).
Wrapping up
As you work to address your risk mitigation tasks and track progress, the Tenable.io Vulnerabilities by Common Ports dashboard provides key analytics. Use the dashboard to greatly reduce the time and effort to review and mitigate risks associated with common ports. Whether you are communicating up the chain, to peers, or to your team, this dashboard provides a thorough look at your outstanding risk with ports and services.
Interested in learning more about Tenable.io?
- Visit the Tenable.io area of our website
- Start a Tenable.io Vulnerability Management trial today
- Vulnerability Management