Nessus Receives CIS Certification for Amazon AWS Foundations Benchmark

Tenable Nessus v6.6 has received certification from the Center for Internet Security (CIS) for the Amazon AWS Foundations benchmark; the first and only CIS member to receive that certification.
Tenable is the first and only security vendor to be certified by CIS for the Amazon AWS Foundations Benchmark
Industry standard security benchmarks such as the guides from CIS are one of the best ways to secure a resource. That resource could be a server, software application, network device or even a cloud service such as Amazon Web Service (AWS). If you own or use these resources and are responsible for their security, these guides provide a solid base to your security program. In addition to providing hardening guidance, they also provide peace of mind, knowing that you did the best job you could do to prevent a breach (at least in the eyes of your industry peers). If you follow the recommendations from the guide, the chances of getting breached will be limited. And if an unfortunate breach does happen, you would probably receive less criticism than if you had no policy around it.
That being said, benchmark authors do tend to play a wait-and-watch game when it comes to publishing content for new technologies. In general you will find that hardening guides are written only after a technology has received a certain level of maturity and acceptance. In the fast moving world of technology, where new products and services live and die every day, to say that AWS has reached a certain level maturity and made an impact is an understatement.
For some organizations the advent of cloud services such as AWS has truly been a game changer, and Tenable recognized that value long before it became common knowledge.
The wait-and-watch game played by benchmark authors does serve as a disadvantage for security vendors such as Tenable, because without these benchmarks, there aren’t any generally accepted guides to publish content against. In such scenarios we at Tenable publish our own content based on commonly accepted best practice and vendor recommendations. And that’s exactly what we did more than two years ago when we added support for auditing AWS. With the CIS benchmark released, we are now publishing our audit to assess the configuration of the AWS account, and we are also the first and only security vendor to get certified.
So what is covered under the new CIS AWS guide? Here’s a quick overview.
CIS AWS Foundations Benchmark overview
The CIS benchmark for AWS provides prescriptive guidance for configuring security options for a basic set of foundational AWS services. Here’s the list of services that are within the scope of this benchmark:
- AWS Identity and Access Management (IAM)
- AWS Config
- AWS CloudTrail
- AWS CloudWatch
- AWS Simple Notification Service (SNS)
- AWS Simple Storage Service (S3)
- AWS VPC (Default)
The benchmark is divided into four sections:
Identity and Access Management (IAM)
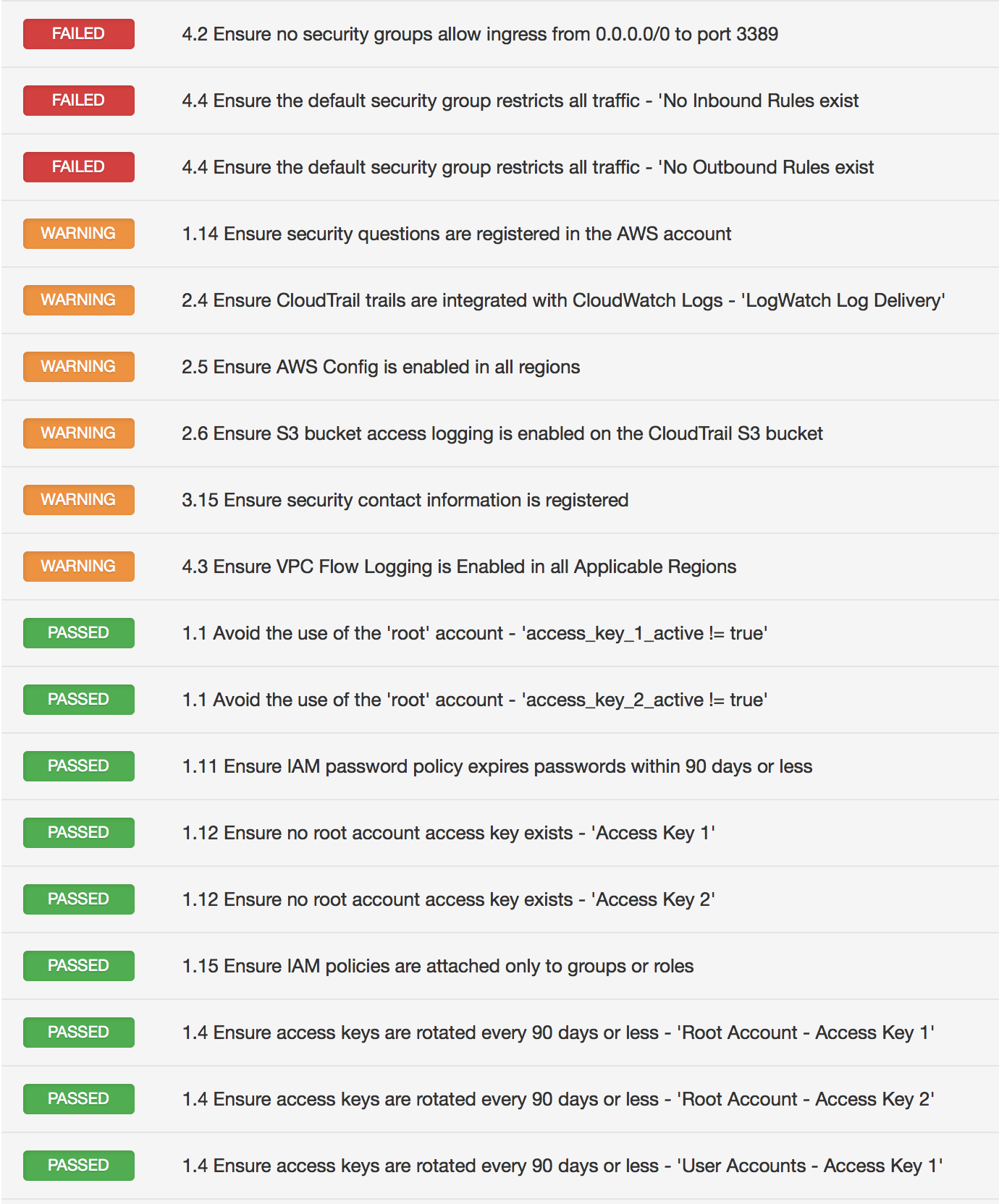
If Amazon Web Services were a kingdom, then the keys to that kingdom would be the “root” account. The root account has unrestricted access to all resources in the AWS account and it must be fiercely guarded and its use limited. This section provides recommendations to limit the use of the root account, and if used, provides necessary monitoring guidance to prevent unauthorized use. In addition, it also recommends using multifactor authentication (MFA), disabling inactive accounts, and having a very strong password policy.
Logging (CloudTrail, CloudWatch, S3, AWS Config)
The use of logging API calls is another important recommendation in this benchmark. It recommends that all AWS API calls should be logged via CloudTrail, and CloudTrail should be configured to send logs to S3 and CloudWatch for long term and real-time analysis respectively. The logs should be encrypted, and the encryption keys should be rotated on a regular basis.
Monitoring (CloudTrail, CloudWatch, SNS)
Monitoring an AWS account is critical to prevent and detect unauthorized use of the account. The benchmark recommends generating alerts by using a combination of metric filters and alarms. Some of the events to monitor and generate alerts against include non-MFA enabled accounts logged in via the console, root account usage, failed authentication attempts, unauthorized changes to IAM, S3, AWS Config and network configuration.
Networking (default VPC)
And last but not least, the networking section makes recommendations for configuring security related aspects of the default virtual private cloud (VPC). The recommendations include prohibiting security groups from allowing unfettered ingress access to remote console services such as SSH and RDP from 0.0.0.0/0, and also ensuring that the default security group restricts all traffic by default.
Sample result
Tenable AWS best practice audit update
Along with the CIS audit, the Tenable best practice audit has also been updated to include recent recommendations. The audit now serves twin objectives: one, to provide a snapshot of your AWS deployment and two, to provide best practice hardening guidance based on the recent update. Both these audit files are now available for download on the Tenable portal.
Wrap up
At Tenable we are always striving to keep our content fresh and up to date. Achieving CIS certification for AWS is just one of the ways for us to meet that goal.
We also realize that AWS is not the only cloud service provider in the marketplace, and there are other cloud service options our customers might consider such as Azure and Rackspace. Over the past few years we have added support for Azure and Rackspace as well, and more recently to OpenStack. So regardless of which cloud computing model or provider you choose, you can rest assured that Tenable has you covered.
- Announcements
- Cloud
- Vulnerability Management