Detecting Snowden - The Insider Threat
The Insider Threat
When I discuss the insider threat with folks in the community, there seems to be several schools of thought. For example, some will apply a much lower risk to the insider threat, treating it as a one-off chance that an employee gets mad and does something bad out of spite. While this is a possibility, insider threats can run much deeper. We tend to pay attention to events that are in our face, such as an employee gone mad running around with WiFi DoS tools and malware-laced USB thumb drives. This would certainly catch our attention.

However, insider threat, while occurring less frequently, can often be much more damaging to your organization. A malicious insider who doesn't outwardly hold a grudge, or the person who keeps to themselves and seems happy, may pose the greatest risk. They do not want to be caught, as they are profiting in some way by acting as an insider. Edward Snowden is an interesting case, as his actions and motives represent a smaller use case, a threat that can only be recognized by nation states or corporations with something to hide (and enough at stake).
For the rest of the organizations in the world, they have two things in common that cause you to worry about the insider, intellectual property and PII. It boils down to protecting your information and other people's information that you may be storing or sending across your network.
In the case of Edward Snowden, it was released that he was crawling the network using automated tools throughout the day. In order to seek out information, Edward basically chose to scan the network for web servers and suck down all the information contained on them. This is a common strategy that good guys and bad guys alike are using to determine where your secrets may be hiding, and often in plain sight because it’s on the "internal" network and therefore it’s automatically protected. This is not always the case, as we seem to assume a higher level of security the deeper we go into our networks.
Detection
Detecting insiders poking around on the network can be very tricky. After all, they are most likely users that should be there, and at some level they must access systems and information on your network. So how do you pull out the anomalies? While it doesn't always work out to be so glaring, understanding what is "normal" and what is an "anomaly" is straightforward in a lot of cases. At least, you want to pick up on some of the behavior in your network that doesn't look right, and chances are that is just one part of a larger attack.
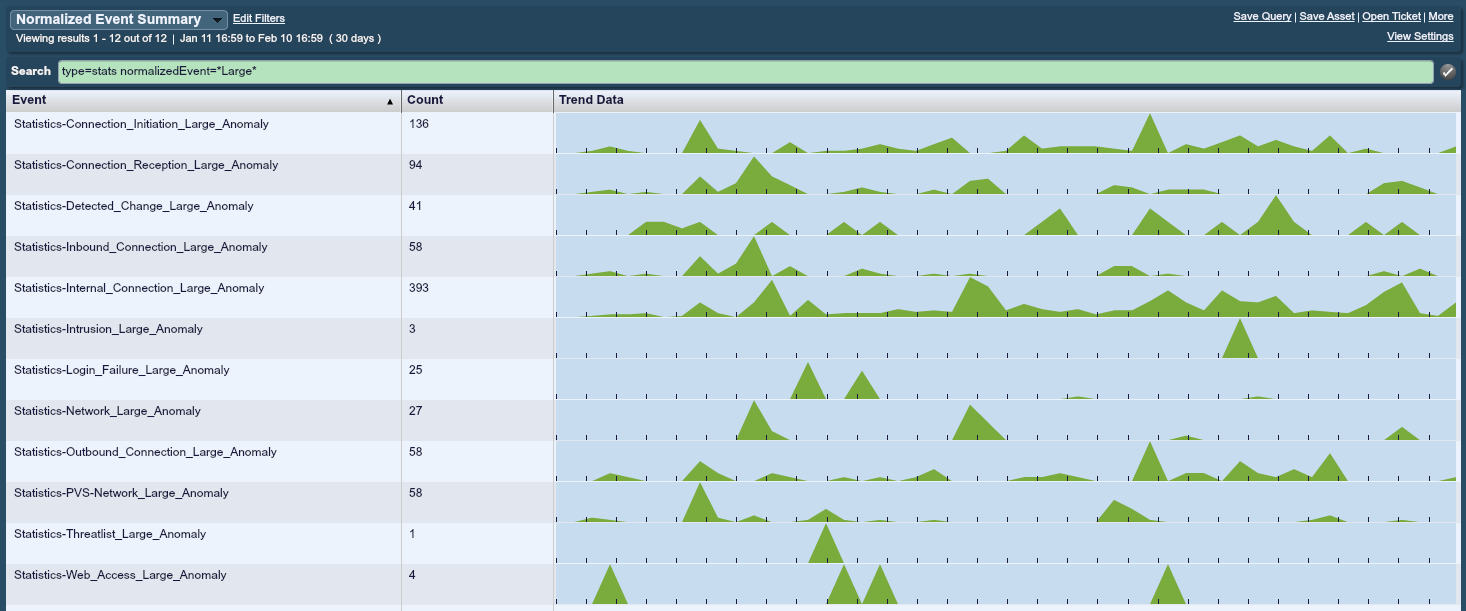
For example, take web crawling. When a user visits a website, they will land on the front page, click on one thing, read that one thing, and then click another. However, when a web crawler finds a website, the automated tool will visit every link on that page, and then visit every link on each subsequent page, including those that exist or not. From a logging perspective, this will always show up as an anomaly, as you will see a sharp increase in both page visits and site errors when someone is crawling your websites. Tenable's LCE (Log Correlation Engine) can visually depict this scenario, as shown below:
The screenshot shows all large anomalies over a 30-day period (by searching for "type=stats normalizedEvent="Large" in SecurityCenter). There are 4 instances of Statistics-Web_Access_Large_Anomoly events indicating there has been a spike in recorded web traffic over the normal amount. The events in LCE pull from all sources of web traffic including Tenable's Passive Vulnerability Scanner (PVS), Apache logs, and/or Blue Coat proxies.
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
If someone, such as Edward Snowden, was web crawling, and it was statistically greater than normal traffic, you could find this in SecurityCenter. LCE tracks spikes from an IP-centric point of view for both clients and servers. For example, if web host A has a spike in traffic, LCE also logs when client A is generating a spike, correlating the two so you can track it right back to a client IP address (e.g., Edward Snowden's workstation).
Conclusion
Tenable's scanning, sniffing, and logging products can comprehensively identify a variety of potentially malicious activity, including activity generated by malicious insiders. Tenable's SecurityCenter Continuous View solution can further automate the detection of events coming from scanners, intrusion detection systems, malware, compliance violations, and much more.
- Insider Threats
- LCE
- Log Analysis
- Nessus Network Monitor
- Passive Network Monitoring
- SecurityCenter