Security 2.0: Assuring that You're Making the Right Security Investments

It’s time to learn new ways from old. That was the theme for my recent keynote at the 2015 RSA Conference Asia Pacific and Japan last week in Singapore. Although my keynote specifically addressed why the Asia Pacific region can lead the next evolution of security, it’s an applicable message for all of us in the information security industry. Consider some challenges that affect all of us.
Technology adoption
We all know that mobile, cloud, and the Internet of Things are the technologies of the future, but how will we secure them? These new technologies change the assumptions we have used in the past to secure technology. Here are two examples:
The adoption of mobile devices has changed the attack surface. We are no longer protecting corporate assets, connected to corporate networks, accessing data from our data centers. BYOD means we don’t own the assets; they are not connected only to our corporate networks; and they access data from anywhere in the world. These are new challenges we all need to solve.
Another emerging trend is Singapore’s Smart Nation Initiative. Technology is at the heart of the initiative to improve every aspect of citizens’ lives. Although focused within Asia Pacific, Singapore will set an example for the rest of the world for implementing smart systems. These systems will deploy devices in homes, cars, and even as wearables. How will we secure these new devices? Traditional endpoint security products will not be installed on these devices. Battery life and performance, not security, will be key design criteria for these new devices. Data collected from these devices will be stored in the cloud, whether owned by the government or an independent vendor. How will we protect this data in the cloud? Our traditional data center security products may no longer work.
Skill sets
By 2020, global demand for security products and services will create a shortage of 1.5 million information security professionals. This is not an excuse, it’s just a fact. This will impact all of us.
The ability to hire a dedicated security staff to deploy and maintain the latest security products is becoming a challenge, and in some countries is just not realistic. Each and every security investment will have to understand the people impact; technology justifications will become secondary.
CISOs must be ready to answer to their executives every time they propose new security investments:
- Is this part of an existing solution I already own?
- Can we find the right resources to maintain a new technology?
- Is it offered as a service?
Regulations
We must learn from our mistakes when it comes to regulations. We cannot continue to treat security as a compliance exercise. We must stop deploying security solutions to meet the letter of the law, instead of the spirit of the law. We all know how this turns out. Breach after breach in the news has taught us that compliance does not equate to security. It’s time to secure our environments regardless of what the law states.
Evolution of security
To evolve and learn new ways, we need to understand our history.
To evolve and learn new ways, we need to understand our history
In the earliest days, our enemies used viruses and worms to attack our computers. These represented the swords of medieval security attacks. And our response as an industry was to deploy anti-virus software and host-based defenses. These represented the shields to protect our assets.
To protect our networks, we deployed firewalls and perimeter defenses. These represented the castles and forts to protect our organization.
This strategy is commonly known as defense in depth: implementing layers of security point solutions to address the latest problem. For years, this strategy provided a level of protection from attacks.
But as we all know, our enemies are winning. The continual growth of the Internet and digital business has only increased the attack surface. This is similar to the invention of gunpowder, which fueled the innovation of firearms and artillery used to penetrate medieval defenses. Today, our enemies are using the Internet to launch sophisticated and targeted attacks from afar that are beating our medieval defenses.
The adoption of emerging technologies is only compounding the problem. Assets and data are no longer within the perimeter, rendering existing perimeter defenses ineffective. Implementing another point solution does not provide the visibility needed to respond and protect our organizations. So where do we go for guidance? The analysts.
The market
The analysts have not made it any easier. We have security markets for:
- Vulnerability assessment
- Web application scanning
- Policy and compliance
- Security information and event management
- Endpoint threat detection and response
- Forensics and incident investigation
- Threat intelligence
And that doesn’t include:
- Governance, risk management, and compliance
- All the security devices, such as firewalls and intrusion detection
- Identity and access management
- Encryption
I’ve been in the industry for over 20 years and even I’m confused. These markets have overlapping use cases and requirements. New security problems are either a new market or are added to an existing large market, making it impossible for any single vendor to solve. It’s time for a new approach.
Security 2.0
Security 2.0 is not a next generation security product or even a point solution, but a collection of critical capabilities integrated together into a complete solution
It’s time to evolve to Security 2.0. Security 2.0 is not a next generation security product or even a point solution, but a collection of critical capabilities integrated together into a complete solution.
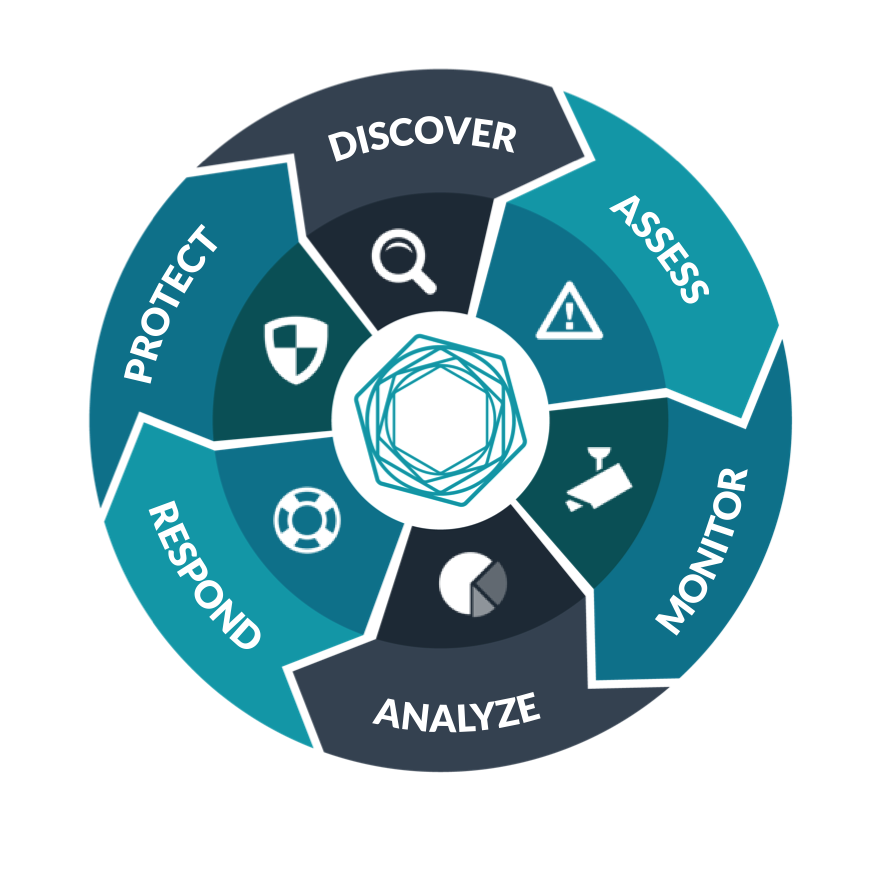
Security 2.0 includes six domains:
Discover is the most basic domain, and the one that every organization still struggles with. Before we can secure our networks, we need to inventory them:
- What assets do I have?
- What data is on them?
- How critical are they?
With emerging technologies, discovery is no longer about servers and workstations; it includes mobile devices, cloud services, virtual applications, and the Internet of Things.
Assess is not just about scanning, but truly understanding the “state” of devices, databases, and applications. This includes remote—but more importantly local—vulnerabilities, configuration settings, and malicious files and processes.
Monitor is not just about log management or SIEM, but truly understanding the “activity” on our networks, devices, and applications. This includes log collection, network packet inspection, and integration of actionable threat intelligence feeds for real-time monitoring.
Analyze is where “state” and “activity” come together to provide real insight into your security posture and whether your security investments are working.
- Am I under attack?
- Have I been compromised?
This includes more than just event correlation, but anomaly detection and behavior analysis.
Respond is the output of analyze:
- How do I respond?
- What assets are affected?
- How do I mitigate loss?
The typical response window of weeks, months, or years must be reduced to days, hours, or minutes. This requires real-time reporting and alerting, and tight integrations with all of your security investments for a quick response.
And finally, Protect is not just about preventive controls, but applying proactive controls to respond to or to mitigate future attacks.
As the need for real-time protection increases, we as an industry must gain the trust of our security investments and processes to automate these protections, including:
- Applying patches
- Modifying configuration settings
- Disabling ports and services
Benefits of 2.0
The benefits of adopting Security 2.0 far outweigh the current approach, by providing comprehensive visibility needed to:
- Quickly identify and respond to attacks
- Truly protect your assets and data
- Assure that your security investments are working
Can you assure that you’ve made the right security investments?
Can you assure that those investments are working?
If you answer “no” to either of these questions, you need to embrace Security 2.0. Use it as your map to continue your security journey. By adopting a more holistic approach to security, you will prepare for the third and final phase of our industry. Yes, we will have another evolution in information security; it will be required to truly make information security a critical business function.
What is that third phase? I’ll save that discussion for a future blog.
- APAC
- BYOD
- Cloud
- Internet of Things
- Mobile Security
- Security Policy


