Cybersecurity Snapshot: CISA and NSA Dive into CI/CD Security, While MITRE Ranks Top Software Weaknesses

Learn about the guidance from the U.S. government for defending CI/CD pipelines. Plus, check out the 25 most dangerous software weaknesses. Also, what developers like about AI tools – and what they don’t. Et bien plus encore !
Dive into six things that are top of mind for the week ending July 14.
1 – CISA and NSA issue CI/CD defense guidance
Looking for recommendations and best practices to improve the security of your continuous integration / continuous delivery (CI/CD) pipelines? Check out the joint guidance from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA)
The 23-page guide, titled “Defending Continuous Integration/Continuous Delivery (CI/CD) Environments,” is aimed at DevSecOps teams tasked with quickly developing and releasing code into production.
“MCAs (malicious cyber actors) can multiply impacts severalfold by exploiting the source of software deployed to multiple operational environments,” the guide reads. “By exploiting a CI/CD environment, MCAs can gain an entryway into corporate networks and access sensitive data and services.”
The guide lists risks against CI/CD pipelines, describes the attack surface, outlines threat scenarios and details active hardening options for areas including authentication and access; development environment; and the development process.
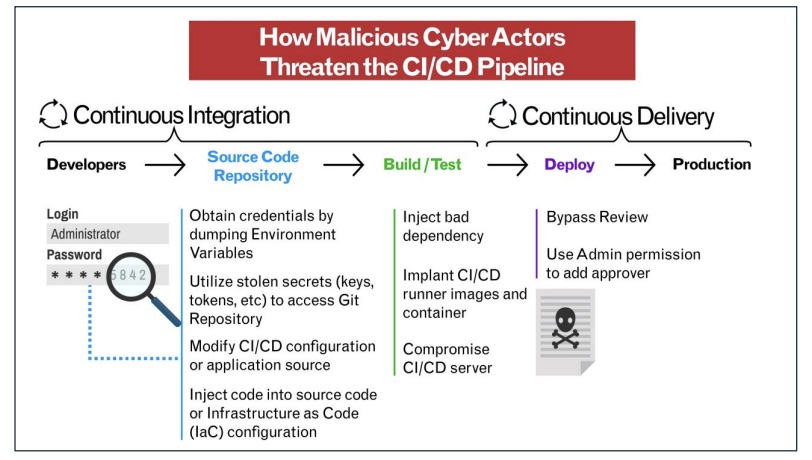
(Source : CISA/NSA)
For more information about CI/CD and supply chain security:
- “OWASP Top 10 CI/CD Security Risks (OWASP)
- “7 best practices to ensure your CI/CD pipeline's security” (TechTarget)
- “5 best practices for securing CI/CD pipelines” (InfoWorld)
- “Secure development and deployment guidance” (U.K. National Cyber Security Centre)
- “Four critical steps for CI/CD security” (SC Magazine)
2 – MITRE ranks nastiest software weaknesses
MITRE’s annual list of the most dangerous software weaknesses is out. Here’s what’s new in the “2023 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses” rankings.
- These are the top five:
- Out-of-bounds Write
CWE-787 - Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
CWE-79 - Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')
CWE-89 - Use After Free
CWE-416 - Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
CWE-78
- Out-of-bounds Write
- There are two new entries:
- This weakness is no longer on the list:
- CWE-611: Improper Restriction of XML External Entity Reference
The rankings are calculated by analyzing public vulnerability data in the National Vulnerability Database for root cause mappings to CWE weaknesses for the previous two calendar years.
“These weaknesses lead to serious vulnerabilities in software. An attacker can often exploit these vulnerabilities to take control of an affected system, steal data, or prevent applications from working,” reads a MITRE statement.
To get more details, check out:
- CISA’s announcement
- MITRE’s announcement
- A highlights summary
- A deep dive into the ranking methodology
- The full list
VIDEOS
What is CWE, why is it important, and how can it help me? (CWE & CAPEC Programs)
What is Common Weakness Enumeration (CWE)? (Debricked)
3 – Banks go bonkers for cloud computing
Financial services organizations have jumped into the cloud computing waters with both feet.
That’s a key takeaway from the Cloud Security Alliance’s “State of Financial Services in Cloud” report, which is based on interviews with dozens of CISOs, chief risk officers and other leaders in charge of cloud architecture and data governance at financial services organizations.
“No longer is the question as to whether cloud will be adopted but more about the execution of ‘how.’ How to adopt cloud-native security, how to apply zero trust, how to educate all relevant stakeholders from staff to regulators to cloud partners?,” reads the report.
Here are some of the main findings:
- 98% of respondents said their organization is using some form of cloud computing, up from 91% in 2020
- The percentage of organizations using the cloud for most of their business critical workloads spiked to 32% from 17% in 2020
- 84% of respondents said they currently have regulated data within their cloud architecture, up from 73%
- Zero trust ranked as the top topic of interest for respondents (72%)
Which of the following topics are you most interested in regarding the financial services industry?
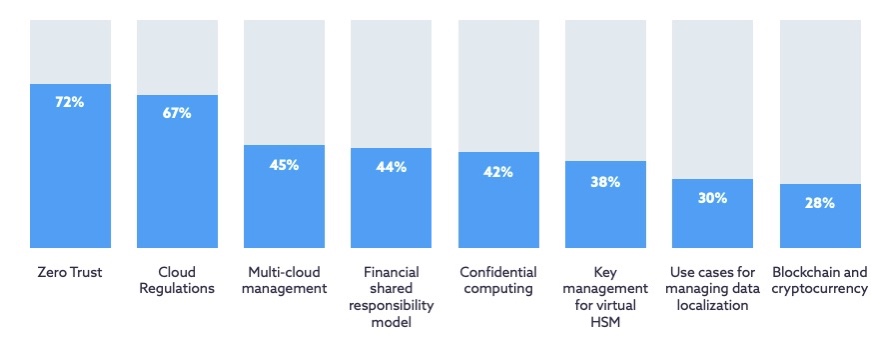
(Source : Cloud Security Alliance’s “State of Financial Services in Cloud” report, June 2023)
When asked to identify their main obstacles for deploying more sensitive cloud workloads, respondents ranked data privacy rules at the top, followed by compliance requirements and technical security control gaps.
“The predominant concerns mostly stem from meeting a very diverse set of regulatory requirements, resiliency to maintain the integrity and availability of financial systems to be accessible to the proper individuals, assurance those security controls can be demonstrated by third-party partners and the ability for staff to properly configure access controls,” the study reads.
To get more details:
- Read the CSA blog “Strong Winds Behind Financial Service Adoption of Cloud”
- Download the report “State of Financial Services in Cloud”
For more information about cloud adoption and cloud security in the financial services industry:
- “US government weighs in on cloud adoption in banking” (CIO Dive)
- “New Treasury Report Assesses Opportunities, Challenges Facing Financial Sector Cloud-Based Technology Adoption” (U.S. Treasury Department)
- “Cloud Skills Gap a Challenge for Financial Institutions” (InformationWeek)
- “Treasury Says Cloud Computing Poses Risks to Financial Sector” (Wall Street Journal)
4 – Developers dip their toes gingerly into AI tool use
Software developers are enthusiastic about the potential of AI development tools, but they’re treading carefully mostly due to concerns about these products’ current accuracy and precision.
That’s according to a survey conducted by Stack Overflow, the popular question-and-answer website for developers. Around 89,100 developers from 185 countries participated in the poll.
“It’s early days in the hype cycle for these newer AI technologies. We expect that a little more time may need to pass before we see developers using more AI tools more broadly,” Erin Yepis, Senior Analyst of Market Research and Insights at Stack Overflow, wrote in a blog.
Key findings include:
- 44% of respondents use AI tools in their development process now and another 26% plan to start using them soon
- Usage is concentrated on only two AI tools – ChatGPT (83%) and GitHub Copilot (56%)
- Increased productivity ranked as respondents’ top benefit (32.8%), followed by accelerated learning and greater efficiency
- Trust is an issue, with barely 3% of respondents saying they “highly trust” AI tools’ accuracy
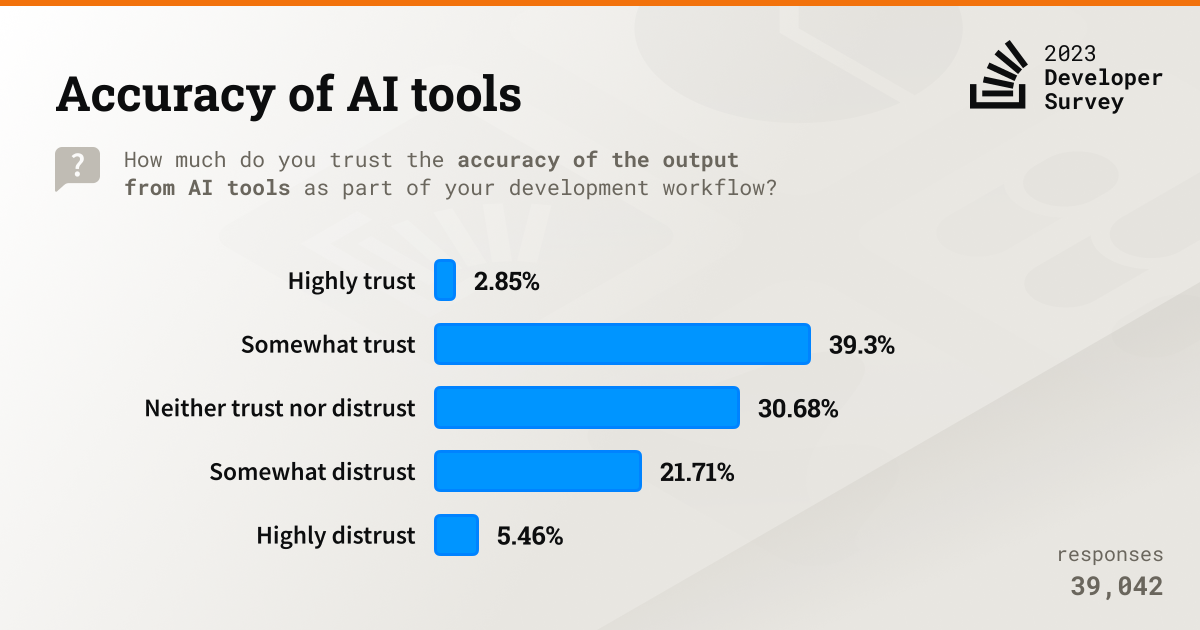
To get more details, check out:
- The blog “Hype or not? AI’s benefits for developers explored in the 2023 Developer Survey”
- A survey summary
- The full survey report
5 – White House outlines cybersecurity investment priorities
Defend critical infrastructure. Disrupt and dismantle threat actors. Invest in a resilient future. Those are three of the cybersecurity investment areas that U.S. government departments and agencies should prioritize for fiscal year 2025.
So said the Office of Management and Budget in a letter sent on behalf of the White House to the heads of executive branch departments and agencies. Here are more details about these U.S. government cybersecurity priorities.
- To defend critical infrastructure, agencies should, among other things, make progress in zero trust deployments, and modernize systems that are approaching their end of life
- With regards to dismantling and disrupting threat actors, a special emphasis should be put on combating ransomware in a way that’s sustained, coordinated and targeted
- In terms of investing in a resilient future, the letter stresses the importance of strengthening the cyber workforce and of preparing for future quantum computing
To get more details, read the letter and for more information about U.S. government cybersecurity efforts and priorities check out the National Cybersecurity Strategy, the Executive Order 14028, Improving the Nation’s Cybersecurity, the Zero Trust Maturity Model and the OMB Memorandum M-22-18, Enhancing the Security of the Software Supply Chain.
6 – What’s on CISA’s plate? Here’s a peek
And speaking of what’s cooking in terms of government cybersecurity efforts, leaders from CISA subcommittees met recently to discuss their ongoing work. Here’s a glimpse at some of the agency’s current priorities and their status.

- The “Transforming the Cyber Workforce” subcommittee is trying to gain insights into the future of work and on hybrid-workforce management.
- At the “Turning the Corner on Cyber Hygiene” subcommittee, the focus is on ensuring that vendors build tech products that are secure by default and by design.
- The “Building Resilience and Reducing Systemic Risk to Critical Infrastructure” subcommittee is centered on collaboration with the 16 critical infrastructure sectors.
Other subcommittees organized under CISA’s Cybersecurity Advisory Committee (CSAC) include the Technical Advisory Council, National Cybersecurity Alert System, and Corporate Cyber Responsibility.
To get more details, check out CISA’s readout from the latest quarterly meeting, the CSAC meeting agendas and CSAC’s main page.
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government



