Industrial Security and Tenable.sc Converge to Close the IT/OT Cyber Exposure Gap
Until now, security leaders have lacked visibility into the risk posture of the operational technology (OT) environments that are critical to their organization’s digitization initiatives. Security leaders now have a single platform to manage and measure cyber risk across both IT and OT.
Business-driven digitization initiatives increasingly require interconnected IT and OT systems to optimize production, drive innovation and increase sustainability. However, most security leaders responsible for managing and measuring cyber risk lack visibility into OT environments.
Security Leaders Cannot Manage and Measure Cyber Risk in OT
Traditional IT asset discovery and vulnerability assessment tools are not widely used in OT because they may disrupt operations. Therefore, security leaders don’t know what assets are installed in their OT environments, what unexpected connections need to be investigated, or what high-priority vulnerabilities must be remediated. The result: security leaders cannot manage and measure cyber risk in OT environments.
Effective risk management is built on a unified understanding of the entire IT/OT attack surface, which includes OT networks – many of which include IT-based systems – and IT networks. The problem is that identifying and assessing IT and OT devices each requires specialized technologies – active scanning for IT and passive monitoring for OT. And, until now, these specialized technologies resulted in disjointed data and a fractured understanding of converged cyber risk. Tenable considers this fractured understanding to be a significant cyber exposure gap for organizations, and one worth addressing.
Extend Processes and Controls to OT
IT Security leaders need to work with OT staff to extend existing IT processes and controls to the OT environment. Of course, adaptations will be required to accommodate unique OT constraints. Organizations may be tempted to independently implement separate processes and controls for IT and OT. This approach avoids the challenge of gaining agreement between IT and OT staff. However, it widens the cyber exposure gap and increases the likelihood of a business-disrupting cyber event.
For example, separate and disjointed IT and OT asset inventories could create a blind spot regarding which assets support an important manufacturing line, and a major upgrade to a dependent IT server could disrupt the entire manufacturing line. Similarly, remediation of vulnerabilities on the IT server may need to be prioritized higher because of its importance to the manufacturing process.
Now, a Single Cyber Exposure Solution Spans OT and IT
Tenable gives security leaders a Cyber Exposure solution that spans both OT and IT networks, from the plant floor up to enterprise applications. Selected asset and vulnerability data can now be imported from Industrial Security into Tenable.sc™ (previously SecurityCenter). Security leaders can now rely on a single platform to manage and measure cyber risk across both OT and IT networks.
Asset inventories deliver an up-to-date view of what must be protected. Vulnerability assessment identifies and prioritizes weaknesses that, if unremediated, could become a pathway for adversaries to compromise control systems and disrupt critical operational processes. Dashboard and report templates can be customized to simplify stakeholder communication.
The Tenable.sc™ on-premises cyber exposure platform, when used with Industrial Security™ includes multiple sensors and aggregation points, each optimized for IT and OT network requirements.
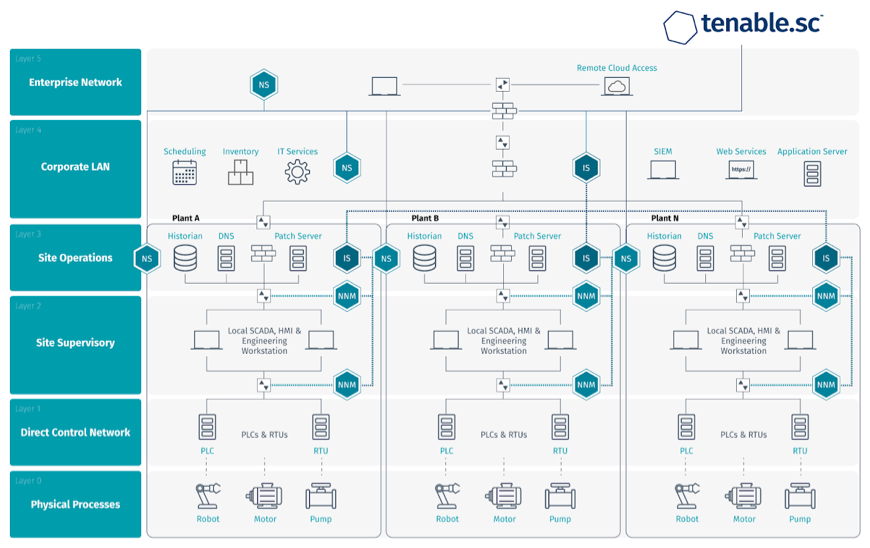
Tenable.sc™ delivers a unified view of information collected from Nessus scanners and Industrial Security consoles across IT/OT networks.
Cyber Exposure Technology Ecosystem Streamlines IT and Security Processes
Additionally, Tenable.sc™ integrates with many partners in the Tenable Cyber Exposure Technology Ecosystem to enhance remediation/response processes while utilizing existing investments. Examples include:
- Siemens professionals available to deliver and deploy Industrial Security and to provide a range of industrial control systems design and vulnerability management services.
- ITSM solutions, such as ServiceNow Security Operations Vulnerability Response, which synchronize asset records, incorporate asset criticality to enhance risk scoring, manage the remediation workflow and report status.
Learn More
Click here to learn more about how Tenable.sc™ and Industrial Security™ converge to help you manage and measure cyber risk in converged IT/OT environments.
- Internet of Things
- SCADA
- Vulnerability Management
- Vulnerability Scanning

