Keeping Anti-Virus in Check

Nessus will generate a finding if the scan target has an Anti-Virus agent deployed with the virus detection rules out of date. We've often received feature requests asking us to allow customers to set a grace period (in days) to avoid generating this alert. Such a preference was added this week under the heading 'Antivirus Software Check':
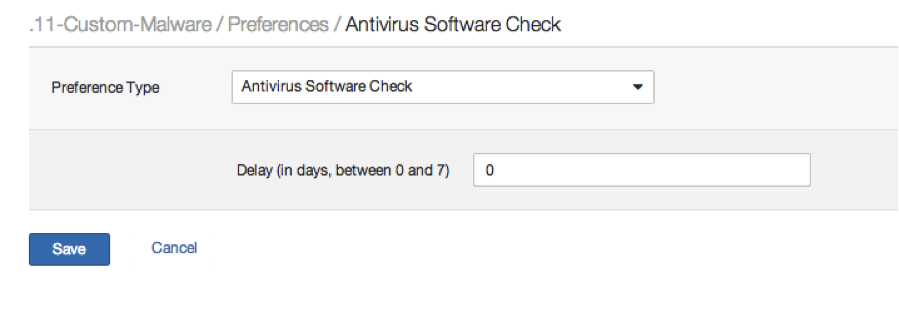
Why does a customer need this? Often customers have their own process for distributing Anti-Virus signature updates rather than using distribution automation that comes directly from their AV vendor. This process exists to allow IT to QA the impact of the rules on their applications and desktop environments before they are pushed out. There have been several instances where an AV vendor has pushed rules that caused applications to crash or prevented access to business critical functions. For example, in 2010 McAfee pushed an update that froze corporate PCs. This happened again in 2012.
In the age of APT, botnets and drive-by malware, getting ahead of the latest threats is extremely difficult. Ask yourself this question: “Why is it acceptable to delay the hard work of malware researchers from all over the world?” Then encourage your organization to take close look at your anti virus solution deployment process, and work to improve it such that you can at the very least quickly block the known malware threats.
- Nessus
- Threat Intelligence
- Threat Management
- Vulnerability Management
