ThemeGrill Demo Importer Vulnerability Actively Exploited in the Wild

Severe vulnerability in ThemeGrill Demo Importer WordPress plugin is being actively exploited in the wild. Users should upgrade to version 1.6.3 ASAP.
Contexte
The ThemeGrill Demo Importer WordPress plugin allows users to import ThemeGrill theme demos in one click. Versions 1.3.4 to 1.6.2 are vulnerable to a remote unauthenticated database wipe and authorization bypass vulnerability. Users are encouraged to upgrade to version 1.6.3 as active attacks have been reported in the wild against users on 1.6.2 and below.
Analyse
On February 15, WebARX disclosed a vulnerability in the ThemeGrill Demo Importer for WordPress, which could allow an unauthenticated, remote attacker to execute administrator functions, including reverting all the site’s settings back to their default configuration and wiping all the database tables.
To exploit this vulnerability, a ThemeGrill theme must be installed and activated on a site. If there is an administrative user with the username ‘admin,’ then an attacker will also be automatically logged in as ‘admin’ after the site is wiped.
Démonstration de faisabilité (PoC)
There is no public proof of concept (PoC) available at this time, but attacks have been reported by WebARX, and a list of known malicious IPs can be found at the bottom of the WebARX disclosure page.
Vendor response
On February 16, ThemeGrill released 1.6.2 to address this vulnerability. However, ThemeGrill released version 1.6.3 on February 18 to address issues with the initial fix. Version 1.6.3 removes the automatic invocation of a full reset, and instead directs the user to the plugin’s reset wizard. This comes after reports that users on version 1.6.2 were still being exploited.
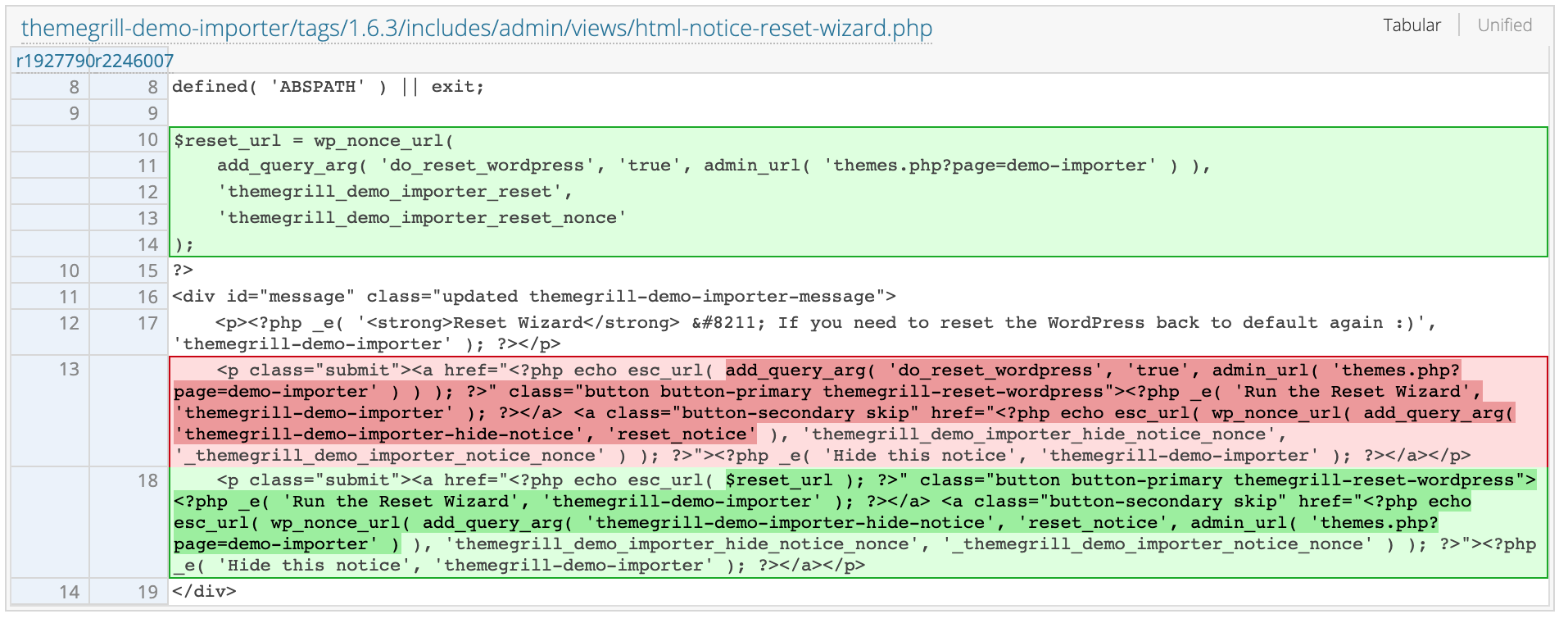
Solution
At the time of publication, there is no known effective workaround that would not disrupt functionality of the plugin. Users are encouraged to upgrade to version 1.6.3 of the plugin for mitigation.
Identification des systèmes affectés
Une liste de plug-ins Tenable permettant d'identifier cette vulnérabilité apparaîtra ici au fur et à mesure de leur publication.
En savoir plus
- ThemeGrill Demo Importer WordPress Plugin Page
- WebARX Disclosure Page
- ThemeGrill Demo Importer 1.6.3 Source Changes
Rejoignez l'équipe SRT de Tenable sur Tenable Community.
Apprenez-en plus sur Tenable, la première plateforme de Cyber Exposure qui vous permet de gérer votre surface d'attaque moderne de manière globale.
Profitez d'un essai gratuit de 30 jours de Tenable.io Vulnerability Management.
- Vulnerability Management



