Detect The Latest OpenSSL Vulnerabilities Using Active and Passive Scanning
Tenable's products dig deep to uncover the latest round of OpenSSL vulnerabilities.
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
Several new vulnerabilities were disclosed in OpenSSL yesterday (yes the very same one which led to the Heartbleed vulnerability), along with updates for the popular open-source SSL library. One of the vulnerabilities is fairly serious, as it could allow for Man-In-The-Middle attacks under certain circumstances. Interesting notes about this new vulnerability include:
- The most serious vulnerability is CVE-2014-0224, which deals with how OpenSSL handles 'ChangeCipherSpec' messages in the SSL protocol, essentially tricking the client and server to communicate without encryption
- If we make a direct comparison to the Heartbleed vulnerability, the "ChangeCipherSpec" flaw is more difficult to exploit, as the attacker must be able to intercept communications between the client and the server
- Both client and server must be vulnerable in order for the attack to work (e.g. fixing just the client-side software fixes the issue)
- Modern web browsers (For example IE, Google Chrome, Mozilla Firefox, Safari) on desktops are not vulnerable as they are not using the OpenSSL libraries. However, Chrome for Android does use OpenSSL, and Google has released an updated version which fixes the vulnerability.
- This vulnerability is yet another tool for attackers targeting SSL and attempting to intercept communications. Researchers state this particular vulnerability has existed in the OpenSSL code since 1998.
New versions of the OpenSSL library are now available (including OpenSSL 0.9.8za, OpenSSL 1.0.0m and OpenSSL 1.0.1h).
Tenable has released several new updates for multiple products including Nessus and the Passive Vulnerability Scanner to help customers detect this vulnerability:
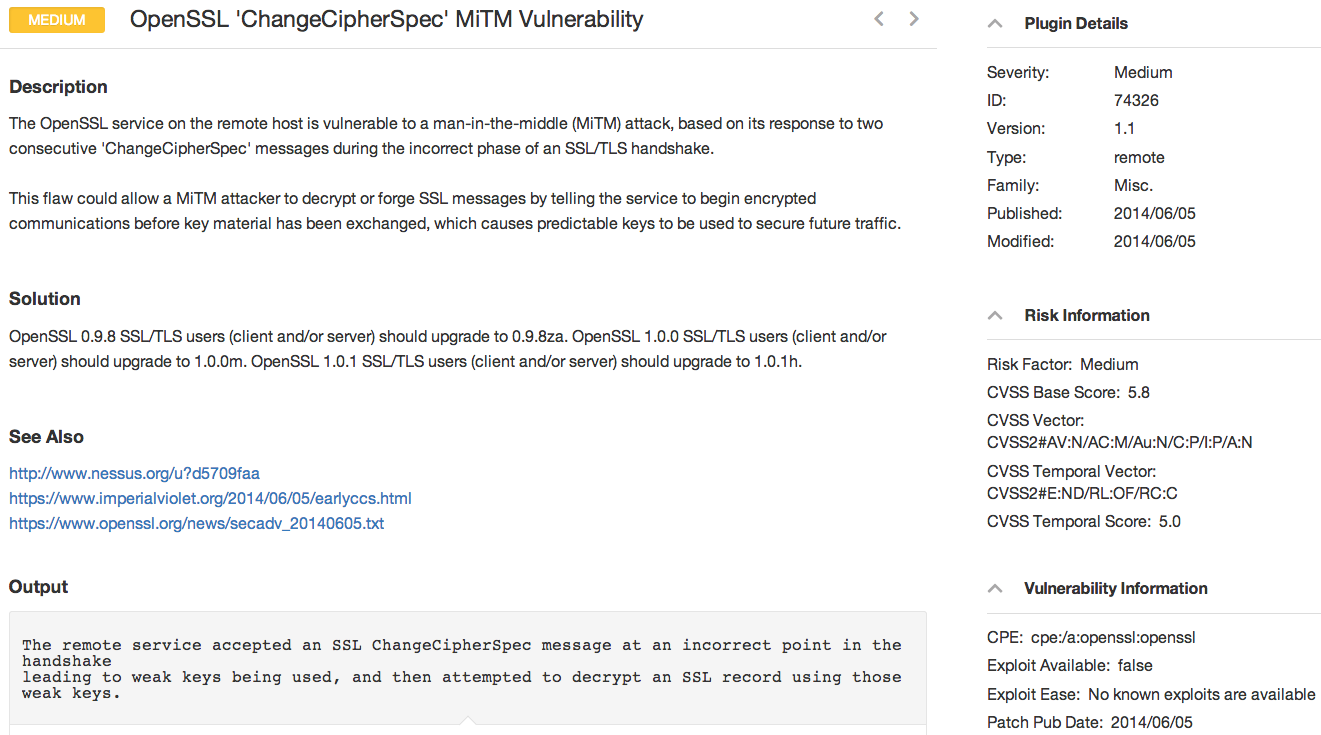
- Nessus Plugin 74326 has been released and accurately identifies vulnerable OpenSSL servers.
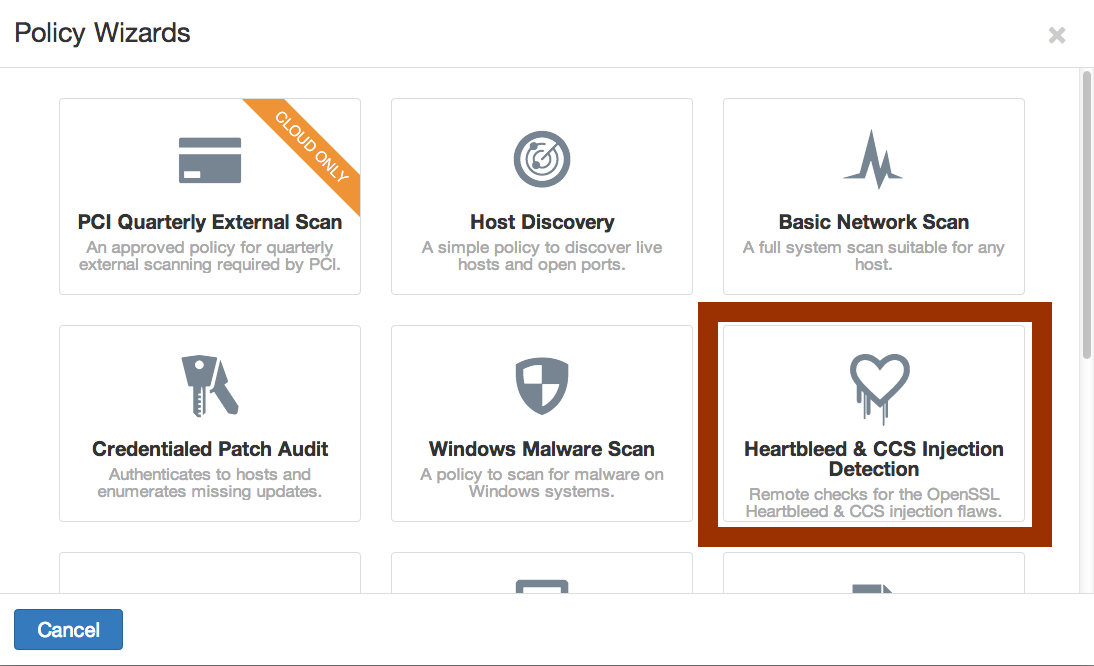
- An updated version Nessus UI has been pushed out to customers and includes an updated "Heartbleed" detection wizard which also enables plugin 74326
- The Passive Vulnerability Scanner plugin 8253 was added yesterday to detect OpenSSL < 0.9.8za / < 1.0.0m / < 1.0.1h Multiple Vulnerabilities
- Several popular Linux and UNIX distribution's local patch checks have been released to detect the vulnerability locally and will continue to be updated
- Nessus Enterprise Cloud was updated yesterday (including the new plugin and Nessus UI policy wizard)
Tenable customers can reference the Discussion Forum thread titled How to test the OpenSSL ChangeCipherSpec Vulnerability with Nessus (and Nessus Enterprise / Nessus Enterprise Cloud) to explore this vulnerability further and ask questions of our experts on this topic. Please visit Tenable's Support Portal for technical support related to detecting the latest OpenSSL vulnerability.
- Nessus
- Nessus Network Monitor
- OpenSSL
- Plugins