Reading and Responding to the Verizon DBIR

A few weeks ago, in the Verizon’s 2016 DBIR Report: Understand the Threats, Prepare Your Defenses, and Take Action blog, I shared a quick synopsis of some of the key highlights from the Verizon 2016 Data Breach Investigations Report (DBIR). In that blog, I also mentioned that Tenable researchers were in the process of developing new Assurance Report Cards (ARCs) and dashboards for SecurityCenter™ and SecurityCenter Continuous View™ based on key findings in the Verizon 2016 DBIR.
Today, I’m pleased to announce that new Tenable 2016 Verizon DBIR ARCs and dashboards are now available for immediate download in the SecurityCenter Feed.
Tenable 2016 Verizon DBIR ARCs and dashboards are now available for immediate download
With these new ARCs and dashboards, you can read and respond to the insights and recommendations from the 2016 DBIR to improve the resilience of your security program. Assess yourself against key findings in the 2016 report. Analyze how well your organization conforms to many of the recommendations and best practices highlighted in the 2016 DBIR, and identify ways to improve your program.
Reading and responding to the Verizon 2016 DBIR
Each year, Verizon releases the Data Breach Investigations Report (DBIR) to provide key insights into how to manage risks and avoid security failings, as well as to help organizations of all sizes learn from the experiences of others. Many people examine the report closely, but most organizations struggle to turn DBIR findings into actionable intelligence. As a result, year after year, little, if any, progress seems to be made when it comes to defending against common vulnerabilities and threats.
As in previous years, the Verizon 2016 DBIR notes that the vast majority of all attacks continue to fall into a few basic patterns. Because attackers are relying largely on common attack methods, you can use the Verizon DBIR to dramatically reduce the success of breach attempts by identifying these patterns on your network – helping you prevent a compromise or breach.
In terms of vulnerabilities, this year’s Verizon DBIR continues to show that most organizations don’t have foundational vulnerability management controls in place. Implementing a repeatable, time-bound, policy-based vulnerability management process that includes automated, near real-time assessments is critical, so you can understand the degree of risk DBIR findings pose to your organization and remediate issues before breaches occur.
Automate DBIR assessment, identify threats and effectively improve defenses
It is a good security practice to regularly assess your organization against DBIR findings and recommendations
It is a good security practice to regularly assess your organization against DBIR findings and recommendations. But to reduce the risk, you can’t stop there. Best-in-class security organizations incorporate the insights that the DBIR provides into their security program on an on-going, measurable basis to better defend against today’s biggest IT security risks.
Tenable enables you to assess yourself by providing a unique combination of active scanning, agent scanning, integrations with third-party systems, passive listening and host data, which automatically feed and correlate security data from across your environment into ARCs and dashboards. This helps you to quickly identify whether the top vulnerabilities and threats in the Verizon DBIR are in your environment.
Tenable Verizon 2016 DBIR ARCs and dashboards give you the visibility and context you need to analyze how well your organization conforms to many of the recommendations and best practices highlighted in the Verizon DBIR. You can then use this information to quickly take decisive action, applying the findings in the Verizon DBIR to better protect your organization against threats.
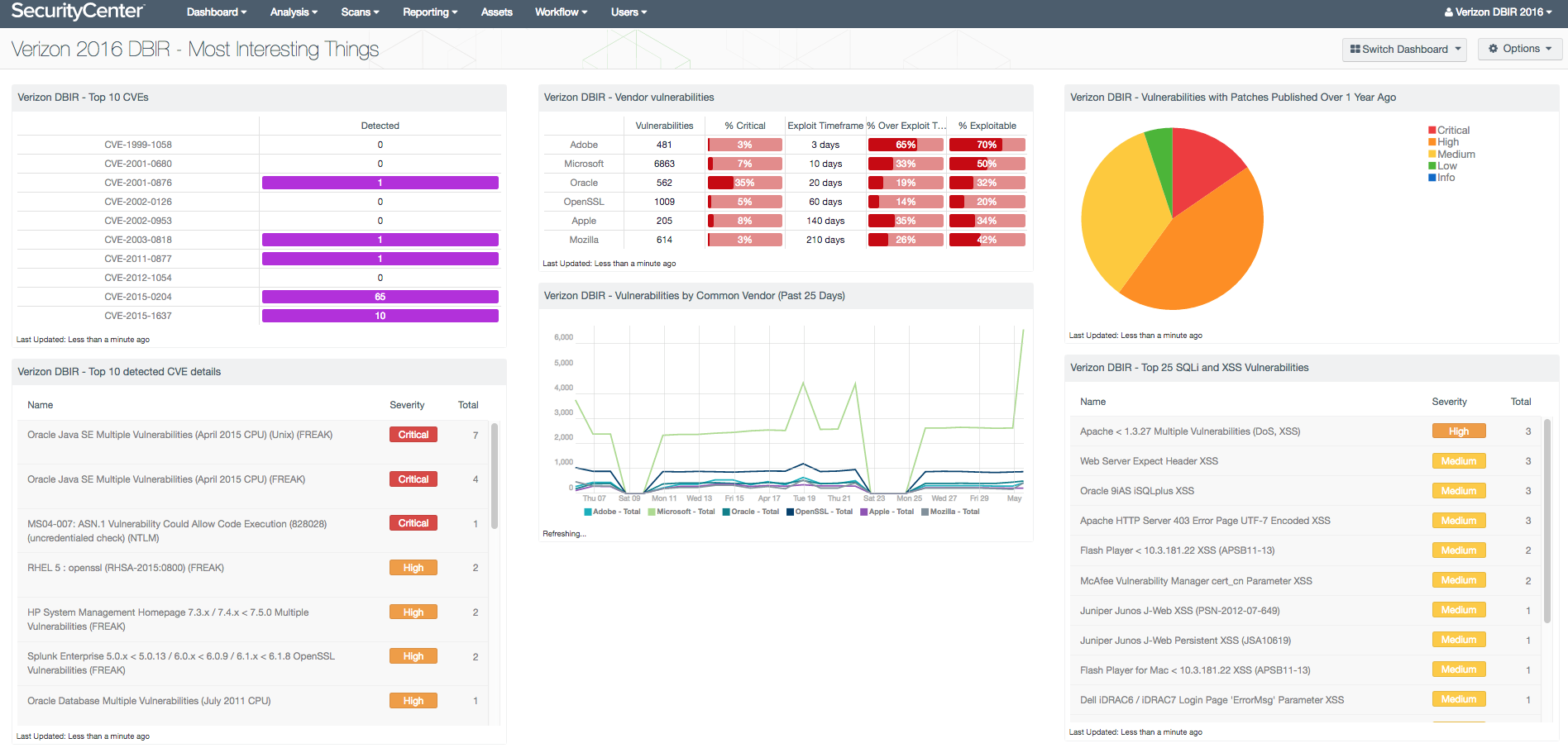
Verizon 2016 DBIR dashboards
SecurityCenter CV dashboards are pre-built, highly customizable dashboards that security managers, analysts and practitioners can use to get the visibility and context they need to connect the dots between the mountains of security data and Verizon 2016 DBIR findings. This helps you more easily determine which events present a real threat in your environment and which are just noise. With dashboards, you can focus action on the events and threats that the Verizon 2016 DBIR highlights as the ones that matter the most, increasing your likelihood of identifying attackers before they are able to find sensitive data.
The following dashboards are now available in SecurityCenter CV:
- Verizon 2016 DBIR - Web Application Vulnerabilities Dashboard
- Verizon 2016 DBIR - Most Interesting Things Dashboard
- Verizon 2016 DBIR - Browser Vulnerabilities Dashboard
- Verizon 2016 DBIR - Vulnerabilities and Malware Collection Dashboard
- Verizon 2016 DBIR - Account Weakness Dashboard
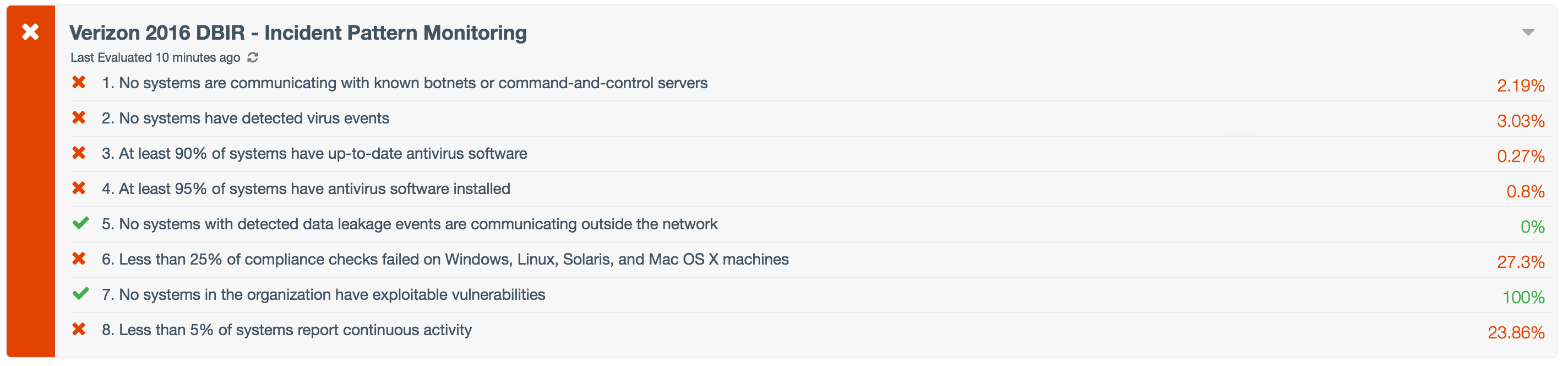
- Verizon 2016 DBIR - Incident Pattern Monitoring Dashboard
- Verizon 2016 DBIR - Network and Host Security Dashboard (formerly called Indicators of Compromise in 2015)
Verizon 2016 DBIR ARCs
SecurityCenter CV provides the industry’s first-ever Assurance Report Cards (ARCs), designed to enable CISOs and security leaders to define their security program objectives in clear and concise terms, identify and close potential security gaps and communicate the effectiveness of their security investments to C-level executives, board members and business managers. Tenable provides several pre-built Verizon 2016 DBIR ARCs that enable you to align the findings and recommendations of the Verizon DBIR to your IT security program using a policy-based approach. You can use the sample policies in Tenable ARCs based on the 2016 DBIR findings, or customize ARC policy statements as needed based on your organizational requirements.
The following ARCs are now available in SecurityCenter CV:
- Verizon 2016 DBIR - Account Weakness ARC
- Verizon 2016 DBIR - Web Application and Browser Security ARC
- Verizon 2016 DBIR - Vulnerabilities and Malware ARC
- Verizon 2016 DBIR - Incident Pattern Monitoring ARC
- Verizon 2016 DBIR - Network and Host Security ARC
- Verizon 2016 DBIR - Most Common Vulnerabilities ARC
- Verizon 2016 DBIR - Vulnerabilities by Common Vendor ARC
Know how you stack up
The Verizon 2016 DBIR is one of the most important reports of the year. Once it’s released, CISOs and other business executives frequently have questions regarding how their organizations measure up against DBIR findings. Use Tenable to assess your security posture within the context of the DBIR and proactively arm yourself with timely, accurate information – before IT security leaders and the business ask.
Use Tenable to assess your security posture within the context of the DBIR and proactively arm yourself with timely, accurate information
Learn more
- Webcast: Register for the upcoming webinar, Assess Yourself Against Key Verizon 2016 DBIR Findings - Tips and Tricks from Tenable Experts at 1:00 p.m. Eastern on Tuesday, June 7th.
- Whitepaper: Assess Yourself Against Key Verizon 2016 DBIR Findings
- Solution Story: Verizon DBIR
This blog was updated on June 1, 2016.
- Announcements
- Dashboards
- Research Reports
- SecurityCenter

