Microsoft’s March 2021 Patch Tuesday Addresses 82 CVEs (CVE-2021-26411)

In its March release, Microsoft addressed 82 CVEs, including a zero-day vulnerability in Internet Explorer that has been exploited in the wild and linked to a nation-state campaign targeting security researchers.
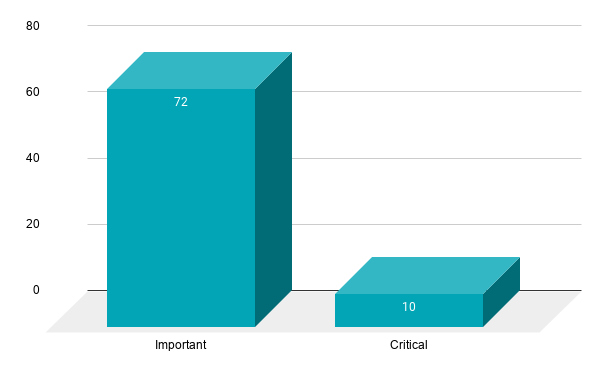
- 10Critical
- 72Important
- 0Moderate
- 0Low
Microsoft patched 82 CVEs in the March 2021 Patch Tuesday release, including 10 CVEs rated as critical and 72 rated as important.
This month's Patch Tuesday release includes fixes for Application Virtualization, Azure, Azure DevOps, Azure Sphere, Internet Explorer, Microsoft ActiveX, Microsoft Exchange Server, Microsoft Edge (Chromium-based), Microsoft Graphics Component, Microsoft Office, Microsoft Office Excel, Microsoft Office PowerPoint, Microsoft Office SharePoint, Microsoft Office Visio, Microsoft Windows Codecs Library, Power BI, DNS Server, Hyper-V, Visual Studio, Visual Studio Code, Windows Admin Center, Windows Container Execution Agent, Windows DirectX, Windows Error Reporting, Windows Event Tracing, Windows Extensible Firmware Interface, Windows Folder Redirection, Windows Installer, Windows Media, Windows Overlay Filter, Windows Print Spooler Components, Windows Projected File System Filter Driver, Windows Registry, Windows Remote Access API, Windows Storage Spaces Controller, Windows Update Assistant, Windows Update Stack, Windows UPnP Device Host, Windows User Profile Service, Windows WalletService, and Windows Win32K.
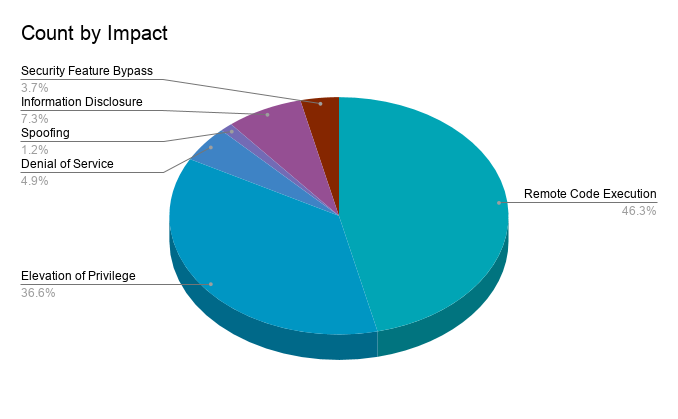
Remote code execution (RCE) vulnerabilities accounted for 46.3% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) flaws at 36.6%.
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 | Microsoft Exchange Server Vulnerabilities
Last week, Microsoft published an out-of-band (OOB) security advisory for four vulnerabilities in Microsoft Exchange Server that were exploited in the wild as zero-days. The unusual decision to release patches OOB underscores how significant these vulnerabilities are. Initial reports claim that over 30,000 organizations may have been compromised as a result of these flaws. Tenable Research published a blog post that provides details on how we can help you identify vulnerable instances of Exchange Server in your environment as well as discover systems that may be compromised.
CVE-2021-26411 | Internet Explorer Memory Corruption Vulnerability
CVE-2021-26411 is a memory corruption vulnerability in Internet Explorer that was exploited in the wild as a zero-day. In order to exploit the flaw, an attacker would need to host the exploit code on a malicious website and convince a user through social engineering tactics to visit the page, or the attacker could inject the malicious payload into a legitimate website.
The vulnerability was publicly disclosed in early February by researchers at ENKI, and has reportedly been linked to a concerted campaign by nation-state actors to target security researchers. This campaign was first disclosed in late January by Google’s Threat Analysis Group, which detailed attempts to trick security researchers into visiting fake security blogs that reportedly hosted the malicious code.
CVE-2021-26877, CVE-2021-26893, CVE-2021-26894, CVE-2021-26895, and CVE-2021-26897 | Windows DNS Server Remote Code Execution Vulnerability
CVE-2021-26877, CVE-2021-26893, CVE-2021-26894, CVE-2021-26895 and CVE-2021-26897 are RCE vulnerabilities found in Windows Domain Name System (DNS) servers. All five of these CVEs were assigned 9.8 CVSSv3 scores and can be exploited by an unauthenticated attacker when dynamic updates are enabled. According to an analysis by researchers at McAfee, these CVEs are not considered “wormable,” yet they do evoke memories of CVE-2020-1350 (SIGRed), a 17-year-old wormable flaw patched in July 2020.
CVE-2021-26896 and CVE-2021-27063 | Windows DNS Server Denial of Service Vulnerability
CVE-2021-26896 and CVE-2021-27063 are denial of service (DoS) vulnerabilities in Windows DNS servers, both receiving a CVSSv3 score of 7.5, and highlighted by Microsoft’s Exploitability Index as “Exploitation Less Likely.” Successful exploitation would result in an exhaustion of resources on the targeted server, causing it to become unresponsive. Exploitation of DNS DoS vulnerabilities usually requires sending a crafted DNS query to a vulnerable server.
CVE-2021-26867 | Windows Hyper-V Remote Code Execution Vulnerability
CVE-2021-26867 is an RCE vulnerability affecting Hyper-V clients that have been configured to utilize the Plan 9 file system (9P). Successful exploitation could allow an authenticated attacker to execute code on a Hyper-V server. Despite Microsoft rating this vulnerability as “Exploitation Less Likely,” the CVSSv3 score assigned to this flaw is a 9.9 out of 10.0. However, it is important to note that Hyper-V clients not utilizing 9P are not affected by this vulnerability.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains March 2021.
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from March 2019 using Tenable.io:
A list of all the plugins released for Tenable’s March 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's March 2021 Security Updates
- Tenable plugins for Microsoft March 2021 Patch Tuesday Security Updates
- Tenable Blog Post for Exchange Server Vulnerabilities
- Tenable Guidance on Identifying and Discovering Compromised Exchange Servers
- ENKI Internet Explorer Zero-Day Analysis
- McAfee: Critical Vulnerabilities in DNS Dynamic Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

