Unauthorized Call and Webcam Access Vulnerability in Zoom Mac Client (CVE-2019-13450)

A zero-day vulnerability in Zoom could potentially lead to a remote code execution attack. Here’s what you need to know.
Background
Security researcher Jonathan Leitschuh has disclosed a zero day in the Zoom client for Mac, that allows an attacker to force a user to join a Zoom call with their webcam enabled. The disclosure blog also suggests this could potentially lead to a remote code execution attack (RCE), which may have been found by other researchers as well but remains undisclosed and unconfirmed. According to the research, a web server running on port 19421 is present if the Zoom client on Mac has ever been installed.
This Zoom vulnerability is bananas. I tried one of the proof of concept links and got connected to three other randos also freaking out about it in real time. https://t.co/w7JKHk8nZy pic.twitter.com/arOE6DbQaf
— Matt Haughey (@mathowie) July 9, 2019
Analysis
Malicious HTTP requests can be sent to the web server installed alongside the Zoom Mac client that launches a video call with the attacker, with the affected user’s webcam enabled. These requests cannot override user configuration though, so if a user has disabled the automatic webcam, they may still be joined to a call, but their webcam will not be enabled. The researcher also mentions CVE-2018-15715, a Zoom message spoofing flaw discovered by Tenable researcher David Wells, which could be used in conjunction with CVE-2019-13450 to execute an RCE attack.
Proof of concept
The advisory blog provides the following lines of code that an attacker could embed in their site to initiate a call with a vulnerable user:
And the following line enables the webcam for users with automatic video turned on:
Vendor response
Zoom has responded to the disclosure with additional information on how it’s going to improve the user experience to alleviate concerns in the future. Zoom also noted that the Denial of Service (DoS) vulnerability reported by the researcher (CVE-2019-13449) was fixed in May 2019 (Client version 4.4.2).
Solution
Zoom has released an update for the Mac client (4.4.53932.0709) that removes the web server and allows users to fully uninstall Zoom from the client. That update can be applied from the Zoom client or downloaded manually here. Zoom has also stated that it plans to provide further updates over the course of the coming weekend (July 12).
Users can disable automatic video in Zoom, which can be found here in your user settings:
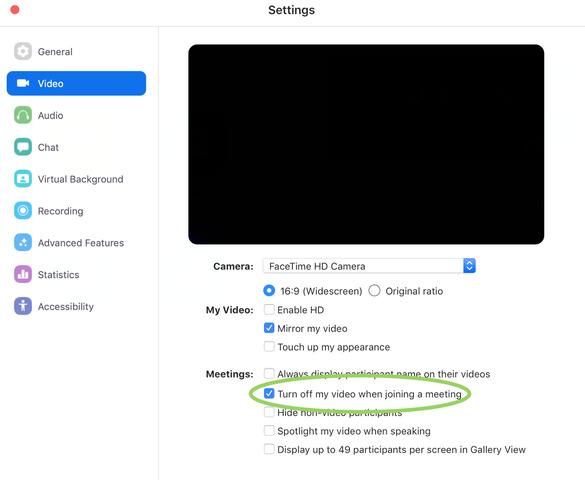
Image Source: Jonathan Leitschuh
Identifying affected systems
A list of Nessus plugins to identify this vulnerability will appear here as they’re released.
Get more information
- Disclosure advisory
- Response from Zoom
- CVE-2019-13450: Zoom Vulnerability Discovered by Tenable Research
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io.
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


