Nessus Helps Harden FireEye Appliances
A new compliance plugin for FireEye appliances is now available for Nessus customers. This new functionality allows you to audit FireEye instances against best-practice hardening guidelines, ensuring that the security appliance and the data contained therein is secure.
FireEye is the creator of threat prevention applications, constantly testing systems for malware.
FireEye is a leader in stopping the new generation of cyber attacks, such as advanced malware, that easily bypass traditional signature-based defenses and compromise over 95% of enterprise networks (based on FireEye end-user data). FireEye has invented a purpose-built, virtual machine-based platform that provides real-time threat protection to organizations across all major threat vectors and each stage of an attack life cycle.
Scanning Requirements
To begin auditing the security of your FireEye installation, you will need the following:
rootor equivalent administrative credentials for the FireEye appliance- SSH access to the targets
- A Nessus policy with plugin ID #70469 (FireEye Compliance Checks) enabled
- The .audit file - Customers may obtain the required .audit file for FireEye systems on the Tenable Support Portal (filename is TNS_BestPractice_FireEye.audit)
What Is Nessus Auditing?
The audit and associated security-related settings recommendations are based on product documentation from FireEye and Common Criteria security guidelines, including:
- Identification and authentication
- Appliance management
- Intelligent Platform Management Interface (IPMI)
- Services enabled
- Encrypted communications
- Malware detection system configuration
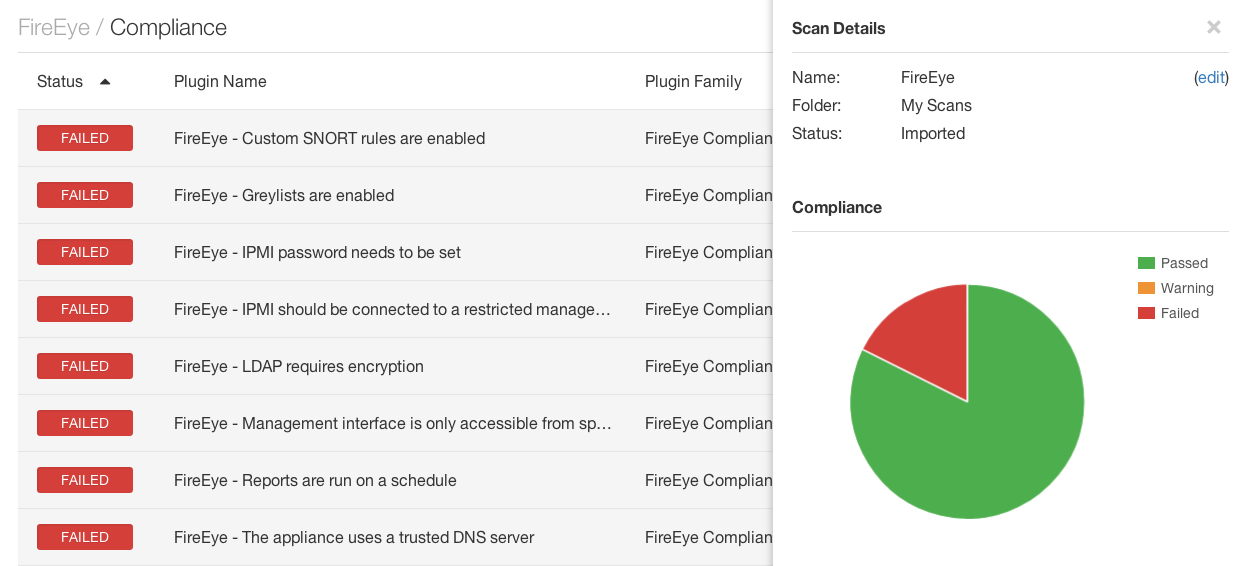
Sample results can be found below. In the first screenshot, the Nessus user interface nicely displays both a listing of the failed audits, in addition to the scan details and pie chart of the findings.
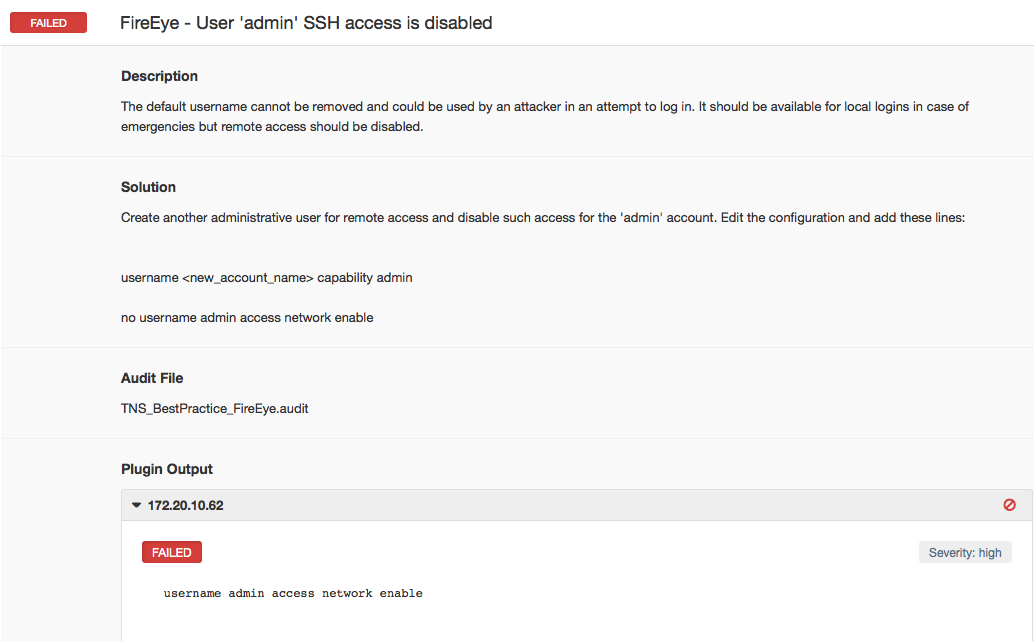
Nessus checks the configuration setting to ensure that the highest-privilege-level account, enabled by default, cannot be used to log into the system remotely. The host below is configured to allow the "admin" account to log in remotely, and therefore has failed the check.
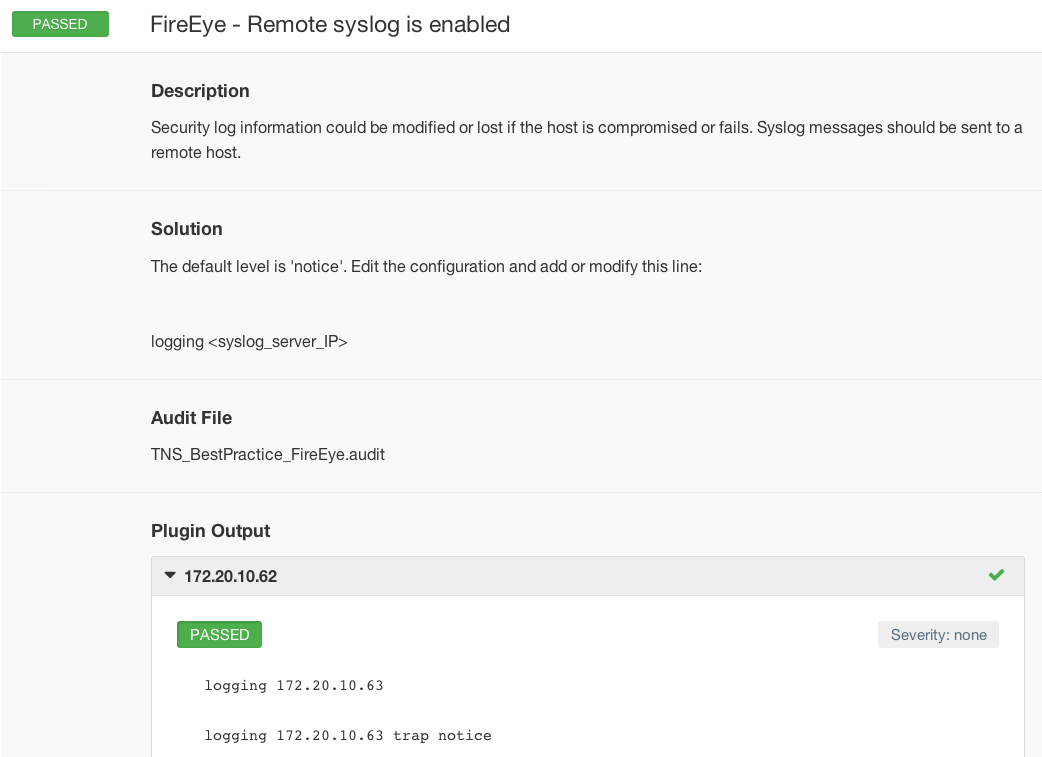
Logging events to a central location, especially from devices collecting information about security-related events in particular, is important. In the following case, the FireEye appliance has been configured to send syslog events to a remote host.
Conclusion
Nessus customers can download all the latest compliance checks from the Tenable Support Portal.
Auditing the configuration of FireEye devices further extends Nessus’ capabilities to help secure your company’s infrastructure. For further information about using Nessus to audit your network, security, or virtual infrastructure, view the following posts:
- Nessus Audits HP ProCurve Routers
- New Nessus Configuration Checks Available for Citrix XenServer
- Nessus Secures NetApp Data ONTAP
- Nessus VMware vSphere/vCenter Audits Available
- Nessus Audits Palo Alto Networks PAN-OS Configurations
- Configuration Auditing Cisco Nexus Operating System (NX-OS) with Nessus
- Nessus Compliance Checks Available for Check Point GAiA
- Nessus Audits Juniper Junos Configuration
- Nessus Cisco Compliance Checks
If you like this feature and plan to use it, please leave us a comment!
- Nessus
- Plugins
- Vulnerability Management

