Microsoft’s June 2021 Patch Tuesday Addresses 49 CVEs (CVE-2021-31955, CVE-2021-31956 and CVE-2021-33742)

Microsoft addresses 49 CVEs with six having been observed as exploited in the wild
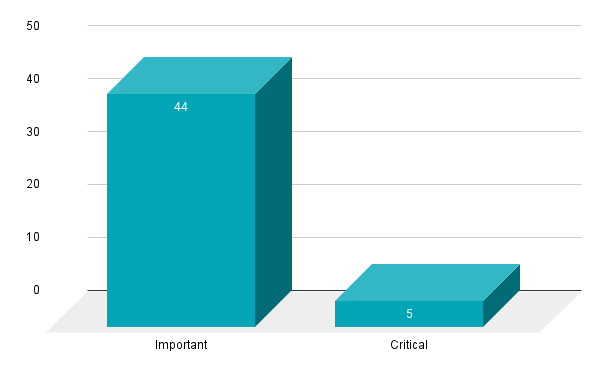
- 5Critical
- 44Important
- 0Moderate
- 0Low
Microsoft patched 49 CVEs in its June 2021 Patch Tuesday release, including five CVEs rated as critical and 44 rated as important.
Tenable's Security Response Team is aware that others may be counting CVE-2021-33741 as part of Patch Tuesday. However, it was patched on June 4 and is not included in our counts.

This month’s update includes fixes for:
- .NET Core & Visual Studio
- 3D Viewer
- Microsoft DWM Core Library
- Microsoft Intune
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Scripting Engine
- Microsoft Windows Codecs Library
- Paint 3D
- Role: Hyper-V
- Visual Studio Code - Kubernetes Tools
- Windows Bind Filter Driver
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows DCOM Server
- Windows Defender
- Windows Drivers
- Windows Event Logging Service
- Windows Filter Manager
- Windows HTML Platform
- Windows Installer
- Windows Kerberos
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Network File System
- Windows NTFS, Windows NTLM
- Windows Print Spooler Components
- Windows Remote Desktop
- Windows TCP/IP
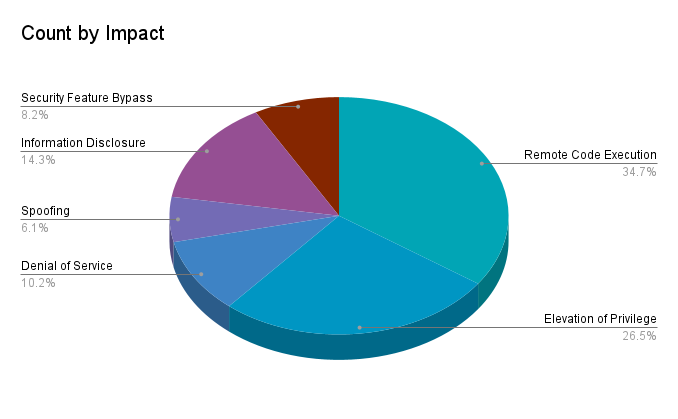
Remote code execution (RCE) vulnerabilities accounted for 34.7% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) at 26.5%.
CVE-2021-31955 | Windows Kernel Information Disclosure Vulnerability
CVE-2021-31955 is an information disclosure vulnerability in the Windows Kernel (ntoskrnl.exe). It was discovered by researchers at Kaspersky and is associated with a “wave of highly targeted attacks” by a group they call PuzzleMaker. An attacker could use this vulnerability to disclose information from the system, such as kernel addresses. They could then combine this with CVE-2021-31956 to elevate privileges on the targeted system.
CVE-2021-31956 | Windows NTFS Elevation of Privilege Vulnerability
CVE-2021-31956 is an EoP vulnerability within Windows NTFS (New Technology File System) which could allow a local user to elevate their privileges on an affected system. A local user could exploit the flaw with a crafted application in order to take control of a system. This vulnerability affects all currently supported Windows variants including Windows Server and Windows Server Core Installations. Microsoft notes that this flaw has been actively exploited in the wild as a zero-day. Like CVE-2021-31955, this vulnerability is credited to researchers at Kaspersky, who have linked this vulnerability to an attack chain from the PuzzleMaker Group, which includes the use of an unidentified Google Chrome zero-day vulnerability.
CVE-2021-33742 | Windows MSHTML Platform Remote Code Execution Vulnerability
CVE-2021-33742 is a RCE vulnerability in the Windows MSHTML Platform, Microsoft’s proprietary browser engine. The vulnerability received a CVSSv3 score of 7.5 and has been exploited in the wild as a zero-day. CVE-2021-33742 requires user interaction to exploit, so an attacker would need to entice a victim to open a crafted file or visit a malicious website using an affected application.This vulnerability affects all currently supported versions of Microsoft Windows. Microsoft also noted in their release that while the MSHTML Platform was designed for Internet Explorer, which has been retired, the underlying platforms including MSHTML are supported. Discovery of the vulnerability is credited to Clément Lecigne of Google’s Threat Analysis Group (TAG). Shane Huntley, director of the Google TAG says that, while they plan to share more details about the attack in the future, they have linked it to a “commercial exploit company” that has provided “capability for limited nation state Eastern Europe / Middle East targeting.”
More details will be on CVE-2021-33742 will come from the team, but for context this seem to be a commercial exploit company providing capability for limited nation state Eastern Europe / Middle East targeting.
— Shane Huntley (@ShaneHuntley) June 8, 2021
CVE-2021-31939 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2021-31939 is a use-after-free (UAF) vulnerability in Microsoft Excel that could lead to RCE if an attacker is able to convince a target into opening a crafted file. Researchers Sagi Tzadik and Netanel Ben-Simon of Check Point Research wrote a blog post describing their research and fuzzing of Microsoft Office, targeting the MSGraph COM component (MSGraph.Chart.8, GRAPH.EXE). This led to the discovery of CVE-2021-31939 along with three additional CVE’s patched in the May 2021 Patch Tuesday update; CVE-2021-31179, CVE-2021-31174, and CVE-2021-31178.
CVE-2021-31939 is also credited to Zhangjie and willJ from cdsrc, Anonymous working with Trend Micro Zero Day Initiative, Jinquan(@jq0904) of DBAPPSecurity Lieying Lab and Ryelv of Tencent. CVE-2021-31939 received a 5.5 CVSSv3 score and is labeled as “Exploitation Less Likely” by Microsoft with no currently known proof-of-concept code available.
CVE-2021-33739 | Microsoft Desktop Window Manager Core Library Elevation of Privilege Vulnerability
CVE-2021-33739 is an EoP vulnerability in the Microsoft Desktop Window Manager (DWM) core library, dwmcore.dll. It was discovered and reported to Microsoft by researchers at DBAPPSecurity Threat Intelligence Center. In February, DBAPPSecurity Threat Intelligence Center disclosed another zero-day vulnerability, CVE-2021-1732, an elevation of privilege vulnerability in Win32k linked to a threat actor known as BITTER APT. In April, researchers at Kaspersky disclosed CVE-2021-28310, an elevation of privilege zero-day vulnerability in Microsoft DWM Core Library that they connected to multiple threat actors including BITTER APT. While it has not yet been confirmed, it is possible this is another zero-day leveraged by BITTER APT in the wild.
CVE-2021-31983, CVE-2021-31946, CVE-2021-31945 | Multiple Vulnerabilities in Paint 3D
CVE-2021-31983, CVE-2021-31946 and CVE-2021-31945 are RCE vulnerabilities in Microsoft’s Paint 3D, which replaced the original MS Paint. All three received a CVSSv3 score of 7.8 and a severity of Important with an “Exploitation Less Likely” designation. These vulnerabilities are more interesting than concerning. They all require user interaction and the application will automatically update in most cases. However, all three vulnerabilities were discovered by several different researchers including Mat Powell from Trend Micro Zero Day Initiative, Li Qiao of Baidu Security Lab, and garmin working with Trend Micro Zero Day Initiative. One can only speculate why these researchers were examining Paint all at once, unless more information becomes available. Paint 3D wasn’t able to provide any insights either.
Beats us.
— Paint 3D Edu. (@Paint3Dedu) June 8, 2021
Tenable solutions
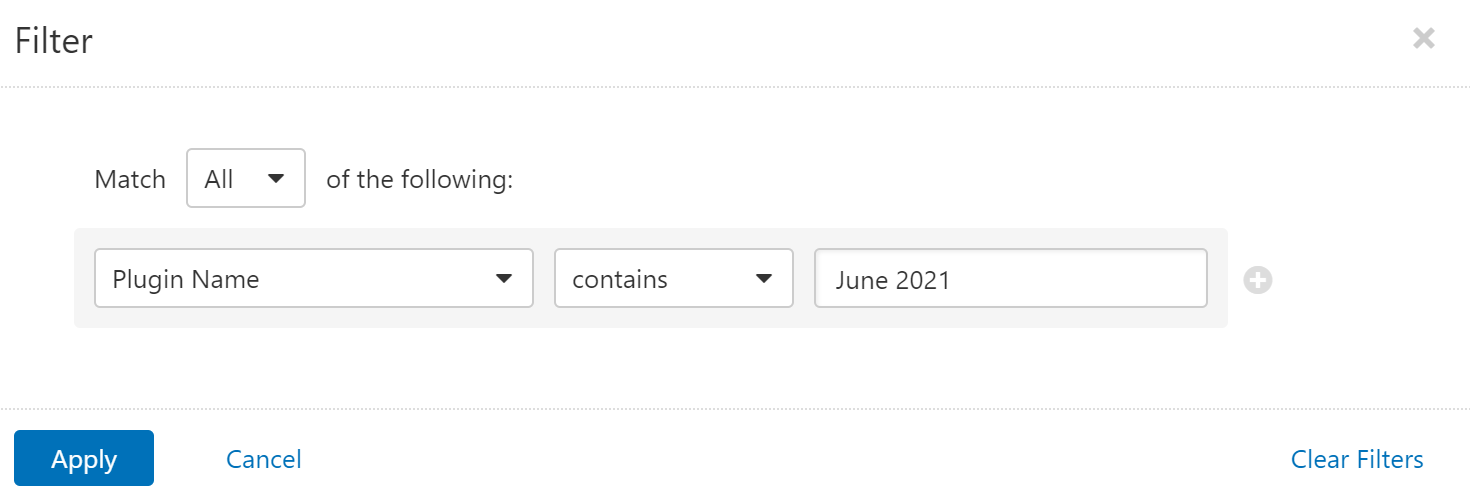
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains June 2021.
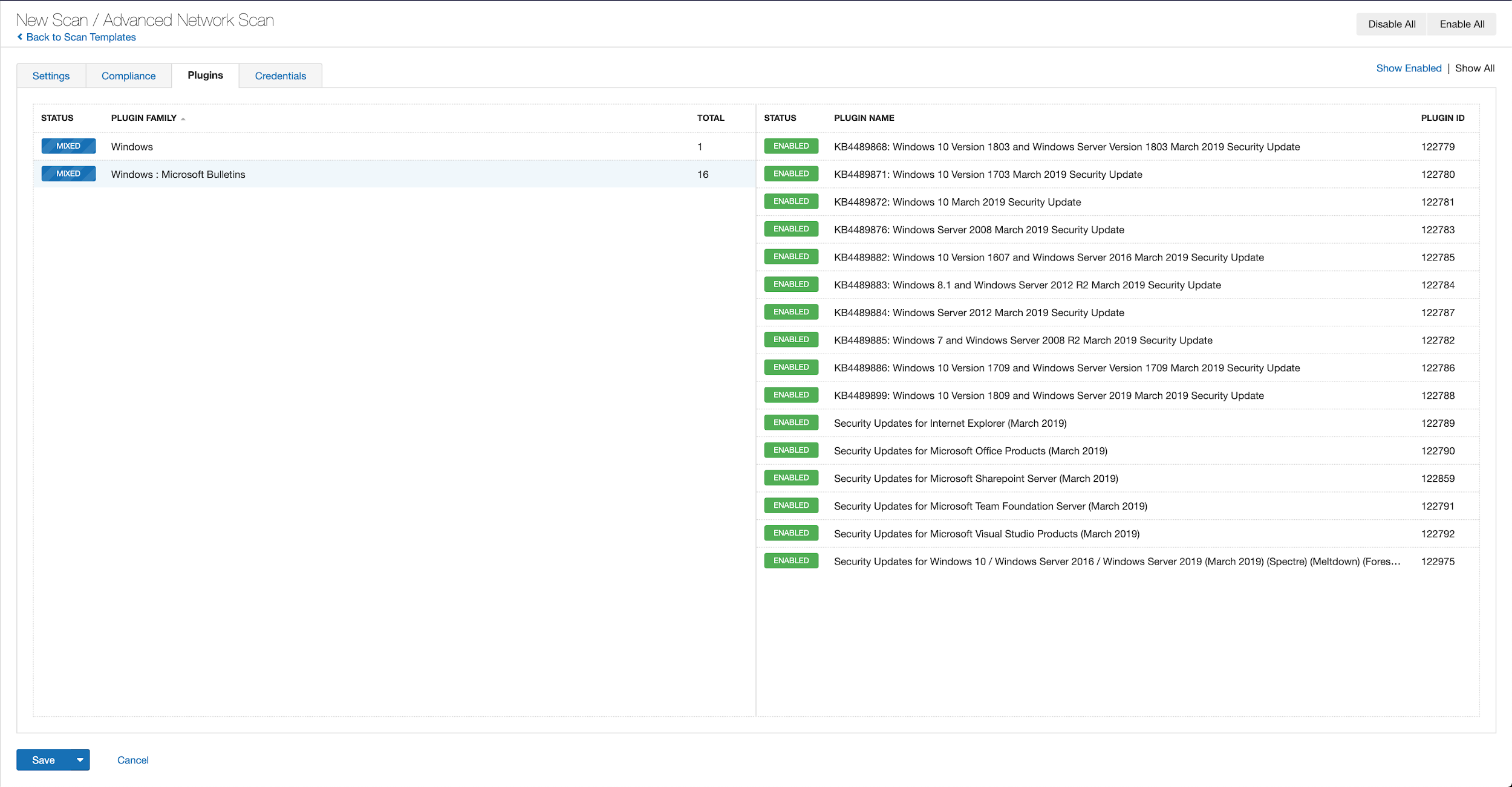
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s June 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's June 2021 Security Updates
- Tenable plugins for Microsoft June 2021 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

