Microsoft’s May 2021 Patch Tuesday Addresses 55 CVEs (CVE-2021-31166)

After crossing the 100 CVEs patched mark for the first time in April, Microsoft patched just 55 CVEs in May, the lowest number of CVEs patched this year.
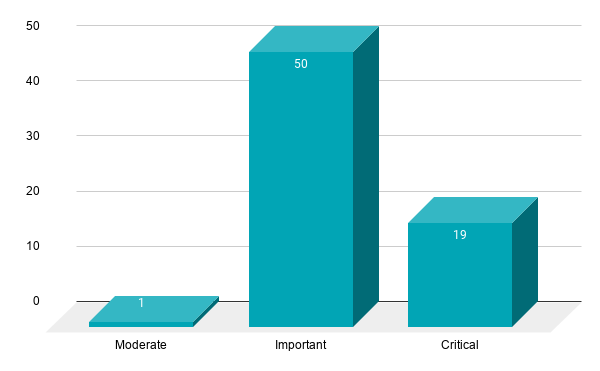
- 4Critical
- 50Important
- 1Moderate
- 0Low
Update May 17: The section for CVE-2021-31166 has been updated to reflect the release of proof-of-concept (PoC) code.
Microsoft patched 55 CVEs in the April 2021 Patch Tuesday release, including four CVEs rated as critical, 50 rated as important and one rated as moderate.
This month's Patch Tuesday release includes fixes for:
- .NET Core & Visual Studio
- HTTP.sys
- Internet Explorer
- Microsoft Accessibility Insights for Web
- Microsoft Bluetooth Driver
- Microsoft Dynamics Finance & Operations
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office, Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Windows Codecs Library
- Microsoft Windows IrDA
- Open Source Software
- Role: Hyper-V
- Skype for Business and Microsoft Lync
- Visual Studio
- Visual Studio Code
- Windows Container Isolation FS Filter Driver
- Windows Container Manager Service
- Windows Cryptographic Services
- Windows CSC Service
- Windows Desktop Bridge
- Windows OLE
- Windows Projected File System FS Filter
- Windows RDP Client
- Windows SMB, Windows SSDP Service
- Windows WalletService
- Windows Wireless Networking.
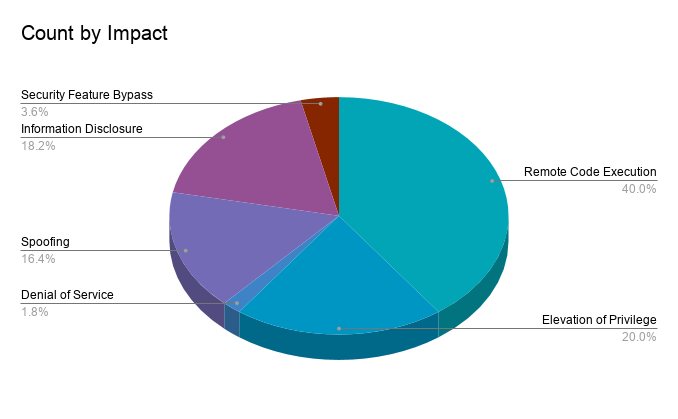
Remote code execution (RCE) vulnerabilities accounted for 40% of the vulnerabilities patched this month, followed by Elevation of Privilege (EoP) at 20%.
CVE-2021-31166 | HTTP Protocol Stack Remote Code Execution Vulnerability
CVE-2021-31166 is a RCE vulnerability which can be exploited by a remote, unauthenticated attacker sending a crafted HTTP packet to a system utilizing the HTTP Protocol Stack (http.sys). The vulnerability is considered to be wormable, which means that a single infection could result in a chain reaction of systems impacted across an enterprise without any user interaction. Microsoft assigned this critical flaw with a 9.8 CVSSv3 score, emphasizing the severity of the vulnerability. While details have not been released, this vulnerability is rated as “Exploitation More Likely” according to Microsoft’s Exploitability Index and we strongly recommend ensuring this patch is applied as soon as possible.
On May 16, security researcher 0vercl0k published PoC code to github for CVE-2021-31166. Based on our analysis, this exploit could only result in a denial of service (DoS) condition.
CVE-2021-28476 | Hyper-V Remote Code Execution Vulnerability
CVE-2021-28476 is a RCE vulnerability in Hyper-V which could allow a remote, unauthenticated attacker to compromise a Hyper-V host via a guest virtual machine (VM). The critical flaw was assigned a CVSSv3 score of 9.9, however it is rated as “Exploitation Less Likely.” The advisory from Microsoft does point out that the likely exploitation scenario for this flaw would result in a denial of service (DoS) condition, though in some cases RCE is possible as a guest VM could cause the Hyper-V host’s kernel to read from an arbitrary address.
CVE-2021-31198, CVE-2021-31207, CVE-2021-31209, CVE-2021-31195 | Multiple Exchange Server Vulnerabilities
CVE-2021-31198, CVE-2021-31207, CVE-2021-31209 and CVE-2021-31195 are several flaws that impact Microsoft Exchange Server 2013, 2016, and 2019 and are all rated “Exploitation Less Likely,” ranging in severity from CVSSv3 6.5 to 7.8. Given the history of prior Exchange Server vulnerabilities in 2021 we felt it was important to highlight them and ensure administrators take action.
CVE-2021-31209 is a server spoofing vulnerability and received a CVSSv3 score of 6.5. CVE-2021-31195 and CVE-2021-31198 are both RCE vulnerabilities, but CVE-2021-31198, which received a CVSSv3 score of 7.8, is listed as a local attack vector. On the other hand, CVE-2021-31195 received a CVSSv3 score of 6.5 and is listed as having no impact on integrity or availability. Both RCEs require user interaction to exploit.
Only one of these vulnerabilities, CVE-2021-31207 — a security feature bypass which received a CVSSv3 score of 6.6, was publicly disclosed. According to Microsoft, it was one of the Exchange Server vulnerabilities found during Pwn2Own 2021. None of these vulnerabilities have been reported as exploited in the wild at the time of publication.
Additionally, Microsoft is introducing new security functionality to Exchange Servers as part of the May Security Update that will allow administrators to validate the version information of their Exchange Servers. Microsoft’s Exchange Team published a blog post highlighting this new functionality.
CVE-2021-28474 and CVE-2021-31181 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2021-28474 and CVE-2021-31181 are a pair of RCE vulnerabilities in Microsoft SharePoint Server. Both were assigned a CVSSv3 score of 8.8 and a severity of Important. Microsoft rates these vulnerabilities as “Exploitation More Likely.” An attacker would need to be authenticated in order to exploit these flaws, though successful exploitation would grant an attacker remote code execution through the creation of a SharePoint site.
Windows 10 Version 1909 End of Life (EOL)
Microsoft has announced that the Home and Pro Windows 10, version 1909 and all editions of Windows Server, version 1909 have reached their end of life. These versions will no longer receive security updates and should be upgraded as soon as possible. The Education and Enterprise editions of Windows 10, version 1909 will remain supported until May 11, 2022, however, we do strongly encourage organizations to begin planning on upgrading or decommissioning these systems early to avoid last minute changes next year.
Tenable solutions
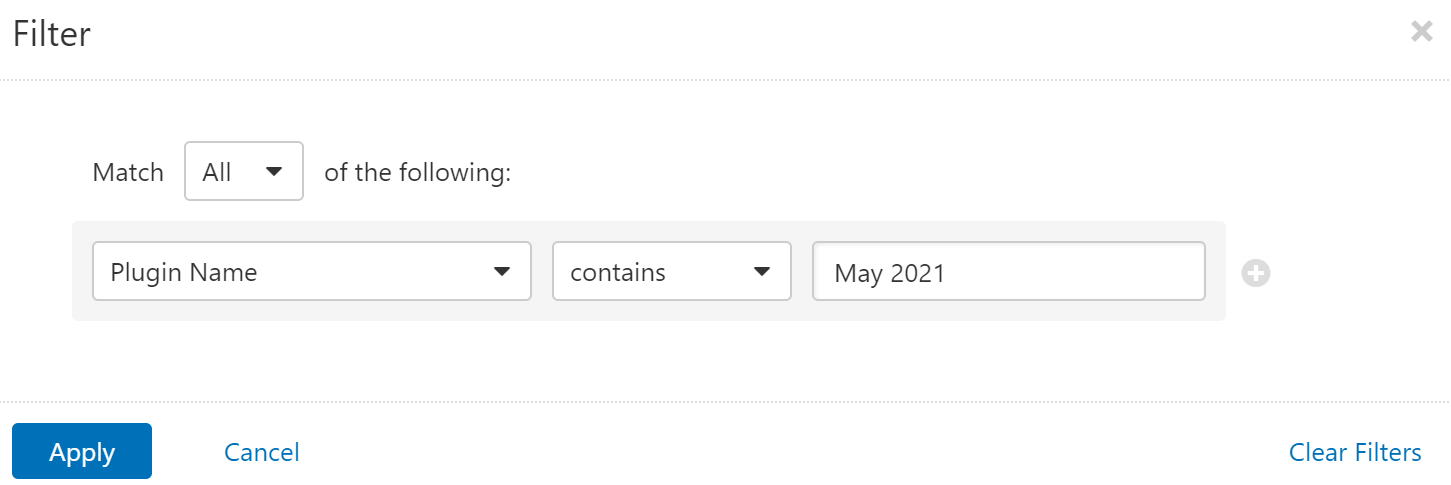
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains May 2021.
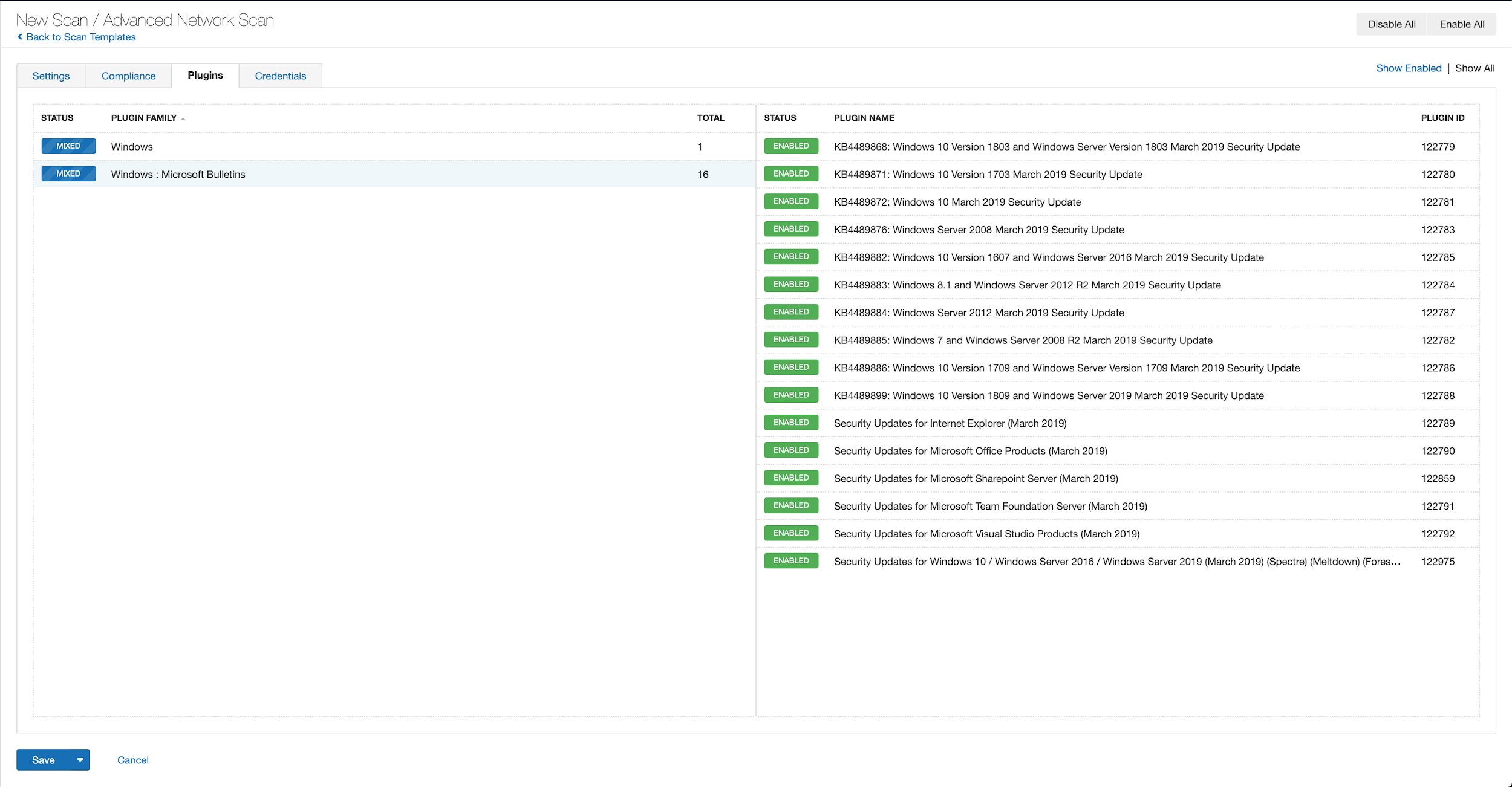
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s May 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's April 2021 Security Updates
- Tenable plugins for Microsoft April 2021 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

