Microsoft’s December 2020 Patch Tuesday Addresses 58 CVEs including CVE-2020-25705 (SAD DNS)

The final Patch Tuesday of 2020 includes fixes for 58 CVEs, including workaround details for a severe vulnerability in Windows DNS Resolver called SAD DNS.
Microsoft patched 58 CVEs in the December 2020 Patch Tuesday release, including 9 CVEs rated as critical.
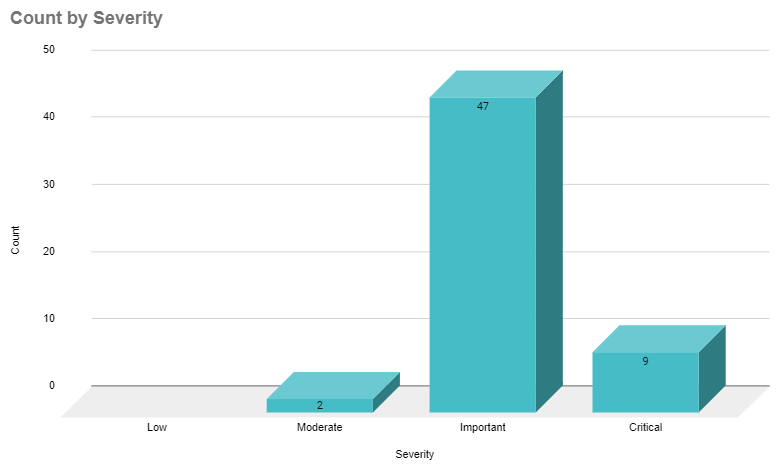
This month's Patch Tuesday release includes fixes for Microsoft Windows, Microsoft Edge (EdgeHTML-based), Microsoft Edge for Android, ChakraCore, Microsoft Office and Microsoft Office Services and Web Apps, Microsoft Exchange Server, Azure DevOps, Microsoft Dynamics, Visual Studio, Azure SDK, and Azure Sphere.
This is a book-end to a year that began with Microsoft addressing 49 CVEs in January of 2020, followed by eight consecutive months with over 90 CVEs addressed. In 2020, Microsoft released patches for over 1,200 CVEs, exceeding 2019’s total of 840.
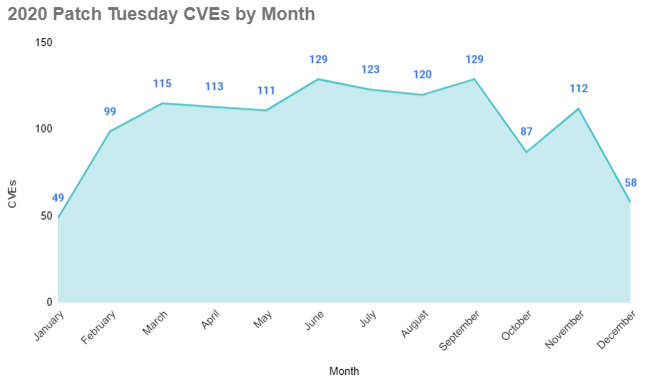
This month’s release did not include any vulnerabilities that were exploited in the wild and no vulnerability was assigned a CVSSv3 score of 9.0 or higher.
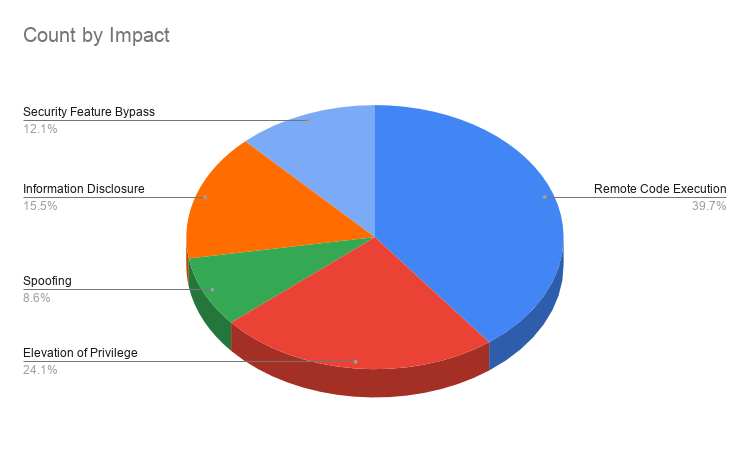
Nearly 40% of the vulnerabilities patched this month were remote code execution (RCE) flaws, followed by elevation of privilege vulnerabilities, which represented approximately 24%. The chart below breaks down the release based on the types of vulnerabilities patched.
The following is a breakdown of some of the notable vulnerabilities addressed this month.
CVE-2020-25705 | Windows DNS Resolver Spoofing Vulnerability
CVE-2020-25705 is a spoofing vulnerability in the Windows DNS Resolver, a component of the Windows TCP/IP stack that is included in each Windows release. As its name implies, the DNS resolver is responsible for resolving DNS queries, such as when browsing to a website like google.com and fetching its IP address because it is easier for users to remember a name like google.com instead of its IP address, which is 142.250.64.78. Since websites like google.com are visited often, it wouldn’t make sense for the DNS resolver to constantly request the IP address for it. To reduce the overhead on these requests, a local copy of the responses to these DNS queries are stored in the DNS cache, which is the crux of this vulnerability.
The vulnerability, dubbed Side-channel AttackeD DNS (or SAD DNS) by researchers at Tsinghua University and the University of California Riverside (UC Riverside), was disclosed at the ACM Conference on Computer and Communications Security in November.

Image Source: UC Riverside
The vulnerability is detailed on the UC Riverside website for associate professor Zhiyun Qian, who was an advisor on this project. The researchers call this a “revival of the classic DNS cache poisoning attack,” which has not been possible since 2008, when it was revealed by security researcher Dan Kaminsky at the Black Hat conference.
For a full breakdown of the vulnerability, we recommend reading this blog post published by Marek Vavruša and Nick Sullivan of Cloudflare.
The researchers have linked to proof-of-concept code for SAD DNS on GitHub, though the resource is currently inaccessible at the time this blog post was published. However, they also shared a YouTube video demonstrating exploitation.
Microsoft released guidance for SAD DNS as part of ADV200013, though they did not explicitly call out the vulnerability by its CVE identifier, which is CVE-2020-25705. Microsoft did not provide patch information, though they did provide a workaround that sets the maximum UDP packet size to 1221.
CVE-2020-17117, CVE-2020-17132, CVE-2020-17141, CVE-2020-17142 and CVE-2020-17144 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2020-17117, CVE-2020-17132, CVE-2020-17141, CVE-2020-17142 and CVE-2020-17144 are remote code execution (RCE) vulnerabilities in Microsoft Exchange. All of these have been labeled by Microsoft as “Exploitation Less Likely” with the exception of CVE-2020-17144, which has been labeled as “Exploitation More Likely.”
The vulnerabilities exist in Microsoft Exchange due to the improper validation of cmdlet arguments. To exploit these vulnerabilities, an attacker would need to be authenticated to the vulnerable Exchange server in order to exploit the flaw.
CVE-2020-17132 is credited to Steven Seeley, a researcher at Source Incite, who is frequently acknowledged for his disclosure of vulnerabilities during Patch Tuesday.
In September’s Patch Tuesday release, Seeley was credited with discovering CVE-2020-16875, which he intended to blog about until he discovered a patch bypass for the flaw. Seeley has now confirmed that CVE-2020-17132 addresses this patch bypass.
CVE-2020-17132 patches the patch bypass apparently https://t.co/BKw0IKSFoB
— ϻг_ϻε (@steventseeley) December 8, 2020
Microsoft Exchange Server remains a valuable target for threat actors with the National Security Agency (NSA) including CVE-2020-0688 as an entry in their list of vulnerabilities known to be exploited by state-sponsored actors. CVE-2020-0688, which was released as part of Microsoft’s February 2020 Patch Tuesday release, has seen continued interest with the development of proofs-of-concept (PoCs) shortly after its release and actively exploited soon after.
CVE-2020-17122, CVE-2020-17123, CVE-2020-17125, CVE-2020-17127, CVE-2020-17128 and CVE-2020-17129 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-17122, CVE-2020-17123, CVE-2020-17125, CVE-2020-17127, CVE-2020-17128 and CVE-2020-17129 are RCE vulnerabilities in Microsoft Excel. All six of these vulnerabilities were assigned a CVSSv3 score of 7.8 and labeled as “Exploitation Less Likely” by Microsoft.
Details about CVE-2020-17123, which is credited to Marcin Noga of Cisco Talos Intelligence Group, have been published on the Talos blog. According to their description, the CVE-2020-17123 is a use-after-free vulnerability in Microsoft Excel. Exploitation of this flaw requires an attacker to socially engineer their victim into opening a malicious XLS file, either via email or hosting the file on a website and convincing the user to download and open it. Successful exploitation would result in remote code execution in the context of the current user. If the user has administrative privileges, it would result in a full system compromise.
While there are no further details for the five remaining Excel vulnerabilities, if they echo CVE-2020-17123 and past Excel flaws, the attack vector could be similar, requiring a user to open a malicious XLS file either via email or by convincing them to download and execute the file from a website. However, Microsoft notes that the Outlook Preview Pane is not affected by these vulnerabilities, which means a victim would need to open the XLS file directly to trigger the exploit.
CVE-2020-17096 | Windows NTFS Remote Code Execution Vulnerability
CVE-2020-17096 is an RCE in Windows NT File System (NTFS), the file system used in Microsoft Windows and Microsoft Windows Server. No user interaction is required to exploit this vulnerability. Depending on the attacker’s position, there are a few avenues for exploitation. For an attacker that has already established a local position on the vulnerable system, executing a malicious application that exploits the flaw would result in an elevation of privileges. Alternatively, a remote attacker could exploit the flaw by sending malicious requests to a vulnerable system, so long as they could access it over the Server Message Block version 2 protocol (SMBv2). Successful exploitation in this context would grant the attacker arbitrary code execution.
CVE-2020-17118 and CVE-2020-17121 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-17118 and CVE-2020-17121 are RCE vulnerabilities in Microsoft SharePoint, which are labeled as “Exploitation More Likely” by Microsoft.
For CVE-2020-17121, Microsoft notes that the attack is network-based and, provided the targeted user has the required privileges, an attacker could gain access to SharePoint to craft a site and in turn remotely execute arbitrary code within the kernel.
The Zero Day Initiative (ZDI) is credited with reporting CVE-2020-17121 and offers additional details about the vulnerability in their summary blog. They note that exploitation would allow the execution of arbitrary .NET code in the context of the SharePoint Web Application service account. In SharePoint’s default configuration, it allows authenticated users to create sites with the required permissions to launch the attack which lines up with Microsoft’s FAQ.
Microsoft SharePoint is another valuable target for threat actors, as was highlighted by CVE-2019-0604, an RCE in Microsoft SharePoint that continued to be exploited nine months after it was patched in the May 2019 Patch Tuesday.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains December 2020.
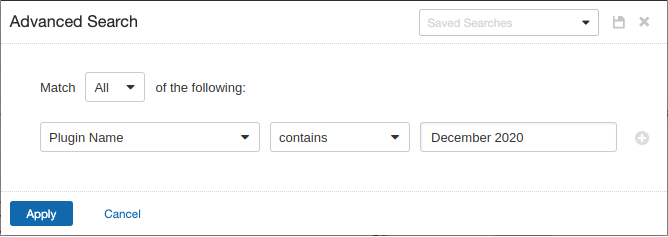
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from March 2019 using Tenable.io:
A list of all the plugins released for Tenable’s December 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's December 2020 Security Updates
- Tenable plugins for Microsoft December 2020 Patch Tuesday Security Updates
- Details on SAD DNS Attack (UC Riverside)
- Cloudflare Blog Post on SAD DNS Attack
- Video Demonstration of SAD DNS Attack
- Talos Vulnerability Spotlight: Code execution vulnerability in Microsoft Excel
- ZDI December 2020 Security Update Review
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

