Staying Ahead of the Curve
As malware attacks continue to make headlines, many organizations struggle to stay ahead of the complex, evolving threat landscape. Attackers use both old and new ways to deliver malware through exploiting existing vulnerabilities, evading security solutions, and using social engineering to deliver malicious payloads. Millions of unique pieces of malware are discovered every year, and even with the best security controls in place, monitoring the thousands of endpoints within your network for malware can be nearly impossible.
Use Tenable.io to quickly address systems that are at risk
Once inside your network, malware can disable security controls, gain access to privileged accounts, replicate to other systems, or maintain persistence for long periods of time. If these risks are not addressed quickly, they can result in long term, devastating consequences for any organization. Using the Malicious Code Prevention Report from Tenable.io™ provides you with the visibility needed to quickly address systems that are at risk.
Malware scanning
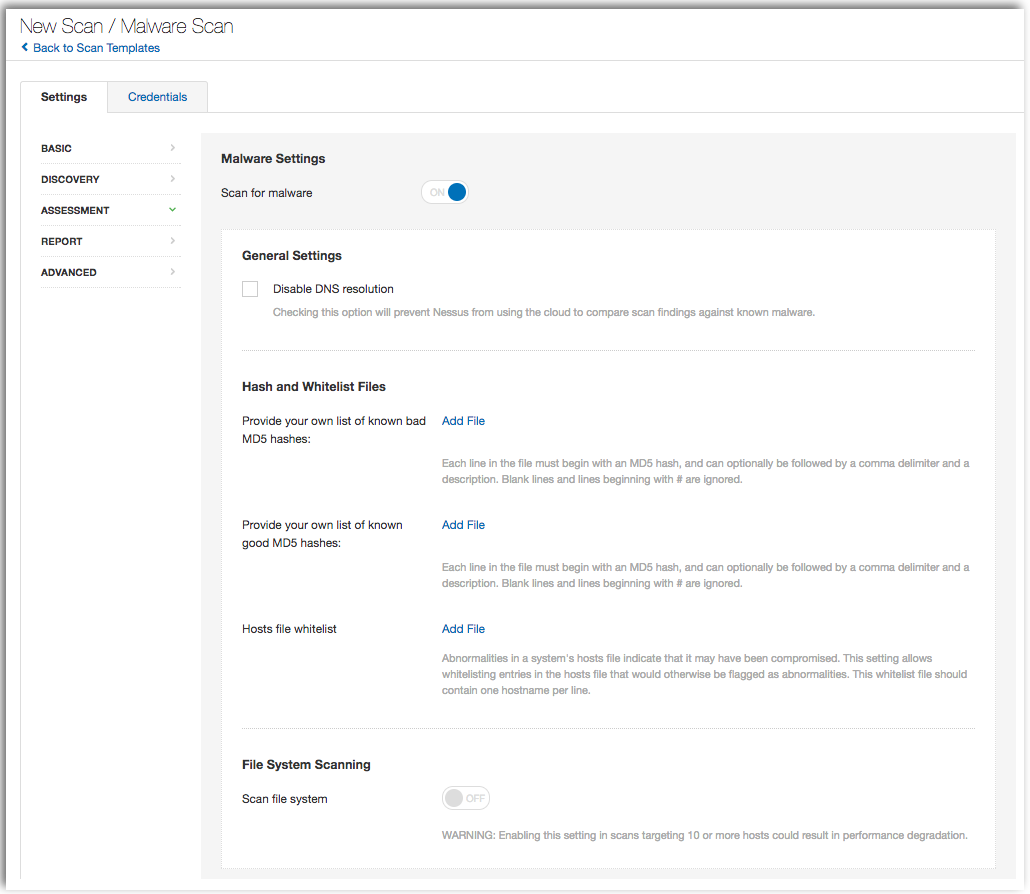
Tenable.io includes a customizable malware scan template where you can incorporate both good and bad known MD5 hashes, along with a hosts file whitelist. On Windows systems, hosts files contain commented lines of text that consist of two localhost address entries. Most systems will query local DNS servers to resolve domain names to IP addresses. Some organizations will add entries into hosts files for dedicated systems within their environment or to block unauthorized websites. Once a hosts file is modified, the local system will use the entries within the hosts file first and bypass records within your DNS server.
Malware also targets the hosts file to insert redirects to malicious sites or block security solutions from obtaining patches and security updates. For organizations utilizing the hosts file, the Malware Scan template provides you with the ability to add whitelist entries that would otherwise be flagged as abnormal by existing security solutions within your environment.
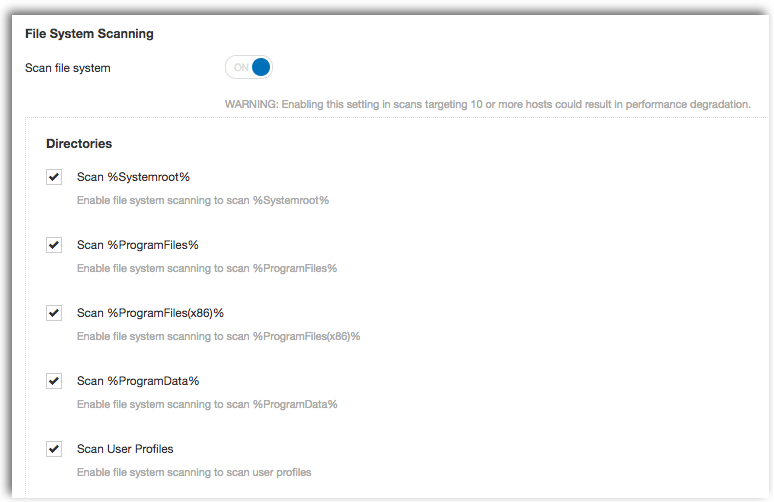
Enabling the File System Scanning option enables you to scan specific directories within your Windows environment such as the C:\Windows, C:\Program Files, and User Profile directories that are frequently used to install malware. You can also scan malware within directories such as C:\ProgramData that are hidden by default on Windows systems.
Organizations can have any number of mapped drives and devices connected to a system. Most anti-virus solutions only scan default directories such as the C:\ drive, and without additional rules in place, malware could easily bypass this security control via flash drive or external USB drive.
The Malware Scan template provides an additional layer of security to scan network drives and attached devices that may not be targeted by your anti-virus solution
The Malware Scan template provides an additional layer of security to scan network drives and attached devices that may not be targeted by your anti-virus solution. Using the Custom File Directories option, you can include a list of directories within your scan to target mapped drives and attached devices.
Yara rules can also be incorporated into your Tenable.io malware scan. Using a combination of regular expressions, text strings, and other values, Yara will examine systems for specific files that match values within the rules file.
Vulnerabilities
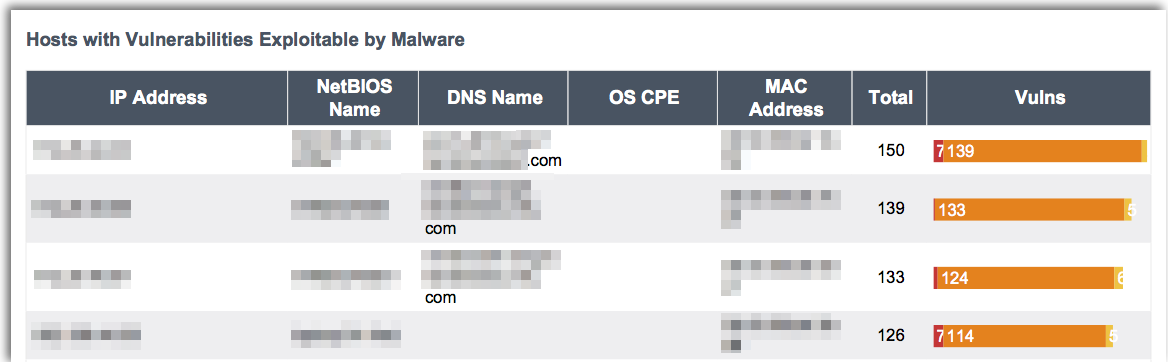
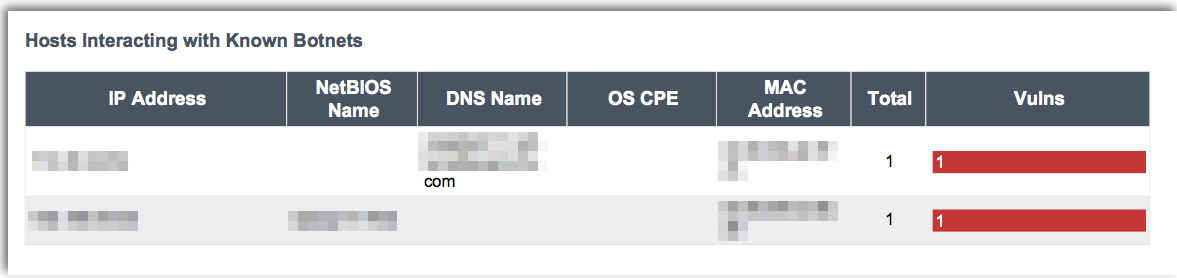
The Malicious Code Prevention report provides a comprehensive overview of systems infected with malicious backdoors, hosts communicating with botnets, and vulnerabilities that can be exploited by malware just to name a few.
Along with malware and malicious processes, this report also highlights systems with vulnerabilities that are exploitable by malware. Exploitable vulnerabilities can provide attackers with a backdoor into your network to enable privilege escalation or launch malicious code.
Tenable.io uses both active and passive methods to detect malicious content
Tenable.io uses both active and passive methods to detect malicious content, including web traffic analysis, md5sum matching, public malware databases, and links pointing to known malware operators. Web servers hosting malicious content are also included within this report. Malicious code can be injected into website due to a cross-site scripting (XSS) or SQL injection vulnerability.
Attackers often target websites to deliver malicious payloads to a larger audience through message boards or blog posts. Malicious code often remains hidden within iframes, JavaScript code, and other embedded tags that link to third-party websites. This data can help you target and remediate issues on web servers before critical assets or services are impacted.
Botnets often use the HTTP protocol as well as encryption to evade detection by modern security solutions. Information reported by Nessus® and Nessus Network Monitor highlights active inbound and outbound communications with command and control (C&C) servers.
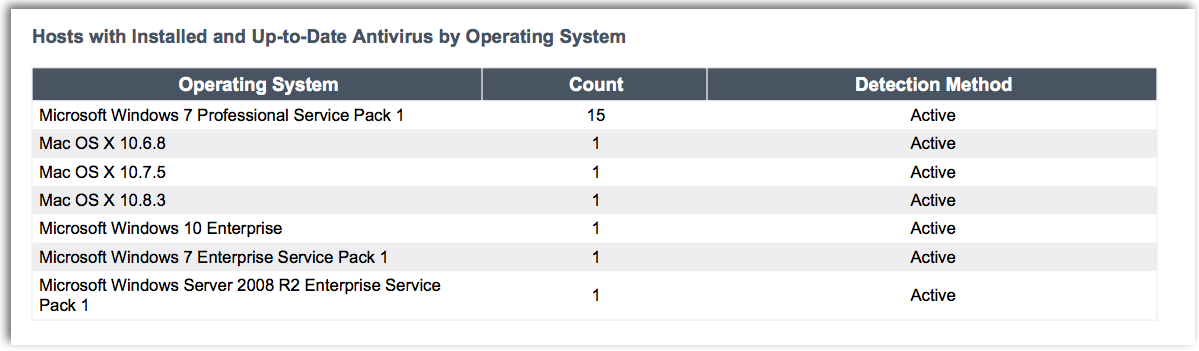
Keeping your anti-virus clients updated helps to ensure your systems remain protected from malware. This report provides valuable information on the status of your anti-virus and anti-malware solutions, ensuring that they are installed and up to date. The Malware Protection chapter provides a summary of hosts running up-to-date anti-virus clients per operating system.
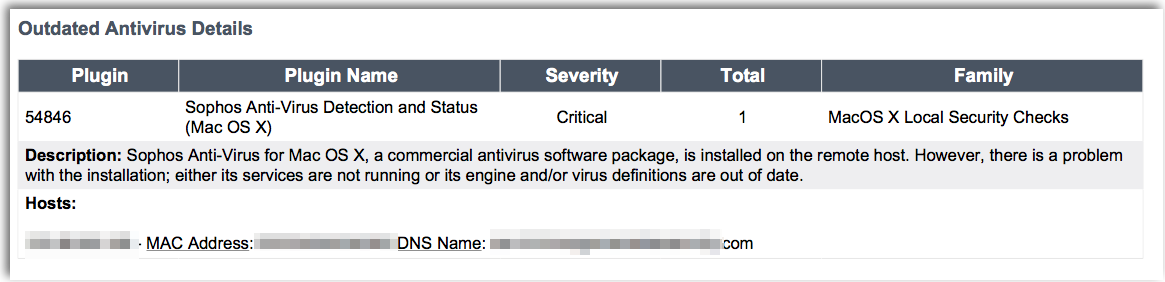
Tenable.io will analyze hosts with outdated anti-virus clients and provide targeted information you can use to remediate issues with anti-virus clients. Data is collected from Nessus that checks the status of various anti-virus clients across Windows, Linux, and Unix-based platforms. Using this information can also help you determine if your anti-virus client has been disabled.
No organization is immune from vulnerabilities and attacks
No organization is immune from vulnerabilities and attacks. Knowing how systems are compromised can help target response efforts and minimize future damage. Tenable.io provides you with critical insight needed to measure the effectiveness of your security program, and to gain insight into your current risk posture. Using the Malicious Code Prevention report by Tenable.io provides you with targeted information to prioritize remediation efforts, close malicious entry points, and stay one step ahead of attackers and other persistent threats.
Start with Tenable.io
To learn more about Tenable.io, visit the Tenable.io area of our website. You can also sign up for a free trial of Tenable.io Vulnerability Management.
- Malware
- Reports
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Vulnerability Management